|
Policeware
Computer and network surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today, and almost all Internet traffic can be monitored. Surveillance allows governments and other agencies to maintain social control, recognize and monitor threats or any suspicious or abnormal activity, and prevent and investigate criminal activities. With the advent of programs such as the Total Information Awareness program, technologies such as NarusInsight, high-speed surveillance computers and Surveillance#Biometric, biometrics software, and laws such as the Communications Assistan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or by wireless communication. The devices may be connected in a variety of network topologies. In order to communicate over the network, computers use agreed-on rules, called communication protocols, over whatever medium is used. The computer network can include personal computers, Server (computing), servers, networking hardware, or other specialized or general-purpose Host (network), hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymous (group)
Anonymous is a decentralized international Activism, activist and Hacktivism, hacktivist collective and Social movement, movement primarily known for its various cyberattacks against several governments, government institutions and Government agency, government agencies, corporations, and the Church of Scientology. Anonymous originated in 2003 on the imageboard 4chan representing the concept of many online and offline community users simultaneously existing as an "Anarchy, anarchic", digitized "global brain" or "Collective consciousness, hivemind". Anonymous members (known as ''anons'') can sometimes be distinguished in public by the wearing of Guy Fawkes masks in the style portrayed in the V for Vendetta, graphic novel and V for Vendetta (film), film ''V for Vendetta''. Some anons also opt to mask their voices through voice changers or text-to-speech programs. Dozens of people have been arrested for involvement in Anonymous cyberattacks in countries including the United Sta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
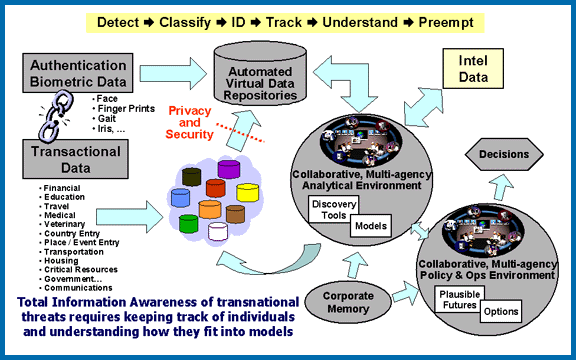
Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric warfare, asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Aware ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Voice Over Internet Protocol
Voice over Internet Protocol (VoIP), also known as IP telephony, is a set of technologies used primarily for voice communication sessions over Internet Protocol (IP) networks, such as the Internet. VoIP enables Voice call, voice calls to be transmitted as data packets, facilitating various methods of voice communication, including traditional applications like Skype, Microsoft Teams, Google Voice, and VoIP phones. Regular telephones can also be used for VoIP by connecting them to the Internet via Analog telephone adapter, analog telephone adapters (ATAs), which convert traditional telephone signals into digital data packets that can be transmitted over IP networks. The broader terms Internet telephony, broadband telephony, and broadband phone service specifically refer to the delivery of voice and other communication services, such as fax, SMS, and voice messaging, over the Internet, in contrast to the traditional public switched telephone network (PSTN), commonly known as plain ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Broadband Internet
In telecommunications, broadband or high speed is the wide- bandwidth data transmission that exploits signals at a wide spread of frequencies or several different simultaneous frequencies, and is used in fast Internet access. The transmission medium can be coaxial cable, optical fiber, wireless Internet (radio), twisted pair cable, or satellite. Originally used to mean 'using a wide-spread frequency' and for services that were analog at the lowest level, nowadays in the context of Internet access, 'broadband' is often used to mean any high-speed Internet access that is seemingly always 'on' and is faster than dial-up access over traditional analog or ISDN PSTN services. The ideal telecommunication network has the following characteristics: ''broadband'', ''multi-media'', ''multi-point'', ''multi-rate'' and economical implementation for a diversity of services (multi-services). The Broadband Integrated Services Digital Network (B-ISDN) was planned to provide these characte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aspen Publishers
Wolters Kluwer N.V. is a Dutch information services company. The company serves legal, business, tax, accounting, finance, audit, risk, compliance, and healthcare markets. Wolters Kluwer in its current form was founded in 1987 with a merger between Kluwer Publishers and Wolters Samsom. It operates in over 150 countries. The company is headquartered in Alphen aan den Rijn, Netherlands (Global). History Early history Jan-Berend Wolters founded the Schoolbook publishing house in Groningen, Groningen, Netherlands, in 1836. In 1858, the Noordhoff publishing house was founded alongside the Schoolbook publishing house. The two publishing houses merged in 1968. Wolters-Noordhoff merged with Information and Communications Union (ICU) in 1972 and took the name ICU. ICU acquired Croner Group, Croner in 1977, ICU changed its name to Wolters-Samsom in 1983. The company began serving foreign law firms and multinational companies in China in 1985. In 1987, Elsevier, the largest publishing hous ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Packet Capture
A packet analyzer (also packet sniffer or network analyzer) is a computer program or computer hardware such as a packet capture appliance that can analyze and log traffic that passes over a computer network or part of a network. Packet capture is the process of intercepting and logging traffic. As data streams flow across the network, the analyzer captures each packet and, if needed, decodes the packet's raw data, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications. A packet analyzer used for intercepting traffic on wireless networks is known as a wireless analyzer - those designed specifically for Wi-Fi networks are Wi-Fi analyzers. While a packet analyzer can also be referred to as a network analyzer or protocol analyzer these terms can also have other meanings. Protocol analyzer can technically be a broader, more general class that includes packet analyzers/sniffers. However, the terms a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Instant Messaging
Instant messaging (IM) technology is a type of synchronous computer-mediated communication involving the immediate ( real-time) transmission of messages between two or more parties over the Internet or another computer network. Originally involving simple text message exchanges, modern IM applications and services (also called "social messengers", "messaging apps", "chat apps" or "chat clients") tend to also feature the exchange of multimedia, emojis, file transfer, VoIP (voice calling), and video chat capabilities. Instant messaging systems facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list") or in chat rooms, and can be standalone apps or integrated into a wider social media platform, or in a website where it can, for instance, be used for conversational commerce. Originally the term "instant messaging" was distinguished from " text messaging" by being run on a computer network instead of a cellula ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Traffic
Web traffic is the data sent and received by visitors to a website. Since the mid-1990s, web traffic has been the largest portion of Internet traffic. Sites monitor the incoming and outgoing traffic to see which parts or pages of their site are popular and if there are any apparent trends, such as one specific page being viewed mostly by people in a particular country. There are many ways to monitor this traffic, and the gathered data is used to help structure sites, highlight security problems or indicate a potential lack of bandwidth. Not all web traffic is welcomed. Some companies offer advertising schemes that, in return for increased web traffic (visitors), pay for screen space on the site. Sites also often aim to increase their web traffic through inclusion on search engines and through search engine optimization. Analysis Web analytics is the measurement of the behavior of visitors to a website. In a commercial context, it especially refers to the measurement of whi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Email
Electronic mail (usually shortened to email; alternatively hyphenated e-mail) is a method of transmitting and receiving Digital media, digital messages using electronics, electronic devices over a computer network. It was conceived in the late–20th century as the digital version of, or counterpart to, mail (hence ''wikt:e-#Etymology 2, e- + mail''). Email is a ubiquitous and very widely used communication medium; in current use, an email address is often treated as a basic and necessary part of many processes in business, commerce, government, education, entertainment, and other spheres of daily life in most countries. Email operates across computer networks, primarily the Internet access, Internet, and also local area networks. Today's email systems are based on a store-and-forward model. Email Server (computing), servers accept, forward, deliver, and store messages. Neither the users nor their computers are required to be online simultaneously; they need to connect, ty ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Traffic
Internet traffic is the flow of data within the entire Internet, or in certain network links of its constituent networks. Common traffic measurements are total volume, in units of multiples of the byte, or as transmission rates in bytes per certain time units. As the topology of the Internet is not hierarchical, no single point of measurement is possible for total Internet traffic. Traffic data may be obtained from the Tier 1 network providers' peering points for indications of volume and growth. However, Such data excludes traffic that remains within a single service provider's network and traffic that crosses private peering points. As of December 2022 almost half (48%) of mobile Internet traffic is in India and China, while North America and Europe have about a quarter. However, mobile traffic remains a minority of total internet traffic. Traffic sources File sharing constitutes a fraction of Internet traffic. The prevalent technology for file sharing is the BitTorrent proto ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |