|
Naccache–Stern Knapsack Cryptosystem
The Naccache–Stern Knapsack cryptosystem is an atypical public-key cryptosystem developed by David Naccache and Jacques Stern in 1997. This cryptosystem is deterministic encryption, deterministic, and hence is not semantic security, semantically secure. While unbroken to date, this system also lacks provable security. System overview This system is based on a type of knapsack problem. Specifically, the underlying problem is this: given integers ''c'',''n'',''p'' and ''v''0,...,''v''''n'', find a vector x \in \^n such that :c \equiv \prod_^n v_i^ \mod p The idea here is that when the ''v''''i'' are relatively prime and much smaller than the modulus ''p'' this problem can be solved easily. It is this observation which allows decryption. Key Generation To generate a public/private key pair *Pick a large Prime number, prime modulus ''p''. *Pick a positive integer ''n'' and for ''i'' from 0 to ''n'', set ''p''''i'' to be the ''i''th prime, starting with ''p''0 = 2 and such that \pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public-key Cryptosystem
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. There are many kinds of public-key cryptosystems, with different security goals, including digital signature, Diffie–Hellman key exchange, public-key key encapsulation, and public-key encryption. Public key algorithms are fundamental security primitives in modern cryptosystems, including applications and protocols that offer assurance of the confidentiality and authenticity of electronic communications and data storage. They underpin numerous Internet standards, such as Transport Layer Security (TLS), SSH, S/MIME, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Merkle–Hellman Knapsack Cryptosystem
The Merkle–Hellman knapsack cryptosystem was one of the earliest public key cryptosystems. It was published by Ralph Merkle and Martin Hellman in 1978. A polynomial time attack was published by Adi Shamir in 1984. As a result, the cryptosystem is now considered insecure. History The concept of public key cryptography was introduced by Whitfield Diffie and Martin Hellman in 1976. At that time they proposed the general concept of a "trap-door one-way function", a function whose inverse is computationally infeasible to calculate without some secret "trap-door information"; but they had not yet found a practical example of such a function. Several specific public-key cryptosystems were then proposed by other researchers over the next few years, such as RSA in 1977 and Merkle-Hellman in 1978. Description Merkle–Hellman is a public key cryptosystem, meaning that two keys are used, a public key for encryption and a private key for decryption. It is based on the subset sum problem (a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hamming Weight
The Hamming weight of a string (computer science), string is the number of symbols that are different from the zero-symbol of the alphabet used. It is thus equivalent to the Hamming distance from the all-zero string of the same length. For the most typical case, a given set of bits, this is the number of bits set to 1, or the digit sum of the Binary numeral system, binary representation of a given number and the Taxicab geometry, ''ℓ''₁ norm of a bit vector. In this binary case, it is also called the population count, popcount, sideways sum, or bit summation. History and usage The Hamming weight is named after the American mathematician Richard Hamming, although he did not originate the notion. The Hamming weight of binary numbers was already used in 1899 by James Whitbread Lee Glaisher, James W. L. Glaisher to give a formula for Gould's sequence, the number of odd binomial coefficients in a single row of Pascal's triangle. Irving S. Reed introduced a concept, equivalen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
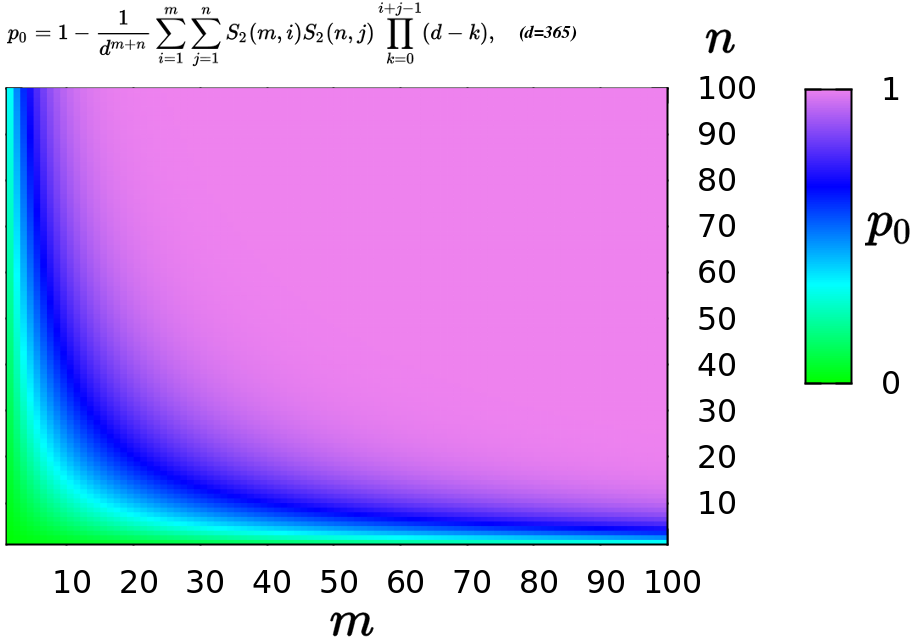
Birthday Paradox
In probability theory, the birthday problem asks for the probability that, in a set of randomly chosen people, at least two will share the same birthday. The birthday paradox is the counterintuitive fact that only 23 people are needed for that probability to exceed 50%. The birthday paradox is a veridical paradox: it seems wrong at first glance but is, in fact, true. While it may seem surprising that only 23 individuals are required to reach a 50% probability of a shared birthday, this result is made more intuitive by considering that the birthday comparisons will be made between every possible pair of individuals. With 23 individuals, there are = 253 pairs to consider. Real-world applications for the birthday problem include a cryptographic attack called the birthday attack, which uses this probabilistic model to reduce the complexity of finding a Collision attack, collision for a hash function, as well as calculating the approximate risk of a hash collision existi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shor's Algorithm
Shor's algorithm is a quantum algorithm for finding the prime factors of an integer. It was developed in 1994 by the American mathematician Peter Shor. It is one of the few known quantum algorithms with compelling potential applications and strong evidence of superpolynomial speedup compared to best known classical (non-quantum) algorithms. On the other hand, factoring numbers of practical significance requires far more qubits than available in the near future. Another concern is that noise in quantum circuits may undermine results, requiring additional qubits for quantum error correction. Shor proposed multiple similar algorithms for solving the factoring problem, the discrete logarithm problem, and the period-finding problem. "Shor's algorithm" usually refers to the factoring algorithm, but may refer to any of the three algorithms. The discrete logarithm algorithm and the factoring algorithm are instances of the period-finding algorithm, and all three are instances of the h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Discrete Logarithm Problem
In mathematics, for given real numbers a and b, the logarithm \log_b(a) is a number x such that b^x=a. Analogously, in any group G, powers b^k can be defined for all integers k, and the discrete logarithm \log_b(a) is an integer k such that b^k=a. In arithmetic modulo an integer m, the more commonly used term is index: One can write k=\mathbb_b a \pmod (read "the index of a to the base b modulo m") for b^k \equiv a \pmod if b is a primitive root of m and \gcd(a,m)=1. Discrete logarithms are quickly computable in a few special cases. However, no efficient method is known for computing them in general. In cryptography, the computational complexity of the discrete logarithm problem, along with its application, was first proposed in the Diffie–Hellman problem. Several important algorithms in public-key cryptography, such as ElGamal, base their security on the hardness assumption that the discrete logarithm problem (DLP) over carefully chosen groups has no efficient solution. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
LLL Algorithm
LLL may refer to: Businesses and organisations * L3 Technologies, an American defense contractor formerly with the NYSE stock symbol LLL * La Leche League, an organization that promotes breastfeeding Education * LL.L (''Legum Licentiatus''), a degree in civil law at various Canadian universities (especially in Québec) * Lifelong learning Lifelong learning is the "ongoing, voluntary, and self-motivated" pursuit of learning for either personal or professional reasons. Lifelong learning is important for an individual's competitiveness and employability, but also enhances social in ... * Lambda Lambda Lambda, a co-ed fraternity Entertainment * '' Leisure Suit Larry in the Land of the Lounge Lizards'', the first of a series of video games * ''Love's Labour's Lost'', a comedy by William Shakespeare * Landau, Luckman, and Lake, a fictional holding company in Marvel Comics * LLL, the production code for the 1972 ''Doctor Who'' serial ''The Sea Devils'' * "L. L. L.", a 2015 song ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Prime Number
A prime number (or a prime) is a natural number greater than 1 that is not a Product (mathematics), product of two smaller natural numbers. A natural number greater than 1 that is not prime is called a composite number. For example, 5 is prime because the only ways of writing it as a product, or , involve 5 itself. However, 4 is composite because it is a product (2 × 2) in which both numbers are smaller than 4. Primes are central in number theory because of the fundamental theorem of arithmetic: every natural number greater than 1 is either a prime itself or can be factorization, factorized as a product of primes that is unique up to their order. The property of being prime is called primality. A simple but slow primality test, method of checking the primality of a given number , called trial division, tests whether is a multiple of any integer between 2 and . Faster algorithms include the Miller–Rabin primality test, which is fast but has a small chance of error ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
David Naccache
David Naccache is a cryptographer, currently a professor at the École normale supérieure and a member of its Computer Laboratory. He was previously a professor at Panthéon-Assas University. Biography He received his Ph.D. in 1995 from the École nationale supérieure des télécommunications. Naccache's most notable work is in public-key cryptography, including the cryptanalysis of digital signature schemes. Together with Jacques Stern he designed the similarly named but very distinct Naccache-Stern cryptosystem and Naccache-Stern knapsack cryptosystem. In 2004 David Naccache and Claire Whelan, then employed by Gemplus International, used image processing techniques to uncover redacted information from the declassified 6 August 2001 President's Daily Brief '' Bin Ladin Determined To Strike in US''. They also demonstrated how the same process could be applied to other redacted documents. Naccache is also a visiting professor and researcher at the Information Secur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Relatively Prime
In number theory, two integers and are coprime, relatively prime or mutually prime if the only positive integer that is a divisor of both of them is 1. Consequently, any prime number that divides does not divide , and vice versa. This is equivalent to their greatest common divisor (GCD) being 1. One says also ''is prime to'' or ''is coprime with'' . The numbers 8 and 9 are coprime, despite the fact that neither—considered individually—is a prime number, since 1 is their only common divisor. On the other hand, 6 and 9 are not coprime, because they are both divisible by 3. The numerator and denominator of a reduced fraction are coprime, by definition. Notation and testing When the integers and are coprime, the standard way of expressing this fact in mathematical notation is to indicate that their greatest common divisor is one, by the formula or . In their 1989 textbook '' Concrete Mathematics'', Ronald Graham, Donald Knuth, and Oren Patashnik proposed an alter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Knapsack Problem
The knapsack problem is the following problem in combinatorial optimization: :''Given a set of items, each with a weight and a value, determine which items to include in the collection so that the total weight is less than or equal to a given limit and the total value is as large as possible.'' It derives its name from the problem faced by someone who is constrained by a fixed-size knapsack and must fill it with the most valuable items. The problem often arises in resource allocation where the decision-makers have to choose from a set of non-divisible projects or tasks under a fixed budget or time constraint, respectively. The knapsack problem has been studied for more than a century, with early works dating as far back as 1897. The subset sum problem is a special case of the decision and 0-1 problems where each kind of item, the weight equals the value: w_i=v_i. In the field of cryptography, the term ''knapsack problem'' is often used to refer specifically to the subset sum pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |