|
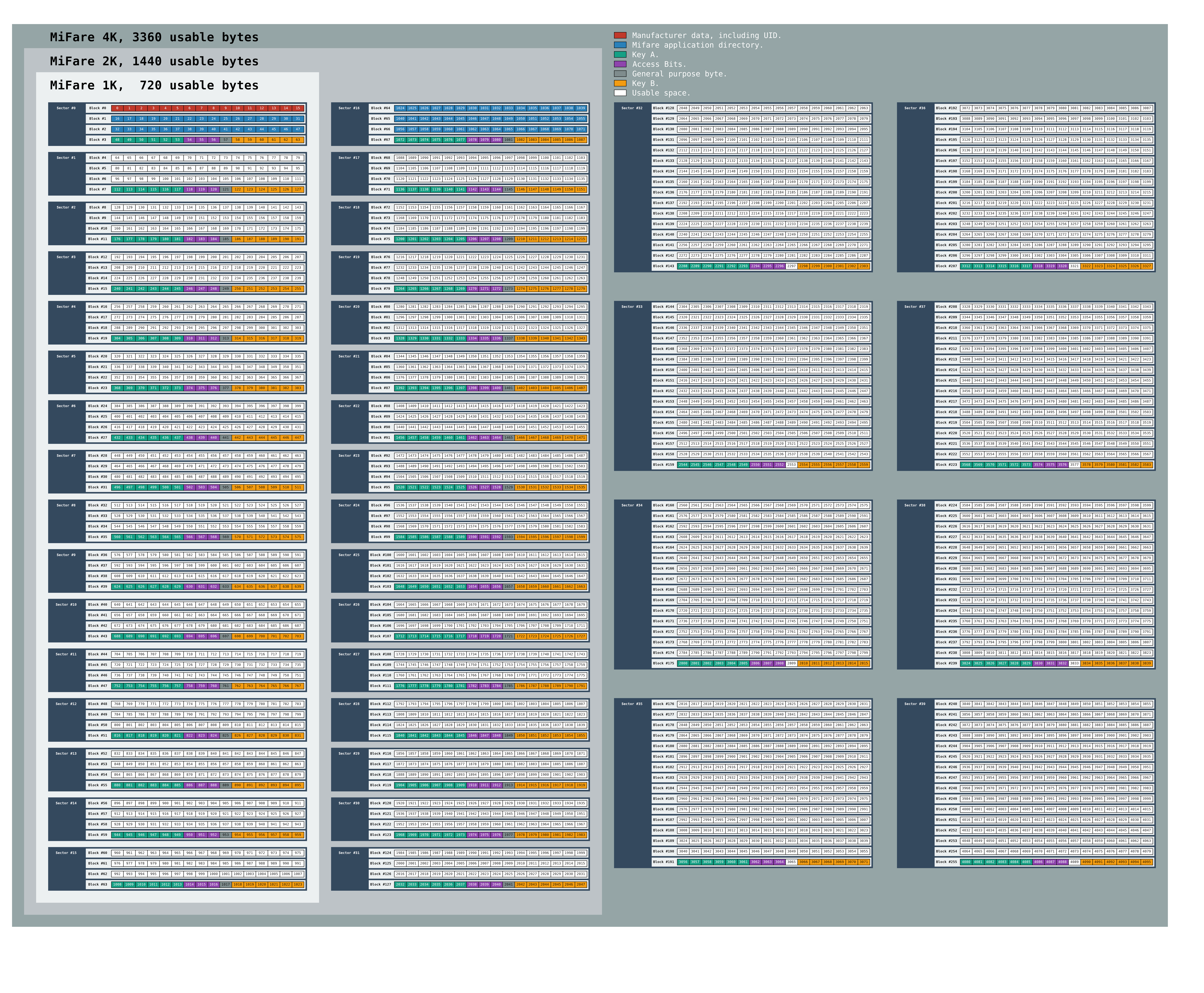
MiFare
MIFARE is a series of integrated circuit (IC) chips used in contactless smart cards and proximity cards. The brand includes proprietary solutions based on various levels of the ISO/IEC 14443 Type-A 13.56 MHz contactless smart card standard. It uses AES and DES/Triple-DES encryption standards, as well as an older proprietary encryption algorithm, Crypto-1. According to NXP, 10 billion of their smart card chips and over 150 million reader modules have been sold. The MIFARE trademark is owned by NXP Semiconductors, which was spun off from Philips Electronics in 2006. Variants MIFARE products are embedded in contactless and contact smart cards, smart paper tickets, wearables and phones. The MIFARE brand name (derived from the term MIKRON FARE collection and created by the company Mikron) covers four families of contactless cards: ; MIFARE Classic: Employs a proprietary protocol compliant with parts 1–3 of ISO/IEC 14443 Type A, with an NXP proprietary security prot ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mifare Logo Rgb
MIFARE is a series of Integrated Circuit, integrated circuit (IC) chips used in contactless smart cards and proximity cards. The brand includes proprietary solutions based on various levels of the ISO/IEC 14443 Type-A 13.56 Megahertz, MHz contactless smart card standard. It uses Advanced Encryption Standard, AES and Data Encryption Standard, DES/Triple-DES encryption standards, as well as an older proprietary encryption algorithm, Crypto-1. According to NXP, 10 billion of their smart card chips and over 150 million reader modules have been sold. The MIFARE trademark is owned by NXP Semiconductors, which was Corporate spin-off, spun off from Philips Electronics in 2006. Variants MIFARE products are embedded in Contactless smart card, contactless and contact smart cards, smart paper tickets, Wearable computer, wearables and phones. The MIFARE brand name (derived from the term MIKRON FARE collection and created by the company NXP Semiconductors, Mikron) covers four families of co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crypto-1
Crypto1 is a proprietary encryption algorithm (stream cipher) and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless smart cards launched in 1994. Such cards have been used in many notable systems, including Oyster card, CharlieCard and OV-chipkaart. By 2009, cryptographic research had reverse engineered the cipher and a variety of attacks were published that effectively broke the security. NXP responded by issuing "hardened" (but still backwards compatible) cards, the MIFARE Classic EV1. However, in 2015 a new attack rendered the cards insecure, and NXP now recommends migrating away from MIFARE Classic. Technical description Crypto1 is a stream cipher very similar in its structure to its successor, Hitag2. Crypto1 consists of * a 48-bit linear feedback shift register for the state of the cipher, * a two-layer 20-to-1 nonlinear function used to generate the keystream, and * a 16-bit LFSR which is used during the authentication phase ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Elliptic-curve Cryptography
Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC allows smaller keys to provide equivalent security, compared to cryptosystems based on modular exponentiation in Galois fields, such as the RSA cryptosystem and ElGamal cryptosystem. Elliptic curves are applicable for key agreement, digital signatures, pseudo-random generators and other tasks. Indirectly, they can be used for encryption by combining the key agreement with a symmetric encryption scheme. They are also used in several integer factorization algorithms that have applications in cryptography, such as Lenstra elliptic-curve factorization. History The use of elliptic curves in cryptography was suggested independently by Neal Koblitz and Victor S. Miller in 1985. Elliptic curve cryptography algorithms entered wide use in 2004 to 2005. In 1999, NIST recommended fifteen elliptic curves. Specifically, FIPS 186 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
2006 FIFA World Cup
The 2006 FIFA World Cup was the 18th FIFA World Cup, the quadrennial international Association football, football world championship tournament. It was held from 9 June to 9 July 2006 in Germany, which had won the right to FIFA World Cup hosts#2006 FIFA World Cup, host the event in July 2000. Teams representing 198 national football associations from all six populated continents participated in the 2006 FIFA World Cup qualification, qualification process which began in September 2003. Thirty-one teams qualified from this process along with hosts Germany national football team, Germany for the finals tournament. It was the second time that Germany staged the competition and the first as a German reunification, unified country along with the former East Germany with Leipzig as a host city (the other was in 1974 FIFA World Cup, 1974 in West Germany), and the 10th time that the tournament was held in Europe. Italy national football team, Italy won the tournament, claiming their fou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Message-authentication Code
In cryptography, a message authentication code (MAC), sometimes known as an authentication tag, is a short piece of information used for authenticating and integrity-checking a message. In other words, it is used to confirm that the message came from the stated sender (its authenticity) and has not been changed (its integrity). The MAC value allows verifiers (who also possess a secret key) to detect any changes to the message content. Terminology The term message integrity code (MIC) is frequently substituted for the term ''MAC'', especially in communications to distinguish it from the use of the latter as '' media access control address'' (''MAC address''). However, some authors use MIC to refer to a message digest, which aims only to uniquely but opaquely identify a single message. RFC 4949 recommends avoiding the term ''message integrity code'' (MIC), and instead using ''checksum'', ''error detection code'', ''hash'', ''keyed hash'', ''message authentication code'', or ''prote ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distance-bounding Protocol
Distance bounding protocols are cryptographic protocols that enable a verifier V to establish an upper bound on the physical distance to a prover P. They are based on timing the delay between sending out challenge bits and receiving back the corresponding response bits. The delay time for responses enables V to compute an upper-bound on the distance, as the round trip delay time divided into twice the speed of light. The computation is based on the fact that electro-magnetic waves travel nearly at the speed of light, but cannot travel faster. Distance bounding protocols can have different applications. For example, when a person conducts a cryptographic identification protocol at an entrance to a building, the access control computer in the building would like to be ensured that the person giving the responses is no more than a few meters away. RF Implementation The distance bound computed by a radio frequency distance bounding protocol is very sensitive to even the slightest ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
APDU
In the context of smart cards, an application protocol data unit (APDU) is the communication unit between a smart card reader and a smart card. The structure of the APDU is defined by ISO/IEC 7816-4 ''Organization, security and commands for interchange''. APDU message command-response pair There are two categories of APDUs: command APDUs and response APDUs. A command APDU is sent by the reader to the card – it contains a mandatory 4-byte header (CLA, INS, P1, P2) and from 0 to 65 535 bytes of data. A response APDU is sent by the card to the reader – it contains from 0 to 65 536 bytes of data, and 2 mandatory status bytes (SW1, SW2). References {{reflist See also * Protocol data unit In telecommunications, a protocol data unit (PDU) is a single unit of information transmitted among peer entities of a computer network. It is composed of protocol-specific control information and user data. In the layered architectures of c ... External links Smartcard ISOs, c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ISO 7816
ISO/IEC 7816 is an international standard related to electronic identification cards with contacts, especially smart cards, and more recently, contactless mobile devices, managed jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It is developed by ISO/IEC JTC 1 (Joint Technical Committee 1) / SC 17 (Subcommittee 17). The following describes the different parts of this standard. : ''Note: abstracts and dates, when present, are mere quotations from the ISO website, and are neither guaranteed at the time of edition nor in the future''. Parts * ISO/IEC 7816-1:2011 ''Part 1: Cards with contacts—Physical characteristics'' * ISO/IEC 7816-2:2007 ''Part 2: Cards with contacts—Dimensions and location of the contacts'' * ISO/IEC 7816-3:2006 ''Part 3: Cards with contacts—Electrical interface and transmission protocols'' * ISO/IEC 7816-4:2013 ''Part 4: Organization, security and commands for interchange'' * IS ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Size
In cryptography, key size or key length refers to the number of bits in a key used by a cryptographic algorithm (such as a cipher). Key length defines the upper-bound on an algorithm's security (i.e. a logarithmic measure of the fastest known attack against an algorithm), because the security of all algorithms can be violated by brute-force attacks. Ideally, the lower-bound on an algorithm's security is by design equal to the key length (that is, the algorithm's design does not detract from the degree of security inherent in the key length). Most symmetric-key algorithms are designed to have security equal to their key length. However, after design, a new attack might be discovered. For instance, Triple DES was designed to have a 168-bit key, but an attack of complexity 2112 is now known (i.e. Triple DES now only has 112 bits of security, and of the 168 bits in the key the attack has rendered 56 'ineffective' towards security). Nevertheless, as long as the security (understood ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Near Field Communication
Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of or less. NFC offers a low-speed connection through a simple setup that can be used for the bootstrapping of capable wireless connections. Like other proximity card technologies, NFC is based on inductive coupling between two electromagnetic coils present on a NFC-enabled device such as a smartphone. NFC communicating in one or both directions uses a frequency of 13.56 MHz in the globally available unlicensed radio frequency ISM band, compliant with the ISO/IEC 18000-3 air interface standard at data rates ranging from 106 to 848 kbit/s. The NFC Forum has helped define and promote the technology, setting standards for certifying device compliance. Secure communications are available by applying encryption algorithms as is done for credit cards and if they fit the criteria for being considered a personal area network. NFC ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TecTile
TecTiles are a near field communication (NFC) application, developed by Samsung, for use with mobile smartphone devices. Each TecTile is a low-cost self-adhesive sticker with an embedded NFC Tag. They are programmed before use, which can be done simply by the user, using a downloadable Android app. When an NFC-capable phone is placed or 'tapped' on a Tag, the programmed action is undertaken. This could cause a website to be displayed, the phone switched to silent mode, or many other possible actions. NFC Tags are an application of RFID technology. Unlike most RFID, which makes an effort to give a long reading range, NFC deliberately limits this range to only a few inches or almost touching the phone to the Tag. This is done deliberately, so that Tags have no effect on a phone unless there is a clear user action to 'trigger' the Tag. Although phones are usually touched to Tags, this does not require any 'docking' or galvanic contact with the Tag, so they are still considered to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |