|
MAC Address Anonymization
MAC address anonymization performs a one-way function on a MAC address so that the result may be used in tracking systems for reporting and the general public, while making it nearly impossible to obtain the original MAC address from the result. The idea is that this process allows companies like Google and CrowdVisionwhich track users' movements via their computer hardwareto simultaneously protect the identities of the people they are tracking while tracking the hardware itself. Flawed approaches Simple hashing An example of MAC address anonymization would be to use a simple hash algorithm. Given an address of 11:22:33:44:55:66, the MD5 hash algorithm produces eb341820cd3a3485461a61b1e97d31b1 (32 hexadecimal digits). An address only one character different (11:22:33:44:55:67) produces 391907146439938c9821856fa181052e, an entirely different hash due to the avalanche effect. The problem lies in the fact that there are only 248 (281,474,976,710,656) possible MAC addresses. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-way Function
In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here, "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems. This has nothing to do with whether the function is one-to-one; finding any one input with the desired image is considered a successful inversion. (See , below.) The existence of such one-way functions is still an open conjecture. Their existence would prove that the complexity classes P and NP are not equal, thus resolving the foremost unsolved question of theoretical computer science.Oded Goldreich (2001). Foundations of Cryptography: Volume 1, Basic Toolsdraft availablefrom author's site). Cambridge University Press. . See als The converse is not known to be true, i.e. the existence of a proof that P ≠ NP would not directly imply the existence of one-way functions. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
K-anonymity
''k''-anonymity is a property possessed by certain anonymized data. The term ''k''-anonymity was first introduced by Pierangela Samarati and Latanya Sweeney in a paper published in 1998, although the concept dates to a 1986 paper by Tore Dalenius. ''k''-anonymity is an attempt to solve the problem "Given person-specific field-structured data, produce a release of the data with scientific guarantees that the individuals who are the subjects of the data cannot be re-identified while the data remain practically useful." A release of data is said to have the ''k''-anonymity property if the information for each person contained in the release cannot be distinguished from at least k - 1 individuals whose information also appear in the release. The guarantees provided by ''k''-anonymity are aspirational, not mathematical. Methods for ''k''-anonymization To use ''k''-anonymity to process a dataset so that it can be released with privacy protection, a data scientist must first examine ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Espionage Techniques
Espionage, spying, or intelligence gathering, as a subfield of the intelligence field, is the act of obtaining secret or confidential information (intelligence). A person who commits espionage on a mission-specific contract is called an ''espionage agent'' or ''spy''. A person who commits espionage as a fully employed officer of a government is called an intelligence officer. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as corpora ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Criminal Investigation
Criminal investigation is an applied science that involves the study of facts that are then used to inform criminal trials. A complete criminal investigation can include Search and seizure, searching, interviews, interrogations, Evidence (law), evidence collection and preservation, and various methods of investigation. Modern-day criminal investigations commonly employ many modern scientific techniques known collectively as forensic science. Criminal investigation is an ancient science that may have roots as far back as in the writings of the Code of Hammurabi. In the code, it is suggested that both the accuser and the accused had the right to present evidence they collected. In the modern era, criminals investigations are most often done by government Police, police forces. Private investigators are also commonly hired to complete or assist in criminal investigations. An early recorded professional criminal investigator was the English constable. Around 1250 CE, it was recorde ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crime Prevention
Crime prevention refers to strategies and measures that seek to reduce the risk of crime occurring by intervening before a crime has been committed. It encompasses many approaches, including developmental, situational, community-based and criminal-justice interventions, to address risk factors at individual, family, community and societal levels. These strategies aim to deter potential offenders, reduce opportunities for offending and mitigate the fear of crime among the public, and are used by many governments in their efforts to reduce crime, enforce the law, maintain criminal justice and uphold overall stability. Studies Criminologists, commissions and research bodies such as the World Health Organization, the United Nations, the United States National Research Council and the UK Audit Commission have analyzed their and others' research on what lowers the rates of interpersonal crime. They agree that governments must go beyond law enforcement and criminal justice to tackle ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Locating
Wireless communication (or just wireless, when the context allows) is the transfer of information (''telecommunication'') between two or more points without the use of an electrical conductor, optical fiber or other continuous guided medium for the transfer. The most common wireless technologies use radio waves. With radio waves, intended distances can be short, such as a few meters for Bluetooth, or as far as millions of kilometers for deep-space radio communications. It encompasses various types of fixed, mobile, and portable applications, including two-way radios, cellular telephones, personal digital assistants (PDAs), and wireless networking. Other examples of applications of radio ''wireless technology'' include GPS units, garage door openers, wireless computer mouse, keyboards and headsets, headphones, radio receivers, satellite television, broadcast television and cordless telephones. Somewhat less common methods of achieving wireless communications involve othe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Technology
Mobile technology is the technology used for Cellular network, cellular communication. Mobile technology has evolved rapidly over the past few years. Since the start of this millennium, a standard mobile device has gone from being no more than a simple two-way pager to being a mobile phone, GPS navigation device, an embedded web browser and instant messaging client, and a handheld gaming console. Many experts believe that the future of computer technology rests in mobile computing with wireless networking. Mobile computing by way of tablet computers is becoming more popular. Tablets are available on the 3G and 4G networks. Mobile communication convergence Source: Nikola Tesla laid the theoretical foundation for wireless communication in 1890. Guglielmo Marconi, known as the father of radio, first transmitted wireless signals two miles away in 1894. Mobile technology gave human society great change. The use of mobile technology in government departments can also be traced back to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GSM Standard
The Global System for Mobile Communications (GSM) is a family of standards to describe the protocols for second-generation ( 2G) digital cellular networks, as used by mobile devices such as mobile phones and mobile broadband modems. GSM is also a trade mark owned by the GSM Association. "GSM" may also refer to the voice codec initially used in GSM. 2G networks developed as a replacement for first generation ( 1G) analog cellular networks. The original GSM standard, which was developed by the European Telecommunications Standards Institute (ETSI), originally described a digital, circuit-switched network optimized for full duplex voice telephony, employing time division multiple access (TDMA) between stations. This expanded over time to include data communications, first by circuit-switched transport, then by packet data transport via its upgraded standards, GPRS and then EDGE. GSM exists in various versions based on the frequency bands used. GSM was first implemented in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Geolocation
In computing, Internet geolocation is software capable of deducing the geographic position of a device connected to the Internet. For example, the device's IP address can be used to determine the country, city, or ZIP code, determining its geographical location. Other methods include examination of Wi-Fi hotspots. Data sources An IP address is assigned to each device (e.g. computer, printer) participating in a computer network that uses the Internet Protocol for communication. The protocol specifies that each IP packet must have a header which contains, among other things, the IP address of the sender. There are a number of free and paid subscription geolocation databases, ranging from country level to state or city—including ZIP/post code level—each with varying claims of accuracy (generally higher at the country level). These databases typically contain IP address data, which may be used in firewalls, ad servers, routing, mail systems, websites, and other automated systems ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
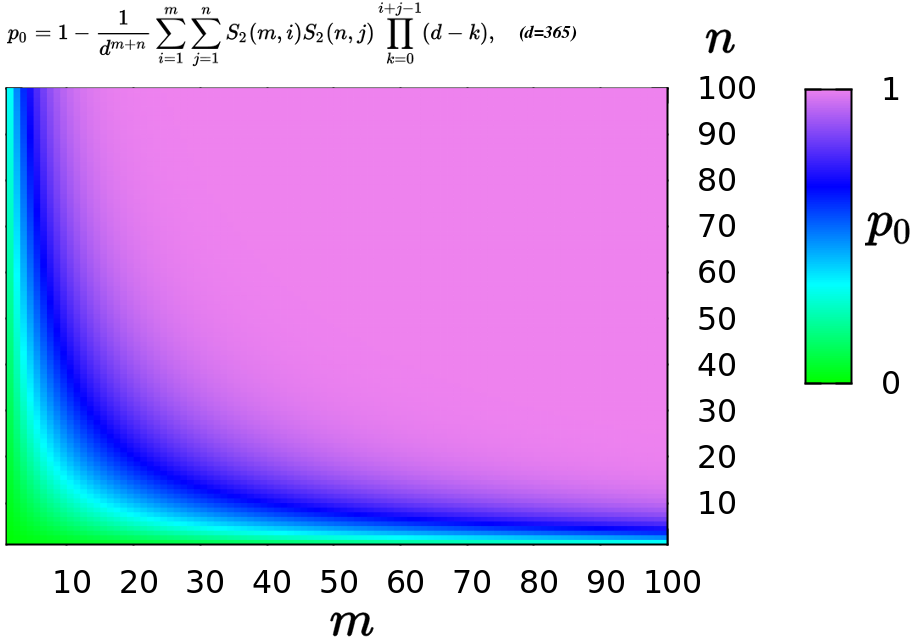
Birthday Paradox
In probability theory, the birthday problem asks for the probability that, in a set of randomly chosen people, at least two will share the same birthday. The birthday paradox is the counterintuitive fact that only 23 people are needed for that probability to exceed 50%. The birthday paradox is a veridical paradox: it seems wrong at first glance but is, in fact, true. While it may seem surprising that only 23 individuals are required to reach a 50% probability of a shared birthday, this result is made more intuitive by considering that the birthday comparisons will be made between every possible pair of individuals. With 23 individuals, there are = 253 pairs to consider. Real-world applications for the birthday problem include a cryptographic attack called the birthday attack, which uses this probabilistic model to reduce the complexity of finding a Collision attack, collision for a hash function, as well as calculating the approximate risk of a hash collision existi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bcrypt
bcrypt is a password-hashing function designed by Niels Provos and David Mazières. It is based on the Blowfish (cipher), Blowfish cipher and presented at USENIX in 1999. Besides incorporating a salt (cryptography), salt to protect against rainbow table attacks, bcrypt is an adaptive function: over time, the iteration count can be increased to make it slower, so it remains resistant to brute-force search attacks even with increasing computation power. The bcrypt function is the default password hash algorithm for OpenBSD, and was the default for some Linux distributions such as SUSE Linux. There are implementations of bcrypt in C (programming language), C, C++, C Sharp (programming language), C#, Embarcadero Delphi, Elixir (programming language), Elixir, Go (programming language), Go, Java (programming language), Java, JavaScript, Perl, PHP, Ruby (programming language), Ruby, Python (programming language), Python, Rust (programming language), Rust,V (programming language), V ( ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MAC Address
A MAC address (short for medium access control address or media access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use is common in most IEEE 802 networking technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the Open Systems Interconnection (OSI) network model, MAC addresses are used in the medium access control protocol sublayer of the data link layer. As typically represented, MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or without a separator. MAC addresses are primarily assigned by device manufacturers, and are therefore often referred to as the burned-in address, or as an Ethernet hardware address, hardware address, or physical address. Each address can be stored in the interface hardware, such as its read-only memory, or by a firmware mechanism. Many network interfaces, however, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |