|
Intelligence Cycle Security
National intelligence programs, and, by extension, the overall defenses of nations, are vulnerable to attack. It is the role of intelligence cycle security to protect the process embodied in the intelligence cycle, and that which it defends. A number of disciplines go into protecting the intelligence cycle. One of the challenges is there are a wide range of potential threats, so threat assessment, if complete, is a complex task. Governments try to protect three things: *Their intelligence personnel *Their intelligence facilities and resources *Their intelligence operations Defending the overall intelligence program, at a minimum, means taking actions to counter the major disciplines of intelligence collection techniques: *Human Intelligence (HUMINT) *Signals Intelligence ( SIGINT) *Imagery Intelligence ( IMINT) *Measurement and Signature Intelligence ( MASINT) *Technical Intelligence ( TECHINT) *Open Source Intelligence ( OSINT) To these are added at least one complementary dis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligence Cycle Management
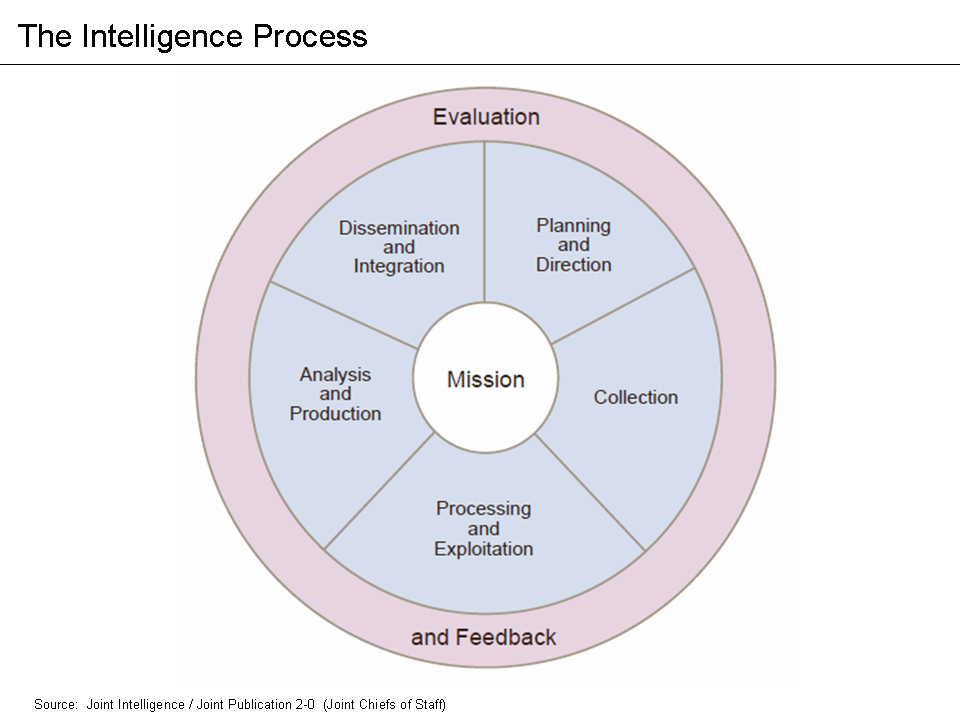
Intelligence cycle management refers to the overall activity of guiding the intelligence cycle, which is a set of processes used to provide decision-useful information (intelligence) to leaders. The cycle consists of several processes, including planning and direction (the focus of this article), collection, processing and exploitation, analysis and production, and dissemination and integration. The related field of counterintelligence is tasked with impeding the intelligence efforts of others. Intelligence organizations are not infallible (intelligence reports are often referred to as "estimates," and often include measures of confidence and reliability) but, when properly managed and tasked, can be among the most valuable tools of management and government. The principles of intelligence have been discussed and developed from the earliest writers on warfare to the most recent writers on technology. Despite the Supercomputer, most powerful computers, the human mind remains at the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Frank Wisner
Frank Gardiner Wisner (June 23, 1909 – October 29, 1965) was one of the founding officers of the Central Intelligence Agency (CIA) and played a major role in CIA operations throughout the 1950s. Wisner began his intelligence career in the Office of Strategic Services in World War II. After the war, he headed the Office of Policy Coordination (OPC), one of the OSS successor organizations, from 1948 to 1950. In 1950, the OPC was placed under the Central Intelligence Agency and renamed the Directorate of Plans. First headed by Allen Dulles, Wisner succeeded Dulles in 1951 when Dulles was named Director of Central Intelligence. Wisner remained as Deputy Director of Plans (DDP) until September 1958, playing an important role in the early history of the CIA. He suffered a breakdown in 1958, and retired from the Agency in 1962. He committed suicide in 1965. Education and early career Wisner was born in Laurel, Mississippi, the son of Mary (Gardiner), a schoolteacher, and Frank ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operation RAFTER
RAFTER was a code name for the MI5 radio receiver detection technique, mostly used against clandestine Soviet agents and monitoring of domestic radio transmissions by foreign embassy personnel from the 1950s on. Explanation Most radio receivers of the period were of the AM superhet design, with local oscillators which generate a signal typically 455 kHz above or sometimes below the frequency to be received. There is always some oscillator radiation leakage from such receivers, and in the initial stages of RAFTER, MI5 simply attempted to locate clandestine receivers by detecting the leaked signal with a sensitive custom-built receiver. This was complicated by domestic radios in people's homes also leaking radiation. By accident, one such receiver for MI5 mobile radio transmissions was being monitored when a passing transmitter produced a powerful signal which overloaded the receiver, producing an audible change in the received signal. The agency realized that they could ide ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spycatcher
''Spycatcher: The Candid Autobiography of a Senior Intelligence Officer'' (1987) is a memoir written by Peter Wright, former MI5 officer and assistant director, and co-author Paul Greengrass. Wright drew on his experiences and research into the history of the British intelligence community. Published first in Australia, the book was banned in England (but not Scotland) due to its allegations about government policy and incidents. These efforts ensured the book's notoriety, and it earned considerable profit for Wright. In 2021 and 2023, the Cabinet Office was still blocking or redacting freedom of information requests for files on the ''Spycatcher'' affair despite the rule that documents should be released after 30 years. Information belonging to the security services is absolutely exempted from the Freedom of Information Act. Content In ''Spycatcher'', Wright says that one of his assignments was to unmask a Soviet mole in MI5, who he says was Roger Hollis, a former ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peter Wright (MI5 Officer)
Peter Maurice Wright CBE (9 August 191626 April 1995) was a principal scientific officer for MI5, the British counter-intelligence agency. His book '' Spycatcher'', written with Paul Greengrass, became an international bestseller with sales of over two million copies. ''Spycatcher'' was part memoir, part exposé detailing what Wright claimed were serious institutional failures he investigated within MI5. Wright is said to have been influenced in his counterespionage activity by James Jesus Angleton, counter-intelligence chief of the US Central Intelligence Agency (CIA) from 1954 to 1975. Early life Peter Wright was born at 26 Cromwell Road, Chesterfield, Derbyshire, the son of (George) Maurice Wright CBE, director of research for the Marconi Company, who was one of the founders of signals intelligence during the First World War.Peter MartlandWright, Peter Maurice (1916–1995) ''Oxford Dictionary of National Biography'' (OUP, 2004), https://doi.org/10.1093/ref:odnb/57934 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DA-Notice
In the United Kingdom, D-Notices, officially known since 2015 as DSMA-Notices (Defence and Security Media Advisory Notices), are official requests to news editors not to publish or broadcast items on specified subjects for reasons of national security. DSMA-Notices were originally called Defence Notices (abbreviated to D-Notice) from their inception in 1912 to 1993, and DA-Notices (Defence Advisory Notices) from 1993 until the mid-2010s. A similar D-Notice system was previously operational in Australia, but has fallen into disuse. Sweden maintained a similar "gray notice" system during World War II, as described below. United Kingdom In the UK, the original D-notice system was introduced in 1912 and run as a voluntary system by a joint committee headed by an Assistant Secretary of the War Office and a representative of the Press Association. Any D-notices are only advisory requests and are not legally enforceable; hence, news editors can choose not to abide by them. However, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Censorship
Censorship is the suppression of speech, public communication, or other information. This may be done on the basis that such material is considered objectionable, harmful, sensitive, or "inconvenient". Censorship can be conducted by governments and private institutions. When an individual such as an author or other creator engages in censorship of their own works or speech, it is referred to as ''self-censorship''. General censorship occurs in a variety of different media, including speech, books, music, films, and other arts, Newspaper, the press, radio, television, and the Internet for a variety of claimed reasons including national security, to control obscenity, pornography, and hate speech, to protect children or other vulnerable groups, to promote or restrict political or religious views, and to prevent Defamation, slander and Defamation, libel. Specific rules and regulations regarding censorship vary between Legal Jurisdiction, legal jurisdictions and/or private organiza ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Attack
An electronic countermeasure (ECM) is an electrical or electronic device designed to trick or deceive radar, sonar, or other detection systems, like infrared (IR) or lasers. It may be used both offensively and defensively to deny targeting information to an enemy. The system may make many separate targets appear to the enemy, or make the real target appear to disappear or move about randomly. It is used effectively to protect aircraft from guided missiles. Most air forces use ECM to protect their aircraft from attack. It has also been deployed by military ships and recently on some advanced tanks to fool laser/IR guided missiles. It is frequently coupled with stealth advances so that the ECM systems have an easier job. Offensive ECM often takes the form of jamming. Self-protecting (defensive) ECM includes using blip enhancement and jamming of missile terminal homers. History The first example of electronic countermeasures being applied in a combat situation took place durin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Traffic Flow Security
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted. In general, the greater the number of messages observed, the greater information be inferred. Traffic analysis can be performed in the context of military intelligence, counter-intelligence, or pattern-of-life analysis, and is also a concern in computer security. Traffic analysis tasks may be supported by dedicated computer software programs. Advanced traffic analysis techniques which may include various forms of social network analysis. Traffic analysis has historically been a vital technique in cryptanalysis, especially when the attempted crack depends on successfully seeding a known-plaintext attack, which often requires an inspired guess based on how specific the operational context might likely influence what an adversary communicates, which may be sufficient to establish a short crib. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OPSEC
Operations security (OPSEC) is a process that identifies critical information to determine whether friendly actions can be observed by enemy intelligence, determines if information obtained by adversaries could be interpreted to be useful to them, and then executes selected measures that eliminate or reduce adversary exploitation of friendly critical information. The term "operations security" was coined by the United States military during the Vietnam War. History Vietnam In 1966, United States Admiral Ulysses Sharp established a multidisciplinary security team to investigate the failure of certain combat operations during the Vietnam War. This operation was dubbed Operation Purple Dragon, and included personnel from the National Security Agency and the Department of Defense. When the operation concluded, the Purple Dragon team codified their recommendations. They called the process "Operations Security" in order to distinguish the process from existing processes and en ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Counterintelligence
Counterintelligence (counter-intelligence) or counterespionage (counter-espionage) is any activity aimed at protecting an agency's Intelligence agency, intelligence program from an opposition's intelligence service. It includes gathering information and conducting activities to prevent espionage, sabotage, assassinations or other Intelligence field, intelligence activities conducted by, for, or on behalf of foreign powers, organizations or persons. Many countries will have multiple organizations focusing on a different aspect of counterintelligence, such as domestic, international, and counter-terrorism. Some states will formalize it as part of the police structure, such as the United States' Federal Bureau of Investigation (FBI). Others will establish independent bodies, such as the United Kingdom's MI5, others have both intelligence and counterintelligence grouped under the same agency, like the Canadian Security Intelligence Service (CSIS). History Modern tactics of espiona ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |