|
Hardware Encryption
Hardware-based encryption is the use of computer hardware to assist software, or sometimes replace software, in the process of data encryption. Typically, this is implemented as part of the processor's instruction set. For example, the AES encryption algorithm (a modern cipher) can be implemented using the AES instruction set on the ubiquitous x86 architecture. Such instructions also exist on the ARM architecture. However, more unusual systems exist where the cryptography module is separate from the central processor, instead being implemented as a coprocessor, in particular a secure cryptoprocessor or cryptographic accelerator, of which an example is the IBM 4758, or its successor, the IBM 4764. Hardware implementations can be faster and less prone to exploitation than traditional software implementations, and furthermore can be protected against tampering. History Prior to the use of computer hardware, cryptography could be performed through various mechanical or elec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Scytale
In cryptography, a scytale (; also transliterated skytale, ''skutálē'' "baton, cylinder", also ''skútalon'') is a tool used to perform a transposition cipher, consisting of a cylinder with a strip of parchment wound around it on which is written a message. The ancient Greeks, and the Sparta Sparta was a prominent city-state in Laconia in ancient Greece. In antiquity, the city-state was known as Lacedaemon (), while the name Sparta referred to its main settlement in the Evrotas Valley, valley of Evrotas (river), Evrotas rive ...ns in particular, are said to have used this cipher to communicate during military campaigns. The recipient uses a rod of the same diameter on which the parchment is wrapped to read the message. Encrypting Suppose the rod allows one to write four letters around in a circle and five letters down the side of it. The plaintext could be: "I am hurt very badly help". To encrypt, one simply writes across the leather: ________________________ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Online Shopping
Online shopping is a form of electronic commerce which allows consumers to directly buy goods or services from a seller over the Internet using a web browser or a mobile app. Consumers find a product of interest by visiting the website of the retailer directly or by searching among alternative vendors using a shopping search engine, which displays the same product's availability and pricing at different e-retailers. customers can shop online using a range of different computers and devices, including desktop computers, laptops, tablet computers and smartphones. Online stores that evoke the physical analogy of buying products or services at a regular "brick-and-mortar" retailer or shopping center follow a process called business-to-consumer (B2C) online shopping. When an online store is set up to enable businesses to buy from another business, the process is instead called business-to-business (B2B) online shopping. A typical online store enables the customer to browse t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
World Wide Web
The World Wide Web (WWW or simply the Web) is an information system that enables Content (media), content sharing over the Internet through user-friendly ways meant to appeal to users beyond Information technology, IT specialists and hobbyists. It allows documents and other web resources to be accessed over the Internet according to specific rules of the HTTP, Hypertext Transfer Protocol (HTTP). The Web was invented by English computer scientist Tim Berners-Lee while at CERN in 1989 and opened to the public in 1993. It was conceived as a "universal linked information system". Documents and other media content are made available to the network through web servers and can be accessed by programs such as web browsers. Servers and resources on the World Wide Web are identified and located through character strings called uniform resource locators (URLs). The original and still very common document type is a web page formatted in Hypertext Markup Language (HTML). This markup lang ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Microcomputer
A microcomputer is a small, relatively inexpensive computer having a central processing unit (CPU) made out of a microprocessor. The computer also includes memory and input/output (I/O) circuitry together mounted on a printed circuit board (PCB). Microcomputers became popular in the 1970s and 1980s with the advent of increasingly powerful microprocessors. The predecessors to these computers, mainframes and minicomputers, were comparatively much larger and more expensive (though indeed present-day mainframes such as the IBM System z machines use one or more custom microprocessors as their CPUs). Many microcomputers (when equipped with a keyboard and screen for input and output) are also personal computers (in the generic sense). An early use of the term "personal computer" in 1962 predates microprocessor-based designs. ''(See "Personal Computer: Computers at Companies" reference below)''. A "microcomputer" used as an embedded control system may have no human-readable input and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
SIGSALY
SIGSALY (also known as the X System, Project X, Ciphony I, and the Green Hornet) was a secure voice, secure speech system used in World War II for the highest-level Allies of World War II, Allied communications. It pioneered a number of digital communications concepts, including the first transmission of speech using pulse-code modulation. The name SIGSALY was not an acronym, but a cover name that resembled an acronym—the SIG part was common in Army Signal Corps names (e.g., SIGABA). The prototype was called the "Green Hornet" after the radio show ''The Green Hornet (radio series), The Green Hornet'', because it sounded like a buzzing hornet, resembling the show's theme tune, to anyone trying to eavesdrop on the conversation. Development At the time of its inception, long-distance telephone communications used the "A-3" voice scrambler developed by Western Electric. It worked on the voice inversion principle. The Germans had a listening station on the Dutch coast which could int ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
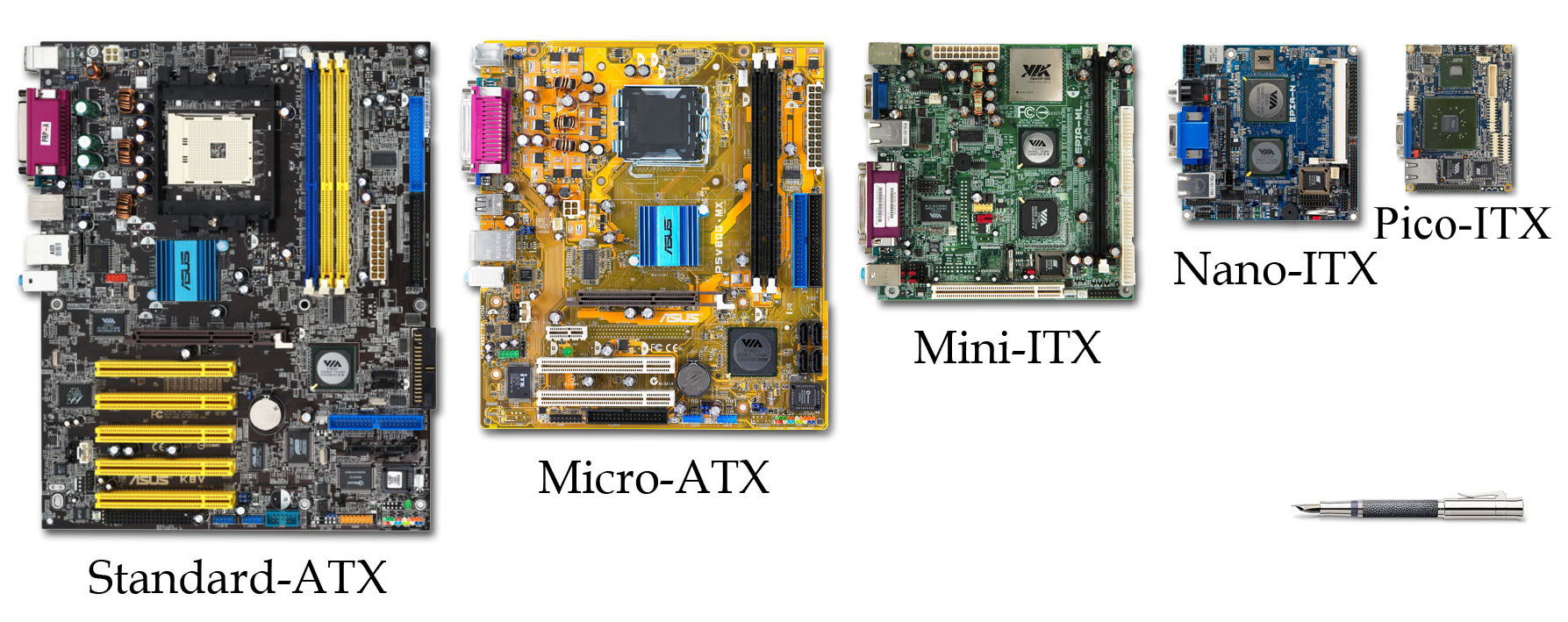 |
Form Factor (design)
Form factor is a hardware design aspect that defines and prescribes the size, shape, and other physical specifications of components, particularly in electronics. A form factor may represent a broad class of similarly sized components, or it may prescribe a specific standard. It may also define an entire system, as in a computer form factor. Evolution and standardization As electronic hardware has become smaller following Moore's law and related patterns, ever-smaller form factors have become feasible. Specific technological advances, such as PCI Express, have had a significant design impact, though form factors have historically evolved slower than individual components. Standardization of form factors is vital for hardware compatibility between different manufacturers. Trade-offs Smaller form factors may offer more efficient use of limited space, greater flexibility in the placement of components within a larger assembly, reduced use of material, and greater ease of transportat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Integrated Circuit
An integrated circuit (IC), also known as a microchip or simply chip, is a set of electronic circuits, consisting of various electronic components (such as transistors, resistors, and capacitors) and their interconnections. These components are etched onto a small, flat piece ("chip") of semiconductor material, usually silicon. Integrated circuits are used in a wide range of electronic devices, including computers, smartphones, and televisions, to perform various functions such as processing and storing information. They have greatly impacted the field of electronics by enabling device miniaturization and enhanced functionality. Integrated circuits are orders of magnitude smaller, faster, and less expensive than those constructed of discrete components, allowing a large transistor count. The IC's mass production capability, reliability, and building-block approach to integrated circuit design have ensured the rapid adoption of standardized ICs in place of designs using discre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
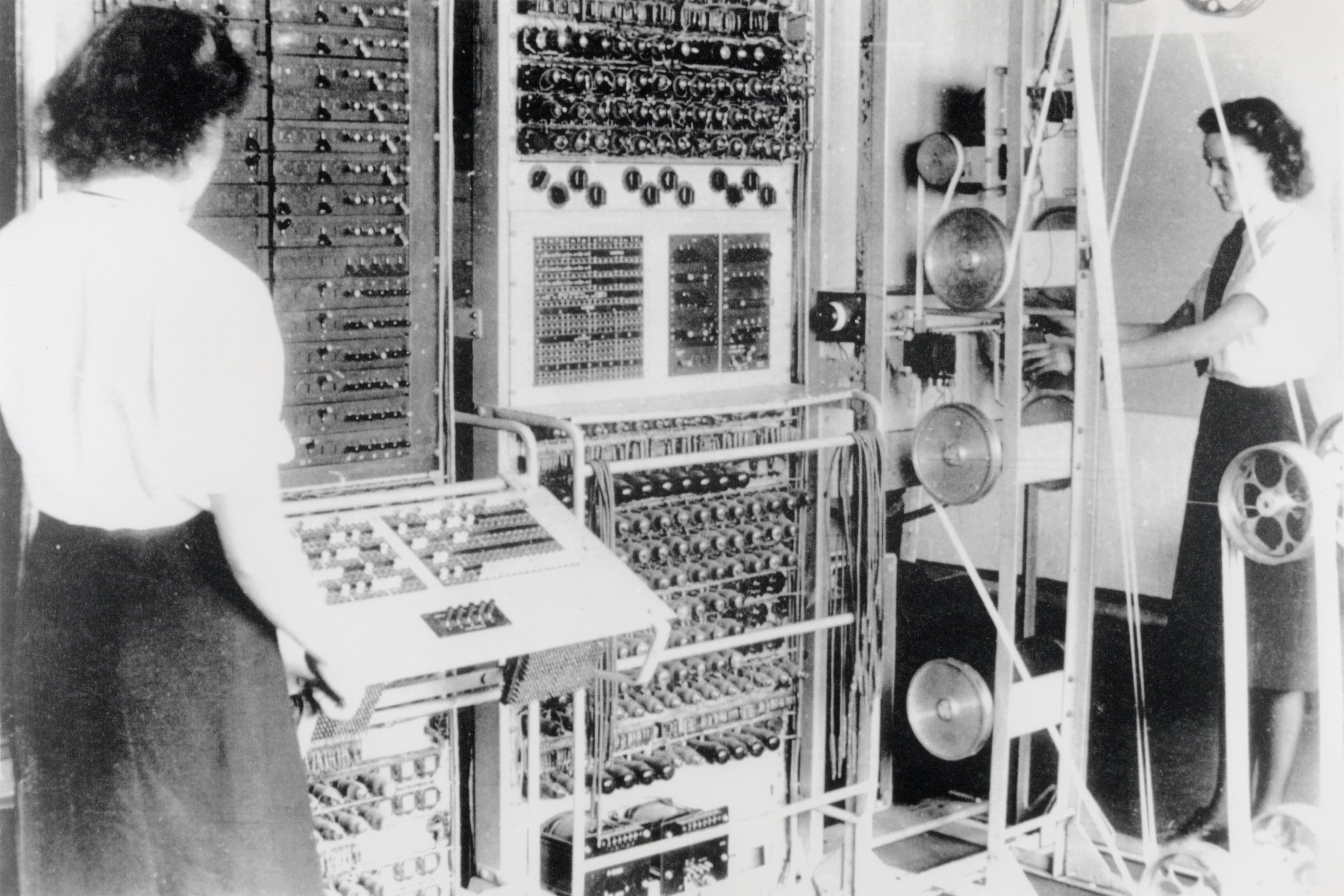 |
Colossus Computer
Colossus was a set of computers developed by British cryptanalysis, codebreakers in the years 1943–1945 to help in the cryptanalysis of the Lorenz cipher. Colossus used vacuum tube, thermionic valves (vacuum tubes) to perform Boolean algebra (logic), Boolean and counting operations. Colossus is thus regarded as the world's first computer programming, programmable, electronics, electronic, digital electronics, digital computer, although it was programmed by switches and plugs and not by a stored-program computer, stored program. Colossus was designed by General Post Office (GPO) research telephone engineer Tommy Flowers based on plans developed by mathematician Max Newman at the Government Code and Cypher School at Bletchley Park. Alan Turing's use of probability in cryptanalysis (see Banburismus) contributed to its design. It has sometimes been erroneously stated that Turing designed Colossus to aid the cryptanalysis of the Enigma. (Turing's machine that helped decode Enigma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
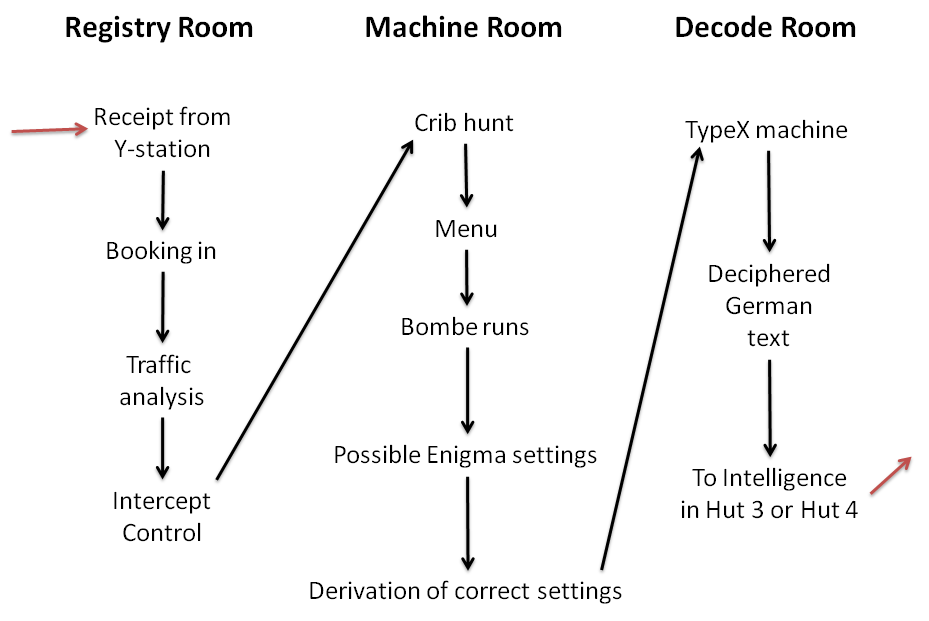 |
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the Second World War. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers most importantly the German Enigma machine, Enigma and Lorenz cipher, Lorenz ciphers. The GC&CS team of codebreakers included John Tiltman, Dilwyn Knox, Alan Turing, Harry Golombek, Gordon Welchman, Conel Hugh O'Donel Alexander, Hugh Alexander, Donald Michie, W. T. Tutte, Bill Tutte and Stuart Milner-Barry. The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus computer, Colossus, the world's first programmable digital electronic computer. Codebreaking operations at Bletchley Park ended in 1946 and al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Software Piracy
Online piracy or software piracy is the practice of downloading and distributing copyrighted works digitally without permission, such as music, movies or software. History Nathan Fisk traces the origins of modern online piracy back to similar problems posed by the advent of the printing press. Quoting from legal standards in '' MGM Studios, Inc. v. Grokster, Ltd.'', he notes that there have historically been a number of technologies which have had a "dual effect" of facilitating legitimate sharing of information, but which also facilitate the ease with which copyright can be violated. He likens online piracy to issues faced in the early 20th century by stationers in England, who tried and failed to prevent the large scale printing and distribution of illicit sheet music. WordStar was so widely pirated that many books on how to use the software appeared, their authors knowing that they were selling documentation for illicit copies. Starting in the 1980s, the availability of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |