|
Guard (information Security)
In information security, a guard is a device or system for allowing computers on otherwise separate networks to communicate, subject to configured constraints. In many respects a guard is like a firewall and guards may have similar functionality to a gateway. Whereas a firewall is designed to limit traffic to certain services, a guard aims to control the information exchange that the network communication is supporting at the business level. Further, unlike a firewall a guard provides assurance that it is effective in providing this control even under attack and failure conditions. A guard will typically sit between a protected network and an external network, and ensure the protected network is safe from threats posed by the external network and from leaks of sensitive information to the external network. A guard is usually dual-homed, though guards can connect more than two networks, and acts as a full application layer proxy, engaging in separate communications on each inte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized or inappropriate access to data or the unlawful use, Data breach, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g., electronic or physical, tangible (e.g., Document, paperwork), or intangible (e.g., knowledge). Information security's primary focus is the balanced protection of data confidentiality, data integrity, integrity, and data availability, availability (also known as the 'CIA' triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process. To stand ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DMZ (computing)
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network or screened subnet) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted, usually larger, network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an external network node can access only what is exposed in the DMZ, while the rest of the organization's network is protected behind a Firewall (computing), firewall. The DMZ functions as a small, isolated network positioned between the Internet and the private network. This is not to be confused with a #DMZ_host, DMZ host, a feature present in some home routers that frequently differs greatly from an ordinary DMZ. The name is from the term ''demilitarized zone'', an area between states in which military operations are not permitted. Rationale The DMZ is seen as not belonging to either netwo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unidirectional Network
A unidirectional network (also referred to as a unidirectional gateway or data diode) is a network appliance or device that allows data to travel in only one direction. Data diodes can be found most commonly in high security environments, such as defense, where they serve as connections between two or more networks of differing security classifications. Given the rise of industrial Internet of things, IoT and digitization, this technology can now be found at the industrial control level for such facilities as nuclear power plants, power generation and safety critical systems like railway networks. After years of development, data diodes have evolved from being only a network appliance or device allowing raw data to travel only in one direction, used in guaranteeing information security or protection of critical digital systems, such as industrial control systems, from inbound cyber attacks, to combinations of hardware and software running in proxy computers in the source and destin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
QinetiQ
QinetiQ ( as in '' kinetic'') is a British defence technology company headquartered in Farnborough, Hampshire. It operates primarily in the defence, security and critical national infrastructure markets and run testing and evaluation capabilities for air, land, sea and target systems. As a private entity, QinetiQ was created in April 2001; prior to this its assets had been part of Defence Evaluation and Research Agency (DERA), a now-defunct British government organisation. While a large portion of DERA's assets, sites, and employees were transferred to QinetiQ, other elements were incorporated into Defence Science and Technology Laboratory (DSTL), which remains in government ownership. Some former DERA locations have thus become key sites for QinetiQ. These include Farnborough, Hampshire; MoD Boscombe Down, Wiltshire; and Malvern, Worcestershire. In February 2006, QinetiQ was floated on the London Stock Exchange. The privatisation process was subject to an inquiry by the U ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
BAE Systems
BAE Systems plc is a British Multinational corporation, multinational Aerospace industry, aerospace, military technology, military and information security company, based in London. It is the largest manufacturer in Britain as of 2017. It is the largest defence contractor in Europe and the seventh largest in the world based on applicable 2021 revenues. Its largest operations are in the United Kingdom and in the United States, where its BAE Systems Inc. subsidiary is one of the six largest suppliers to the United States Department of Defense, US Department of Defense. Its next biggest markets are Saudi Arabia, then Australia; other major markets include Canada, Japan, India, Turkey, Qatar, Oman and Sweden. The company was formed on 30 November 1999 by the British pound sterling, £7.7 billion purchase of and merger of Marconi Electronic Systems (MES), the defence electronics and naval shipbuilding subsidiary of the General Electric Company plc (GEC), with British Aerospace ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Raytheon
Raytheon is a business unit of RTX Corporation and is a major U.S. defense contractor and industrial corporation with manufacturing concentrations in weapons and military and commercial electronics. Founded in 1922, it merged in 2020 with United Technologies Corporation to form Raytheon Technologies, which changed its name to RTX Corporation in July 2023. Raytheon was established in 1922, reincorporated in 1928, and adopted the Raytheon Company name in 1959. More than 90% of Raytheon's revenues were obtained from military contracts and, as of 2012, it was the fifth-largest military contractor in the world. , it was the third-largest defense contractor in the United States by defense revenue. It was the world's largest producer of guided missiles, and was involved in corporate and special-mission aircraft until early 2007. In 2018, the company had around 67,000 employees worldwide and annual revenues of about US$25.35 billion. Over the years, Raytheon shifted its headquarters ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rockwell Collins
Rockwell Collins, Inc. was a multinational corporation headquartered in Cedar Rapids, Iowa, providing avionics and information technology systems and services to government agencies and aircraft manufacturers. It was formed when the Collins Radio Company, facing financial difficulties, was purchased by Rockwell International in 1973. In 2001, the avionics division of Rockwell International was spun off to form the current Rockwell Collins, Inc., retaining its name. It was acquired by United Technologies Corporation on November 27, 2018, and since then operates as part of Collins Aerospace, a subsidiary of the RTX Corporation (formerly Raytheon Technologies). History Arthur A. Collins founded Collins Radio Company in 1933 in Cedar Rapids, Iowa. It designed and produced both shortwave radio equipment and equipment for the AM radio broadcast industry. Collins supplied the military, the scientific community, and the larger AM radio stations with equipment. Collins provided the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Radiant Mercury
Radiant Mercury is a cross-domain solution (CDS) software application developed by Lockheed Martin primarily in use by the US Navy. As a CDS, it is designed to allow communications between higher-level classified networks and lower-level, unclassified networks. See also *Guard (information security) In information security, a guard is a device or system for allowing computers on otherwise separate networks to communicate, subject to configured constraints. In many respects a guard is like a firewall and guards may have similar functionality t ... References Computer security software Lockheed Martin {{Security-software-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Solaris 10
Oracle Solaris is a proprietary Unix operating system offered by Oracle for SPARC and x86-64 based workstations and servers. Originally developed by Sun Microsystems as Solaris, it superseded the company's earlier SunOS in 1993 and became known for its scalability, especially on SPARC systems, and for originating many innovative features such as DTrace, ZFS and Time Slider. After the Sun acquisition by Oracle in 2010, it was renamed Oracle Solaris. Solaris was registered as compliant with the Single UNIX Specification until April 29, 2019. Historically, Solaris was developed as proprietary software. In June 2005, Sun Microsystems released most of the codebase under the CDDL license, and founded the OpenSolaris open-source project. Sun aimed to build a developer and user community with OpenSolaris; after the Oracle acquisition in 2010, the OpenSolaris distribution was discontinued and later Oracle discontinued providing public updates to the source code of the Solaris kernel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nexor
Nexor Limited is a privately held company based in Nottingham, providing products and services to safeguard government, defence and critical national infrastructure computer systems. It was originally known as X-Tel Services Limited. History Nexor Limited was founded in 1989 as X-Tel Services Limited out of the University of Nottingham and UCL, following research into X.400 and X.500 systems for the ISODE project. In 1992 Stephen Kingan joined the business as CEO. In 1993 X-Tel Services Limited was renamed Nexor Limited. In 1996 3i invested in the business to launch Nexor Inc. In 2004 Kingan and Nigel Fasey acquired the business. In 2008 Colin Robbins was appointed to the board as CTO. In 2012 Kingan acquired 100% ownership of Nexor. In October 2013, the company moved its headquarters from Nottingham Science Park to the NG2 Business Park. Nexor customers include NATO, European Defence Agency, UK MoD, US DOD, Canadian DND, Foreign and Commonwealth Office and Met Office ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
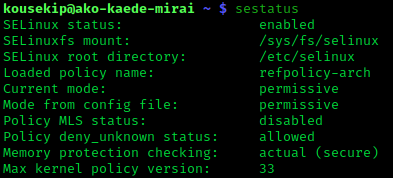
Security-Enhanced Linux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allows t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |