|
Dual Factor Authentication
Multi-factor authentication (MFA; two-factor authentication, or 2FA) is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more distinct types of evidence (or factors) to an authentication mechanism. MFA protects personal data—which may include personal identification or financial assets—from being accessed by an unauthorized third party that may have been able to discover, for example, a single password. Usage of MFA has increased in recent years. Security issues which can cause the bypass of MFA are fatigue attacks, phishing and SIM swapping. Accounts with MFA enabled are significantly less likely to be compromised. Authentication factors Authentication takes place when someone tries to log into a computer resource (such as a computer network, device, or application). The resource requires the user to supply the identity by which the user is known to the resource, along wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
U2F Hardware Authentication Security Keys (Yubico Yubikey 4 And Feitian MultiPass FIDO) (42286852310)
U, or u, is the twenty-first letter (alphabet), letter and the fifth vowel letter of the Latin alphabet, used in the modern English alphabet and the alphabets of other western European languages and others worldwide. Its English alphabet#Letter names, name in English is ''u'' (pronounced ), plural ''ues''. Name In English, the name of the letter is the "long U" sound, pronounced . In most other languages, its name matches the letter's pronunciation in open syllables. History U derives from the Semitic waw (letter), waw, as does F, and later, Y, W, and V. Its oldest ancestor goes back to Egyptian hieroglyphs, and is probably from a hieroglyph of a mace or fowl, representing the sound or the sound . This was borrowed to Phoenician, where it represented the sound , and seldom the vowel . In Greek language, Greek, two letters were adapted from the Phoenician waw. The letter was adapted, but split in two, with Digamma or wau being adapted to represent , and the second on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bank Card
A bank card is typically a plastic card issued by a bank to its clients that performs one or more of a number of services that relate to giving the client access to a bank account. Physically, a bank card will usually have the client's name, the issuer's name, and a unique card number printed on it. It will have a magnetic strip on the back enabling various machines to read and access information. Depending on the issuing bank and the preferences of the client, this may allow the card to be used as an ATM card, enabling transactions at automated teller machines; or as a debit card, linked to the client's bank account and able to be used for making purchases at the point of sale with a bank card using a payment terminal. Later, in 2010s, smart card technology was adopted for bank card. The first bank cards were ATM cards issued by Barclays in London, in 1967, and by Chemical Bank in Long Island, New York (state), New York, in 1969. In 1972, Lloyds Bank issued the first bank card ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
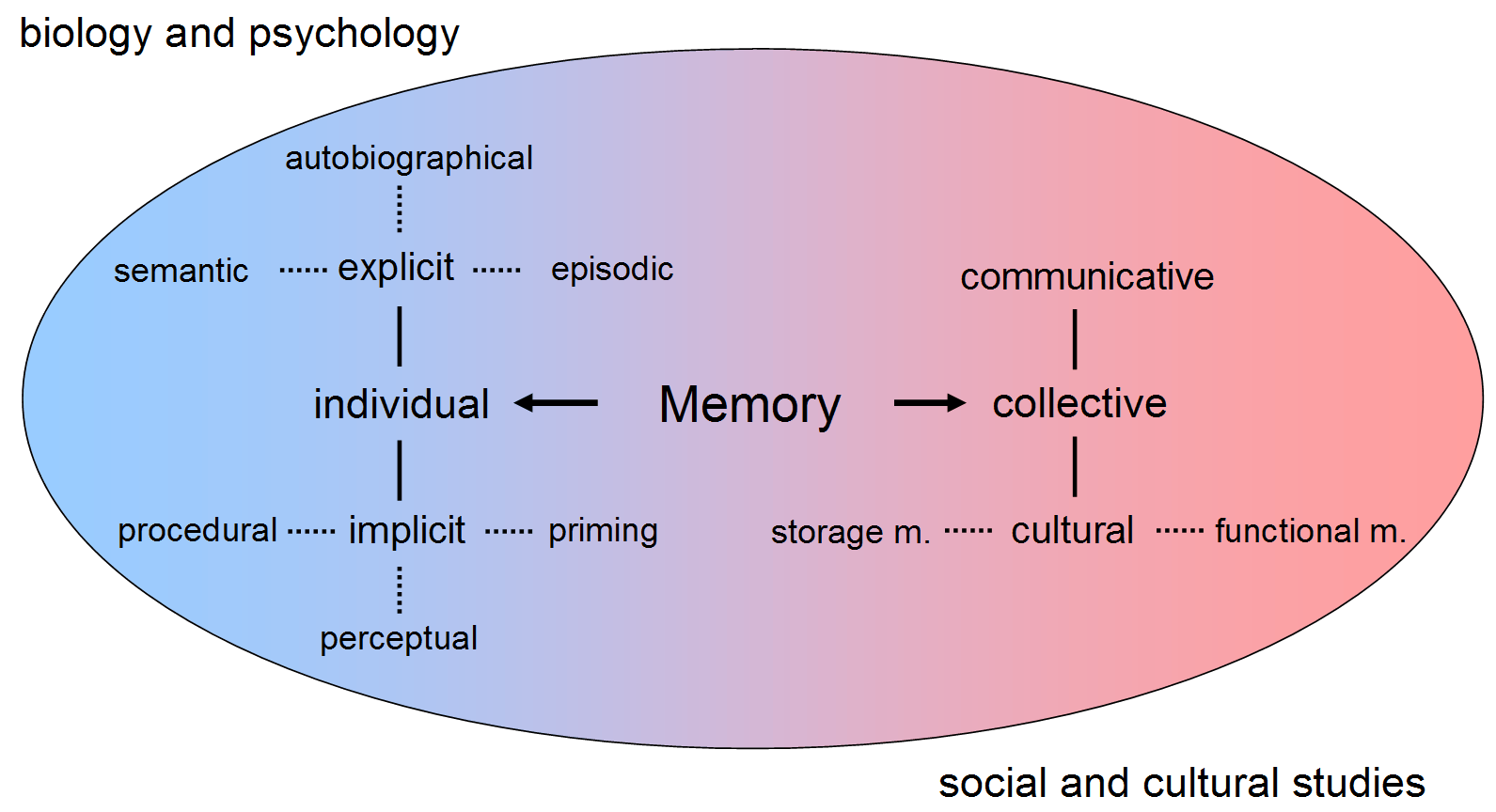
Memory
Memory is the faculty of the mind by which data or information is encoded, stored, and retrieved when needed. It is the retention of information over time for the purpose of influencing future action. If past events could not be remembered, it would be impossible for language, relationships, or personal identity to develop. Memory loss is usually described as forgetfulness or amnesia. Memory is often understood as an informational processing system with explicit and implicit functioning that is made up of a sensory processor, short-term (or working) memory, and long-term memory. This can be related to the neuron. The sensory processor allows information from the outside world to be sensed in the form of chemical and physical stimuli and attended to various levels of focus and intent. Working memory serves as an encoding and retrieval processor. Information in the form of stimuli is encoded in accordance with explicit or implicit functions by the working memory p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Passphrase
A passphrase is a sequence of words or other text used to control access to a computer system, program or data. It is similar to a password in usage, but a passphrase is generally longer for added security. Passphrases are often used to control both access to, and the operation of, Cryptography, cryptographic programs and systems, especially those that derive an encryption key from a passphrase. The origin of the term is by analogy with ''password''. The modern concept of passphrases is believed to have been invented by Sigmund N. Porter in 1982. Security Source: Considering that the information entropy, entropy of written English is less than 1.1 bits per character, passphrases can be relatively weak. NIST has estimated that the 23-character passphrase "IamtheCapitanofthePina4" contains a 45-bit strength. The equation employed here is: : 4 bits (1st character) + 14 bits (characters 2–8) + 18 bits (characters 9–20) + 3 bits (characters 21–23) + 6 bits (bonus f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time-based One-time Password
Time-based one-time password (TOTP) is a computer algorithm that generates a one-time password (OTP) using the current time as a source of uniqueness. As an extension of the HMAC-based one-time password (HOTP) algorithm, it has been adopted as Internet Engineering Task Force (IETF) standard . TOTP is a cornerstone of the Initiative for Open Authentication (OATH) and is used in a number of two-factor authentication (2FA) systems. History Through the collaboration of several OATH members, a TOTP draft was developed in order to create an industry-backed standard. It complements the event-based one-time standard HOTP, and it offers end user organizations and enterprises more choice in selecting technologies that best fit their application requirements and security guidelines. In 2008, OATH submitted a draft version of the specification to the IETF. This version incorporates all the feedback and commentary that the authors received from the technical community based on the prior v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wired (magazine)
''Wired'' is a bi-monthly American magazine that focuses on how emerging technologies affect culture, the economy, and politics. It is published in both print and Online magazine, online editions by Condé Nast. The magazine has been in publication since its launch in January 1993. Its editorial office is based in San Francisco, California, with its business headquarters located in New York City. ''Wired'' quickly became recognized as the voice of the emerging digital economy and culture and a pace setter in print design and web design. From 1998 until 2006, the magazine and its website, ''Wired.com'', experienced separate ownership before being fully consolidated under Condé Nast in 2006. It has won multiple National Magazine Awards and has been credited with shaping discourse around the digital revolution. The magazine also coined the term Crowdsourcing, ''crowdsourcing'', as well as its annual tradition of handing out Vaporware Awards. ''Wired'' has launched several in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Smartphone
A smartphone is a mobile phone with advanced computing capabilities. It typically has a touchscreen interface, allowing users to access a wide range of applications and services, such as web browsing, email, and social media, as well as multimedia playback and Streaming media, streaming. Smartphones have built-in cameras, GPS navigation, and support for various communication methods, including voice calls, text messaging, and internet-based messaging apps. Smartphones are distinguished from older-design feature phones by their more advanced hardware capabilities and extensive mobile operating systems, access to the internet, business applications, Mobile payment, mobile payments, and multimedia functionality, including music, video, mobile gaming, gaming, Internet radio, radio, and Mobile television, television. Smartphones typically feature MOSFET, metal–oxide–semiconductor (MOS) integrated circuit (IC) chips, various sensors, and support for multiple wireless communicati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authenticator
An authenticator is a means used to confirm a user's identity, that is, to perform digital authentication. A person authenticates to a computer system or application by demonstrating that he or she has possession and control of an authenticator. In the simplest case, the authenticator is a common password. Using the terminology of the NIST Digital Identity Guidelines, the party to be authenticated is called the ''claimant'' while the party verifying the identity of the claimant is called the ''verifier''. When the claimant successfully demonstrates possession and control of one or more authenticators to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity. Classification Authenticators may be characterized in terms of secrets, factors, and physical forms. Authenticator secrets Every authenticator is associated with at least one secret that the claimant uses to demonstrate possession and control of the authenticator. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-time Password
A one-time password (OTP), also known as a one-time PIN, one-time passcode, one-time authorization code (OTAC) or dynamic password, is a password that is valid for only one login session or transaction, on a computer system or other digital device. OTPs avoid several shortcomings that are associated with traditional (static) password-based authentication; a number of implementations also incorporate two-factor authentication by ensuring that the one-time password requires access to ''something a person has'' (such as a small keyring fob device with the OTP calculator built into it, or a smartcard or specific cellphone) as well as ''something a person knows'' (such as a PIN). OTP generation algorithms typically make use of pseudorandomness or randomness to generate a shared key or seed, and cryptographic hash functions, which can be used to derive a value but are hard to reverse and therefore difficult for an attacker to obtain the data that was used for the hash. This is necessa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Automated Teller Machine
An automated teller machine (ATM) is an electronic telecommunications device that enables customers of financial institutions to perform financial transactions, such as cash withdrawals, deposits, funds transfers, balance inquiries or account information inquiries, at any time and without the need for direct interaction with bank staff. ATMs are known by a variety of other names, including automatic teller machines (ATMs) in the United States (sometimes RAS syndrome, redundantly as "ATM machine"). In Canada, the term automated banking machine (ABM) is also used, although ATM is also very commonly used in Canada, with many Canadian organizations using ATM rather than ABM. In British English, the terms cashpoint, cash machine and hole in the wall are also used. ATMs that are Independent ATM deployer, not operated by a financial institution are known as "White-label ABMs, white-label" ATMs. Using an ATM, customers can access their bank deposit or credit accounts in order to make ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keystroke Dynamics
Keystroke dynamics, keystroke biometrics, typing dynamics, or typing biometrics refer to the collection of biometric information generated by key-press-related events that occur when a user types on a keyboard. Use of patterns in key operation to identify operators predates modern computing, and has been proposed as an authentication alternative to passwords and PIN numbers. Science The behavioral biometric of keystroke dynamics uses the manner and rhythm in which an individual types characters on a keyboard or keypad. The user's keystroke rhythms are measured to develop a unique biometric template of the user's typing pattern for future authentication. Keystrokes are separated into static and dynamic typing, which are used to help distinguish between authorized and unauthorized users. Vibration information may be used to create a pattern for future use in both identification and authentication tasks. History During the late nineteenth century, telegram operators began ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fingerprint
A fingerprint is an impression left by the friction ridges of a human finger. The recovery of partial fingerprints from a crime scene is an important method of forensic science. Moisture and grease on a finger result in fingerprints on surfaces such as glass or metal. Deliberate impressions of entire fingerprints can be obtained by ink or other substances transferred from the peaks of friction ridges on the skin to a smooth surface such as paper. Fingerprint records normally contain impressions from the pad on the last joint of fingers and thumbs, though fingerprint cards also typically record portions of lower joint areas of the fingers. Human fingerprints are detailed, unique, difficult to alter, and durable over the life of an individual, making them suitable as long-term markers of human identity. They may be employed by police or other authorities to identify individuals who wish to conceal their identity, or to identify people who are incapacitated or dead and thus unab ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |