|
Domain Separation (cryptography)
In cryptography, domain separation is a construct used to implement multiple different functions using only one underlying template in an efficient way. The domain separation can be defined as partitioning of the domain of a function to assign separate subdomains to different applications of the same function. For example, cryptographic protocols typically rely on random oracles (ROs, functions that return a value fully determined by their input yet otherwise random). The security proofs for these protocols are based on the assumption that the random oracle is unique to the protocol: if two protocols share the same RO, the assumptions of the proof are not met anymore. Since creating a new cryptographic primitive from scratch each time an RO is needed is impractical, multiple ROs (say, RO1 and RO2) are produced by prepending unique domain separation tags (DSTs, also known as ''domain separators'') to the input of a base oracle RO: :RO1(x) := RO("RO1" , , x) :RO2(x) := RO("RO2" , , ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Strong Typing
In computer programming, one of the many ways that programming languages are colloquially classified is whether the language's type system makes it strongly typed or weakly typed (loosely typed). However, there is no precise technical definition of what the terms mean and different authors disagree about the implied meaning of the terms and the relative rankings of the "strength" of the type systems of mainstream programming languages. For this reason, writers who wish to write unambiguously about type systems often eschew the terms "strong typing" and "weak typing" in favor of specific expressions such as "type safety". Generally, a strongly typed language has stricter typing rules at compile time, which implies that errors are more likely to happen during compilation. Most of these rules affect variable assignment, function return values, procedure arguments and function calling. Dynamically typed languages (where type checking happens at run time) can also be strongly typed. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
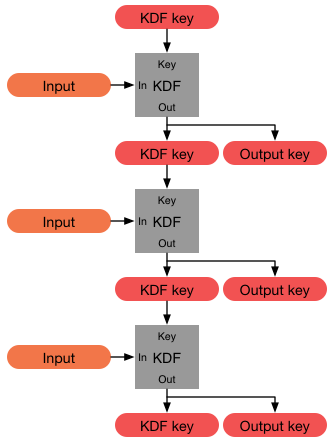
Key Derivation Function
In cryptography, a key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation. History The first deliberately slow (key stretching) password-based key derivation function was called "crypt" (or "crypt(3)" after its man page), and was invented by Robert Morris in 1978. It would encrypt a constant (zero), using the first 8 characters of the user's password as the key, by performing 25 iterations of a modified DES encryption algorithm (in which a 12-b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keying Material
Keying may refer to: * Keying (electrical connector), used by electrical connectors to prevent mating in incorrect orientation * Keying (graphics), a technique for compositing two full frame images together * Keying (official) (1787–1858), a Manchu statesman during the Qing dynasty ** ''Keying'' (ship), a Chinese junk which sailed to the U.S. and Britain in 1847–1848, named after the official * Keying (telecommunications), a form of modulation where the modulating signal takes one of two or more values at all times * Keying, vandalism of a painted surface by scratching it with a key * Keying, in the sociology of Erving Goffman Erving Goffman (11 June 1922 – 19 November 1982) was a Canadian-born American sociologist, social psychologist, and writer, considered by some "the most influential American sociologist of the twentieth century". In 2007, '' The Time ..., is an action or utterance that signals the meaning of interaction to participants. Introduced in ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Message Authentication Code
In cryptography, a message authentication code (MAC), sometimes known as an authentication tag, is a short piece of information used for authentication, authenticating and Data integrity, integrity-checking a message. In other words, it is used to confirm that the message came from the stated sender (its authenticity) and has not been changed (its integrity). The MAC value allows verifiers (who also possess a secret key) to detect any changes to the message content. Terminology The term message integrity code (MIC) is frequently substituted for the term ''MAC'', especially in communications to distinguish it from the use of the latter as ''media access control address'' (''MAC address''). However, some authors use MIC to refer to a message digest, which aims only to uniquely but opaquely identify a single message. RFC 4949 recommends avoiding the term ''message integrity code'' (MIC), and instead using ''checksum'', ''error detection code'', ''hash function, hash'', ''keyed hash'' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Symmetric Cipher
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption (also known as asymmetric-key encryption). However, symmetric-key encryption algorithms are usually better for bulk encryption. With exception of the one-time pad they have a smaller key size, which means less storage space and faster transmission. Due to this, asymmetric-key encryption is often used to exchange the secret key for symmetric-key encryption. Types Symmetric-key encryption can use either stream ciphers or block ciphers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHAKE128
SHA-3 (Secure Hash Algorithm 3) is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. Although part of the same series of standards, SHA-3 is internally different from the MD5-like structure of SHA-1 and SHA-2. SHA-3 is a subset of the broader cryptographic primitive family Keccak ( or ), designed by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche, building upon RadioGatún. Keccak's authors have proposed additional uses for the function, not (yet) standardized by NIST, including a stream cipher, an authenticated encryption system, a "tree" hashing scheme for faster hashing on certain architectures, and AEAD ciphers Keyak and Ketje. Keccak is based on a novel approach called sponge construction. Sponge construction is based on a wide random function or random permutation, and allows inputting ("absorbing" in sponge terminology) any amount of data, and outputting ("squeezing") any amount of data, w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHA-3
SHA-3 (Secure Hash Algorithm 3) is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. Although part of the same series of standards, SHA-3 is internally different from the MD5-like structure of SHA-1 and SHA-2. SHA-3 is a subset of the broader cryptographic primitive family Keccak ( or ), designed by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche, building upon RadioGatún. Keccak's authors have proposed additional uses for the function, not (yet) standardized by NIST, including a stream cipher, an authenticated encryption system, a "tree" hashing scheme for faster hashing on certain architectures, and AEAD ciphers Keyak and Ketje. Keccak is based on a novel approach called sponge construction. Sponge construction is based on a wide random function or random permutation, and allows inputting ("absorbing" in sponge terminology) any amount of data, and outputting ("squeezing") any amount o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Block Cipher
In cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called ''blocks''. Block ciphers are the elementary building blocks of many cryptographic protocols. They are ubiquitous in the storage and exchange of data, where such data is secured and authenticated via encryption. A block cipher uses blocks as an unvarying transformation. Even a secure block cipher is suitable for the encryption of only a single block of data at a time, using a fixed key. A multitude of modes of operation have been designed to allow their repeated use in a secure way to achieve the security goals of confidentiality and authenticity. However, block ciphers may also feature as building blocks in other cryptographic protocols, such as universal hash functions and pseudorandom number generators. Definition A block cipher consists of two paired algorithms, one for encryption, , and the other for decryption, . Both algorithms accept two inputs: an input ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Of A Function
In mathematics, the domain of a function is the Set (mathematics), set of inputs accepted by the Function (mathematics), function. It is sometimes denoted by \operatorname(f) or \operatornamef, where is the function. In layman's terms, the domain of a function can generally be thought of as "what x can be". More precisely, given a function f\colon X\to Y, the domain of is . In modern mathematical language, the domain is part of the definition of a function rather than a property of it. In the special case that and are both sets of real numbers, the function can be graphed in the Cartesian coordinate system. In this case, the domain is represented on the -axis of the graph, as the projection of the graph of the function onto the -axis. For a function f\colon X\to Y, the set is called the ''codomain'': the set to which all outputs must belong. The set of specific outputs the function assigns to elements of is called its ''Range of a function, range'' or ''Image (mathematic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |