|
Dm-crypt
dm-crypt is a transparent block device encryption subsystem in Linux kernel versions 2.6 and later and in DragonFly BSD. It is part of the device mapper (dm) infrastructure, and uses cryptographic routines from the kernel's Crypto API. Unlike its predecessor cryptoloop, dm-crypt was designed to support advanced modes of operation, such as XTS, LRW and ESSIV, in order to avoid watermarking attacks. In addition to that, dm-crypt addresses some reliability problems of cryptoloop. dm-crypt is implemented as a device mapper target and may be stacked on top of other device mapper transformations. It can thus encrypt whole disks (including removable media), partitions, software RAID volumes, logical volumes, as well as files. It appears as a block device, which can be used to back file systems, swap or as an LVM physical volume. Some Linux distributions support the use of dm-crypt on the root file system. These distributions use initrd to prompt the user to enter a pass ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Encryption
Disk encryption is a technology which protects information by converting it into code that cannot be deciphered easily by unauthorized people or processes. Disk encryption uses disk encryption software or disk encryption hardware, hardware to encryption, encrypt every bit of data that goes on a disk storage, disk or disk volume (computing), volume. It is used to prevent unauthorized access to data storage. The expression ''full disk encryption (FDE)'' (or ''whole disk encryption'') signifies that everything on the disk is encrypted, but the master boot record (MBR), or similar area of a bootable disk, with code that starts the operating system loading sequence, is not encrypted. Some hardware-based full disk encryption systems can truly encrypt an entire boot disk, including the MBR. Transparent encryption Transparent encryption, also known as real-time encryption and on-the-fly encryption (OTFE), is a method used by some disk encryption software. "Transparent" refers to the fact ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ARM Architecture
ARM (stylised in lowercase as arm, formerly an acronym for Advanced RISC Machines and originally Acorn RISC Machine) is a family of reduced instruction set computer, RISC instruction set architectures (ISAs) for central processing unit, computer processors. Arm Holdings develops the ISAs and licenses them to other companies, who build the physical devices that use the instruction set. It also designs and licenses semiconductor intellectual property core, cores that implement these ISAs. Due to their low costs, low power consumption, and low heat generation, ARM processors are useful for light, portable, battery-powered devices, including smartphones, laptops, and tablet computers, as well as embedded systems. However, ARM processors are also used for desktop computer, desktops and server (computing), servers, including Fugaku (supercomputer), Fugaku, the world's fastest supercomputer from 2020 to 2022. With over 230 billion ARM chips produced, , ARM is the most widely used ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
X86-64
x86-64 (also known as x64, x86_64, AMD64, and Intel 64) is a 64-bit extension of the x86 instruction set architecture, instruction set. It was announced in 1999 and first available in the AMD Opteron family in 2003. It introduces two new operating modes: 64-bit mode and compatibility mode, along with a new four-level paging mechanism. In 64-bit mode, x86-64 supports significantly larger amounts of virtual memory and physical memory compared to its 32-bit computing, 32-bit predecessors, allowing programs to utilize more memory for data storage. The architecture expands the number of general-purpose registers from 8 to 16, all fully general-purpose, and extends their width to 64 bits. Floating-point arithmetic is supported through mandatory SSE2 instructions in 64-bit mode. While the older x87 FPU and MMX registers are still available, they are generally superseded by a set of sixteen 128-bit Processor register, vector registers (XMM registers). Each of these vector registers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unix-like
A Unix-like (sometimes referred to as UN*X, *nix or *NIX) operating system is one that behaves in a manner similar to a Unix system, although not necessarily conforming to or being certified to any version of the Single UNIX Specification. A Unix-like Application software, application is one that behaves like the corresponding List of POSIX commands, Unix command or Unix shell, shell. Although there are general Unix philosophy, philosophies for Unix design, there is no technical standard defining the term, and opinions can differ about the degree to which a particular operating system or application is Unix-like. Some well-known examples of Unix-like operating systems include Linux, FreeBSD and OpenBSD. These systems are often used on servers as well as on personal computers and other devices. Many popular applications, such as the Apache HTTP Server, Apache web server and the Bash (Unix shell), Bash shell, are also designed to be used on Unix-like systems. Definition The Open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C (programming Language)
C (''pronounced'' '' – like the letter c'') is a general-purpose programming language. It was created in the 1970s by Dennis Ritchie and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of the targeted Central processing unit, CPUs. It has found lasting use in operating systems code (especially in Kernel (operating system), kernels), device drivers, and protocol stacks, but its use in application software has been decreasing. C is commonly used on computer architectures that range from the largest supercomputers to the smallest microcontrollers and embedded systems. A successor to the programming language B (programming language), B, C was originally developed at Bell Labs by Ritchie between 1972 and 1973 to construct utilities running on Unix. It was applied to re-implementing the kernel of the Unix operating system. During the 1980s, C gradually gained popularity. It has become one of the most widely used programming langu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Front And Back Ends
In software development, frontend refers to the presentation layer that users interact with, while backend involves the data management and processing behind the scenes, and full-stack development refers to mastering both. In the client–server model, the client is usually considered the frontend, handling user-facing tasks, and the server is the backend, managing data and logic. Some presentation tasks may also be performed by the server. Introduction In software architecture, there may be many layers between the hardware and end user. The ''front'' is an abstraction, simplifying the underlying component by providing a user-friendly interface, while the ''back'' usually handles data storage and business logic. Examples E-commerce Website: The ''frontend'' is the user interface (e.g., product pages, search bar), while the ''backend'' processes payments and updates inventory. Banking App: The ''frontend'' displays account balances, while the ''backend'' handles secure tra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
User Space
A modern computer operating system usually uses virtual memory to provide separate address spaces or regions of a single address space, called user space and kernel space. This separation primarily provides memory protection and hardware protection from malicious or errant software behaviour. Kernel space is strictly reserved for running a privileged operating system kernel, kernel extensions, and most device drivers. In contrast, user space is the memory area where application software and some drivers execute, typically with one address space per process. Overview The term user space (or userland) refers to all code that runs outside the operating system's kernel. User space usually refers to the various programs and libraries that the operating system uses to interact with the kernel: software that performs input/output, manipulates file system objects, application software, etc. Each user space process usually runs in its own virtual memory space, and, unless explici ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Block Device
In Unix-like operating systems, a device file, device node, or special file is an interface to a device driver that appears in a file system as if it were an ordinary file. There are also special files in DOS, OS/2, and Windows. These special files allow an application program to interact with a device by using its device driver via standard input/output system calls. Using standard system calls simplifies many programming tasks, and leads to consistent user-space I/O mechanisms regardless of device features and functions. Overview Device files usually provide simple interfaces to standard devices (such as printers and serial ports), but can also be used to access specific unique resources on those devices, such as disk partitions. Additionally, device files are useful for accessing system resources that have no connection with any actual device, such as data sinks and random number generators. There are two general kinds of device files in Unix-like operating systems, k ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
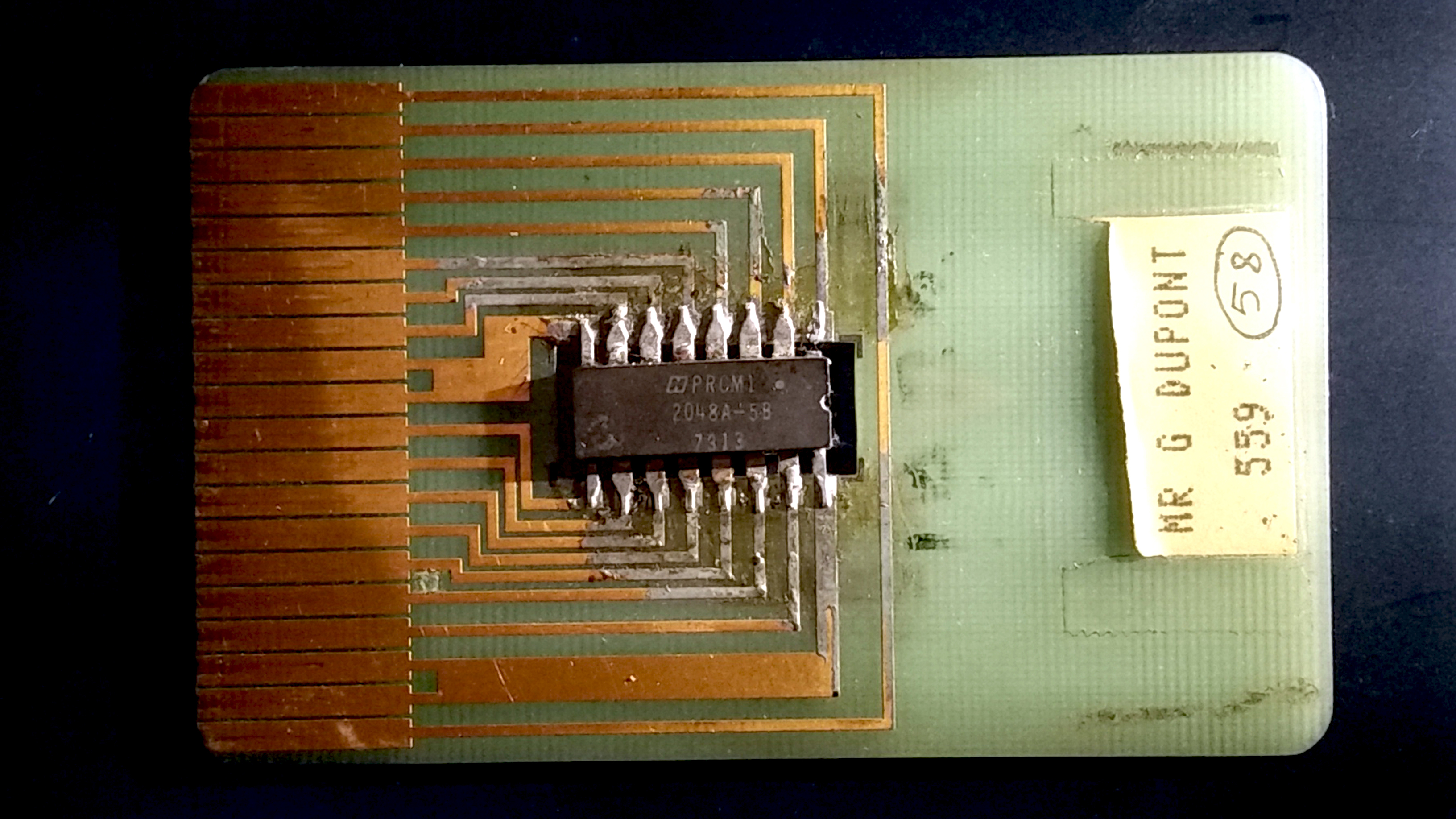
Smart Card
A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an Embedded system, embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are Contactless smart card, contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card (UICC) for mobile phones, installed as pluggable SIM card or embedded eSIM, is also a type of smart card. , 10.5billion smart card IC chips are manufactured annually ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Initrd
In Linux systems, initrd (''initial ramdisk'') is a scheme for loading a temporary root file system into memory, to be used as part of the Linux startup process. initrd and initramfs (from INITial RAM File System) refer to two different methods of achieving this. Both are commonly used to make preparations before the real root file system can be mounted. Rationale Many Linux distributions ship a single, generic Linux kernel image one which the distribution's developers create specifically to boot on a wide variety of hardware. The device drivers for this generic kernel image are included as loadable kernel modules because statically compiling many drivers into one kernel causes the kernel image to be much larger, perhaps too large to boot on computers with limited memory, or in some cases to cause boot-time crashes or other problems due to probing for nonexistent or conflicting hardware. This static-compiled kernel approach also leaves modules in kernel memory which are no long ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux Distribution
A Linux distribution, often abbreviated as distro, is an operating system that includes the Linux kernel for its kernel functionality. Although the name does not imply product distribution per se, a distro—if distributed on its own—is often obtained via a website intended specifically for the purpose. Distros have been designed for a wide variety of systems ranging from personal computers (for example, Linux Mint) to servers (for example, Red Hat Enterprise Linux) and from embedded devices (for example, OpenWrt) to supercomputers (for example, Rocks Cluster Distribution). A distro typically includes many components in addition to the Linux kernel. Commonly, it includes a package manager, an init system (such as systemd, OpenRC, or runit), GNU tools and libraries, documentation, IP network configuration utilities, the getty TTY setup program, and many more. To provide a desktop experience (most commonly the Mesa userspace graphics drivers) a display server (the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |