|
Distributed Hash Table
A distributed hash table (DHT) is a Distributed computing, distributed system that provides a lookup service similar to a hash table. Key–value pairs are stored in a DHT, and any participating node (networking), node can efficiently retrieve the value associated with a given key. The main advantage of a DHT is that nodes can be added or removed with minimum work around re-distributing keys. ''Keys'' are unique identifiers which map to particular ''values'', which in turn can be anything from addresses, to Electronic document, documents, to arbitrary Data (computing), data. Responsibility for maintaining the mapping from keys to values is distributed among the nodes, in such a way that a change in the set of participants causes a minimal amount of disruption. This allows a DHT to scale (computing), scale to extremely large numbers of nodes and to handle continual node arrivals, departures, and failures. DHTs form an infrastructure that can be used to build more complex services, su ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Distributed Computing
Distributed computing is a field of computer science that studies distributed systems, defined as computer systems whose inter-communicating components are located on different networked computers. The components of a distributed system communicate and coordinate their actions by passing messages to one another in order to achieve a common goal. Three significant challenges of distributed systems are: maintaining concurrency of components, overcoming the lack of a global clock, and managing the independent failure of components. When a component of one system fails, the entire system does not fail. Examples of distributed systems vary from SOA-based systems to microservices to massively multiplayer online games to peer-to-peer applications. Distributed systems cost significantly more than monolithic architectures, primarily due to increased needs for additional hardware, servers, gateways, firewalls, new subnets, proxies, and so on. Also, distributed systems are prone to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Storm Botnet
The Storm botnet or Storm Worm botnet (also known as Dorf botnet and Ecard malware) was a remotely controlled network of "zombie" computers (or "botnet") that had been linked by the Storm Worm, a Trojan horse spread through e-mail spam. At its height in September 2007, the Storm botnet was running on anywhere from 1 million to 50 million computer systems, and accounted for 8% of all malware on Microsoft Windows computers. It was first identified around January 2007, having been distributed by email with subjects such as "230 dead as storm batters Europe," giving it its well-known name. The botnet began to decline in late 2007, and by mid-2008 had been reduced to infecting about 85,000 computers, far less than it had infected a year earlier. As of December 2012, the original creators of Storm have not been found. The Storm botnet has displayed defensive behaviors that indicated that its controllers were actively protecting the botnet against attempts at tracking and disabling ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
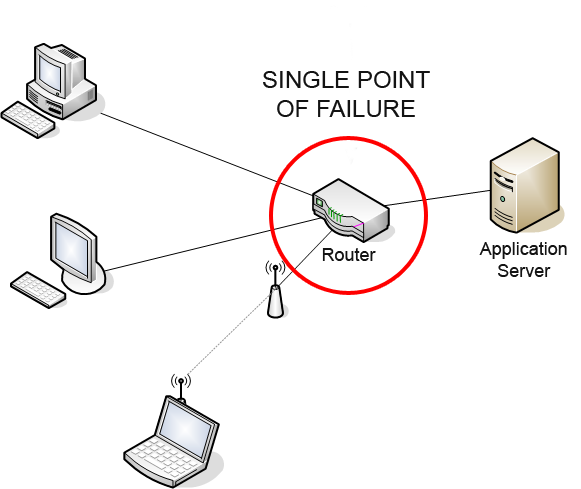 |
Single Point Of Failure
A single point of failure (SPOF) is a part of a system that would Cascading failure, stop the entire system from working if it were to fail. The term single point of failure implies that there is not a backup or redundant option that would enable the system to continue to function without it. SPOFs are undesirable in any system with a goal of high availability or Reliability engineering, reliability, be it a business practice, software application, or other industrial system. If there is a SPOF present in a system, it produces a potential interruption to the system that is substantially more disruptive than an error would elsewhere in the system. Overview Systems can be made robust by adding Redundancy (engineering), redundancy in all potential SPOFs. Redundancy can be achieved at various levels. The assessment of a potential SPOF involves identifying the critical components of a complex system that would provoke a total systems failure in case of wikt:malfunction, malfunction. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Query Flooding
{{short description, Search method on a peer-to-peer network Query flooding is a method to search for a resource on a peer-to-peer network. It is simple and scales very poorly and thus is rarely used. Early versions of the Gnutella protocol operated by query flooding; newer versions use more efficient search algorithms. Operation A peer-to-peer network generally consists of a large number of nodes each connected to a small subset of the nodes and not all nodes in the network. If a node wants to find a resource on the network, which may be on a node it does not know about, it could simply broadcast its search query to its immediate neighbours. If the neighbours do not have the resource, it then asks its neighbours to forward the query to their neighbours in turn. This is repeated until the resource is found or all the nodes have been contacted, or perhaps a network-imposed hop limit is reached. Query flooding is simple to implement and is practical for small networks with few re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Hard Disk
A hard disk drive (HDD), hard disk, hard drive, or fixed disk is an electro-mechanical data storage device that stores and retrieves digital data using magnetic storage with one or more rigid rapidly rotating hard disk drive platter, platters coated with magnetic material. The platters are paired with disk read-and-write head, magnetic heads, usually arranged on a moving actuator arm, which read and write data to the platter surfaces. Data is accessed in a random-access manner, meaning that individual Block (data storage), blocks of data can be stored and retrieved in any order. HDDs are a type of non-volatile storage, retaining stored data when powered off. Modern HDDs are typically in the form of a small disk enclosure, rectangular box. Hard disk drives were introduced by IBM in 1956, and were the dominant secondary storage device for History of general-purpose CPUs, general-purpose computers beginning in the early 1960s. HDDs maintained this position into the modern er ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Bandwidth (computing)
In computing, bandwidth is the maximum rate of data transfer across a given path. Bandwidth may be characterized as network bandwidth, data bandwidth, or digital bandwidth. This definition of ''bandwidth'' is in contrast to the field of signal processing, wireless communications, modem data transmission, digital communications, and electronics, in which ''bandwidth'' is used to refer to the signal bandwidth measured in hertz, meaning the frequency range between lowest and highest attainable frequency while meeting a well-defined impairment level in signal power. The actual bit rate that can be achieved depends not only on the signal bandwidth but also on the noise on the channel. Network capacity The term ''bandwidth'' sometimes defines the net bit rate ''peak bit rate'', ''information rate'', or physical layer ''useful bit rate'', channel capacity, or the maximum throughput of a logical or physical communication path in a digital communication system. For example, bandwi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Napster
Napster was an American proprietary peer-to-peer (P2P) file sharing application primarily associated with digital audio file distribution. Founded by Shawn Fanning and Sean Parker, the platform originally launched on June 1, 1999. Audio shared on the service was typically encoded in the MP3 format. As the software became popular, the company encountered legal difficulties over copyright infringement. Napster ceased operations in 2001 after losing multiple lawsuits and filed for bankruptcy in June 2002. The P2P model employed by Napster involved a centralized database that indexed a complete list of all songs being shared from connected clients. While effective, the service could not function without the central database, which was hosted by Napster and eventually forced to shut down. Following Napster's demise, alternative decentralized methods of P2P file-sharing emerged, including LimeWire, Gnutella, Freenet, FastTrack, I2P, and BitTorrent. Napster's assets were event ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
BitTorrent
BitTorrent is a Protocol (computing), communication protocol for peer-to-peer file sharing (P2P), which enables users to distribute data and electronic files over the Internet in a Decentralised system, decentralized manner. The protocol is developed and maintained by Rainberry, Inc., and was first released in 2001. To send or receive files, users use a Comparison of BitTorrent clients, BitTorrent client on their Internet-connected computer, which are available for a variety of computing platforms and Comparison of BitTorrent clients#Operating system support, operating systems, including BitTorrent (software), an official client. BitTorrent trackers provide a list of files available for transfer and allow the client to find peer users, known as "seeds", who may transfer the files. BitTorrent downloading is considered to be faster than HTTP ("direct downloading") and File Transfer Protocol, FTP due to the lack of a central server that could limit bandwidth. BitTorrent is one o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Gnutella
Gnutella is a peer-to-peer network protocol. Founded in 2000, it was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model. In June 2005, Gnutella's population was 1.81 million computers increasing to over three million nodes by January 2006.On the Long-term Evolution of the Two-Tier Gnutella Overlay . Rasti, Stutzbach, Rejaie, 2006. See Figure 2a. In late 2007, it was the most popular file-sharing network on the Internet with an estimated market share of more than 40%. History The first client (also called Gnutella) from which the network got its name was developed by Justin Frankel and Tom Pepper of Nullsoft in early 2000, soon after the company's acquisition by AOL. On March 14, the program was ...[...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network, forming a peer-to-peer network of Node (networking), nodes. In addition, a personal area network (PAN) is also in nature a type of Decentralized computing, decentralized peer-to-peer network typically between two devices. Peers make a portion of their resources, such as processing power, disk storage, or network bandwidth, directly available to other network participants, without the need for central coordination by servers or stable hosts. Peers are both suppliers and consumers of resources, in contrast to the traditional client–server model in which the consumption and supply of resources are divided. While P2P systems had previously been used in many application domains, the architecture was popularized by the Internet file sharing system Napster, originally released in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
InterPlanetary File System
The InterPlanetary File System (IPFS) is a protocol, hypermedia and file sharing peer-to-peer network for sharing data using a distributed hash table to store provider information. By using content addressing, IPFS uniquely identifies each file in a global namespace that connects IPFS hosts, creating a distributed system of file storage and sharing. IPFS allows users to host and receive content in a manner similar to BitTorrent. As opposed to a centrally located server, IPFS is built around a decentralized system of user-operators who hold a portion of the overall data. Any user in the network can serve a file by its content address, and other peers in the network can find and request that content from any node who has it using a distributed hash table (DHT). In contrast to traditional location-based protocols like HTTP and HTTPS, IPFS uses content-based addressing to provide a decentralized alternative for distributing the World Wide Web. Design The InterPlanetary File ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |