 |
Surveillance Databases
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing, or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. Increasingly, governments may also obtain consumer data through the purchase of online information, effectively expanding surveillance capabilities through commercially available digital records. It can also include simple technical methods, such as human intelligence gathering and postal interception. Surveillance is used by citizens, for instance for protecting their neighborhoods. It is widely used by governments for intelligence gathering, including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Democracies
Democracy (from , ''dēmos'' 'people' and ''kratos'' 'rule') is a form of government in which political power is vested in the people or the population of a state. Under a minimalist definition of democracy, rulers are elected through competitive Election, elections while more expansive or maximalist definitions link democracy to guarantees of civil liberties and human rights in addition to competitive elections. In a direct democracy, the people have the direct authority to Deliberation, deliberate and decide legislation. In a representative democracy, the people choose governing officials through elections to do so. The definition of "the people" and the ways authority is shared among them or delegated by them have changed over time and at varying rates in different countries. Features of democracy oftentimes include freedom of assembly, freedom of association, association, personal property, freedom of religion and freedom of speech, speech, citizenship, consent of the governe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
ECHELON
Echelon may refer to: * A level formation ** A level or rank in an organization, profession, or society ** A military sub-subunit smaller than a company but larger than a platoon ** Echelon formation, a step-like arrangement of units * ECHELON, a worldwide electronic intelligence-gathering operation, within the UKUSA Agreement, mainly for industry espionage Places * Echelon, New Jersey Sciences * En echelon veins, geological feature * Row echelon form, in mathematics, a kind of matrix Arts * Echelon (band), a four-piece band hailing from Essex, England * The Echelon, fanbase of the band Thirty Seconds to Mars Thirty Seconds to Mars (commonly stylized as 30 Seconds to Mars) is an American Rock music, rock band from Los Angeles, California, formed in 1998. The band consists of brothers Jared Leto (lead vocals, guitar, bass, keyboards) and Shannon Let ..., named after a song on their debut album. * ''Echelons'' (album) Games * ''Echelon'' (1987 video game), a space f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Narus (company)
Narus Inc. was a Software industry, software company and Independent software vendor, vendor of big data analytics for cybersecurity. History In 1997, Ori Cohen, Vice President of Business and Technology Development for VDONet, founded Narus with Stas Khirman in Israel. Presently, they are employed with Deutsche Telekom AG and are not members of Narus' executive team. In 2010, Narus became a subsidiary of Boeing, located in Sunnyvale, California, Sunnyvale, California. In 2015, Narus was sold to NortonLifeLock, Symantec. Management In 2004, Narus employed former Deputy Director of the National Security Agency, William P. Crowell, William Crowell as a director. Narus software Narus software primarily captures various computer network traffic in Real-time computing, real-time and analyzes results. Before 9/11 Narus built carrier-grade tools to analyze IP network traffic for billing purposes, to prevent what Narus called "revenue leakage". Post-9/11 Narus added more "semantic mon ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Carnivore (FBI)
Carnivore, later renamed DCS1000, was a system implemented by the Federal Bureau of Investigation (FBI) that was designed to monitor email and electronic communications. It used a customizable packet sniffer that could monitor all of a target user's Internet traffic. Carnivore was implemented in October 1997. By 2005 it had been replaced with improved commercial software. Development Carnivore grew out of an earlier FBI project called "Omnivore", which itself replaced an older undisclosed (at the time) surveillance tool migrated at the US Navy by FBI Director of Integrity and Compliance, Patrick W. Kelley. In September 2000, the FBI's Data Intercept Technology Unit (DITU) in Quantico, Virginia, launched a project to migrate Omnivore from Sun's Solaris operating system to a Windows NT platform. This was done to facilitate the miniaturization of the system and support a wider range of personal computer (CPU) equipment. The migration project was called "Triple Phoenix" and the re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
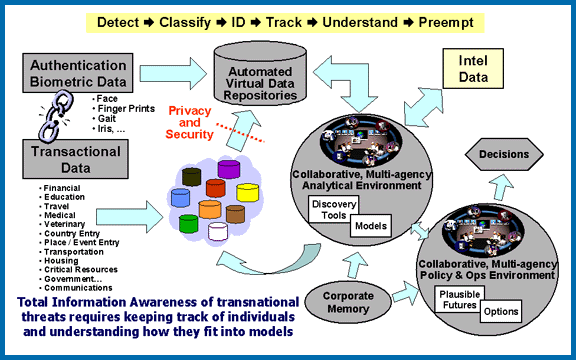 |
Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric warfare, asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Aware ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Email
Electronic mail (usually shortened to email; alternatively hyphenated e-mail) is a method of transmitting and receiving Digital media, digital messages using electronics, electronic devices over a computer network. It was conceived in the late–20th century as the digital version of, or counterpart to, mail (hence ''wikt:e-#Etymology 2, e- + mail''). Email is a ubiquitous and very widely used communication medium; in current use, an email address is often treated as a basic and necessary part of many processes in business, commerce, government, education, entertainment, and other spheres of daily life in most countries. Email operates across computer networks, primarily the Internet access, Internet, and also local area networks. Today's email systems are based on a store-and-forward model. Email Server (computing), servers accept, forward, deliver, and store messages. Neither the users nor their computers are required to be online simultaneously; they need to connect, ty ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Internet
The Internet (or internet) is the Global network, global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a internetworking, network of networks that consists of Private network, private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, Wireless network, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the interlinked hypertext documents and Web application, applications of the World Wide Web (WWW), email, electronic mail, internet telephony, streaming media and file sharing. The origins of the Internet date back to research that enabled the time-sharing of computer resources, the development of packet switching in the 1960s and the design of computer networks for data communication. The set of rules (communication protocols) to enable i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Traffic Analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted. In general, the greater the number of messages observed, the greater information be inferred. Traffic analysis can be performed in the context of military intelligence, counter-intelligence, or pattern-of-life analysis, and is also a concern in computer security. Traffic analysis tasks may be supported by dedicated computer software programs. Advanced traffic analysis techniques which may include various forms of social network analysis. Traffic analysis has historically been a vital technique in cryptanalysis, especially when the attempted crack depends on successfully seeding a known-plaintext attack, which often requires an inspired guess based on how specific the operational context might likely influence what an adversary communicates, which may be sufficient to establish a short cr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Data Mining
Data mining is the process of extracting and finding patterns in massive data sets involving methods at the intersection of machine learning, statistics, and database systems. Data mining is an interdisciplinary subfield of computer science and statistics with an overall goal of extracting information (with intelligent methods) from a data set and transforming the information into a comprehensible structure for further use. Data mining is the analysis step of the " knowledge discovery in databases" process, or KDD. Aside from the raw analysis step, it also involves database and data management aspects, data pre-processing, model and inference considerations, interestingness metrics, complexity considerations, post-processing of discovered structures, visualization, and online updating. The term "data mining" is a misnomer because the goal is the extraction of patterns and knowledge from large amounts of data, not the extraction (''mining'') of data itself. It also is a buzzwo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |