|
Connected-component Analysis
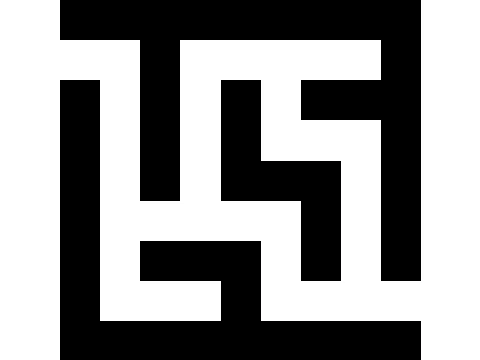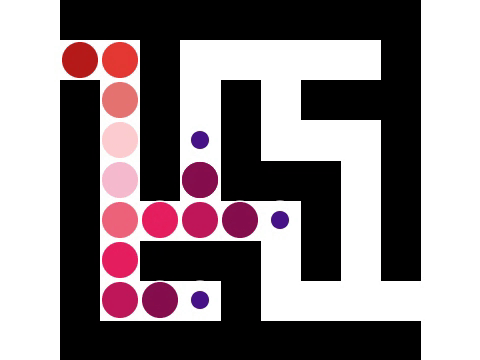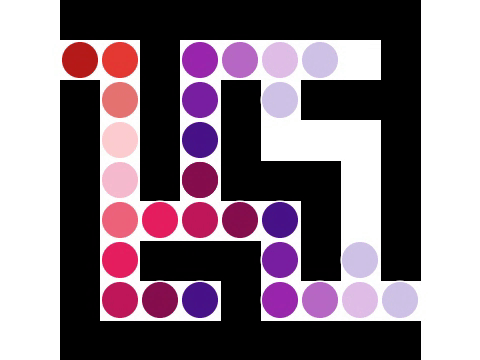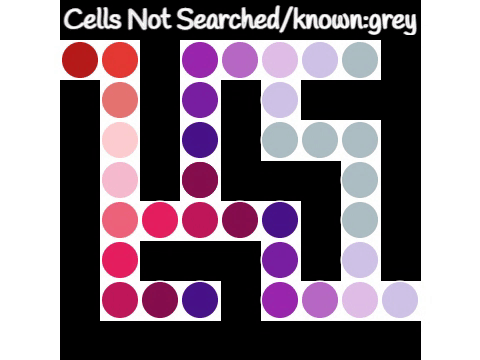
Connected-component labeling (CCL), connected-component analysis (CCA), blob extraction, region labeling, blob discovery, or region extraction is an algorithmic application of graph theory, where subsets of connected component (graph theory), connected components are uniquely labeled based on a given heuristic. Connected-component labeling is not to be confused with segmentation (image processing), segmentation. Connected-component labeling is used in computer vision to detect connected regions in binary image, binary digital images, although color images and data with higher dimensionality can also be processed. When integrated into an image recognition system or human-computer interaction interface, connected component labeling can operate on a variety of information. Blob extraction is generally performed on the resulting binary image from a thresholding step, but it can be applicable to gray-scale and color images as well. Blobs may be counted, filtered, and tracked. Blob ext ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graph Theory
In mathematics and computer science, graph theory is the study of ''graph (discrete mathematics), graphs'', which are mathematical structures used to model pairwise relations between objects. A graph in this context is made up of ''Vertex (graph theory), vertices'' (also called ''nodes'' or ''points'') which are connected by ''Glossary of graph theory terms#edge, edges'' (also called ''arcs'', ''links'' or ''lines''). A distinction is made between undirected graphs, where edges link two vertices symmetrically, and directed graphs, where edges link two vertices asymmetrically. Graphs are one of the principal objects of study in discrete mathematics. Definitions Definitions in graph theory vary. The following are some of the more basic ways of defining graphs and related mathematical structures. Graph In one restricted but very common sense of the term, a graph is an ordered pair G=(V,E) comprising: * V, a Set (mathematics), set of vertices (also called nodes or points); * ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
8-connected Neighborhood
In image processing, pixel connectivity is the way in which pixels in 2-dimensional (or hypervoxels in n-dimensional) images relate to their neighbors. Formulation In order to specify a set of connectivities, the dimension and the width of the neighborhood , must be specified. The dimension of a neighborhood is valid for any dimension n\geq1. A common width is 3, which means along each dimension, the central cell will be adjacent to 1 cell on either side for all dimensions. Let M_N^n represent a N-dimensional hypercubic neighborhood with size on each dimension of n=2k+1, k\in\mathbb Let \vec represent a discrete vector in the first orthant from the center structuring element to a point on the boundary of M_N^n. This implies that each element q_i \in \ ,\forall i \in \ and that at least one component q_i = k Let S_N^d represent a N-dimensional hypersphere with radius of d=\left \Vert \vec \right \Vert. Define the amount of elements on the hypersphere S_N^d within the nei ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Introduction To Algorithms
''Introduction to Algorithms'' is a book on computer programming by Thomas H. Cormen, Charles E. Leiserson, Ron Rivest, Ronald L. Rivest, and Clifford Stein. The book is described by its publisher as "the leading algorithms text in universities worldwide as well as the standard reference for professionals". It is commonly Citation, cited as a reference for algorithms in published Academic publishing#Scholarly paper, papers, with over 10,000 citations documented on CiteSeerX, and over 70,000 citations on Google Scholar as of 2024. The book sold half a million copies during its first 20 years, and surpassed a million copies sold in 2022. Its fame has led to the common use of the abbreviation "CLRS" (Cormen, Leiserson, Rivest, Stein), or, in the first edition, "CLR" (Cormen, Leiserson, Rivest). In the preface, the authors write about how the book was written to be comprehensive and useful in both teaching and professional environments. Each chapter focuses on an algorithm, and discus ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disjoint-set Data Structure
In computer science, a disjoint-set data structure, also called a union–find data structure or merge–find set, is a data structure that stores a collection of Disjoint sets, disjoint (non-overlapping) Set (mathematics), sets. Equivalently, it stores a partition of a set into disjoint subsets. It provides operations for adding new sets, merging sets (replacing them with their Union (set theory), union), and finding a representative member of a set. The last operation makes it possible to determine efficiently whether any two elements belong to the same set or to different sets. While there are several ways of implementing disjoint-set data structures, in practice they are often identified with a particular implementation known as a disjoint-set forest. This specialized type of Forest (graph theory), forest performs union and find operations in near-constant Amortized analysis, amortized time. For a sequence of addition, union, or find operations on a disjoint-set forest with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Corruption
Data corruption refers to errors in computer data that occur during writing, reading, storage, transmission, or processing, which introduce unintended changes to the original data. Computer, transmission, and storage systems use a number of measures to provide end-to-end data integrity, or lack of errors. In general, when data corruption occurs, a Computer file, file containing that data will produce unexpected results when accessed by the system or the related application. Results could range from a minor loss of data to a system crash. For example, if a Document file format, document file is corrupted, when a person tries to open that file with a document editor they may get an error message, thus the file might not be opened or might open with some of the data corrupted (or in some cases, completely corrupted, leaving the document unintelligible). The adjacent image is a corrupted image file in which most of the information has been lost. Some types of malware may intentional ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
In Situ
is a Latin phrase meaning 'in place' or 'on site', derived from ' ('in') and ' ( ablative of ''situs'', ). The term typically refers to the examination or occurrence of a process within its original context, without relocation. The term is used across many disciplines to denote methods, observations, or interventions carried out in their natural or intended environment. By contrast, ' methods involve the removal or displacement of materials, specimens, or processes for study, preservation, or modification in a controlled setting, often at the cost of contextual integrity. The earliest known use of ''in situ'' in the English language dates back to the mid-17th century. In scientific literature, its usage increased from the late 19th century onward, initially in medicine and engineering. The natural sciences typically use methods to study phenomena in their original context. In geology, field analysis of soil composition and rock formations provides direct insights into Earth' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hoshen–Kopelman Algorithm
The Hoshen–Kopelman algorithm is a simple and efficient algorithm for labeling clusters on a grid, where the grid is a regular network of cells, with the cells being either occupied or unoccupied. This algorithm is based on a well-known union-finding algorithm. The algorithm was originally described by Joseph Hoshen and Raoul Kopelman in their 1976 paper "Percolation and Cluster Distribution. I. Cluster Multiple Labeling Technique and Critical Concentration Algorithm". Percolation theory Percolation theory is the study of the behavior and statistics of clusters on lattices. Suppose we have a large square lattice where each cell can be occupied with the probability p and can be empty with the probability 1 – ''p''. Each group of neighboring occupied cells forms a cluster. Neighbors are defined as cells having a common side but not those sharing only a corner i.e. we consider the 4-connected neighborhood that is top, bottom, left and right. Each occupied cell is ind ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pseudocode
In computer science, pseudocode is a description of the steps in an algorithm using a mix of conventions of programming languages (like assignment operator, conditional operator, loop) with informal, usually self-explanatory, notation of actions and conditions. Although pseudocode shares features with regular programming languages, it is intended for human reading rather than machine control. Pseudocode typically omits details that are essential for machine implementation of the algorithm, meaning that pseudocode can only be verified by hand. The programming language is augmented with natural language description details, where convenient, or with compact mathematical notation. The reasons for using pseudocode are that it is easier for people to understand than conventional programming language code and that it is an efficient and environment-independent description of the key principles of an algorithm. It is commonly used in textbooks and scientific publications to document ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
LIFO (computing)
In computer science, a stack is an abstract data type that serves as a collection of elements with two main operations: * Push, which adds an element to the collection, and * Pop, which removes the most recently added element. Additionally, a peek operation can, without modifying the stack, return the value of the last element added. The name ''stack'' is an analogy to a set of physical items stacked one atop another, such as a stack of plates. The order in which an element added to or removed from a stack is described as last in, first out, referred to by the acronym LIFO. As with a stack of physical objects, this structure makes it easy to take an item off the top of the stack, but accessing a datum deeper in the stack may require removing multiple other items first. Considered a sequential collection, a stack has one end which is the only position at which the push and pop operations may occur, the ''top'' of the stack, and is fixed at the other end, the ''bottom''. A s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Breadth-first Search
Breadth-first search (BFS) is an algorithm for searching a tree data structure for a node that satisfies a given property. It starts at the tree root and explores all nodes at the present depth prior to moving on to the nodes at the next depth level. Extra memory, usually a queue, is needed to keep track of the child nodes that were encountered but not yet explored. For example, in a chess endgame, a chess engine may build the game tree from the current position by applying all possible moves and use breadth-first search to find a win position for White. Implicit trees (such as game trees or other problem-solving trees) may be of infinite size; breadth-first search is guaranteed to find a solution node if one exists. In contrast, (plain) depth-first search (DFS), which explores the node branch as far as possible before backtracking and expanding other nodes, may get lost in an infinite branch and never make it to the solution node. Iterative deepening depth-first search ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Depth-first Search
Depth-first search (DFS) is an algorithm for traversing or searching tree or graph data structures. The algorithm starts at the root node (selecting some arbitrary node as the root node in the case of a graph) and explores as far as possible along each branch before backtracking. Extra memory, usually a stack, is needed to keep track of the nodes discovered so far along a specified branch which helps in backtracking of the graph. A version of depth-first search was investigated in the 19th century by French mathematician Charles Pierre Trémaux as a strategy for solving mazes. Properties The time and space analysis of DFS differs according to its application area. In theoretical computer science, DFS is typically used to traverse an entire graph, and takes time where , V, is the number of vertices and , E, the number of edges. This is linear in the size of the graph. In these applications it also uses space O(, V, ) in the worst case to store the stack of vertices on t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |