|
Clock (cryptology)
In cryptography, the clock was a method devised by Polish mathematician-cryptologist Jerzy Różycki, at the Polish General Staff's Cipher Bureau, to facilitate decrypting German Enigma ciphers. The method determined the rightmost rotor in the German Enigma by exploiting the different turnover positions. For the Poles, learning the rightmost rotor reduced the rotor-order search space by a factor of 3 (the number of rotors). The British improved the method, and it allowed them to use their limited number of bombes more effectively (the British confronted 5 to 8 rotors). Method This method sometimes made it possible to determine which of the Enigma machine's rotors was at the far right, that is, in the position where the rotor always revolved at every depression of a key. The clock method was developed by Jerzy Różycki during 1933–1935. Marian Rejewski's grill method could determine the right-hand rotor, but that involved trying each possible rotor permutation (there w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
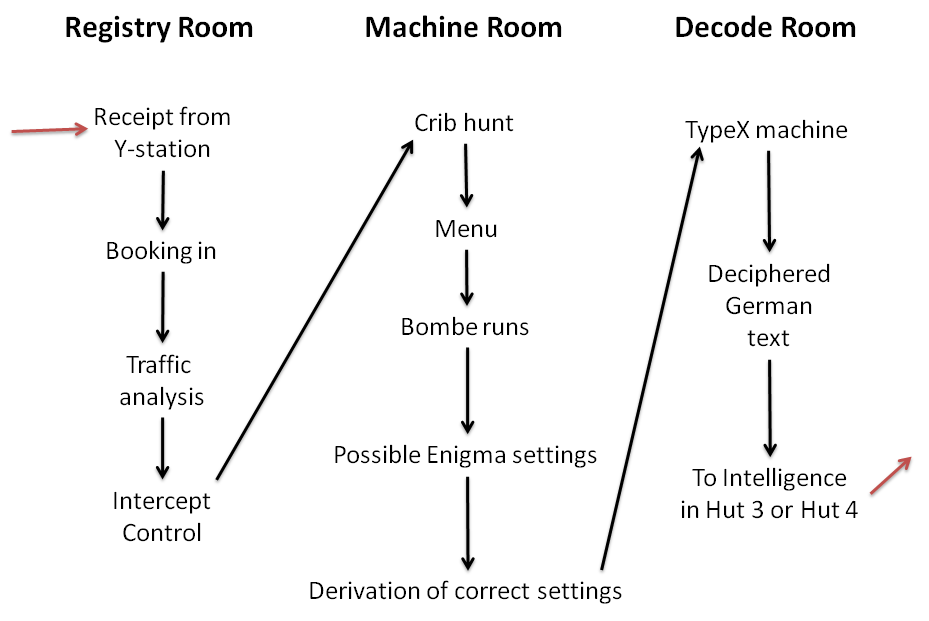
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the Second World War. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers most importantly the German Enigma machine, Enigma and Lorenz cipher, Lorenz ciphers. The GC&CS team of codebreakers included John Tiltman, Dilwyn Knox, Alan Turing, Harry Golombek, Gordon Welchman, Conel Hugh O'Donel Alexander, Hugh Alexander, Donald Michie, W. T. Tutte, Bill Tutte and Stuart Milner-Barry. The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus computer, Colossus, the world's first programmable digital electronic computer. Codebreaking operations at Bletchley Park ended in 1946 and al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptanalytic Devices
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the Mathematics, mathematically adva ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Warsaw
Warsaw, officially the Capital City of Warsaw, is the capital and List of cities and towns in Poland, largest city of Poland. The metropolis stands on the Vistula, River Vistula in east-central Poland. Its population is officially estimated at 1.86 million residents within a Warsaw metropolitan area, greater metropolitan area of 3.27 million residents, which makes Warsaw the List of cities in the European Union by population within city limits, 6th most-populous city in the European Union. The city area measures and comprises List of districts and neighbourhoods of Warsaw, 18 districts, while the metropolitan area covers . Warsaw is classified as an Globalization and World Cities Research Network#Alpha 2, alpha global city, a major political, economic and cultural hub, and the country's seat of government. It is also the capital of the Masovian Voivodeship. Warsaw traces its origins to a small fishing town in Masovia. The city rose to prominence in the late 16th cent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
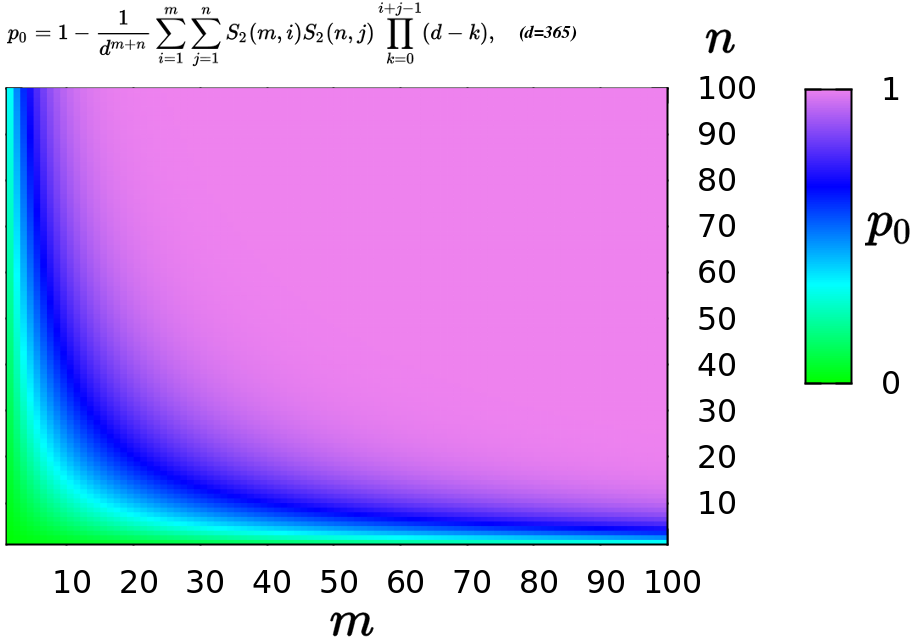
Birthday Problem
In probability theory, the birthday problem asks for the probability that, in a set of randomly chosen people, at least two will share the same birthday. The birthday paradox is the counterintuitive fact that only 23 people are needed for that probability to exceed 50%. The birthday paradox is a veridical paradox: it seems wrong at first glance but is, in fact, true. While it may seem surprising that only 23 individuals are required to reach a 50% probability of a shared birthday, this result is made more intuitive by considering that the birthday comparisons will be made between every possible pair of individuals. With 23 individuals, there are = 253 pairs to consider. Real-world applications for the birthday problem include a cryptographic attack called the birthday attack, which uses this probabilistic model to reduce the complexity of finding a Collision attack, collision for a hash function, as well as calculating the approximate risk of a hash collision existi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Letter Frequency
Letter frequency is the number of times letters of the alphabet appear on average in written language. Letter frequency analysis dates back to the Arab mathematician Al-Kindi (c. AD 801–873), who formally developed the method to break ciphers. Letter frequency analysis gained importance in Europe with the development of movable type in AD 1450, wherein one must estimate the amount of type required for each letterform. Linguists use letter frequency analysis as a rudimentary technique for language identification, where it is particularly effective as an indication of whether an unknown writing system is alphabetic, syllabic, or ideographic. The use of letter frequencies and frequency analysis plays a fundamental role in cryptograms and several word puzzle games, including hangman, ''Scrabble'', '' Wordle'' and the television game show '' Wheel of Fortune''. One of the earliest descriptions in classical literature of applying the knowledge of English letter frequency to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Discrete Uniform Distribution
In probability theory and statistics, the discrete uniform distribution is a symmetric probability distribution wherein each of some finite whole number ''n'' of outcome values are equally likely to be observed. Thus every one of the ''n'' outcome values has equal probability 1/''n''. Intuitively, a discrete uniform distribution is "a known, finite number of outcomes all equally likely to happen." A simple example of the discrete uniform distribution comes from throwing a fair six-sided die. The possible values are 1, 2, 3, 4, 5, 6, and each time the die is thrown the probability of each given value is 1/6. If two dice were thrown and their values added, the possible sums would not have equal probability and so the distribution of sums of two dice rolls is not uniform. Although it is common to consider discrete uniform distributions over a contiguous range of integers, such as in this six-sided die example, one can define discrete uniform distributions over any finite set. Fo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Index Of Coincidence
In cryptography, coincidence counting is the technique (invented by William F. Friedman) of putting two texts side-by-side and counting the number of times that identical letters appear in the same position in both texts. This count, either as a ratio of the total or normalized by dividing by the expected count for a random source model, is known as the index of coincidence, or IC or IOC or IoC for short. Because letters in a natural language are not letter frequency, distributed evenly, the IC is higher for such texts than it would be for uniformly random text strings. What makes the IC especially useful is the fact that its value does not change if both texts are scrambled by the same single-alphabet substitution cipher, allowing a cryptanalyst to quickly detect that form of encryption. Calculation The index of coincidence provides a measure of how likely it is to draw two matching letters by randomly selecting two letters from a given text. The chance of drawing a given letter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
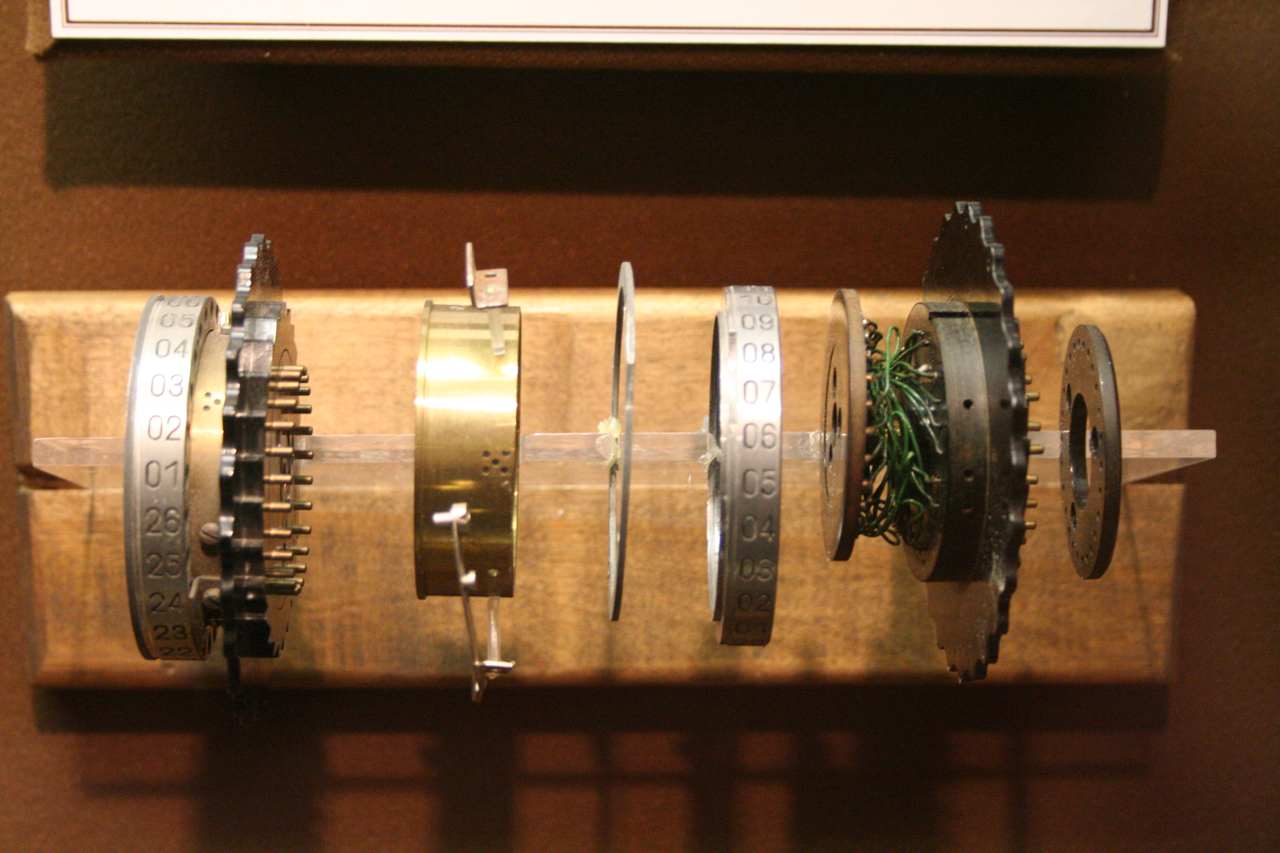
Enigma Rotor
This article contains technical details about the rotors of the Enigma machine The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the W .... Understanding the way the machine encrypts requires taking into account the current position of each rotor, the ring setting and its internal wiring. Physical design of rotors Image:Enigma-rotor-pin-contacts.jpg, The right side of a rotor, showing the pin electrical contacts. The Roman numeral V identifies the wiring of the rotor. Image:Enigma-rotor-flat-contacts.jpg, The left side of an Enigma rotor, showing the flat (plate) electrical contacts. A single turnover notch is visible on the left edge of the rotor. Rotor electrical view No letter can map to itself, a cryptographic weakness caused by the same wires being used for forwards and bac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Banburismus
Banburismus was a Cryptanalysis, cryptanalytic process developed by Alan Turing at Bletchley Park in United Kingdom, Britain during the Second World War. It was used by Bletchley Park's Hut 8 to help break German ''Kriegsmarine'' (naval) messages enciphered on Enigma machines. The process used Sequential analysis, sequential conditional probability to infer information about the likely settings of the Enigma machine. It gave rise to Turing's invention of the ''Ban (unit), ban'' as a measure of the weight of evidence in favour of a hypothesis. This concept was later applied in Turingery and all the other methods used for breaking the Lorenz cipher. Overview The aim of Banburismus was to reduce the time required of the electromechanical Bombe machines by identifying the most likely right-hand and middle wheels of the Enigma. Hut 8 performed the procedure continuously for two years, stopping only in 1943 when sufficient bombe time became readily available. Banburismus was a developm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher and theoretical biologist. He was highly influential in the development of theoretical computer science, providing a formalisation of the concepts of algorithm and computation with the Turing machine, which can be considered a model of a general-purpose computer. Turing is widely considered to be the father of theoretical computer science. Born in London, Turing was raised in southern England. He graduated from University of Cambridge, King's College, Cambridge, and in 1938, earned a doctorate degree from Princeton University. During World War II, Turing worked for the Government Code and Cypher School at Bletchley Park, Britain's codebreaking centre that produced Ultra (cryptography), Ultra intelligence. He led Hut 8, the section responsible for German naval cryptanalysis. Turing devised techniques for speeding the breaking of Germ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Poland
Poland, officially the Republic of Poland, is a country in Central Europe. It extends from the Baltic Sea in the north to the Sudetes and Carpathian Mountains in the south, bordered by Lithuania and Russia to the northeast, Belarus and Ukraine to the east, Slovakia and the Czech Republic to the south, and Germany to the west. The territory has a varied landscape, diverse ecosystems, and a temperate climate. Poland is composed of Voivodeships of Poland, sixteen voivodeships and is the fifth most populous member state of the European Union (EU), with over 38 million people, and the List of European countries by area, fifth largest EU country by area, covering . The capital and List of cities and towns in Poland, largest city is Warsaw; other major cities include Kraków, Wrocław, Łódź, Poznań, and Gdańsk. Prehistory and protohistory of Poland, Prehistoric human activity on Polish soil dates to the Lower Paleolithic, with continuous settlement since the end of the Last Gla ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |