|
802.11i
IEEE 802.11i-2004, or 802.11i for short, is an amendment to the original IEEE 802.11, implemented as Wi-Fi Protected Access II (WPA2). The draft standard was ratified on 24 June 2004. This standard specifies security mechanisms for wireless networks, replacing the short ''Authentication and privacy'' clause of the original standard with a detailed ''Security'' clause. In the process, the amendment deprecated broken Wired Equivalent Privacy (WEP), while it was later incorporated into the published IEEE 802.11-2007 standard. Replacement of WEP 802.11i supersedes the previous security specification, Wired Equivalent Privacy (WEP), which was shown to have security vulnerabilities. Wi-Fi Protected Access (WPA) had previously been introduced by the Wi-Fi Alliance as an intermediate solution to WEP insecurities. WPA implemented a subset of a draft of 802.11i. The Wi-Fi Alliance refers to their approved, interoperable implementation of the full 802.11i as WPA2, also called RSN (Robust ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Security
Wireless security is the prevention of unauthorized access or damage to computers or data using wireless networks, which include Wi-Fi networks. The term may also refer to the protection of the wireless network itself from adversaries seeking to damage the confidentiality, integrity, or availability of the network. The most common type is Wi-Fi security, which includes Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is an old IEEE 802.11 standard from 1997. It is a notoriously weak security standard: the password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP was superseded in 2003 by WPA, a quick alternative at the time to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP. Enterprises ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA) (Wireless Protected Access), Wi-Fi Protected Access 2 (WPA2), and Wi-Fi Protected Access 3 (WPA3) are the three security certification programs developed after 2000 by the Wi-Fi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses researchers had found in the previous system, Wired Equivalent Privacy (WEP). WPA (sometimes referred to as the TKIP standard) became available in 2003. The Wi-Fi Alliance intended it as an intermediate measure in anticipation of the availability of the more secure and complex WPA2, which became available in 2004 and is a common shorthand for the full IEEE 802.11i (or IEEE 802.11i-2004) standard. In January 2018, the Wi-Fi Alliance announced the release of WPA3, which has several security improvements over WPA2. As of 2023, most computers that connect to a wireless network have support for using WPA, WPA2, or WPA3. All versions thereof, at least as implemented throu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wired Equivalent Privacy
Wired Equivalent Privacy (WEP) is an obsolete, and insecure security algorithm for 802.11 wireless networks. It was introduced as part of the original IEEE 802.11 standard ratified in 1997. The intention was to provide a level of security and privacy comparable to that of a traditional wired network. WEP, recognizable by its key of 10 or 26 hexadecimal digits (40 or 104 bits), was at one time widely used, and was often the first security choice presented to users by router configuration tools. After a severe design flaw in the algorithm was disclosed in 2001, WEP was no longer considered a secure method of wireless connection; however, in the vast majority of cases, Wi-Fi hardware devices relying on WEP security could not be upgraded to secure operation. Some of WEP's design flaws were addressed in WEP2, but it also proved insecure, and never saw wide adoption or standardization. In 2003, the Wi-Fi Alliance announced that WEP and WEP2 had been superseded by Wi-Fi Protected Acc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Temporal Key Integrity Protocol
Temporal Key Integrity Protocol (TKIP ) is a security protocol used in the IEEE 802.11 wireless networking standard. TKIP was designed by the IEEE 802.11i task group and the Wi-Fi Alliance as an interim solution to replace Wired Equivalent Privacy, WEP without requiring the replacement of legacy hardware. This was necessary because the breaking of WEP had left Wi-Fi networks without viable Data link layer#Logical link control sublayer, link-layer security, and a solution was required for already deployed hardware. However, TKIP itself is no longer considered secure, and was deprecated in the 2012 revision of the 802.11 standard. Background On October 31, 2002, the Wi-Fi Alliance endorsed TKIP under the name Wi-Fi Protected Access, Wi-Fi Protected Access (WPA). The IEEE endorsed the final version of TKIP, along with more robust solutions such as 802.1X and the Advanced Encryption Standard, AES based CCMP (cryptography), CCMP, when they published IEEE 802.11i-2004 on 23 July 2004 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CCM Mode
CCM mode (counter with cipher block chaining message authentication code; counter with CBC-MAC) is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both authentication and confidentiality. CCM mode is only defined for block ciphers with a block length of 128 bits. The nonce of CCM must be carefully chosen to never be used more than once for a given key. This is because CCM is a derivation of counter (CTR) mode and the latter is effectively a stream cipher. Encryption and authentication As the name suggests, CCM mode combines counter (CTR) mode for confidentiality with cipher block chaining message authentication code (CBC-MAC) for authentication. These two primitives are applied in an "authenticate-then-encrypt" manner: CBC-MAC is first computed on the message to obtain a message authentication code (MAC), then the message and the MAC are encrypted using counter mode. The main insight is that the same ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Extensible Authentication Protocol
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by . EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods. There are many methods defined by RFCs, and a number of vendor-specific methods and new proposals exist. EAP is not a wire protocol; instead it only defines the information from the interface and the formats. Each protocol that uses EAP defines a way to encapsulate by the user EAP messages within that protocol's messages. EAP is in wide use. For example, in IEEE 802.11 (Wi-Fi) the WPA and WPA2 standards have adopted IEEE 802.1X (with various EAP types) as the canonical authentication mechanism. Methods EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wi-Fi Alliance
The Wi-Fi Alliance is a non-profit organization that owns the Wi-Fi trademark. Manufacturers may use the trademark to brand products certified for Wi-Fi interoperability. It is based in Austin, Texas. History Early IEEE 802.11, 802.11 products suffered from interoperability problems because the Institute of Electrical and Electronics Engineers (IEEE) had no provision for testing equipment for compliance with its standards. In 1999, pioneers of a new, higher-speed variant endorsed the IEEE 802.11b specification to form the Wireless Ethernet Compatibility Alliance (WECA) and branded the new technology Wi-Fi. The group of companies included 3Com, Aironet (acquired by Cisco), Harris Semiconductor (now Intersil), Lucent Technologies (the WLAN part was renamed as Orinoco, become part of Avaya, then acquired by Extreme Networks), Nokia and Symbol Technologies (acquired by Motorola, Zebra Technologies, and now Extreme Networks). The alliance lists Apple Inc., Apple, Comcast, Samsung ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RC4 (cipher)
In cryptography, RC4 (Rivest Cipher 4, also known as ARC4 or ARCFOUR, meaning Alleged RC4, see below) is a stream cipher. While it is remarkable for its simplicity and speed in software, multiple vulnerabilities have been discovered in RC4, rendering it insecure. It is especially vulnerable when the beginning of the output keystream is not discarded, or when nonrandom or related keys are used. Particularly problematic uses of RC4 have led to very insecure protocols such as WEP. , there is speculation that some state cryptologic agencies may possess the capability to break RC4 when used in the TLS protocol. IETF has published RFC 7465 to prohibit the use of RC4 in TLS; Mozilla and Microsoft have issued similar recommendations. A number of attempts have been made to strengthen RC4, notably Spritz, RC4A, VMPC, and RC4+. History RC4 was designed by Ron Rivest of RSA Security in 1987. While it is officially termed "Rivest Cipher 4", the RC acronym is alternatively understood to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Access Point
In Computer networking device, computer networking, a wireless access point (WAP) (also just access point (AP)) is a networking hardware device that allows other Wi-Fi devices to connect to a wired network or wireless network. As a standalone device, the AP may have a wired or wireless connection to a Network switch, switch or Router (computing), router, but in a wireless router it can also be an integral component of the networking device itself. A WAP and AP is differentiated from a Wi-Fi hotspot, hotspot, which can be a physical location or digital location where Wi-Fi or WAP access is available. Connections An AP connects directly to a wired local area network, local local area network, area network, typically Ethernet, and the AP then provides wireless connections using wireless LAN technology, typically Wi-Fi, for other devices to use that wired connection. APs support the connection of multiple wireless devices through their one wired connection. Wireless data standa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CCMP (cryptography)
Counter Mode Cipher Block Chaining Message Authentication Code Protocol (Counter Mode CBC-MAC Protocol) or CCM mode Protocol (CCMP) is an authenticated encryption protocol designed for Wireless LAN products that implements the standards of the IEEE 802.11i amendment to the original IEEE 802.11 standard. CCMP is a data cryptographic encapsulation mechanism designed for data confidentiality, integrity and authentication. It is based upon the Counter Mode with CBC-MAC (CCM mode) of the Advanced Encryption Standard (AES) standard. It was created to address the vulnerabilities presented by Wired Equivalent Privacy (WEP), a dated, insecure protocol. Technical details CCMP uses CCM that combines CTR mode for data confidentiality and cipher block chaining message authentication code (CBC-MAC) for authentication and integrity. CCM protects the integrity of both the MPDU data field and selected portions of the IEEE 802.11 MPDU header. CCMP is based on AES processing and uses a 128-bit k ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
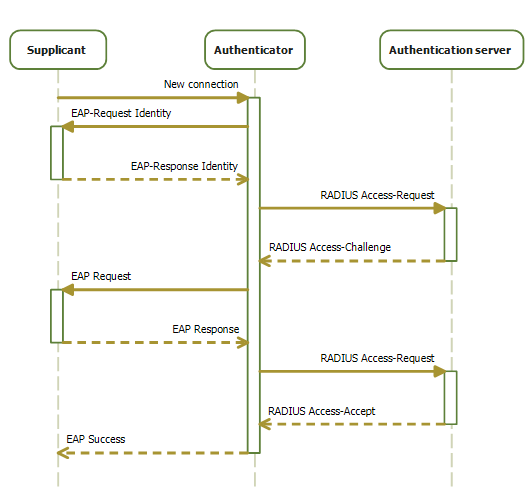
EAPOL
IEEE 802.1X is an IEEE Standard for port-based network access control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN. The standard directly addresses an attack technique called Hardware Addition where an attacker posing as a guest, customer or staff smuggles a hacking device into the building that they then plug into the network giving them full access. A notable example of the issue occurred in 2005 when a machine attached to Walmart's network hacked thousands of their servers. IEEE 802.1X defines the encapsulation of the Extensible Authentication Protocol (EAP) over wired IEEE 802 networks and over 802.11 wireless networks, which is known as "EAP over LAN" or EAPOL. EAPOL was originally specified for IEEE 802.3 Ethernet, IEEE 802.5 Token Ring, and FDDI (ANSI X3T9.5/X3T12 and ISO 9314) in 802.1X-2001, but was extended to suit other IEEE 802 LAN technologies such as IEEE 8 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |