XKeyscore on:
[Wikipedia]
[Google]
[Amazon]
XKeyscore (XKEYSCORE or XKS) is a secret computer system used by the United States

 According to an NSA slide presentation about XKeyscore from 2013, it is a " DNI Exploitation System/Analytic Framework". DNI stands for Digital Network Intelligence, which means intelligence derived from internet traffic.
Edward Snowden said about XKeyscore: "It's a front end search engine" in an interview with the German
According to an NSA slide presentation about XKeyscore from 2013, it is a " DNI Exploitation System/Analytic Framework". DNI stands for Digital Network Intelligence, which means intelligence derived from internet traffic.
Edward Snowden said about XKeyscore: "It's a front end search engine" in an interview with the German
3 slides about the XKeyscore program
A detailed commentary on an NSA presentation published in ''The Guardian'' in July 2013 cites a document published in 2008 declaring that "At some sites, the amount of data we receive per day (20+ terabytes) can only be stored for as little as 24 hours." Greenwald, Glenn (July 31, 2013
"XKeyscore: NSA tool collects 'nearly everything a user does on the internet' XKeyscore Gives 'Widest-Reaching' Collection of Online Data NSA Analysts Require No Prior Authorization for Searches Sweeps Up Emails, Social Media Activity and Browsing History"
. ''
 For analysts, XKeyscore provides a "series of viewers for common data types", which allows them to query terabytes of raw data gathered at the aforementioned collection sites. This enables them to find targets that cannot be found by searching only the metadata, and also to do this against data sets that otherwise would have been dropped by the front-end data processing systems. According to a slide from an XKeyscore presentation, NSA collection sites select and forward less than 5% of the internet traffic to the PINWALE database for internet content.
Because XKeyscore holds raw and unselected communications traffic, analysts can not only perform queries using "strong selectors" like e-mail addresses, but also using "soft selectors", like keywords, against the body texts of e-mail and chat messages and digital documents and spreadsheets in English, Arabic and Chinese.
This is useful because "a large amount of time spent on the web is performing actions that are anonymous" and therefore those activities can't be found by just looking for e-mail addresses of a target. When content has been found, the analyst might be able to find new intelligence or a strong selector, which can then be used for starting a traditional search.
Besides using soft selectors, analysts can also use the following other XKeyscore capabilities:
* Look for the usage of
For analysts, XKeyscore provides a "series of viewers for common data types", which allows them to query terabytes of raw data gathered at the aforementioned collection sites. This enables them to find targets that cannot be found by searching only the metadata, and also to do this against data sets that otherwise would have been dropped by the front-end data processing systems. According to a slide from an XKeyscore presentation, NSA collection sites select and forward less than 5% of the internet traffic to the PINWALE database for internet content.
Because XKeyscore holds raw and unselected communications traffic, analysts can not only perform queries using "strong selectors" like e-mail addresses, but also using "soft selectors", like keywords, against the body texts of e-mail and chat messages and digital documents and spreadsheets in English, Arabic and Chinese.
This is useful because "a large amount of time spent on the web is performing actions that are anonymous" and therefore those activities can't be found by just looking for e-mail addresses of a target. When content has been found, the analyst might be able to find new intelligence or a strong selector, which can then be used for starting a traditional search.
Besides using soft selectors, analysts can also use the following other XKeyscore capabilities:
* Look for the usage of
Ally and Target: US Intelligence Watches Germany Closely
, August 12, 2013. To create additional motivation, the NSA incorporated various
 According to documents ''
According to documents ''
"'Prolific Partner': German Intelligence Used NSA Spy Program"
. ''
A full NSA presentation about XKeyscore from 2008
Building a panopticon: The evolution of the NSA’s XKeyscore
* * {{Mass surveillance 2013 scandals Counterterrorism in the United States Espionage Human rights in the United States Mass surveillance Obama administration controversies Privacy in the United States Privacy of telecommunications American secret government programs Surveillance scandals United States national security policy War on terror GCHQ operations National Security Agency operations Intelligence agency programmes revealed by Edward Snowden Federal Intelligence Service Communications Security Establishment
National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collecti ...
(NSA) for searching and analyzing global Internet data, which it collects in real time. The NSA has shared XKeyscore with other intelligence agencies, including the Australian Signals Directorate
Australian Signals Directorate (ASD), formerly the Defence Signals Directorate (DSD) is the federal statutory agency in the Australian Government responsible for foreign signals intelligence, support to military operations, cyber warfare, and i ...
, Canada's Communications Security Establishment
The Communications Security Establishment (CSE; french: Centre de la sécurité des télécommunications, ''CST''), formerly (from 2008-2014) called the Communications Security Establishment Canada (CSEC), is the Government of Canada's national ...
, New Zealand's Government Communications Security Bureau
The Government Communications Security Bureau (GCSB) ( mi, Te Tira Tiaki) is the public-service department of New Zealand charged with promoting New Zealand's national security by collecting and analysing information of an intelligence nature. ...
, Britain's Government Communications Headquarters
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the Uni ...
, Japan's Defense Intelligence Headquarters, and Germany's Bundesnachrichtendienst
The Federal Intelligence Service (German: ; , BND) is the foreign intelligence agency of Germany, directly subordinate to the Chancellor's Office. The BND headquarters is located in central Berlin and is the world's largest intelligence h ...
.
In July 2013, Edward Snowden
Edward Joseph Snowden (born June 21, 1983) is an American and naturalized Russian former computer intelligence consultant who leaked highly classified information from the National Security Agency (NSA) in 2013, when he was an employee and su ...
publicly revealed the program's purpose and use by the NSA in ''The Sydney Morning Herald
''The Sydney Morning Herald'' (''SMH'') is a daily compact newspaper published in Sydney, New South Wales, Australia, and owned by Nine. Founded in 1831 as the ''Sydney Herald'', the ''Herald'' is the oldest continuously published newspaper ...
'' and ''O Globo
''O Globo'' (, ''The Globe'') is a Brazilian newspaper based in Rio de Janeiro. ''O Globo'' is the most prominent print publication in the Grupo Globo media conglomerate.
Founded by journalist Irineu Marinho, owner of ''A Noite'', it was ori ...
'' newspapers. The code name was already public knowledge because it was mentioned in earlier articles, and, like many other code names, it appears in job postings and online résumé
A résumé, sometimes spelled resume (or alternatively resumé), also called a curriculum vitae (CV), is a document created and used by a person to present their background, skills, and accomplishments. Résumés can be used for a variety of rea ...
s of employees.
On July 3, 2014, German public broadcaster
Public broadcasting involves radio, television and other electronic media outlets whose primary mission is public service. Public broadcasters receive funding from diverse sources including license fees, individual contributions, public financing ...
Norddeutscher Rundfunk
Norddeutscher Rundfunk (NDR; ''Northern German Broadcasting'') is a public radio and television broadcaster, based in Hamburg. In addition to the city-state of Hamburg, NDR broadcasts for the German states of Lower Saxony, Mecklenburg-Vorpommer ...
, a member of ARD, published excerpts of XKeyscore's source code. A team of experts analyzed the source code.
Scope and functioning
XKeyscore is a complicated system, and various authors have different interpretations of its actual capabilities.Edward Snowden
Edward Joseph Snowden (born June 21, 1983) is an American and naturalized Russian former computer intelligence consultant who leaked highly classified information from the National Security Agency (NSA) in 2013, when he was an employee and su ...
and Glenn Greenwald
Glenn Edward Greenwald (born March 6, 1967) is an American journalist, author and lawyer. In 2014, he cofounded ''The Intercept'', of which he was an editor until he resigned in October 2020. Greenwald subsequently started publishing on Substac ...
explained XKeyscore as being a system which enables almost unlimited surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as ...
of anyone anywhere in the world, while the NSA has said that usage of the system is limited and restricted.
According to ''The Washington Post
''The Washington Post'' (also known as the ''Post'' and, informally, ''WaPo'') is an American daily newspaper published in Washington, D.C. It is the most widely circulated newspaper within the Washington metropolitan area and has a large n ...
'' and national security reporter Marc Ambinder
Marc Ambinder (; born ) is an American university professor, journalist, and television producer. He is a former politics editor at ''The Atlantic'', a White House Correspondent for ''National Journal'', contributing editor for '' GQ'', and was edi ...
, XKeyscore is an NSA data-retrieval system which consists of a series of user interfaces, backend databases, servers and software that selects certain types of data and metadata
Metadata is "data that provides information about other data", but not the content of the data, such as the text of a message or the image itself. There are many distinct types of metadata, including:
* Descriptive metadata – the descriptive ...
that the NSA has already collected using other methods.
According to Snowden and Greenwald
On January 26, 2014, the German broadcasterNorddeutscher Rundfunk
Norddeutscher Rundfunk (NDR; ''Northern German Broadcasting'') is a public radio and television broadcaster, based in Hamburg. In addition to the city-state of Hamburg, NDR broadcasts for the German states of Lower Saxony, Mecklenburg-Vorpommer ...
asked Edward Snowden in its TV interview: "What could you do if you would use XKeyscore?" and he answered:
According to ''The Guardian
''The Guardian'' is a British daily newspaper. It was founded in 1821 as ''The Manchester Guardian'', and changed its name in 1959. Along with its sister papers '' The Observer'' and '' The Guardian Weekly'', ''The Guardian'' is part of the ...
''s Glenn Greenwald
Glenn Edward Greenwald (born March 6, 1967) is an American journalist, author and lawyer. In 2014, he cofounded ''The Intercept'', of which he was an editor until he resigned in October 2020. Greenwald subsequently started publishing on Substac ...
, low-level NSA analysts can, via systems like XKeyscore, "listen to whatever emails they want, whatever telephone calls, browsing histories, Microsoft Word documents. And it's all done with no need to go to a court, with no need to even get supervisor approval on the part of the analyst."
He added that the NSA's database of collected communications allows its analysts to listen "to the calls or read the emails of everything that the NSA has stored, or look at the browsing histories or Google search terms that you've entered, and it also alerts them to any further activity that people connected to that email address or that IP address do in the future".
According to the NSA
In an official statement from July 30, 2013, the NSA said "XKeyscore is used as a part of NSA's lawful foreignsignals intelligence
Signals intelligence (SIGINT) is intelligence-gathering by interception of '' signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly used in communication ...
collection system. ..." to legally obtain information about "legitimate foreign intelligence targets in response to requirements that our leaders need for information necessary to protect our nation and its interests. ... to collect the information, that enables us to perform our missions successfully – to defend the nation and to protect U.S. and allied troops abroad."
In terms of access, an NSA press statement reads that there is no "unchecked analyst access to NSA collection data. Access to XKeyscore, as well as all of NSA's analytic tools, is limited to only those personnel who require access for their assigned tasks." and that there are "...stringent oversight and compliance mechanisms built in at several levels. One feature is the system's ability to limit what an analyst can do with a tool, based on the source of the collection and each analyst's defined responsibilities."
Workings

 According to an NSA slide presentation about XKeyscore from 2013, it is a " DNI Exploitation System/Analytic Framework". DNI stands for Digital Network Intelligence, which means intelligence derived from internet traffic.
Edward Snowden said about XKeyscore: "It's a front end search engine" in an interview with the German
According to an NSA slide presentation about XKeyscore from 2013, it is a " DNI Exploitation System/Analytic Framework". DNI stands for Digital Network Intelligence, which means intelligence derived from internet traffic.
Edward Snowden said about XKeyscore: "It's a front end search engine" in an interview with the German Norddeutscher Rundfunk
Norddeutscher Rundfunk (NDR; ''Northern German Broadcasting'') is a public radio and television broadcaster, based in Hamburg. In addition to the city-state of Hamburg, NDR broadcasts for the German states of Lower Saxony, Mecklenburg-Vorpommer ...
.
XKeyscore is a "piece of Linux software that is typically deployed on Red Hat
Red Hat, Inc. is an American software company that provides open source software products to enterprises. Founded in 1993, Red Hat has its corporate headquarters in Raleigh, North Carolina, with other offices worldwide.
Red Hat has become a ...
servers. It uses the Apache web server
The Apache HTTP Server ( ) is a free and open-source cross-platform web server software, released under the terms of Apache License 2.0. Apache is developed and maintained by an open community of developers under the auspices of the Apache Soft ...
and stores collected data in MySQL
MySQL () is an open-source relational database management system (RDBMS). Its name is a combination of "My", the name of co-founder Michael Widenius's daughter My, and "SQL", the acronym for Structured Query Language. A relational database ...
databases".
XKeyscore is considered a "passive" program, in that it listens, but does not transmit anything on the networks that it targets. But it can trigger other systems, which perform "active" attacks through Tailored Access Operations
The Office of Tailored Access Operations (TAO), now Computer Network Operations, and structured as S32, is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA). It has been active since at least 1998, possibly 1997, ...
which are "tipping", for example, the QUANTUM family of programs, including QUANTUMINSERT, QUANTUMHAND, QUANTUMTHEORY, QUANTUMBOT and QUANTUMCOPPER and Turbulence
In fluid dynamics, turbulence or turbulent flow is fluid motion characterized by chaotic changes in pressure and flow velocity. It is in contrast to a laminar flow, which occurs when a fluid flows in parallel layers, with no disruption between ...
. These run at so-called "defensive sites" including the Ramstein Air Force base in Germany, Yokota Air Base
, is a Japan Air Self-Defense Force (JASDF) and United States Air Force (USAF) base in the Tama Area, or Western Tokyo.
It occupies portions of Akishima, Fussa, Hamura, Mizuho, Musashimurayama, and Tachikawa.
The base houses 14,000 perso ...
in Japan, and numerous military and non-military locations within the US. Trafficthief, a core program of Turbulence, can alert NSA analysts when their targets communicate, and trigger other software programs, so select data is "promoted" from the local XKeyscore data store to the NSA's "corporate repositories" for long term storage.
Data sources
XKeyscore consists of over 700 servers at approximately 150 sites where the NSA collects data, like "US and allied military and other facilities as well as US embassies and consulates" in many countries around the world. Among the facilities involved in the program are four bases inAustralia
Australia, officially the Commonwealth of Australia, is a sovereign country comprising the mainland of the Australian continent, the island of Tasmania, and numerous smaller islands. With an area of , Australia is the largest country by ...
and one in New Zealand
New Zealand ( mi, Aotearoa ) is an island country in the southwestern Pacific Ocean. It consists of two main landmasses—the North Island () and the South Island ()—and over 700 smaller islands. It is the sixth-largest island coun ...
.
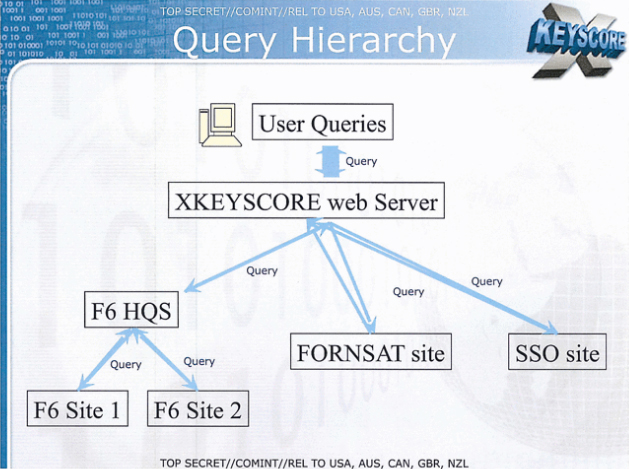
According to an NSA presentation from 2008, these XKeyscore servers are fed with data from the following collection systems:
# '' F6 (Special Collection Service)'' joint operation of the CIA and NSA that carries out clandestine operations including espionage on foreign diplomats and leaders
# '' FORNSAT'' which stands for "foreign satellite collection", and refers to intercepts from satellites
# '' SSO (Special Source Operations)'' a division of the NSA that cooperates with telecommunication providers
In a single, undated slide published by Swedish media in December 2013, the following additional data sources for XKeyscore are mentioned:
# ''Overhead'' intelligence derived from American spy planes, drones and satellites
# ''Tailored Access Operations
The Office of Tailored Access Operations (TAO), now Computer Network Operations, and structured as S32, is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA). It has been active since at least 1998, possibly 1997, ...
'' a division of the NSA that deals with hacking and cyberwarfare
Cyberwarfare is the use of cyber attacks against an enemy state, causing comparable harm to actual warfare and/or disrupting vital computer systems. Some intended outcomes could be espionage, sabotage, propaganda, manipulation or economic ...
# '' FISA'' all types of surveillance approved by the Foreign Intelligence Surveillance Court
The United States Foreign Intelligence Surveillance Court (FISC), also called the FISA Court, is a U.S. federal court established under the Foreign Intelligence Surveillance Act of 1978 (FISA) to oversee requests for surveillance warrants aga ...
#''Third party
Third party may refer to:
Business
* Third-party source, a supplier company not owned by the buyer or seller
* Third-party beneficiary, a person who could sue on a contract, despite not being an active party
* Third-party insurance, such as a V ...
'' foreign partners of the NSA such as the (signals) intelligence agencies of Belgium, Denmark, France, Germany, Italy, Japan, the Netherlands, Norway, Sweden, etc. However the Netherlands is out of any cooperation concerning intelligence gathering and sharing for illegal spying.
From these sources, XKeyscore stores "full-take data", which are indexed by plug-ins that extract certain types of metadata (like phone numbers, e-mail addresses, log-ins, and user activity) and index them in metadata tables, which can be queried by analysts. XKeyscore has been integrated with MARINA
A marina (from Spanish , Portuguese and Italian : ''marina'', "coast" or "shore") is a dock or basin with moorings and supplies for yachts and small boats.
A marina differs from a port in that a marina does not handle large passenger ships or ...
, which is NSA's database for internet metadata.
However, the system continuously gets so much Internet data that it can be stored only for short periods of time. Content data remain on the system for only three to five days, while metadata is stored for up to thirty days.See also3 slides about the XKeyscore program
A detailed commentary on an NSA presentation published in ''The Guardian'' in July 2013 cites a document published in 2008 declaring that "At some sites, the amount of data we receive per day (20+ terabytes) can only be stored for as little as 24 hours." Greenwald, Glenn (July 31, 2013
"XKeyscore: NSA tool collects 'nearly everything a user does on the internet' XKeyscore Gives 'Widest-Reaching' Collection of Online Data NSA Analysts Require No Prior Authorization for Searches Sweeps Up Emails, Social Media Activity and Browsing History"
. ''
The Guardian
''The Guardian'' is a British daily newspaper. It was founded in 1821 as ''The Manchester Guardian'', and changed its name in 1959. Along with its sister papers '' The Observer'' and '' The Guardian Weekly'', ''The Guardian'' is part of the ...
''. Retrieved August 1, 2013.
Types of XKeyscore
According to a document from an internal GCHQ website which was disclosed by the German magazine ''Der Spiegel'' in June 2014, there are three different types of the Xkeyscore system: * Traditional: The initial version of XKeyscore is fed with data from low-rate data signals, after being processed by the WEALTHYCLUSTER system. This traditional version is not only used by NSA but also at many intercept sites of GCHQ. * Stage 2: This version of XKeyscore is used for higher data rates. The data are first processed by the TURMOIL system, which sends 5% of the internet data packets to XKeyscore. GCHQ only uses this version for its collection under theMUSCULAR
Skeletal muscles (commonly referred to as muscles) are organs of the vertebrate muscular system and typically are attached by tendons to bones of a skeleton. The muscle cells of skeletal muscles are much longer than in the other types of muscle ...
program.
* Deep Dive: This latest version can process internet traffic at data rates of 10 gigabits per second. Data that could be useful for intelligence purposes are then selected and forwarded by using the "GENESIS selection language". GCHQ also operates a number of Deep Dive versions of XKeyscore at three locations under the codename TEMPORA
Tempora is the codeword for a formerly-secret computer system that is used by the British Government Communications Headquarters (GCHQ). This system is used to buffer most Internet communications that are extracted from fibre-optic cables, so t ...
.
Capabilities
 For analysts, XKeyscore provides a "series of viewers for common data types", which allows them to query terabytes of raw data gathered at the aforementioned collection sites. This enables them to find targets that cannot be found by searching only the metadata, and also to do this against data sets that otherwise would have been dropped by the front-end data processing systems. According to a slide from an XKeyscore presentation, NSA collection sites select and forward less than 5% of the internet traffic to the PINWALE database for internet content.
Because XKeyscore holds raw and unselected communications traffic, analysts can not only perform queries using "strong selectors" like e-mail addresses, but also using "soft selectors", like keywords, against the body texts of e-mail and chat messages and digital documents and spreadsheets in English, Arabic and Chinese.
This is useful because "a large amount of time spent on the web is performing actions that are anonymous" and therefore those activities can't be found by just looking for e-mail addresses of a target. When content has been found, the analyst might be able to find new intelligence or a strong selector, which can then be used for starting a traditional search.
Besides using soft selectors, analysts can also use the following other XKeyscore capabilities:
* Look for the usage of
For analysts, XKeyscore provides a "series of viewers for common data types", which allows them to query terabytes of raw data gathered at the aforementioned collection sites. This enables them to find targets that cannot be found by searching only the metadata, and also to do this against data sets that otherwise would have been dropped by the front-end data processing systems. According to a slide from an XKeyscore presentation, NSA collection sites select and forward less than 5% of the internet traffic to the PINWALE database for internet content.
Because XKeyscore holds raw and unselected communications traffic, analysts can not only perform queries using "strong selectors" like e-mail addresses, but also using "soft selectors", like keywords, against the body texts of e-mail and chat messages and digital documents and spreadsheets in English, Arabic and Chinese.
This is useful because "a large amount of time spent on the web is performing actions that are anonymous" and therefore those activities can't be found by just looking for e-mail addresses of a target. When content has been found, the analyst might be able to find new intelligence or a strong selector, which can then be used for starting a traditional search.
Besides using soft selectors, analysts can also use the following other XKeyscore capabilities:
* Look for the usage of Google Maps
Google Maps is a web mapping platform and consumer application offered by Google. It offers satellite imagery, aerial photography, street maps, 360° interactive panoramic views of streets (Street View), real-time traffic conditions, and rou ...
and terms entered into a search engine by known targets looking for suspicious things or places.
* Look for "anomalies" without any specific person attached, like detecting the nationality of foreigners by analyzing the language used within intercepted emails. An example would be a German speaker in Pakistan. The Brazilian paper ''O Globo'' claims that this has been applied to Latin America and specifically to Colombia, Ecuador, Mexico and Venezuela.
* Detect people who use encryption by doing searches like "all PGP
PGP or Pgp may refer to:
Science and technology
* P-glycoprotein, a type of protein
* Pelvic girdle pain, a pregnancy discomfort
* Personal Genome Project, to sequence genomes and medical records
* Pretty Good Privacy, a computer program for the ...
usage in Iran". The caveat given is that very broad queries can result in too much data to transmit back to the analyst.
* Showing the usage of virtual private network
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The b ...
s (VPNs) and machines that can potentially be hacked via TAO.
* Track the source and authorship of a document that has passed through many hands.
* On July 3, 2014 ARD revealed that XKeyscore is used to closely monitor users of the Tor anonymity network, people who search for privacy-enhancing software on the web, and readers of ''Linux Journal
''Linux Journal'' (''LJ'') is an American monthly technology magazine originally published by Specialized System Consultants, Inc. (SSC) in Seattle, Washington since 1994. In December 2006 the publisher changed to Belltown Media, Inc. in Houston, ...
''.
''The Guardian'' revealed in 2013 that most of these things cannot be detected by other NSA tools, because they operate with strong selectors (like e-mail and IP addresses and phone numbers) and the raw data volumes are too high to be forwarded to other NSA databases.
In 2008, NSA planned to add a number of new capabilities in the future, like VoIP
Voice over Internet Protocol (VoIP), also called IP telephony, is a method and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. The terms Internet t ...
, , Exif
Exchangeable image file format (officially Exif, according to JEIDA/JEITA/CIPA specifications) is a standard that specifies formats for images, sound, and ancillary tags used by digital cameras (including smartphones), scanners and other syste ...
tags, which often include geolocation
Geopositioning, also known as geotracking, geolocalization, geolocating, geolocation, or geoposition fixing, is the process of determining or estimating the geographic position of an object.
Geopositioning yields a set of geographic coordinates ...
(GPS
The Global Positioning System (GPS), originally Navstar GPS, is a satellite-based radionavigation system owned by the United States government and operated by the United States Space Force. It is one of the global navigation satellite sy ...
) data.
Contribution to U.S. security
The NSA slides published in ''The Guardian'' during 2013 claimed that XKeyscore had played a role in capturing 300 terrorists by 2008, which could not be substantiated as the redacted documents do not cite instances of terrorist interventions. A 2011 report from the NSA unit in theDagger Complex
The Dagger Complex is a US military base in Darmstadt (Germany), close to Griesheim and located at the ''Eberstädter Weg'', south of the August-Euler-Airfield.
The complex is under US Army Intelligence and Security Command (INSCOM) command ...
(close to Griesheim in Germany) said that XKeyscore made it easier and more efficient to target surveillance. Previously, analysis often accessed data NSA was not interested in. XKeyscore allowed them to focus on the intended topics, while ignoring unrelated data. XKeyscore also proved to be outstanding for tracking active groups associated with the Anonymous
Anonymous may refer to:
* Anonymity, the state of an individual's identity, or personally identifiable information, being publicly unknown
** Anonymous work, a work of art or literature that has an unnamed or unknown creator or author
* Anony ...
movement in Germany, because it allows for searching on patterns, rather than particular individuals. An analyst is able to determine when targets research new topics, or develop new behaviors.Laura Poitras, Marcel Rosenbach and Holger StarkAlly and Target: US Intelligence Watches Germany Closely
, August 12, 2013. To create additional motivation, the NSA incorporated various
gamification
Gamification is the strategic attempt to enhance systems, services, organizations, and activities by creating similar experiences to those experienced when playing games in order to motivate and engage users. This is generally accomplished thro ...
features. For instance, analysts who were especially good at using XKeyscore could acquire "skilz" points and "unlock achievements." The training units in Griesheim were apparently successful and analysts there had achieved the "highest average of skilz points" compared with all other NSA departments participating in the training program.
Usage by foreign partners of the NSA
Germany
 According to documents ''
According to documents ''Der Spiegel
''Der Spiegel'' (, lit. ''"The Mirror"'') is a German weekly news magazine published in Hamburg. With a weekly circulation of 695,100 copies, it was the largest such publication in Europe in 2011. It was founded in 1947 by John Seymour Chaloner ...
'' acquired from Snowden, the German intelligence agencies BND (foreign intelligence) and BfV BFV may refer to:
* Baden Football Association, the ''Badischer Fussball-Verband'', a regional football association in Germany
* Bavarian Football Association, the ''Bayerischer Fussball-Verband'', a regional football association in Germany
* Ber ...
(domestic intelligence) were also allowed to use the XKeyscore system. In those documents the BND agency was described as the NSA's most prolific partner in information gathering.Staff (July 20, 2013)"'Prolific Partner': German Intelligence Used NSA Spy Program"
. ''
Der Spiegel
''Der Spiegel'' (, lit. ''"The Mirror"'') is a German weekly news magazine published in Hamburg. With a weekly circulation of 695,100 copies, it was the largest such publication in Europe in 2011. It was founded in 1947 by John Seymour Chaloner ...
''. Retrieved August 5, 2013. This led to political confrontations, after which the directors of the German intelligence agencies briefed members of the German parliamentary intelligence oversight committee on July 25, 2013. They declared that XKeyscore has been used by the BND since 2007 and that the BfV has been using a test version since 2012. The directors also explained that the program is not for collecting data, but rather only for the analysis of collected data.
Sweden
As part of theUKUSA Agreement
The United Kingdom – United States of America Agreement (UKUSA, ) is a multilateral agreement for cooperation in signals intelligence between Australia, Canada, New Zealand, the United Kingdom, and the United States. The alliance of intellig ...
, a secret treaty was signed in 1954 by Sweden with the United States, the United Kingdom, Canada, Australia and New Zealand (called the Five Eyes
The Five Eyes (FVEY) is an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States. These countries are parties to the multilateral UKUSA Agreement, a treaty for joint cooperation in sig ...
) for the purpose of intelligence collaboration and data sharing
Data sharing is the practice of making data used for scholarly research available to other investigators. Many funding agencies, institutions, and publication venues have policies regarding data sharing because transparency and openness are consid ...
. According to documents leaked by Snowden, the National Defence Radio Establishment
The National Defence Radio Establishment ( sv, Försvarets radioanstalt, FRA) is a Swedish
government agency organised under the Ministry of Defence. The two main tasks of FRA are signals intelligence (SIGINT), and support to government authorit ...
(FRA) has been granted access to XKeyscore.
Denmark
In an ongoing scandal, where it has been revealed that NSA helped FE (Danish Military Intelligence Service) build a new Spy datacenter at Sandagergård, Amager, Xkeyscore has been made available for FE to use on the collected data.Japan
The classified documents leaked by Snowden also indicate that in April 2013, NSA had secretly provided the XKeyscore system to theJapanese government
The Government of Japan consists of legislative, executive and judiciary branches and is based on popular sovereignty. The Government runs under the framework established by the Constitution of Japan, adopted in 1947. It is a unitary state, ...
.
See also
*List of government surveillance projects
This is a list of government surveillance projects and related databases throughout the world.
International
* ECHELON: A signals intelligence (SIGINT) collection and analysis network operated on behalf of the five signatory states to the ...
* PRISM
Prism usually refers to:
* Prism (optics), a transparent optical component with flat surfaces that refract light
* Prism (geometry), a kind of polyhedron
Prism may also refer to:
Science and mathematics
* Prism (geology), a type of sedimentary ...
* :File:XKeyscore presentation from 2008.pdf, a redacted presentation about X-Keyscore via The Guardian (UK) via Edward Snowden via U.S. National Security Agency
* Targeted surveillance
Targeted surveillance (or targeted interception) is a form of surveillance, such as wiretapping, that is directed towards specific persons of interest, and is distinguishable from mass surveillance (or bulk interception). Both untargeted and tar ...
References
External links
A full NSA presentation about XKeyscore from 2008
Building a panopticon: The evolution of the NSA’s XKeyscore
* * {{Mass surveillance 2013 scandals Counterterrorism in the United States Espionage Human rights in the United States Mass surveillance Obama administration controversies Privacy in the United States Privacy of telecommunications American secret government programs Surveillance scandals United States national security policy War on terror GCHQ operations National Security Agency operations Intelligence agency programmes revealed by Edward Snowden Federal Intelligence Service Communications Security Establishment