Spoofed URL on:
[Wikipedia]
[Google]
[Amazon]
A spoofed URL describes one website that poses as another website. It sometimes applies a mechanism that exploits bugs in http://www.wikipedia.org '' but is, in reality, sending information to an entirely different location that would typically be monitored by an information thief. When sensitive information is requested by a fraudulent website, it is called

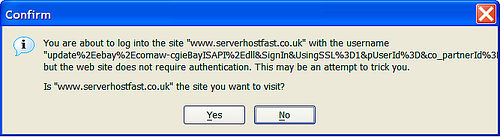 The most common are: using authentication based on key exchange between the machines on your
The most common are: using authentication based on key exchange between the machines on your
web browser
A web browser is application software for accessing websites. When a user requests a web page from a particular website, the browser retrieves its files from a web server and then displays the page on the user's screen. Browsers are used o ...
technology, allowing a malicious computer attack. Such attacks are most effective against computers that lack recent security patches. Others are designed for the purpose of a parody
A parody, also known as a spoof, a satire, a send-up, a take-off, a lampoon, a play on (something), or a caricature, is a creative work designed to imitate, comment on, and/or mock its subject by means of satiric or ironic imitation. Often its sub ...
.
During such an attack, a computer user innocently visits a website and sees a familiar URL in the address bar such as ''phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwa ...
.
The user is typically enticed to the false website from an email or a hyperlink from another website.
In another variation, a website may look like the original, but is in fact a parody
A parody, also known as a spoof, a satire, a send-up, a take-off, a lampoon, a play on (something), or a caricature, is a creative work designed to imitate, comment on, and/or mock its subject by means of satiric or ironic imitation. Often its sub ...
of it. These are mostly harmless, and are more noticeably different from the original, as they usually ''do not'' exploit bugs in web browser
A web browser is application software for accessing websites. When a user requests a web page from a particular website, the browser retrieves its files from a web server and then displays the page on the user's screen. Browsers are used o ...
technology.
Redirects can also take place in a hosts file
The computer file hosts is an operating system file that maps hostnames to IP addresses. It is a plain text file. Originally a file named HOSTS.TXT was manually maintained and made available via file sharing by Stanford Research Institute for the ...
, redirecting from legitimate site(s) to another IP, that of the spoofed URL.
Website spoofing – Using a fake website that looks legitimate or resembles a well-known website, hackers cheat users into entering their credentials or using the spoofed website, causing data theft.
Cyber security
Spoofing is the act of deception or hoaxing.URLs
A Uniform Resource Locator (URL), colloquially termed as a web address, is a reference to a web resource that specifies its location on a computer network and a mechanism for retrieving it. A URL is a specific type of Uniform Resource Identifi ...
are the address of a resource (as a document or website) on the Internet that consists of a communications protocol followed by the name or address of a computer on the network and that often includes additional locating information (as directory and file names). Simply, a spoofed URL is a web address that illuminates an immense amount of deception through its ability to appear as an original site, despite it not being one. In order to prevent falling victim to the prevalent scams stemmed from the spoofed URLs, major software
Software is a set of computer programs and associated software documentation, documentation and data (computing), data. This is in contrast to Computer hardware, hardware, from which the system is built and which actually performs the work.
...
companies have come forward and advised techniques to detect and prevent spoofed URLs.

Detection
In order to prevent criminals from accessing personal information, such as credit card information, bank account/routing numbers, and one’s telephone number, home address, etc. it is important to learn and understand how these spoof URLs can be detected. It is very important to first verify the name of the site on a digital certification through the use of SSL/TLS. Always try to identify the actual URL for the web page you are on. Make sure you are able to see the full URL for any hyperlink, so that you can examine the address. Some characters that are commonly found in spoofed URLs are: %00, %01, @. Sometimes the URLs can differ by a single letter or number. In addition, set your Internet security level to high to ensure that your computer is protected from possible attacks from spoofed sites. In general, only input personal information on a Website if the name has been verified on the digital certificate. Also, if you have any concern about the confidentiality of a website leave the page immediately.Prevention
Spoofed URLs, a universal defining identity forphishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwa ...
scams, pose a serious threat to end-users and commercial institutions. Email
Electronic mail (email or e-mail) is a method of exchanging messages ("mail") between people using electronic devices. Email was thus conceived as the electronic ( digital) version of, or counterpart to, mail, at a time when "mail" mean ...
continues to be the favorite vehicle to perpetrate such scams mainly due to its widespread use combined with the ability to easily spoof them. Several approaches, both generic and specialized, have been proposed to address this problem. However, phishing techniques, growing in ingenuity as well as sophistication, render these solutions weak. In order to prevent users from future victimization stemmed from a spoofed URL, Internet
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a '' network of networks'' that consists of private, pub ...
vigilantes
Vigilantism () is the act of preventing, investigating and punishing perceived offenses and crimes without legal authority.
A vigilante (from Spanish, Italian and Portuguese “vigilante”, which means "sentinel" or "watcher") is a person who ...
have published numerous tips to help users identify a spoof.  The most common are: using authentication based on key exchange between the machines on your
The most common are: using authentication based on key exchange between the machines on your network
Network, networking and networked may refer to:
Science and technology
* Network theory, the study of graphs as a representation of relations between discrete objects
* Network science, an academic field that studies complex networks
Mathematics ...
, using an access control list to deny private IP addresses on your downstream interface, implementing filter
Filter, filtering or filters may refer to:
Science and technology
Computing
* Filter (higher-order function), in functional programming
* Filter (software), a computer program to process a data stream
* Filter (video), a software component tha ...
s of both inbound and outbound traffic, configuring routers and switches if they support such configuration, to reject packets originating from outside the local network that claim to originate from within, and enable encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can de ...
sessions in the router so that trusted hosts that are outside your network can securely communicate with your local hosts. Ultimately, protection comes from the individual user. Keeping up with new spoofing techniques or scams will readily allow one to identify a scam and most importantly keep information secure and personal.
Susceptible targets
PayPal
PayPal Holdings, Inc. is an American multinational financial technology company operating an online payments system in the majority of countries that support online money transfers, and serves as an electronic alternative to traditional paper ...
, an e-commerce
E-commerce (electronic commerce) is the activity of electronically buying or selling of products on online services or over the Internet. E-commerce draws on technologies such as mobile commerce, electronic funds transfer, supply chain managem ...
business allows money transactions to be made through the Internet and is a common target for spoofed URLs. This forgery of a legitimate PayPal website allows hacker
A hacker is a person skilled in information technology who uses their technical knowledge to achieve a goal or overcome an obstacle, within a computerized system by non-standard means. Though the term ''hacker'' has become associated in popu ...
s to gain personal and financial information and thus, steal money through fraud. Along with spoof or fake emails that appear with generic greetings, misspellings, and a false sense of urgency, spoofed URLs are an easy way for hackers to violate one’s PayPal privacy. For example, www.paypalsecure.com, includes the name, but is a spoofed URL designed to deceive. Remember to always log into PayPal through a new window browser and never log in through email. In the case that you do receive a suspected spoofed URL, forward the entire email to spoof@PayPal.com to help prevent the URL from tricking other PayPal users.
Common crimes
A majorcrime
In ordinary language, a crime is an unlawful act punishable by a state or other authority. The term ''crime'' does not, in modern criminal law, have any simple and universally accepted definition,Farmer, Lindsay: "Crime, definitions of", in Ca ...
associated with spoofed URLs is identity theft
Identity theft occurs when someone uses another person's personal identifying information, like their name, identifying number, or credit card number, without their permission, to commit fraud or other crimes. The term ''identity theft'' was c ...
. The thief will create a website
A website (also written as a web site) is a collection of web pages and related content that is identified by a common domain name and published on at least one web server. Examples of notable websites are Google, Facebook, Amazon, and Wi ...
very similar in appearance to that of a popular site, then when a user accesses the spoofed URL, they can inadvertently give the thief their credit card
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt (i.e., promise to the card issuer to pay them for the amounts plus the o ...
and personal details. Their spoofed URLs might use “too good to be true” prices to lure more and more looking for a good deal. Crimes like these happen quite often, and most frequently during the festive holidays and other heavy online shopping periods of the year.
Another crime associated with spoofed URLs is setting up a fake anti-malware software. An example of this would be Ransomware, fake anti-malware software that locks up important files for the computer to run, and forces the user to pay a ransom to get the files back. If the user refuses to pay after a certain period of time, the Ransomware will delete the files from the computer, essentially making the computer unusable. Ads for these programs usually appear on popular websites, such as dating sites or social media sites like Facebook
Facebook is an online social media and social networking service owned by American company Meta Platforms. Founded in 2004 by Mark Zuckerberg with fellow Harvard College students and roommates Eduardo Saverin, Andrew McCollum, Dustin Mosk ...
and Twitter
Twitter is an online social media and social networking service owned and operated by American company Twitter, Inc., on which users post and interact with 280-character-long messages known as "tweets". Registered users can post, like, and ...
. They can also come in the form of attachments to emails.
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwa ...
scams are also another major way that users can get tricked into scams (see below).
Phishing
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwa ...
is a scam
A confidence trick is an attempt to defraud a person or group after first gaining their trust. Confidence tricks exploit victims using their credulity, naïveté, compassion, vanity, confidence, irresponsibility, and greed. Researchers hav ...
by which an e-mail
Electronic mail (email or e-mail) is a method of exchanging messages ("mail") between people using electronic devices. Email was thus conceived as the electronic (digital) version of, or counterpart to, mail, at a time when "mail" meant ...
user is duped into revealing personal or confidential information which the scammer can use illicitly. Phishing is the action of fraudsters sending an email to an individual, hoping to seek private information used for identity theft, by falsely asserting to be a reputable legal business. Phishing is performed through emails containing a spoofed URL, which links them to a website. Since it usually appears in the form on an email, it is crucial to not rely just on the address in the “from” field in order to prevent phishing. Computer users should also look out for spelling mistakes within the website's URLs, as this is another common sign to look out for in a phishing email. The website whose URLs are in the e-mails requests individuals to enter personal information so businesses can update it in their system. This information often includes passwords, credit card numbers, social security, and bank account numbers. In turn, the email recipients are giving these fake businesses their information the real businesses already have.
See also
*Computer insecurity
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, the ...
* Hosts File
The computer file hosts is an operating system file that maps hostnames to IP addresses. It is a plain text file. Originally a file named HOSTS.TXT was manually maintained and made available via file sharing by Stanford Research Institute for the ...
* IDN homograph attack
The internationalized domain name (IDN) homograph attack is a way a malicious party may deceive computer users about what remote system they are communicating with, by exploiting the fact that many different characters look alike (i.e., they ar ...
* Internet fraud prevention
Internet fraud prevention is the act of stopping various types of internet fraud. Due to the many different ways of committing fraud over the Internet, such as stolen credit cards, identity theft, phishing, and chargebacks, users of the Internet, ...
* Social engineering (computer security) Social engineering may refer to:
* Social engineering (political science), a means of influencing particular attitudes and social behaviors on a large scale
* Social engineering (security), obtaining confidential information by manipulating and/or ...
* Spoofing attack
In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage.
Internet Spoofing an ...
References
{{Scams and confidence tricks URL Web security exploits