Signature Record Type Definition on:
[Wikipedia]
[Google]
[Amazon]
In
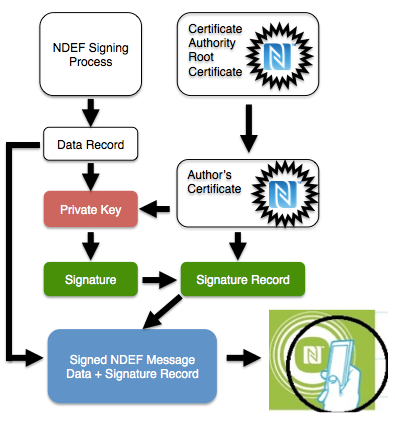 Referring to the diagrams. An author obtains a signing certificate from a valid certificate authority. The author's private key is used to sign the Data Record (text, URI, or whatever you like). The signature and author's certificate comprise the signature record. The Data Record and Signature Record are concatenated to produce the Signed NDEF Message that can be written to a standard NFC tag with sufficient memory (typically on the order of 300 to 500 bytes). The NDEF record remains in the clear (not encrypted) so any NFC tag reader will be able to read the signed data even if they cannot verify it.
Referring to the diagrams. An author obtains a signing certificate from a valid certificate authority. The author's private key is used to sign the Data Record (text, URI, or whatever you like). The signature and author's certificate comprise the signature record. The Data Record and Signature Record are concatenated to produce the Signed NDEF Message that can be written to a standard NFC tag with sufficient memory (typically on the order of 300 to 500 bytes). The NDEF record remains in the clear (not encrypted) so any NFC tag reader will be able to read the signed data even if they cannot verify it.
 Referring to the diagram. Upon reading the Signed NDEF Message, the Signature on the Data Record is first cryptographically verified using the author's public key (extracted from the Author's Certificate). Once verified, the Author's Certificate can be verified using the NFC Root Certificate. If both verifications are valid then one can trust the NDEF record and perform the desired operation.
Referring to the diagram. Upon reading the Signed NDEF Message, the Signature on the Data Record is first cryptographically verified using the author's public key (extracted from the Author's Certificate). Once verified, the Author's Certificate can be verified using the NFC Root Certificate. If both verifications are valid then one can trust the NDEF record and perform the desired operation.
Machine to Machine (M2M) Certificate format
The M2M Certificate format is a subset of X.509 designed for limited memory typically found on NFC tags. The author's certificate can optionally be replaced with a URI reference to that certificate or Certificate Chain so that messages can be cryptographically verified. The URI certificate reference designed to save memory for NFC tags.
near field communication
Near-field communication (NFC) is a set of communication protocols that enables communication between two electronic devices over a distance of 4 cm (1 in) or less. NFC offers a low-speed connection through a simple setup that can be u ...
s the NFC Forum Signature Record Type Definition (RTD) is a security protocol used to protect the integrity and authenticity of NDEF (NFC Data Exchange Format) Messages. The Signature RTD is an open interoperable specification modeled after Code signing
Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed. The process employs the use of a cryptographic hash to v ...
where the trust of signed messages is tied to digital certificate
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a public key. The certificate includes information about the key, information about the ...
s.
Signing NDEF records prevents malicious use of NFC tags (containing a protected NDEF record). For example, smartphone users tapping NFC tags containing URLs. Without some level of integrity protection an adversary could launch a phishing attack. Signing the NDEF record protects the integrity of the contents and allows the user to identify the signer if they wish. Signing certificates are obtained from third party Certificate Authorities and are governed by the NFC Forum Signature RTD Certificate Policy.
How it works
The NDEF signing process
 Referring to the diagrams. An author obtains a signing certificate from a valid certificate authority. The author's private key is used to sign the Data Record (text, URI, or whatever you like). The signature and author's certificate comprise the signature record. The Data Record and Signature Record are concatenated to produce the Signed NDEF Message that can be written to a standard NFC tag with sufficient memory (typically on the order of 300 to 500 bytes). The NDEF record remains in the clear (not encrypted) so any NFC tag reader will be able to read the signed data even if they cannot verify it.
Referring to the diagrams. An author obtains a signing certificate from a valid certificate authority. The author's private key is used to sign the Data Record (text, URI, or whatever you like). The signature and author's certificate comprise the signature record. The Data Record and Signature Record are concatenated to produce the Signed NDEF Message that can be written to a standard NFC tag with sufficient memory (typically on the order of 300 to 500 bytes). The NDEF record remains in the clear (not encrypted) so any NFC tag reader will be able to read the signed data even if they cannot verify it.
The NDEF Verification Process
 Referring to the diagram. Upon reading the Signed NDEF Message, the Signature on the Data Record is first cryptographically verified using the author's public key (extracted from the Author's Certificate). Once verified, the Author's Certificate can be verified using the NFC Root Certificate. If both verifications are valid then one can trust the NDEF record and perform the desired operation.
Referring to the diagram. Upon reading the Signed NDEF Message, the Signature on the Data Record is first cryptographically verified using the author's public key (extracted from the Author's Certificate). Once verified, the Author's Certificate can be verified using the NFC Root Certificate. If both verifications are valid then one can trust the NDEF record and perform the desired operation.
Supported certificate formats
The Signature RTD 2.0 supports two certificate formats. One being X.509 certificate format and the other thMachine to Machine (M2M) Certificate format
The M2M Certificate format is a subset of X.509 designed for limited memory typically found on NFC tags. The author's certificate can optionally be replaced with a URI reference to that certificate or Certificate Chain so that messages can be cryptographically verified. The URI certificate reference designed to save memory for NFC tags.
Supported cryptographic algorithms
The Signature RTD 2.0 uses industry standard digital signature algorithms. The following algorithms are supported:On the security of the Signature RTD
The Signature RTD 2.0's primary purpose is the protect the integrity and authenticity of NDEF records. Thus, NFC tag contents using the Signature RTD 2.0 is protected. The security of the system is tied to acertificate authority
In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. Thi ...
and the associated Certificate Chain. The NFC Forum Signature RTD Certificate Policy defines the policies under which certificate authorities can operate in the context of NFC. Root certificates are carried in verification devices and are not contained in the signature record. This separation is important for the security of the system just as web browser certificates are separated from web server certificates in TLS.
References
{{Reflist Cryptographic protocols