Relay attack on:
[Wikipedia]
[Google]
[Amazon]
 A relay attack (also known as the two-thief attack) in
A relay attack (also known as the two-thief attack) in
Academic Survey on Relay Attacks
* ttps://www.youtube.com/watch?v=VxeqiBG18xA Relay Attack Demonstration(and relate
Software
an
Paper
Practical Relay Attack on Contactless Transactions by Using NFC Mobile Phones
Hacking (computer security) Computer security exploits
 A relay attack (also known as the two-thief attack) in
A relay attack (also known as the two-thief attack) in computer security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, t ...
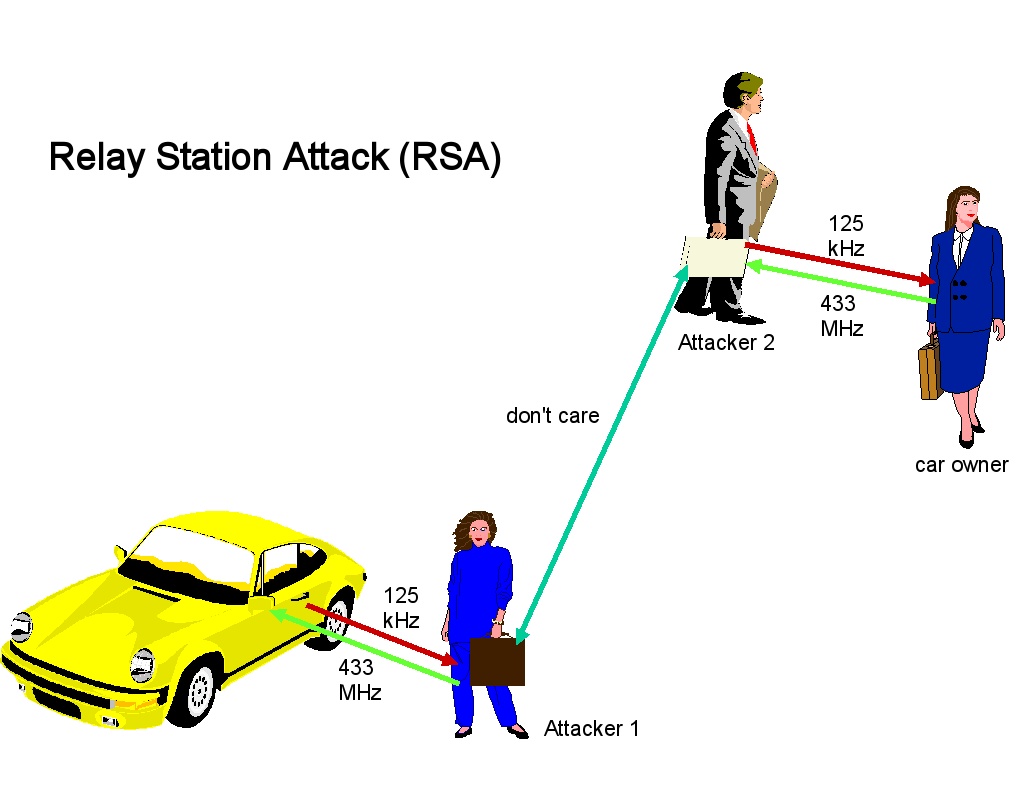
is a type of hacking technique related to man-in-the-middle and replay attacks. In a classic man-in-the-middle attack, an attacker intercepts and manipulates communications between two parties initiated by one of the parties. In a classic relay attack, communication with both parties is initiated by the attacker who then merely relays messages between the two parties without manipulating them or even necessarily reading them.
Example attack
Peggy works in a high security building that she accesses using a smart card in her purse. When she approaches the door of the building, the building detects the presence of a smart card and initiates an exchange of messages that constitute azero-knowledge password proof In cryptography, a zero-knowledge password proof (ZKPP) is a type of zero-knowledge proof that allows one party (the prover) to prove to another party (the verifier) that it knows a value of a password, without revealing anything other than the fac ...
that the card is Peggy's. The building then allows Peggy to enter.
Mallory wants to break into the building.
# Mallory approaches the building with a device that simulates a smart card, and the building responds by initiating the exchange of messages.
# Mallory forwards the message to her accomplice Evelyn who is tailing Peggy as she runs errands in another part of town.
# Evelyn relays the message to Peggy's smart card, listens for the answer, and forwards the answer to Mallory, who relays it to the building. Continuing in this way, Mallory and Evelyn relay messages between the building and Peggy's smart card until the building is satisfied that it is communicating with Peggy's smart card.
# The building opens and Mallory enters.
References
{{ReflistExternal links
Academic Survey on Relay Attacks
* ttps://www.youtube.com/watch?v=VxeqiBG18xA Relay Attack Demonstration(and relate
Software
an
Paper
Practical Relay Attack on Contactless Transactions by Using NFC Mobile Phones
Hacking (computer security) Computer security exploits