Information Awareness Office on:
[Wikipedia]
[Google]
[Amazon]
The Information Awareness Office (IAO) was established by the United States
''Electronic Privacy Information Center (EPIC)'' The program also included funding for
 The IAO was established after Admiral John Poindexter, former
The IAO was established after Admiral John Poindexter, former
 The Human Identification at a Distance (HumanID) project developed automated
The Human Identification at a Distance (HumanID) project developed automated
 Genisys aimed at developing technologies which would enable "ultra-large, all-source information repositories".
Vast amounts of information were going to be collected and analyzed, and the available
Genisys aimed at developing technologies which would enable "ultra-large, all-source information repositories".
Vast amounts of information were going to be collected and analyzed, and the available
/ref> The
 Translingual Information Detection, Extraction and Summarization (TIDES) developed advanced language processing technology to enable English speakers to find and interpret critical information in multiple languages without requiring knowledge of those languages.
Outside groups (such as universities, corporations, etc.) were invited to participate in the annual
Translingual Information Detection, Extraction and Summarization (TIDES) developed advanced language processing technology to enable English speakers to find and interpret critical information in multiple languages without requiring knowledge of those languages.
Outside groups (such as universities, corporations, etc.) were invited to participate in the annual
 Effective Affordable Reusable Speech-to-text (EARS) developed automatic speech-to-text transcription technology whose output is substantially richer and much more accurate than previously possible. The aim of EARS was to focus on everyday human-to-human speech from broadcasts and telephone conversations in multiple languages. It is expected to increase the speed with which speech can be processed by computers by 100 times or more.
The intent is to create a core enabling technology (technology that is used as a component for future technologies) suitable for a wide range of future surveillance applications.
Effective Affordable Reusable Speech-to-text (EARS) developed automatic speech-to-text transcription technology whose output is substantially richer and much more accurate than previously possible. The aim of EARS was to focus on everyday human-to-human speech from broadcasts and telephone conversations in multiple languages. It is expected to increase the speed with which speech can be processed by computers by 100 times or more.
The intent is to create a core enabling technology (technology that is used as a component for future technologies) suitable for a wide range of future surveillance applications.
Big Brother ...
/ref>
Overview of the Information Awareness Office
(Remarks as prepared for delivery by Dr. John Poindexter, Director, Information Awareness Office, at the DARPATech 2002 Conference) (August 2, 2002).
Information Awareness Office
Defense Advanced Research Projects Agency
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military.
Originally known as the Adv ...
(DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as ...
and information technology to track and monitor terrorists and other asymmetric threats to U.S. national security
National security, or national defence, is the security and defence of a sovereign state, including its citizens, economy, and institutions, which is regarded as a duty of government. Originally conceived as protection against military att ...
by achieving "Total Information Awareness
Total Information Awareness (TIA) was a mass detection program by the United States Information Awareness Office. It operated under this title from February to May 2003 before being renamed Terrorism Information Awareness.
Based on the concep ...
" (TIA).
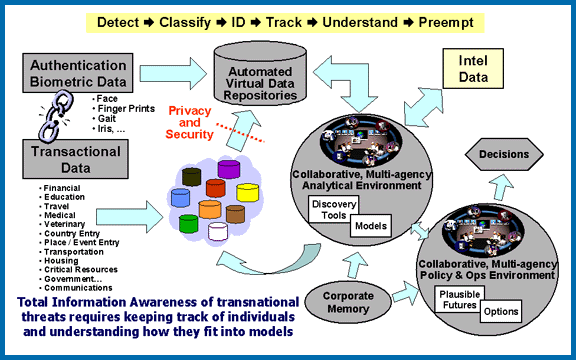
It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant
A search warrant is a court order that a magistrate or judge issues to authorize law enforcement officers to conduct a search of a person, location, or vehicle for evidence of a crime and to confiscate any evidence they find. In most countries, ...
. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Awareness (TIA)''Electronic Privacy Information Center (EPIC)'' The program also included funding for
biometric surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as c ...
technologies that could identify and track individuals using surveillance cameras and other methods.
Following public criticism that the technology's development and deployment could lead to a mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizati ...
system, the IAO was defunded by Congress
A congress is a formal meeting of the representatives of different countries, constituent states, organizations, trade unions, political parties, or other groups. The term originated in Late Middle English to denote an encounter (meeting of ...
in 2003. However, several IAO projects continued to be funded under different names, as revealed by Edward Snowden
Edward Joseph Snowden (born June 21, 1983) is an American and naturalized Russian former computer intelligence consultant who leaked highly classified information from the National Security Agency (NSA) in 2013, when he was an employee and su ...
during the course of the 2013 mass surveillance disclosures
Thirteen or 13 may refer to:
* 13 (number), the natural number following 12 and preceding 14
* One of the years 13 BC, AD 13, 1913, 2013
Music
* 13AD (band), an Indian classic and hard rock band
Albums
* ''13'' (Black Sabbath album), 2013
* ...
.
History
 The IAO was established after Admiral John Poindexter, former
The IAO was established after Admiral John Poindexter, former United States National Security Advisor
The Assistant to the President for National Security Affairs (APNSA), commonly referred to as the National Security Advisor (NSA),The National Security Advisor and Staff: p. 1. is a senior aide in the Executive Office of the President, based at ...
to President Ronald Reagan
Ronald Wilson Reagan ( ; February 6, 1911June 5, 2004) was an American politician, actor, and union leader who served as the 40th president of the United States from 1981 to 1989. He also served as the 33rd governor of California from 1967 ...
, and SAIC executive Brian Hicks approached the US Department of Defense
The United States Department of Defense (DoD, USDOD or DOD) is an executive branch department of the federal government charged with coordinating and supervising all agencies and functions of the government directly related to national sec ...
with the idea for an information awareness program after the attacks of September 11, 2001
The September 11 attacks, commonly known as 9/11, were four coordinated suicide terrorist attacks carried out by al-Qaeda against the United States on Tuesday, September 11, 2001. That morning, nineteen terrorists hijacked four commerc ...
.
Poindexter and Hicks had previously worked together on intelligence-technology programs for the Defense Advanced Research Projects Agency. DARPA agreed to host the program and appointed Poindexter to run it in 2002.
The IAO began funding research and development of the Total Information Awareness
Total Information Awareness (TIA) was a mass detection program by the United States Information Awareness Office. It operated under this title from February to May 2003 before being renamed Terrorism Information Awareness.
Based on the concep ...
(TIA) Program in February 2003 but renamed the program the ''Terrorism'' Information Awareness Program in May that year after an adverse media reaction to the program's implications for public surveillance. Although TIA was only one of several IAO projects, many critics and news reports conflated TIA with other related research projects of the IAO, with the result that TIA came in popular usage to stand for an entire subset of IAO programs.
The TIA program itself was the "systems-level" program of the IAO that intended to integrate information technologies into a prototype system to provide tools to better detect, classify, and identify potential terrorists with the goal to increase the probability that authorized agencies of the United States could preempt adverse actions.
As a systems-level program of programs, TIA's goal was the creation of a "counter-terrorism information architecture" that integrated technologies from other IAO programs (and elsewhere, as appropriate). The TIA program was researching, developing, and integrating technologies to virtually aggregate data, to follow subject-oriented link analysis, to develop descriptive and predictive models through data mining or human hypothesis, and to apply such models to additional datasets to identify terrorists and terrorist groups.
Among the other IAO programs that were intended to provide TIA with component data aggregation and automated analysis technologies were the Genisys, Genisys Privacy Protection, Evidence Extraction and Link Discovery, and Scalable Social Network Analysis programs.
On August 2, 2002, Dr. Poindexter gave a speech at DARPAtech 2002 entitled "Overview of the Information Awareness Office" in which he described the TIA program.
In addition to the program itself, the involvement of Poindexter as director of the IAO also raised concerns among some, since he had been earlier convicted of lying to Congress and altering and destroying documents pertaining to the Iran-Contra Affair, although those convictions were later overturned on the grounds that the testimony used against him was protected.
On January 16, 2003, Senator Russ Feingold
Russell Dana Feingold ( ; born March 2, 1953) is an American lawyer and politician who served as a United States Senator from Wisconsin from 1993 to 2011. A member of the Democratic Party, he was its nominee in the 2016 election for the same U ...
introduced legislation to suspend the activity of the IAO and the Total Information Awareness program pending a Congressional review of privacy issues involved. A similar measure introduced by Senator Ron Wyden
Ronald Lee Wyden (; born May 3, 1949) is an American politician and retired educator serving as the senior United States senator from Oregon, a seat he has held since 1996. A member of the Democratic Party, he served in the United States Hou ...
would have prohibited the IAO from operating within the United States unless specifically authorized to do so by Congress, and would have shut the IAO down entirely 60 days after passage unless either the Pentagon prepared a report to Congress assessing the impact of IAO activities on individual privacy and civil liberties or the President certified the program's research as vital to national security interests. In February 2003, Congress passed legislation suspending activities of the IAO pending a Congressional report of the office's activities (Consolidated Appropriations Resolution, 2003, No.108–7, Division M, §111(b) igned Feb. 20, 2003.
In response to this legislation, DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military.
Originally known as the A ...
provided Congress on May 20, 2003 with a report on its activities. In this report, IAO changed the name of the program to the ''Terrorism'' Information Awareness Program and emphasized that the program was not designed to compile dossiers on US citizens, but rather to research and develop the tools that would allow authorized agencies to gather information on terrorist networks. Despite the name change and these assurances, the critics continued to see the system as prone to potential misuse or abuse.
As a result, House and Senate negotiators moved to prohibit further funding for the TIA program by adding provisions to the Department of Defense Appropriations Act, 2004 (signed into law by President Bush on October 1, 2003). Further, the Joint Explanatory Statement included in the conference committee report specifically directed that the IAO as program manager for TIA be terminated immediately.
Research
IAO research was conducted along five major investigative paths: secure collaboration problem solving; structured discovery; link and group understanding; context aware visualization; and decision making with corporate memory. Among the IAO projects were:Human Identification at a Distance (HumanID)
 The Human Identification at a Distance (HumanID) project developed automated
The Human Identification at a Distance (HumanID) project developed automated biometric
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify in ...
identification technologies to detect, recognize and identify humans at great distances for "force protection", crime prevention, and "homeland security/defense" purposes.
Its goals included programs to:
* Develop algorithms for locating and acquiring subjects out to 150 meters (500 ft) in range.
* Fuse face and gait
Gait is the pattern of movement of the limbs of animals, including humans, during locomotion over a solid substrate. Most animals use a variety of gaits, selecting gait based on speed, terrain, the need to maneuver, and energetic efficiency. ...
recognition into a 24/7 human identification system.
* Develop and demonstrate a human identification system that operates out to 150 meters (500 ft) using visible imagery.
* Develop a low power millimeter wave radar system for wide field of view detection and narrow field of view gait classification.
* Characterize gait performance from video for human identification at a distance.
* Develop a multi-spectral infrared and visible facial recognition system
A facial recognition system is a technology capable of matching a human face from a digital image or a video frame against a database of faces. Such a system is typically employed to authenticate users through ID verification services, and ...
.
Evidence Extraction and Link Discovery
Evidence Extraction and Link Discovery (EELD) developed technologies and tools for automated discovery, extraction and linking of sparse evidence contained in large amounts of classified and unclassified data sources (such as phone call records from theNSA call database
MAINWAY is a database maintained by the United States' National Security Agency (NSA) containing metadata for hundreds of billions of telephone calls made through the largest telephone carriers in the United States, including AT&T, Verizon, ...
, internet histories, or bank records).
EELD was designed to design systems with the ability to extract data from multiple sources (e.g., text messages, social networking sites, financial records, and web pages). It was to develop the ability to detect patterns comprising multiple types of links between data items or people communicating (e.g., financial transactions, communications, travel, etc.).
It is designed to link items relating potential "terrorist" groups and scenarios, and to learn patterns of different groups or scenarios to identify new organizations and emerging threats.
Genisys
 Genisys aimed at developing technologies which would enable "ultra-large, all-source information repositories".
Vast amounts of information were going to be collected and analyzed, and the available
Genisys aimed at developing technologies which would enable "ultra-large, all-source information repositories".
Vast amounts of information were going to be collected and analyzed, and the available database
In computing, a database is an organized collection of data stored and accessed electronically. Small databases can be stored on a file system, while large databases are hosted on computer clusters or cloud storage. The design of databases ...
technology at the time was insufficient for storing and organizing such enormous quantities of data. So they developed techniques for virtual data aggregation in order to support effective analysis across heterogeneous databases, as well as unstructured public data sources, such as the World Wide Web. "Effective analysis across heterogenous databases" means the ability to take things from databases which are designed to store different types of data—such as a database containing criminal records, a phone call database and a foreign intelligence database. The World Wide Web is considered an "unstructured public data source" because it is publicly accessible and contains many different types of data—such as blogs, emails, records of visits to web sites, etc.—all of which need to be analyzed and stored efficiently.
Another goal was to develop "a large, distributed system architecture for managing the huge volume of raw data input, analysis results, and feedback, that will result in a simpler, more flexible data store that performs well and allows us to retain important data indefinitely."
Genisys had an internal "Privacy Protection Program." It was intended to restrict analysts' access to irrelevant information on private U.S. citizens, enforce privacy law
Privacy law is the body of law that deals with the regulating, storing, and using of personally identifiable information, personal healthcare information, and financial information of individuals, which can be collected by governments, public o ...
s and policies via software mechanisms, and report misuse of data.
Scalable Social Network Analysis
Scalable Social Network Analysis (SSNA) aimed at developing techniques based onsocial network analysis
Social network analysis (SNA) is the process of investigating social structures through the use of networks and graph theory. It characterizes networked structures in terms of ''nodes'' (individual actors, people, or things within the network) ...
for modeling the key characteristics of terrorist groups and discriminating these groups from other types of societal groups.
Sean McGahan, of Northeastern University
Northeastern University (NU) is a private research university with its main campus in Boston. Established in 1898, the university offers undergraduate and graduate programs on its main campus as well as satellite campuses in Charlotte, North Ca ...
said the following in his study of SSNA:
Futures Markets Applied to Prediction (FutureMAP)
Futures Markets Applied to Prediction (FutureMAP) was intended to harnesscollective intelligence
Collective intelligence (CI) is shared or group intelligence (GI) that emerges from the collaboration, collective efforts, and competition of many individuals and appears in consensus decision making. The term appears in sociobiology, politi ...
by researching prediction market
Prediction markets (also known as betting markets, information markets, decision markets, idea futures or event derivatives) are open markets where specific outcomes can be predicted using financial incentives. Essentially, they are exchange-trad ...
techniques for avoiding surprise and predicting future events. The intent was to explore the feasibility of market-based trading mechanisms to predict political instability, threats to national security, and other major events in the near future. In laymans terms, FutureMap would be a website that allowed people to bet on when a terrorist attack would occur.CNN/ref> The
bookmaker
A bookmaker, bookie, or turf accountant is an organization or a person that accepts and pays off bets on sporting and other events at agreed-upon odds.
History
The first bookmaker, Ogden, stood at Newmarket in 1795.
Range of events
Bookm ...
would have been the federal government. Several Senators were outraged at the very notion of such a program. Then Senate Minority Leader Tom Daschle
Thomas Andrew Daschle ( ; born December 9, 1947) is an American politician and lobbyist who served as a United States senator from South Dakota from 1987 to 2005. A member of the Democratic Party, he became U.S. Senate Minority Leader in 1995 a ...
said on the floor of the Senate "I couldn't believe that we would actually commit $8 million to create a Web site that would encourage investors to bet on futures involving terrorist attacks and public assassinations. ... I can't believe that anybody would seriously propose that we trade in death. ... How long would it be before you saw traders investing in a way that would bring about the desired result?" Democratic Senator from Oregon
Oregon () is a U.S. state, state in the Pacific Northwest region of the Western United States. The Columbia River delineates much of Oregon's northern boundary with Washington (state), Washington, while the Snake River delineates much of it ...
, Ron Wyden said, "The idea of a federal betting parlor on atrocities and terrorism is ridiculous and it's grotesque." The ranking Democrat on the Armed Services Committee, Sen. Carl Levin
Carl Milton Levin (June 28, 1934 – July 29, 2021) was an American attorney and politician who served as a United States senator from Michigan from 1979 to 2015. A member of the Democratic Party, he was the chair of the Senate Armed Services ...
of Michigan, thought the program was so ridiculous that he thought initial reports of it were the result of a hoax. The program was then dropped.
TIDES
 Translingual Information Detection, Extraction and Summarization (TIDES) developed advanced language processing technology to enable English speakers to find and interpret critical information in multiple languages without requiring knowledge of those languages.
Outside groups (such as universities, corporations, etc.) were invited to participate in the annual
Translingual Information Detection, Extraction and Summarization (TIDES) developed advanced language processing technology to enable English speakers to find and interpret critical information in multiple languages without requiring knowledge of those languages.
Outside groups (such as universities, corporations, etc.) were invited to participate in the annual information retrieval
Information retrieval (IR) in computing and information science is the process of obtaining information system resources that are relevant to an information need from a collection of those resources. Searches can be based on full-text or other c ...
, topic detection and tracking, automatic content extraction, and machine translation
Machine translation, sometimes referred to by the abbreviation MT (not to be confused with computer-aided translation, machine-aided human translation or interactive translation), is a sub-field of computational linguistics that investigates ...
evaluations run by NIST
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into physical sci ...
.
Genoa / Genoa II
Genoa
Genoa ( ; it, Genova ; lij, Zêna ). is the capital of the Italian region of Liguria and the sixth-largest city in Italy. In 2015, 594,733 people lived within the city's administrative limits. As of the 2011 Italian census, the Province of ...
and Genoa II focused on providing advanced decision-support and collaboration tools to rapidly deal with and adjust to dynamic crisis management and allow for inter-agency collaboration in real-time. Another function was to be able to make estimates of possible future scenarios to assist intelligence officials in deciding what to do, in a manner similar to the DARPA's Deep Green
Deep Green is a project that ran under the Information Processing Technology Office of the Defense Advanced Research Projects Agency. The purpose of the project was to develop a decision-making support system for United States Army commanders. Th ...
program which is designed to assist Army commanders in making battlefield decisions.
Wargaming the Asymmetric Environment (WAE)
Wargaming the Asymmetric Environment (WAE) focused on developing automated technology capable of identifying predictive indicators of terrorist activity or impending attacks by examining individual and group behavior in broad environmental context and examining the motivation of specific terrorists.Effective Affordable Reusable Speech-to-text (EARS)
 Effective Affordable Reusable Speech-to-text (EARS) developed automatic speech-to-text transcription technology whose output is substantially richer and much more accurate than previously possible. The aim of EARS was to focus on everyday human-to-human speech from broadcasts and telephone conversations in multiple languages. It is expected to increase the speed with which speech can be processed by computers by 100 times or more.
The intent is to create a core enabling technology (technology that is used as a component for future technologies) suitable for a wide range of future surveillance applications.
Effective Affordable Reusable Speech-to-text (EARS) developed automatic speech-to-text transcription technology whose output is substantially richer and much more accurate than previously possible. The aim of EARS was to focus on everyday human-to-human speech from broadcasts and telephone conversations in multiple languages. It is expected to increase the speed with which speech can be processed by computers by 100 times or more.
The intent is to create a core enabling technology (technology that is used as a component for future technologies) suitable for a wide range of future surveillance applications.
Babylon
Babylon aimed to develop rapid, two-way, natural language speech translation interfaces and platforms. Its goal was to help the warfighter in field environments to complete tasks such as force protection, refugee processing, and medicaltriage
In medicine, triage () is a practice invoked when acute care cannot be provided for lack of resources. The process rations care towards those who are most in need of immediate care, and who benefit most from it. More generally it refers to prio ...
.
Bio-Surveillance
Bio-Surveillance aimed to develop the necessary information technologies and resulting prototype capable of detecting the covert release of a biological pathogen automatically, and significantly earlier than traditional approaches.Communicator
Communicator was to develop "dialogue interaction" technology that enables warfighters to talk with computers, such that information will be accessible on the battlefield or in command centers without ever having to touch a keyboard. The Communicator Platform was to be both wireless and mobile, and to be designed to function in a networked environment. The dialogue interaction software was to interpret the ''context'' of the dialogue in order to improve performance, and to be capable of automatically adapting to new topics (because situations quickly change in war) so conversation is natural and efficient. The Communicator program emphasized task knowledge to compensate for natural language effects and noisy environments. Unlike automated translation ofnatural language
In neuropsychology, linguistics, and philosophy of language, a natural language or ordinary language is any language that has evolved naturally in humans through use and repetition without conscious planning or premeditation. Natural languages ...
speech, which is much more complex due to an essentially unlimited vocabulary and grammar, the Communicator program is directed task specific issues so that there are constrained vocabularies (the system only needs to be able to understand language related to war). Research was also started to focus on foreign language computer interaction for use in supporting coalition operations.
Live exercises were conducted involving small unit logistics operations involving the United States Marines
The United States Marine Corps (USMC), also referred to as the United States Marines, is the maritime land force service branch of the United States Armed Forces responsible for conducting expeditionary and amphibious operations through com ...
to test the technology in extreme environments.
Components of TIA projects that continue to be developed
Despite the withdrawal of funding for the TIA and the closing of the IAO, the core of the project survived. Legislators included a classified annex to the Defense Appropriations Act that preserved funding for TIA's component technologies, if they were transferred to other government agencies. TIA projects continued to be funded under classified annexes to Defense and Intelligence appropriation bills. However, the act also stipulated that the technologies be used only for military or foreign intelligence purposes involving foreigners. TIA's two core projects are now operated by Advanced Research and Development Activity (ARDA) located among the 60-odd buildings of "Crypto City" at NSA headquarters in Fort Meade, MD. ARDA itself has been shifted from the NSA to theDisruptive Technology Office
The Disruptive Technology Office (DTO) was a funding agency within the United States Intelligence Community. It was previously known as the Advanced Research and Development Activity (ARDA). In December 2007, DTO was folded into the newly created ...
(run by the Director of National Intelligence
The director of national intelligence (DNI) is a senior, cabinet-level United States government official, required by the Intelligence Reform and Terrorism Prevention Act of 2004 to serve as executive head of the United States Intelligence Co ...
). They are funded by National Foreign Intelligence Program for foreign counterterrorism intelligence purposes.
One technology, codenamed "Basketball", is the Information Awareness Prototype System, the core architecture to integrate all the TIA's information extraction, analysis, and dissemination tools. Work on this project is conducted by SAIC through its former Hicks & Associates consulting arm, and run by former Defense and military officials and which had originally been awarded US$19 million IAO contract to build the prototype system in late 2002.
The other project has been re-designated "Topsail" (formerly Genoa II) and would provide IT tools to help anticipate and preempt terrorist attacks. SAIC has also been contracted to work on Topsail, including a US$3.7 million contract in 2005.
Media coverage and criticism
The first mention of the IAO in themainstream media
In journalism, mainstream media (MSM) is a term and abbreviation used to refer collectively to the various large mass news media that influence many people and both reflect and shape prevailing currents of thought. Chomsky, Noam, ''"What makes ma ...
came from ''The New York Times
''The New York Times'' (''the Times'', ''NYT'', or the Gray Lady) is a daily newspaper based in New York City with a worldwide readership reported in 2020 to comprise a declining 840,000 paid print subscribers, and a growing 6 million paid ...
'' reporter John Markoff
John Gregory Markoff (born October 24, 1949) is a journalist best known for his work covering technology at '' The New York Times'' for 28 years until his retirement in 2016, and a book and series of articles about the 1990s pursuit and captur ...
on February 13, 2002. Initial reports contained few details about the program. In the following months, as more information emerged about the scope of the TIA project, civil libertarians became concerned over what they saw as the potential for the development of an Orwellian
"Orwellian" is an adjective describing a situation, idea, or societal condition that George Orwell identified as being destructive to the welfare of a free and open society. It denotes an attitude and a brutal policy of draconian control by pro ...
mass surveillance system.
On November 14, 2002, ''The New York Times'' published a column by William Safire
William Lewis Safire (; Safir; December 17, 1929 – September 27, 2009Safire, William (1986). ''Take My Word for It: More on Language.'' Times Books. . p. 185.) was an American author, columnist, journalist, and presidential speechwriter. He ...
in which he claimed " IAhas been given a $200 million budget to create computer dossiers on 300 million Americans." Safire has been credited with triggering the anti-TIA movement./ref>
See also
*ADVISE
ADVISE (Analysis, Dissemination, Visualization, Insight, and Semantic Enhancement) is a research and development program within the United States Department of Homeland Security (DHS) Threat and Vulnerability Testing and Assessment (TVTA) portfoli ...
, full population data mining & analysis to "monitor social threats"
* Carnivore
A carnivore , or meat-eater (Latin, ''caro'', genitive ''carnis'', meaning meat or "flesh" and ''vorare'' meaning "to devour"), is an animal or plant whose food and energy requirements derive from animal tissues (mainly muscle, fat and other s ...
, FBI US digital interception program
* Combat Zones That See, or CTS, a project to link up all security cameras citywide and "track everything that moves".
* Communications Assistance For Law Enforcement Act
* ECHELON
ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the five signatory states to the UKUSA Security Agreement:Given the 5 dialects that use ...
, NSA worldwide digital interception program
* Fusion center
In the United States, fusion centers are designed to promote information sharing at the federal level between agencies such as the Federal Bureau of Investigation, the U.S. Department of Homeland Security, the U.S. Department of Justice, and st ...
* Government Information Awareness
* Information Processing Technology Office
The Information Processing Techniques Office (IPTO), originally "Command and Control Research",Lyon, Matthew; Hafner, Katie (1999-08-19). ''Where Wizards Stay Up Late: The Origins Of The Internet'' (p. 39). Simon & Schuster. Kindle Edition. was par ...
* Intellipedia
Intellipedia is an online system for collaborative data sharing used by the United States Intelligence Community (IC). It was established as a pilot project in late 2005 and formally announced in April 2006. Intellipedia consists of three w ...
, a collection of wikis used by the U.S. intelligence community to "connect the dots" between pieces of intelligence
* MALINTENT MALINTENT is a technological system that was developed by the U.S. Department of Homeland Security to be implemented for detection of potential terrorist suspects.
The system does various test scanning for elevated blood pressure, rapid heart and ...
—similar program to HumanID
* Mass surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizati ...
* Multistate Anti-Terrorism Information Exchange
* Pre-crime
''Pre-crime'' (or ''precrime'') is the idea that the occurrence of a crime can be anticipated before it happens. The term was coined by science fiction author Philip K. Dick, and is increasingly used in academic literature to describe and critici ...
concept in criminology
* PRISM (surveillance program)
Prism usually refers to:
* Prism (optics), a transparent optical component with flat surfaces that refract light
* Prism (geometry), a kind of polyhedron
Prism may also refer to:
Science and mathematics
* Prism (geology), a type of sedimentary ...
* Synthetic Environment for Analysis and Simulations
* TALON (database)
* Utah Data Center
References
Further reading
* Copies of the original IAO web pages formerly available at https://web.archive.org/web/20021123234437/http://www.darpa.mil/iao/ (June 12, 2002 – June 3, 2003) can be found at * John PoindexterOverview of the Information Awareness Office
(Remarks as prepared for delivery by Dr. John Poindexter, Director, Information Awareness Office, at the DARPATech 2002 Conference) (August 2, 2002).
External links
Information Awareness Office
Media coverage
* * * * * *Academic articles
* *Critical views
* * * * * *Proponent views
* * * Accord: * * Also: *{{cite news , first= David , last= Ignatius , pages=A19 (discussing opposition to the IAO FutureMap project) , title=Back in the Safe Zone , date=August 1, 2003 , newspaper=The Washington Post , url=https://www.washingtonpost.com/wp-dyn/articles/A10955-2003Jul31.html DARPA offices Government databases in the United States Mass surveillance 2002 establishments in the United States Organizations established in 2002