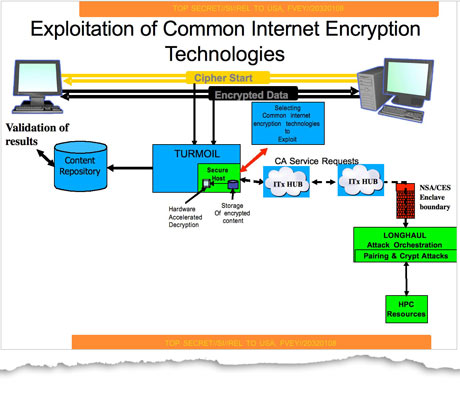
|
Dual EC DRBG
Dual_EC_DRBG (Dual Elliptic Curve Deterministic Random Bit Generator) is an algorithm that was presented as a cryptographically secure pseudorandom number generator (CSPRNG) using methods in elliptic curve cryptography. Despite wide public criticism, including the public identification of a backdoor, it was for seven years one of four CSPRNGs standardized in NIST SP 800-90A as originally published circa June 2006, until it was withdrawn in 2014. Weakness: a potential backdoor Weaknesses in the cryptographic security of the algorithm were known and publicly criticised well before the algorithm became part of a formal standard endorsed by the ANSI, ISO, and formerly by the National Institute of Standards and Technology (NIST). One of the weaknesses publicly identified was the potential of the algorithm to harbour a kleptographic backdoor advantageous to those who know about it—the United States government's National Security Agency (NSA)—and no one else. In 2013, ''Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSA Security
RSA Security LLC, formerly RSA Security, Inc. and doing business as RSA, is an American computer and network security company with a focus on encryption and encryption standards. RSA was named after the initials of its co-founders, Ron Rivest, Adi Shamir and Leonard Adleman, after whom the RSA public key cryptography algorithm was also named. Among its products is the SecurID authentication token. The BSAFE cryptography libraries were also initially owned by RSA. RSA is known for incorporating backdoors developed by the NSA in its products. It also organizes the annual RSA Conference, an information security conference. Founded as an independent company in 1982, RSA Security was acquired by EMC Corporation in 2006 for US$2.1 billion and operated as a division within EMC. When EMC was acquired by Dell Technologies in 2016, RSA became part of the Dell Technologies family of brands. On 10 March 2020, Dell Technologies announced that they will be selling RSA Security to a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NIST SP 800-90A
NIST SP 800-90A ("SP" stands for "''special publication''") is a publication by the National Institute of Standards and Technology with the title ''Recommendation for Random Number Generation Using Deterministic Random Bit Generators''. The publication contains the specification for three allegedly cryptographically secure pseudorandom number generators for use in cryptography: Hash DRBG (based on hash functions), HMAC DRBG (based on HMAC), and CTR DRBG (based on block ciphers in counter mode). Since June 24, 2015, the current version of the publication is Revision 1. Earlier versions included a fourth generator, Dual_EC_DRBG (based on elliptic curve cryptography). Dual_EC_DRBG was later reported to probably contain a kleptographic backdoor inserted by the United States National Security Agency (NSA), while the other three random number generators are accepted as uncontroversial and secure by multiple cryptographers. As a work of the US Federal Government, NIST SP 800-90A is i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSA BSAFE
Dell BSAFE, formerly known as RSA BSAFE, is a FIPS 140-2 validated cryptography library, available in both C and Java. BSAFE was initially created by RSA Security, which was purchased by EMC and then, in turn, by Dell. When Dell sold the RSA business to Symphony Technology Group in 2020, Dell elected to retain the BSAFE product line. BSAFE was one of the most common encryption toolkits before the RSA patent expired in September 2000. It also contained implementations of the RC''x'' ciphers, with the most common one being RC4. From 2004 to 2013 the default random number generator in the library was a NIST-approved RNG standard, widely known to be insecure from at least 2006, containing a kleptographic backdoor from the American National Security Agency (NSA), as part of its secret Bullrun program. In 2013 Reuters revealed that RSA had received a payment of $10 million to set the compromised algorithm as the default option. The RNG standard was subsequently withdrawn in 2014, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographically Secure Pseudorandom Number Generator
A cryptographically secure pseudorandom number generator (CSPRNG) or cryptographic pseudorandom number generator (CPRNG) is a pseudorandom number generator (PRNG) with properties that make it suitable for use in cryptography. It is also loosely known as a cryptographic random number generator (CRNG) (see Random number generation § "True" vs. pseudo-random numbers). Most cryptographic applications require random numbers, for example: * key generation * nonces * salts in certain signature schemes, including ECDSA, RSASSA-PSS The "quality" of the randomness required for these applications varies. For example, creating a nonce in some protocols needs only uniqueness. On the other hand, the generation of a master key requires a higher quality, such as more entropy. And in the case of one-time pads, the information-theoretic guarantee of perfect secrecy only holds if the key material comes from a true random source with high entropy, and thus any kind of pseudorandom number gen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kleptographic
Kleptography is the study of stealing information securely and subliminally. The term was introduced by Adam Young and Moti Yung in the Proceedings of Advances in Cryptology—Crypto '96.A. Young, M. Yung, "The Dark Side of Black-Box Cryptography, or: Should we trust Capstone?" In Proceedings of Crypto '96, Neal Koblitz (Ed.), Springer-Verlag, pages 89–103, 1996. Kleptography is a subfield of cryptovirology and is a natural extension of the theory of subliminal channels that was pioneered by Gus Simmons while at Sandia National Laboratory. G. J. Simmons, "The Prisoners' Problem and the Subliminal Channel," In Proceedings of Crypto '83, D. Chaum (Ed.), pages 51–67, Plenum Press, 1984.G. J. Simmons, "The Subliminal Channel and Digital Signatures," In Proceedings of Eurocrypt '84, T. Beth, N. Cot, I. Ingemarsson (Eds.), pages 364-378, Springer-Verlag, 1985.G. J. Simmons, "Subliminal Communication is Easy Using the DSA," In proceedings of Eurocrypt '93, T. Helleseth (Ed.), page ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Elliptic Curve Cryptography
Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC allows smaller keys compared to non-EC cryptography (based on plain Galois fields) to provide equivalent security.Commercial National Security Algorithm Suite and Quantum Computing FAQ U.S. National Security Agency, January 2016. Elliptic curves are applicable for key agreement, digital signatures, [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bullrun Program
Bullrun (stylized BULLRUN) is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States National Security Agency (NSA). The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the Bullrun classification guide published by ''The Guardian'', the program uses multiple methods including computer network exploitation, interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques. Information about the program's existence was leaked in 2013 by Edward Snowden. Although Snowden's documents do not contain technical information on exact cryptanalytic capabilities because Snowden did not have clearance access to such information, they do contain a 2010 GCHQ presentation which claims that "vast amounts of encrypted Internet data which have up till now been discarded are now exploitable". A n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bullrun (decryption Program)
Bullrun (stylized BULLRUN) is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States National Security Agency (NSA). The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the Bullrun classification guide published by ''The Guardian'', the program uses multiple methods including computer network exploitation, interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques. Information about the program's existence was leaked in 2013 by Edward Snowden. Although Snowden's documents do not contain technical information on exact cryptanalytic capabilities because Snowden did not have clearance access to such information, they do contain a 2010 GCHQ presentation which claims that "vast amounts of encrypted Internet data which have up till now been discarded are now exploitable". A num ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dan Shumow
Dan Shumow is a cryptographer working at Microsoft Research. At the CRYPTO 2007 conference rump session, Dan Shumow and Niels Ferguson presented an informal paper describing a kleptographic backdoor in the NIST specified Dual_EC_DRBG cryptographically secure pseudorandom number generator. The backdoor was confirmed to be real in 2013 as part of the Edward Snowden leaks. Dan Shumow co-authored an algorithm for detecting SHA-1 collisions with Marc Stevens, prior to the demonstration of a SHA-1 In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographically broken but still widely used hash function which takes an input and produces a 160- bit (20- byte) hash value known as a message digest – typically rendered as 40 hexa ... collision.http://shattered.io References External links Dan Shumow- Microsoft Research Modern cryptographers Living people Year of birth missing (living people) Place of birth missing (living people) Microsoft Research people ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Niels Ferguson
Niels T. Ferguson (born 10 December 1965, Eindhoven) is a Dutch cryptographer and consultant who currently works for Microsoft. He has worked with others, including Bruce Schneier, designing cryptographic algorithms, testing algorithms and protocols, and writing papers and books. Among the designs Ferguson has contributed to is the AES finalist block cipher algorithm Twofish as well as the stream cipher Helix and the Skein hash function. In 1999, Niels Ferguson, together with Bruce Schneier and John Kelsey, developed the Yarrow algorithm, a Cryptographically-Secure Pseudorandom Number Generator (CSPRNG). Yarrow was later further developed by Niels Ferguson and Bruce Schneier into the Fortuna CSPRNG In 2001, he claimed to have broken the HDCP system that is incorporated into HD DVD and Blu-ray Disc The Blu-ray Disc (BD), often known simply as Blu-ray, is a digital optical disc data storage format. It was invented and developed in 2005 and released on June 20, 200 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptovirology
Cryptovirology refers to the use of cryptography to devise particularly powerful malware, such as ransomware and asymmetric backdoors. Traditionally, cryptography and its applications are defensive in nature, and provide privacy, authentication, and security to users. Cryptovirology employs a twist on cryptography, showing that it can also be used offensively. It can be used to mount extortion based attacks that cause loss of access to information, loss of confidentiality, and information leakage, tasks which cryptography typically prevents. The field was born with the observation that public-key cryptography can be used to break the symmetry between what an antivirus analyst sees regarding malware and what the attacker sees. The antivirus analyst sees a public key contained in the malware, whereas the attacker sees the public key contained in the malware as well as the corresponding private key (outside the malware) since the attacker created the key pair for the attack. The pu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |