|
BoringSSL
OpenSSL is a software library for applications that provide secure communications over computer networks against eavesdropping or need to identify the party at the other end. It is widely used by Internet servers, including the majority of HTTPS websites. OpenSSL contains an open-source implementation of the SSL and TLS protocols. The core library, written in the C programming language, implements basic cryptographic functions and provides various utility functions. Wrappers allowing the use of the OpenSSL library in a variety of computer languages are available. The OpenSSL Software Foundation (OSF) represents the OpenSSL project in most legal capacities including contributor license agreements, managing donations, and so on. OpenSSL Software Services (OSS) also represents the OpenSSL project for support contracts. OpenSSL is available for most Unix-like operating systems (including Linux, macOS, and BSD), Microsoft Windows and OpenVMS. Project history The OpenSSL pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications. In technical writing you often you will see references to (D)TLS when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first defined in 1999, and th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C (programming Language)
C (''pronounced like the letter c'') is a General-purpose language, general-purpose computer programming language. It was created in the 1970s by Dennis Ritchie, and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of the targeted CPUs. It has found lasting use in operating systems, device drivers, protocol stacks, though decreasingly for application software. C is commonly used on computer architectures that range from the largest supercomputers to the smallest microcontrollers and embedded systems. A successor to the programming language B (programming language), B, C was originally developed at Bell Labs by Ritchie between 1972 and 1973 to construct utilities running on Unix. It was applied to re-implementing the kernel of the Unix operating system. During the 1980s, C gradually gained popularity. It has become one of the measuring programming language popularity, most widely used programming languages, with C compilers avail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs. Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computer from cellular phones and video game consoles to web servers and supercomputers. The dominant general-purpose personal computer operating system is Microsoft Windows with a market share of around 74.99%. macOS by Apple Inc. is in second place (14.84%), ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Elliptic-curve Cryptography
Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC allows smaller keys compared to non-EC cryptography (based on plain Galois fields) to provide equivalent security.Commercial National Security Algorithm Suite and Quantum Computing FAQ U.S. National Security Agency, January 2016. Elliptic curves are applicable for , s, [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FIPS 140
The 140 series of Federal Information Processing Standards ( FIPS) are U.S. government computer security standards that specify requirements for cryptography modules. , FIPS 140-2 and FIPS 140-3 are both accepted as current and active. FIPS 140-3 was approved on March 22, 2019 as the successor to FIPS 140-2 and became effective on September 22, 2019. FIPS 140-3 testing began on September 22, 2020, although no FIPS 140-3 validation certificates have been issued yet. FIPS 140-2 testing is still available until September 21, 2021 (later changed for applications already in progress to April 1, 2022), creating an overlapping transition period of one year. FIPS 140-2 test reports that remain in the CMVP queue will still be granted validations after that date, but all FIPS 140-2 validations will be moved to the Historical List on September 21, 2026 regardless of their actual final validation date. Purpose of FIPS 140 The National Institute of Standards and Technology (NIST) issues th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Revocation List
In cryptography, a certificate revocation list (or CRL) is "a list of digital certificates that have been revoked by the issuing certificate authority (CA) before their scheduled expiration date and should no longer be trusted". CRLs are no longer required by the CA/Browser forum, as alternate certificate revocation technologies (such as OCSP) are increasingly used instead. Nevertheless, CRLs are still widely used by the CAs. Revocation states There are two different states of revocation defined in RFC 5280: ; Revoked: A certificate is irreversibly revoked if, for example, it is discovered that the certificate authority (CA) had improperly issued a certificate, or if a private-key is thought to have been compromised. Certificates may also be revoked for failure of the identified entity to adhere to policy requirements, such as publication of false documents, misrepresentation of software behaviour, or violation of any other policy specified by the CA operator or its customer. The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SCTP
The Stream Control Transmission Protocol (SCTP) is a computer networking communications protocol in the transport layer of the Internet protocol suite. Originally intended for Signaling System 7 (SS7) message transport in telecommunication, the protocol provides the message-oriented feature of the User Datagram Protocol (UDP), while ensuring reliable, in-sequence transport of messages with congestion control like the Transmission Control Protocol (TCP). Unlike UDP and TCP, the protocol supports multihoming and redundant paths to increase resilience and reliability. SCTP is standardized by the Internet Engineering Task Force (IETF) in . The SCTP reference implementation was released as part of FreeBSD version 7, and has since been widely ported to other platforms. Formal oversight The IETF Signaling Transport ( SIGTRAN) working group defined the protocol (number 132) in October 2000, and the IETF Transport Area (TSVWG) working group maintains it. defines the protocol. provides ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
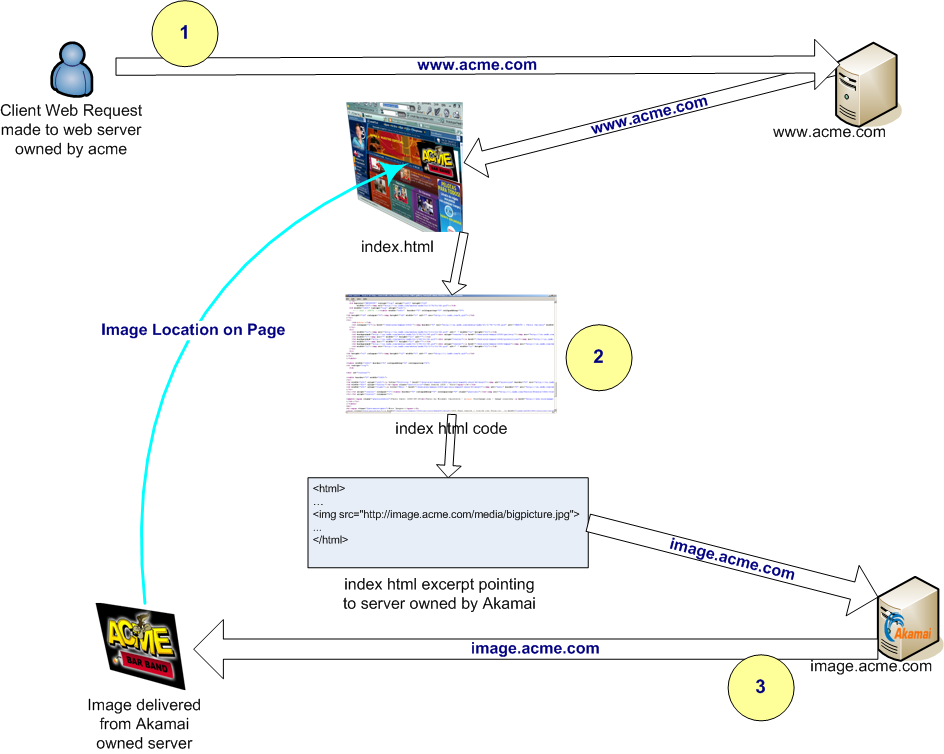
Akamai Technologies
Akamai Technologies, Inc. is an American content delivery networkJ. Dilley, B. Maggs, J. Parikh, H. Prokop, R. Sitaraman, and B. Weihl. (CDN), cybersecurity, and cloud service company, providing web and Internet security services. Akamai's Intelligent Edge Platform is a distributed computing platform. The company operates a network of servers worldwide and rents capacity of the servers to customers wanting increase effiency of their websites by using Akamai owned servers located near the user. When a user navigates to the URL of an Akamai customer, their browser is directed by Akamai's domain name systemKyle Schomp, Onkar Bhardwaj, Eymen Kurdoglu, Mashooq Muhaimen, and Ramesh K. Sitaraman. to a proximal edge server that can serve the requested content. Akamai's mapping system assigns each user to a proximal edge server using sophisticated algorithms such as stable matching and consistent hashing, enabling more reliable and faster web downloads. Further, Akamai implements DDoS ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ben Laurie
Ben Laurie is an English software engineer. He is currently the Director of Security at The Bunker Secure Hosting. Laurie wrote Apache-SSL, the basis of most SSL-enabled versions of the Apache HTTP Server. He developed the MUD ''Gods'', which was innovative in including online creation in its endgame. Laurie also has written several articles, papers and books, and is interested in ideal knots and their applications. Laurie was a member of WikiLeaks' Advisory Board. According to Laurie, he had little involvement with WikiLeaks, and didn't know who ran the site other than Julian Assange Julian Paul Assange ( ; Hawkins; born 3 July 1971) is an Australian editor, publisher, and activist who founded WikiLeaks in 2006. WikiLeaks came to international attention in 2010 when it published a series of leaks provided by U.S. Army int .... In 2009, he also said he wouldn't trust WikiLeaks to protect him if he were a whistleblower because "the things that Wikileaks relies on are not s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSA Security
RSA Security LLC, formerly RSA Security, Inc. and doing business as RSA, is an American computer and network security company with a focus on encryption and encryption standards. RSA was named after the initials of its co-founders, Ron Rivest, Adi Shamir and Leonard Adleman, after whom the RSA public key cryptography algorithm was also named. Among its products is the SecurID authentication token. The BSAFE cryptography libraries were also initially owned by RSA. RSA is known for incorporating backdoors developed by the NSA in its products. It also organizes the annual RSA Conference, an information security conference. Founded as an independent company in 1982, RSA Security was acquired by EMC Corporation in 2006 for US$2.1 billion and operated as a division within EMC. When EMC was acquired by Dell Technologies in 2016, RSA became part of the Dell Technologies family of brands. On 10 March 2020, Dell Technologies announced that they will be selling RSA Security to a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SSLeay
SSLeay is an open-source SSL implementation. It was developed by Eric Andrew Young and Tim J. Hudson as an SSL 3.0 implementation using RC2 and RC4 encryption. The recommended pronunciation is to say each letter s-s-l-e-a-y and was first developed by Eric A. Young ("eay"). SSLeay also included an implementation of the DES from earlier work by Eric Young which was believed to be the first open-source implementation of DES. Development of SSLeay unofficially mostly ended, and volunteers forked the project under the OpenSSL banner around December 1998, when Tim and Eric both commenced working for RSA Security in Australia. SSLeay SSLeay was developed by Eric A. Young, starting in 1995. Windows support was added by Tim J. Hudson. Patches to open source applications to support SSL using SSLeay were produced by Tim Hudson. Development by Young and Hudson ceased in 1998. The SSLeay library and codebase is licensed under its own SSLeay License, a form of free software license. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |