|
AIDS (computer Virus)
AIDS is a DOS computer virus which overwrites COM files. Description AIDS is the first virus known to exploit the MS-DOS COM file#Execution preference, "corresponding file" vulnerability. In MS-DOS, if the user enters in the command interpreter, in a directory where both and exist, then will always be executed. Thus, by creating infected COM files, AIDS code will always be executed before the intended .exe, EXE file. When the AIDS virus activates, it displays the following screen: ATTENTION: I have been elected to inform you that throughout your process of collecting and executing files, you have accidentally ¶HÜ¢KΣ► [:wikt:phuck, phucked in leet] yourself over: again, that's PHUCKED yourself over. No, it cannot be; YES, it CAN be, a √ìτûs [virus] has infected your system. Now what do you have to say about that? HAHAHAHAHA. Have ¶HÜÑ [phun] with this one and rememember, there is NO cure for HIV/AIDS, AIDS In the message above, the word "AIDS" covers about hal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. A computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the host program, but can run independently and actively carry out attacks. Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. Viruses use complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can inclu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
COM File
A COM file is a type of simple executable file. On the Digital Equipment Corporation (DEC) VAX operating systems of the 1970s, .COM was used as a filename extension for text files containing commands to be issued to the operating system (similar to a batch file). With the introduction of Digital Research's CP/M (a microcomputer operating system), the type of files commonly associated with COM extension changed to that of executable files. This convention was later carried over to DOS. Even when complemented by the more general .exe, EXE file format for executables, the compact COM files remained viable and frequently used under DOS. The .COM file name extension has no relation to the .com (for "commercial") top-level Internet domain name. However, this similarity in name has been exploited by malware writers. DOS binary format The COM format is the original binary executable format used in CP/M (including SCP (operating system), SCP and MSX-DOS) as well as DOS. It is very sim ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. A computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the host program, but can run independently and actively carry out attacks. Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. Viruses use complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can inclu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MS-DOS
MS-DOS ( ; acronym for Microsoft Disk Operating System, also known as Microsoft DOS) is an operating system for x86-based personal computers mostly developed by Microsoft. Collectively, MS-DOS, its rebranding as IBM PC DOS, and a few operating systems attempting to be compatible with MS-DOS, are sometimes referred to as "DOS" (which is also the generic acronym for disk operating system). MS-DOS was the main operating system for IBM PC compatibles during the 1980s, from which point it was gradually superseded by operating systems offering a graphical user interface (GUI), in various generations of the graphical Microsoft Windows operating system. IBM licensed and re-released it in 1981 as PC DOS 1.0 for use in its PCs. Although MS-DOS and PC DOS were initially developed in parallel by Microsoft and IBM, the two products diverged after twelve years, in 1993, with recognizable differences in compatibility, syntax, and capabilities. Beginning in 1988 with DR-DO ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Leet
Leet (or "1337"), also known as eleet or leetspeak, is a system of modified spellings used primarily on the Internet. It often uses character replacements in ways that play on the similarity of their glyphs via reflection or other resemblance. Additionally, it modifies certain words based on a system of suffixes and alternate meanings. There are many dialects or linguistic varieties in different online communities. The term "leet" is derived from the word ''elite'', used as an adjective to describe skill or accomplishment, especially in the fields of online gaming and computer hacking. The leet lexicon includes spellings of the word as ''1337'' or ''leet''. History Leet originated within bulletin board systems (BBS) in the 1980s,Mitchell.An Explanation of l33t Speak. where having "elite" status on a BBS allowed a user access to file folders, games, and special chat rooms. The Cult of the Dead Cow hacker collective has been credited with the original coining of the term, in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HIV/AIDS
Human immunodeficiency virus infection and acquired immunodeficiency syndrome (HIV/AIDS) is a spectrum of conditions caused by infection with the human immunodeficiency virus (HIV), a retrovirus. Following initial infection an individual may not notice any symptoms, or may experience a brief period of influenza-like illness. Typically, this is followed by a prolonged incubation period with no symptoms. If the infection progresses, it interferes more with the immune system, increasing the risk of developing common infections such as tuberculosis, as well as other opportunistic infections, and tumors which are rare in people who have normal immune function. These late symptoms of infection are referred to as acquired immunodeficiency syndrome (AIDS). This stage is often also associated with unintended weight loss. HIV is spread primarily by unprotected sex (including anal and vaginal sex), contaminated blood transfusions, hypodermic needles, and from mother to ch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Byte
The byte is a unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character of text in a computer and for this reason it is the smallest addressable unit of memory in many computer architectures. To disambiguate arbitrarily sized bytes from the common 8-bit definition, network protocol documents such as The Internet Protocol () refer to an 8-bit byte as an octet. Those bits in an octet are usually counted with numbering from 0 to 7 or 7 to 0 depending on the bit endianness. The first bit is number 0, making the eighth bit number 7. The size of the byte has historically been hardware-dependent and no definitive standards existed that mandated the size. Sizes from 1 to 48 bits have been used. The six-bit character code was an often-used implementation in early encoding systems, and computers using six-bit and nine-bit bytes were common in the 1960s. These systems often had memory words ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Working Directory
In computing, the working directory of a process is a directory of a hierarchical file system, if any, dynamically associated with each process. It is sometimes called the current working directory (CWD), e.g. the BSD getcwd function, or just current directory. When the process refers to a file using a simple file name or relative path (as opposed to a file designated by a full path from a root directory), the reference is interpreted relative to the working directory of the process. So for example a process with working directory /rabbit-shoes that asks to create the file foo.txt will end up creating the file /rabbit-shoes/foo.txt. In operating systems In most computer file systems, every directory has an entry (usually named ".") which points to the directory itself. In most DOS and UNIX command shells, as well as in the Microsoft Windows command line interpreters cmd.exe and Windows PowerShell, the working directory can be changed by using the CD or CHDIR commands. In Unix s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyclic Redundancy Check
A cyclic redundancy check (CRC) is an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to digital data. Blocks of data entering these systems get a short ''check value'' attached, based on the remainder of a polynomial division of their contents. On retrieval, the calculation is repeated and, in the event the check values do not match, corrective action can be taken against data corruption. CRCs can be used for error correction (see bitfilters). CRCs are so called because the ''check'' (data verification) value is a ''redundancy'' (it expands the message without adding information) and the algorithm is based on ''cyclic'' codes. CRCs are popular because they are simple to implement in binary hardware, easy to analyze mathematically, and particularly good at detecting common errors caused by noise in transmission channels. Because the check value has a fixed length, the function that generates it is occasionally used as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Antivirus Software
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect from other computer threats. In particular, modern antivirus software can protect users from malicious browser helper objects (BHOs), browser hijackers, ransomware, keyloggers, backdoors, rootkits, trojan horses, worms, malicious LSPs, dialers, fraud tools, adware, and spyware. Some products also include protection from other computer threats, such as infected and malicious URLs, spam, scam and phishing attacks, online identity (privacy), online banking attacks, social engineering techniques, advanced persistent threat (APT), and botnet DDoS attacks. History 1949–1980 period (pre-antivirus days) Although the roots of the computer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
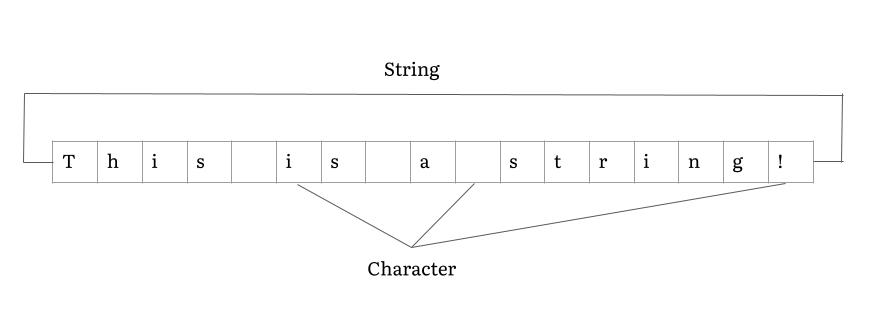
Character String (computer Science)
In computer programming, a string is traditionally a sequence of characters, either as a literal constant or as some kind of variable. The latter may allow its elements to be mutated and the length changed, or it may be fixed (after creation). A string is generally considered as a data type and is often implemented as an array data structure of bytes (or words) that stores a sequence of elements, typically characters, using some character encoding. ''String'' may also denote more general arrays or other sequence (or list) data types and structures. Depending on the programming language and precise data type used, a variable declared to be a string may either cause storage in memory to be statically allocated for a predetermined maximum length or employ dynamic allocation to allow it to hold a variable number of elements. When a string appears literally in source code, it is known as a string literal or an anonymous string. In formal languages, which are used in mathematical l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |