Storm Worm on:
[Wikipedia]
[Google]
[Amazon]
 The Storm Worm (dubbed so by the Finnish company F-Secure) is a
The Storm Worm (dubbed so by the Finnish company F-Secure) is a
Spamtrackers SpamWiki: StormWired.com: Analysis by
"There's a Storm Coming"
from the IBM ISS X-Force Blog
Trojan.Peacomm (Storm) at SymantecStormy Weather: A Quantitative Assessment of the Storm Web Threat in 2007 (Trend Micro)
from The Observer.
from PC World.
Storm and the future of social engineering
from Help Net Security (HNS). * Bodmer, Kilger, Carpenter, & Jones (2012). Reverse Deception: Organized Cyber Threat Counter-Exploitation. New York: McGraw-Hill Osborne Media. , {{ISBN, 978-0071772495 Email worms 2007 in computing Hacking in the 2000s
 The Storm Worm (dubbed so by the Finnish company F-Secure) is a
The Storm Worm (dubbed so by the Finnish company F-Secure) is a phishing
Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information or installing malware such as viruses, worms, adware, or ransomware. Phishing attacks have become increasingly sophisticate ...
backdoor Trojan horse
In Greek mythology, the Trojan Horse () was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer, Homer's ''Iliad'', with the poem ending ...
that affects computers using Microsoft
Microsoft Corporation is an American multinational corporation and technology company, technology conglomerate headquartered in Redmond, Washington. Founded in 1975, the company became influential in the History of personal computers#The ear ...
operating systems, discovered on January 17, 2007. The worm is also known as:
* Small.dam or Trojan-Downloader.Win32.Small.dam ( F-Secure)
* CME-711 (MITRE
The mitre (Commonwealth English) or miter (American English; American and British English spelling differences#-re, -er, see spelling differences; both pronounced ; ) is a type of headgear now known as the traditional, ceremonial headdress of ...
)
* W32/Nuwar@MM and Downloader-BAI (specific variant) (McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American proprietary software company focused on online ...
)
* Troj/Dorf and Mal/Dorf (Sophos
Sophos Limited is a British security software and hardware company. It develops and markets managed security services and cybersecurity software and hardware, such as managed detection and response, incident response and endpoint security s ...
)
* Trojan.DL.Tibs.Gen!Pac13
* Trojan.Downloader-647
* Trojan.Peacomm ( Symantec)
* TROJ_SMALL.EDW (Trend Micro
is an American-Japanese cyber security software company. The company has globally dispersed R&D in 16 locations across every continent excluding Antarctica. The company develops enterprise security software for servers, containers, and cloud ...
)
* Win32/Nuwar ( ESET)
* Win32/Nuwar.N@MM!CME-711 ( Windows Live OneCare)
* W32/Zhelatin ( F-Secure and Kaspersky)
* Trojan.Peed, Trojan.Tibs ( BitDefender)
The Storm Worm began attacking thousands of (mostly private) computers in Europe
Europe is a continent located entirely in the Northern Hemisphere and mostly in the Eastern Hemisphere. It is bordered by the Arctic Ocean to the north, the Atlantic Ocean to the west, the Mediterranean Sea to the south, and Asia to the east ...
and the United States
The United States of America (USA), also known as the United States (U.S.) or America, is a country primarily located in North America. It is a federal republic of 50 U.S. state, states and a federal capital district, Washington, D.C. The 48 ...
on Friday, January 19, 2007, using an e-mail message with a subject line about a recent weather disaster, "230 dead as storm batters Europe". During the weekend there were six subsequent waves of the attack. As of January 22, 2007, the Storm Worm accounted for 8% of all malware infections globally.
There is evidence, according to PCWorld
''PC World'' (stylized as PCWorld) is a global computer magazine published monthly by IDG. Since 2013, it has been an online-only publication.
It offers advice on various aspects of PCs and related items, the Internet, and other personal te ...
, that the Storm Worm was of Russia
Russia, or the Russian Federation, is a country spanning Eastern Europe and North Asia. It is the list of countries and dependencies by area, largest country in the world, and extends across Time in Russia, eleven time zones, sharing Borders ...
n origin, possibly traceable to the Russian Business Network.
History
Originally propagated in messages about Cyclone Kyrill, the Storm Worm has also been seen in emails with the following subjects: * 230 dead as storm batters Europe. he worm was dubbed "Storm" because of this message subject.* A killer at 11, he's free at 21 and kill again! * U.S. Secretary of StateCondoleezza Rice
Condoleezza "Condi" Rice ( ; born November 14, 1954) is an American diplomat and political scientist serving since 2020 as the 8th director of Stanford University's Hoover Institution. A member of the Republican Party, she previously served ...
has kicked German Chancellor Angela Merkel
* British Muslims Genocide
* Naked teens attack home director.
* Re: Your text
* Radical Muslim drinking enemies' blood.
* Chinese/Russian missile shot down Russian/Chinese satellite/aircraft
* Saddam Hussein
Saddam Hussein (28 April 1937 – 30 December 2006) was an Iraqi politician and revolutionary who served as the fifth president of Iraq from 1979 until Saddam Hussein statue destruction, his overthrow in 2003 during the 2003 invasion of Ira ...
safe and sound!
* Saddam Hussein alive!
* Venezuelan leader: "Let's the War beginning".
* Fidel Castro
Fidel Alejandro Castro Ruz (13 August 1926 – 25 November 2016) was a Cuban politician and revolutionary who was the leader of Cuba from 1959 to 2008, serving as the prime minister of Cuba from 1959 to 1976 and President of Cuba, president ...
dead.
* If I Knew
* FBI vs. Facebook
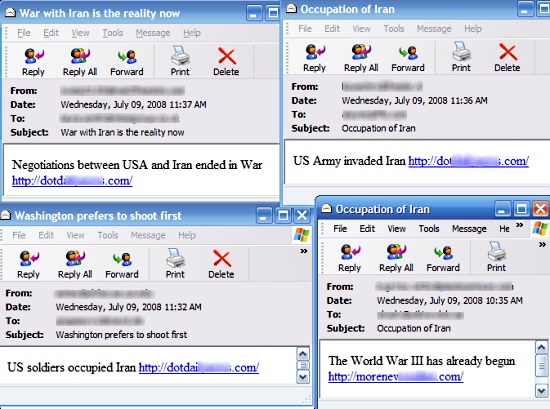
* USA occupies Iran
When an attachment is opened, the malware installs the wincom32 service, and injects a payload, passing on packets to destinations encoded within the malware itself. According to Symantec, it may also download and run the Trojan.Abwiz.F trojan, and the W32.Mixor.Q@mm worm
Worms are many different distantly related bilateria, bilateral animals that typically have a long cylindrical tube-like body, no limb (anatomy), limbs, and usually no eyes.
Worms vary in size from microscopic to over in length for marine ...
. The Trojan piggybacks on the spam
Spam most often refers to:
* Spam (food), a consumer brand product of canned processed pork of the Hormel Foods Corporation
* Spamming, unsolicited or undesired electronic messages
** Email spam, unsolicited, undesired, or illegal email messages
...
with names such as "postcard .exe" and "Flash Postcard.exe," with more changes from the original wave as the attack mutates. Some of the known names for the attachments include:
* Postcard.exe
* ecard.exe
* FullVideo.exe
* Full Story.exe
* Video.exe
* Read More.exe
* FullClip.exe
* GreetingPostcard.exe
* MoreHere.exe
* FlashPostcard.exe
* GreetingCard.exe
* ClickHere.exe
* ReadMore.exe
* FlashPostcard.exe
* FullNews.exe
* NflStatTracker.exe
* ArcadeWorld.exe
* ArcadeWorldGame.exe
Later, as F-Secure confirmed, the malware began spreading the subjects such as "Love birds" and "Touched by Love". These emails contain links to websites hosting some of the following files, which are confirmed to contain the virus:
* with_love.exe
* withlove.exe
* love.exe
* frommetoyou.exe
* iheartyou.exe
* fck2008.exe
* fck2009.exe
According to Joe Stewart, director of malware research for SecureWorks, Storm remains amazingly resilient, in part because the Trojan horse it uses to infect systems changes its packing code every 10 minutes, and, once installed, the bot uses fast flux to change the IP addresses for its command and control servers.
Botnetting
The compromised machine becomes merged into abotnet
A botnet is a group of Internet-connected devices, each of which runs one or more Internet bot, bots. Botnets can be used to perform distributed denial-of-service attack, distributed denial-of-service (DDoS) attacks, steal data, send Spamming, sp ...
. While most botnets are controlled through a central server, which if found can be taken down to destroy the botnet, the Storm Worm seeds a botnet that acts in a similar way to a peer-to-peer network, with no centralized control. Each compromised machine connects to a list of a subset of the entire botnet - around 30 to 35 other compromised machines, which act as hosts. While each of the infected hosts share lists of other infected hosts, no one machine has a full list of the entire botnet - each only has a subset, making it difficult to gauge the true extent of the zombie network. On 7 September 2007, estimates of the size of the Storm botnet ranged from 1 to 10 million computers. Researchers from the University of Mannheim and the Institut Eurecom have estimated concurrent online storm nodes to be between 5,000 and 40,000.
Rootkit
Another action the Storm Worm takes is to install therootkit
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the exist ...
Win32.agent.dh. Symantec pointed out that flawed rootkit code voids some of the Storm Worm author's plans. Later variants, starting around July 2007, loaded the rootkit component by patching existing Windows drivers such as tcpip.sys and cdrom.sys with a stub of code that loads the rootkit driver module without requiring it to have an entry in the Windows driver list.
April Fools' Day
On April 1, 2008, a new Storm Worm was released onto the net, with April Fools' -themed subject titles.Feedback
The list of antivirus companies that can detect the Storm Worm include Authentium, BitDefender, ClamAV, eSafe, Eset, F-Prot, F-Secure, Kaspersky,McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American proprietary software company focused on online ...
, Sophos
Sophos Limited is a British security software and hardware company. It develops and markets managed security services and cybersecurity software and hardware, such as managed detection and response, incident response and endpoint security s ...
, Symantec, Trend Micro
is an American-Japanese cyber security software company. The company has globally dispersed R&D in 16 locations across every continent excluding Antarctica. The company develops enterprise security software for servers, containers, and cloud ...
, avast! and Windows Live OneCare. The Storm Worm is constantly being updated by its authors to evade antivirus detection, so this does not imply that all the vendors listed above are able to detect all the Storm Worm variants. An intrusion detection system
An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically either reported to an administrator or collec ...
offers some protection from the rootkit, as it may warn that the Windows process "services.exe" is trying to access the Internet using ports 4000 or 7871. Windows 2000
Windows 2000 is a major release of the Windows NT operating system developed by Microsoft, targeting the server and business markets. It is the direct successor to Windows NT 4.0, and was Software release life cycle#Release to manufacturing (RT ...
, Windows XP
Windows XP is a major release of Microsoft's Windows NT operating system. It was released to manufacturing on August 24, 2001, and later to retail on October 25, 2001. It is a direct successor to Windows 2000 for high-end and business users a ...
and presumably Windows Vista
Windows Vista is a major release of the Windows NT operating system developed by Microsoft. It was the direct successor to Windows XP, released five years earlier, which was then the longest time span between successive releases of Microsoft W ...
can be infected by all the Storm Worm variants, but Windows Server 2003
Windows Server 2003, codenamed "Whistler Server", is the sixth major version of the Windows NT operating system produced by Microsoft and the first server version to be released under the Windows Server brand name. It is part of the Windows NT ...
cannot, as the malware's author specifically excluded that edition of Windows from the code. Additionally, the decryption layer for some variants requires Windows API functions that are only available in Windows XP Service Pack 2 and later, effectively preventing infection on older versions of Windows.
Peter Gutmann sent an email noting that the Storm botnet comprises between 1 and 10 million PCs depending on whose estimates you believe. Although Dr. Gutmann makes a hardware resource comparison between the Storm botnet and distributed memory
In computer science, distributed memory refers to a Multiprocessing, multiprocessor computer system in which each Central processing unit, processor has its own private Computer memory, memory. Computational tasks can only operate on local data ...
and distributed shared memory high performance computers at TOP500
The TOP500 project ranks and details the 500 most powerful non-distributed computing, distributed computer systems in the world. The project was started in 1993 and publishes an updated list of the supercomputers twice a year. The first of these ...
, exact performance matches were not his intention—rather a more general appreciation of the botnet's size compared to other massive computing resources. Consider for example the size of the Storm botnet compared to grid computing projects such as the World Community Grid.
An article in PCWorld dated October 21, 2007 says that a network security analyst presented findings at the Toorcon hacker conference in San Diego on October 20, 2007, saying that Storm is down to about 20,000 active hosts or about one-tenth of its former size. However, this is being disputed by security researcher Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is an Adjunct Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman ...
, who notes that the network is being partitioned in order to sell the parts off independently.
Notes
External links
Spamtrackers SpamWiki: Storm
Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is an Adjunct Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman ...
"There's a Storm Coming"
from the IBM ISS X-Force Blog
Trojan.Peacomm (Storm) at Symantec
from The Observer.
from PC World.
Storm and the future of social engineering
from Help Net Security (HNS). * Bodmer, Kilger, Carpenter, & Jones (2012). Reverse Deception: Organized Cyber Threat Counter-Exploitation. New York: McGraw-Hill Osborne Media. , {{ISBN, 978-0071772495 Email worms 2007 in computing Hacking in the 2000s