Sniffer (protocol Analyzer) on:
[Wikipedia]
[Google]
[Amazon]
The Sniffer was a computer network packet and protocol analyzer developed and first sold in 1986 by Network General Corporation of Mountain View, CA. By 1994 the Sniffer had become the market leader in high-end protocol analyzers. According to SEC 10-K filings and corporate annual reports, between 1986 and March 1997 about $933M worth of Sniffers and related products and services had been sold as tools for network managers and developers.
The Sniffer was the antecedent of several generations of network protocol analyzers, of which the current most popular is
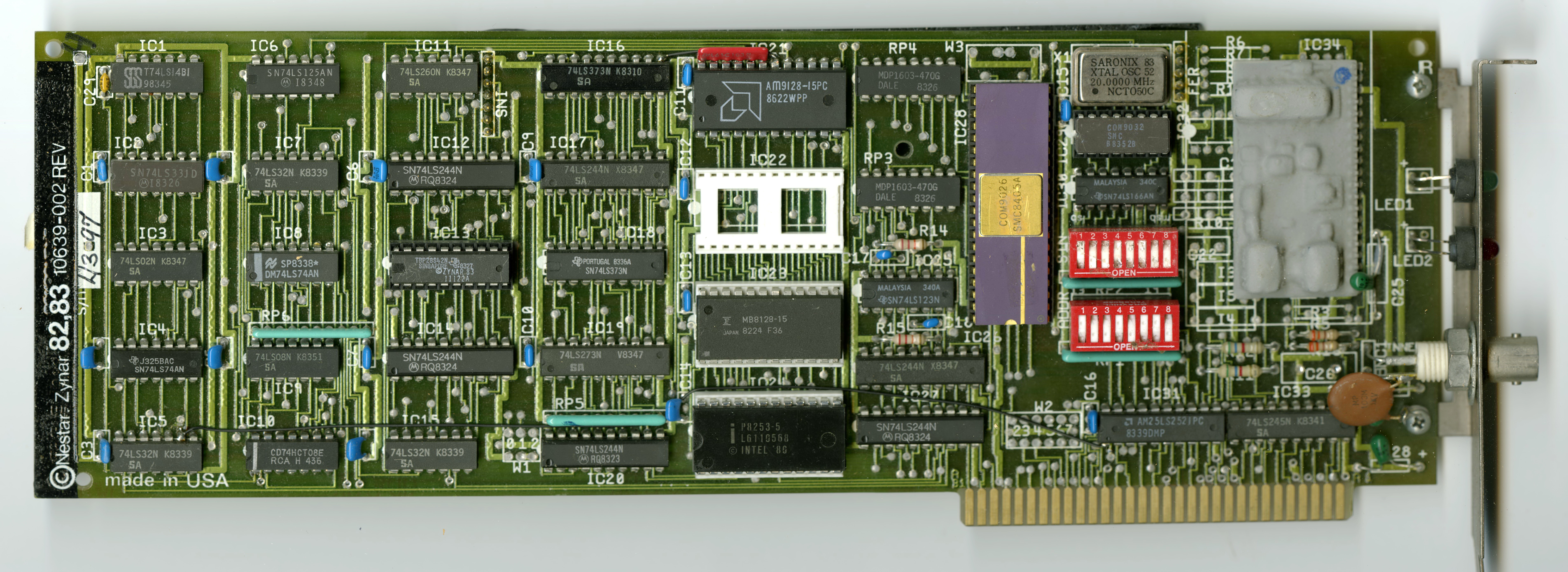 The ARCNET Sniffer developed as an internal test tool by Zynar used the IBM PC ARCNET Network Interface Card developed by Nestar for the PLAN networking systems. That board used the COM9026 integrated ARCNET controller from
The ARCNET Sniffer developed as an internal test tool by Zynar used the IBM PC ARCNET Network Interface Card developed by Nestar for the PLAN networking systems. That board used the COM9026 integrated ARCNET controller from  Since the ability to receive all packets was viewed as a violation of network privacy, the circuitry implementing it was kept secret, and the daughterboard was potted in black epoxy to discourage reverse-engineering.
The source code of the original TART/Sniffer BASIC and assembler program is available on GitHub.
Since the ability to receive all packets was viewed as a violation of network privacy, the circuitry implementing it was kept secret, and the daughterboard was potted in black epoxy to discourage reverse-engineering.
The source code of the original TART/Sniffer BASIC and assembler program is available on GitHub.
 The Sniffer was a
The Sniffer was a 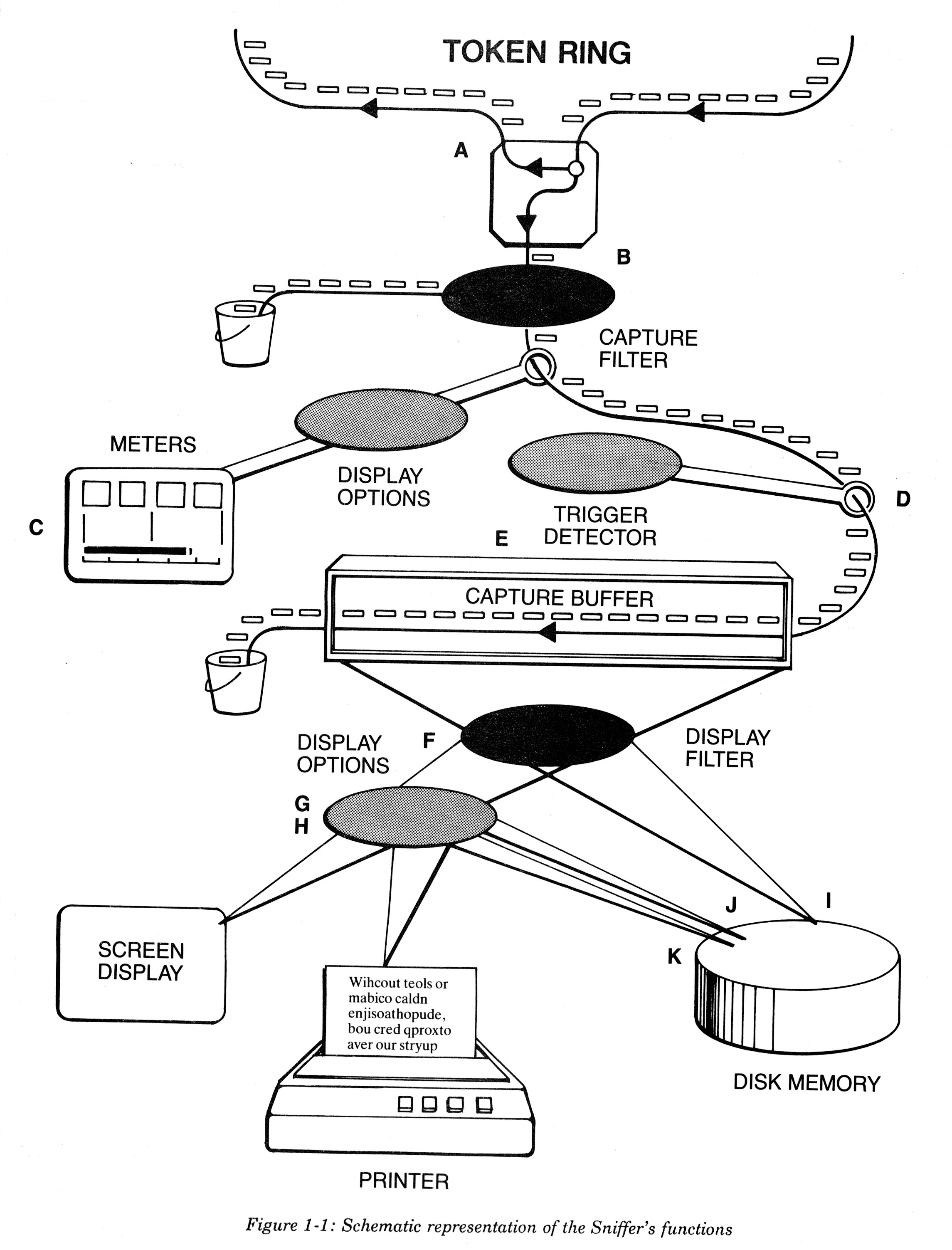 The two major modes of operation were:
* “capture”, in which
** packets are captured, stored, counted, and summarized
** filters control which packets are captured
** triggers control when capture should stop, perhaps because a sought-after network error condition had occurred
*“display”, in which
** packets are analyzed and interpreted
** filters control which packets are displayed
** options control which aspects of the packets are displayed
Navigation of the extensive menu system on the character-mode display was through a variation of
The two major modes of operation were:
* “capture”, in which
** packets are captured, stored, counted, and summarized
** filters control which packets are captured
** triggers control when capture should stop, perhaps because a sought-after network error condition had occurred
*“display”, in which
** packets are analyzed and interpreted
** filters control which packets are displayed
** options control which aspects of the packets are displayed
Navigation of the extensive menu system on the character-mode display was through a variation of  Pressing F10 initiated capture and a real-time display of activity.
Pressing F10 initiated capture and a real-time display of activity.
 When capture ended, packets were analyzed and displayed in one or more of the now-standard three synchronized vertical windows: multiple packet summary, single packet decoded detail, and raw numerical packet data. Highlighting linked the selected items in each window.
In the multiple-packet summary, the default display was of information at the highest level of the protocol stack present in that packet. Other displays could be requested using the “display options” menu.
The translation of data at a particular level of the network protocol stack into user-friendly text was the job of a “protocol interpreter”, or PI. Network General provided over 100 PI’s for commonly-used protocols of the day:
Decoding higher protocol levels often required the interpreter to maintain state information about connections so that subsequent packets could be property interpreted. That was implemented with a combination of locally cached data within the protocol interpreter, and the ability to look back at earlier packets stored in the capture buffer.
Sniffer customers could write their own protocol interpreters to decode new or rare protocols not supported by Network General. Interpreters were written in C and linked with the rest of the Sniffer modules to create a new executable program. The procedure for creating new PIs was documented in April 1987 as part of Sniffer version 1.20.
In addition to supporting many network protocols, there were versions of the Sniffer that collected data from the major local area networks in use in the 1980s and early 1990s:
*IBM Token-Ring
*
When capture ended, packets were analyzed and displayed in one or more of the now-standard three synchronized vertical windows: multiple packet summary, single packet decoded detail, and raw numerical packet data. Highlighting linked the selected items in each window.
In the multiple-packet summary, the default display was of information at the highest level of the protocol stack present in that packet. Other displays could be requested using the “display options” menu.
The translation of data at a particular level of the network protocol stack into user-friendly text was the job of a “protocol interpreter”, or PI. Network General provided over 100 PI’s for commonly-used protocols of the day:
Decoding higher protocol levels often required the interpreter to maintain state information about connections so that subsequent packets could be property interpreted. That was implemented with a combination of locally cached data within the protocol interpreter, and the ability to look back at earlier packets stored in the capture buffer.
Sniffer customers could write their own protocol interpreters to decode new or rare protocols not supported by Network General. Interpreters were written in C and linked with the rest of the Sniffer modules to create a new executable program. The procedure for creating new PIs was documented in April 1987 as part of Sniffer version 1.20.
In addition to supporting many network protocols, there were versions of the Sniffer that collected data from the major local area networks in use in the 1980s and early 1990s:
*IBM Token-Ring
*
Wireshark
Wireshark is a Free and open-source software, free and open-source packet analyzer. It is used for computer network, network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, ...
.
Background
The Sniffer was the first product of Network General Corporation, founded on May 13, 1986 by Harry Saal and Len Shustek to develop and market network protocol analyzers. The inspiration was an internal test tool that had been developed withinNestar Systems
Nestar Systems, Inc., was an early independent manufacturer of pre-internet local area networks for personal computers from 1978 to 1986 and was considered "a pioneer in the industry". It produced three major generations of products:
* Cluster/ ...
, a personal computer networking company founded in October 1978 by Saal and Shustek along with Jim Hinds and Nick Fortis. In 1982 engineers John Rowlands and Chris Reed at Nestar’s UK subsidiary Zynar Ltd developed an ARCNET
Attached Resource Computer NETwork (ARCNET or ARCnet) is a communications protocol for local area networks. ARCNET was the first widely available networking system for microcomputers and it became popular in the 1980s for office automation task ...
promiscuous packet receiver and analyzer called TART (“Transmit and Receive Totaliser”) for use as an internal engineering test tool. It used custom hardware, and software for an IBM PC written in a combination of BASIC and 8086 assembly code. When Nestar was acquired by Digital Switch Corporation (now DSC Communications) of Plano, Texas in 1986, Saal and Shustek received the rights to TART.
At Network General, Saal and Shustek initially sold TART as the “R-4903 ARCNET Line Analyzer (‘The Sniffer’)”. They then reengineered TART for IBM’s Token Ring
Token Ring is a Physical layer, physical and data link layer computer networking technology used to build local area networks. It was introduced by IBM in 1984, and standardized in 1989 as IEEE Standards Association, IEEE 802.5. It uses a sp ...
network hardware, created a different user interface with software written in C, and began selling it as The Sniffer™ in December 1986. The company had four employees at the end of that year.
In April 1987 the company released an Ethernet version of the Sniffer, and in October, versions for ARCNET, StarLAN
StarLAN was the first IEEE 802.3 standard for Ethernet over twisted pair wiring. It was standardized by the IEEE Standards Association as 802.3e in 1986, as the 1BASE5 version of Ethernet. The StarLAN Task Force was chaired by Bob Galin.
Descripti ...
, and IBM PC Network Broadband. Protocol interpreters were written for about 100 network protocols at various levels of the protocol stack
The protocol stack or network stack is an implementation of a computer networking protocol suite or protocol family. Some of these terms are used interchangeably but strictly speaking, the ''suite'' is the definition of the communication protoc ...
, and customers were given the ability to write their own interpreters. The product line gradually expanded to include the Distributed Sniffer System for multiple remote network segments, the Expert Sniffer for advanced problem diagnosis, and the Watchdog for simple network monitoring.
Development
Nestar ARCNET Sniffer
 The ARCNET Sniffer developed as an internal test tool by Zynar used the IBM PC ARCNET Network Interface Card developed by Nestar for the PLAN networking systems. That board used the COM9026 integrated ARCNET controller from
The ARCNET Sniffer developed as an internal test tool by Zynar used the IBM PC ARCNET Network Interface Card developed by Nestar for the PLAN networking systems. That board used the COM9026 integrated ARCNET controller from Standard Microsystems Corporation
Microchip Technology Incorporated is a publicly listed American semiconductor corporation that manufactures microcontroller, mixed-signal, analog, and Flash-IP integrated circuits.
Its corporate headquarters is located in Chandler, Arizona. ...
, which had been developed in collaboration with Datapoint.
There was no promiscuous mode in the SMC chip that would allow all packets to be received regardless of the destination address. So to create the Sniffer, a daughterboard was developed that intercepted the receive data line to the chip and manipulated the data so that every packet looked like a broadcast and was received by the chip.
 Since the ability to receive all packets was viewed as a violation of network privacy, the circuitry implementing it was kept secret, and the daughterboard was potted in black epoxy to discourage reverse-engineering.
The source code of the original TART/Sniffer BASIC and assembler program is available on GitHub.
Since the ability to receive all packets was viewed as a violation of network privacy, the circuitry implementing it was kept secret, and the daughterboard was potted in black epoxy to discourage reverse-engineering.
The source code of the original TART/Sniffer BASIC and assembler program is available on GitHub.
Network General Sniffer
 The Sniffer was a
The Sniffer was a promiscuous mode
In computer networking, promiscuous mode is a mode for a wired network interface controller (NIC) or wireless network interface controller (WNIC) that causes the controller to pass all traffic it receives to the central processing unit (CPU) rath ...
packet receiver, which means it received a copy of all network packets without regard to what computer they were addressed to. The packets were filtered, analyzed using what is now sometimes called deep packet inspection
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data (Network packet, packets) being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep ...
, and stored for later examination.
The Sniffer was implemented above Microsoft’s MS-DOS
MS-DOS ( ; acronym for Microsoft Disk Operating System, also known as Microsoft DOS) is an operating system for x86-based personal computers mostly developed by Microsoft. Collectively, MS-DOS, its rebranding as IBM PC DOS, and a few op ...
operating system, and used a 40 line 80-character text-only display. The first version, the PA-400 protocol analyzer for Token-Ring networks, was released on a Compaq Portable II “luggable” computer that had an Intel 80286 processor, 640 KB of RAM, a 20 MB internal hard disk, a 5 ¼” floppy disk drive, and a 9” monochrome CRT screen. The retail price of the Sniffer in unit quantities was $19,995.
 The two major modes of operation were:
* “capture”, in which
** packets are captured, stored, counted, and summarized
** filters control which packets are captured
** triggers control when capture should stop, perhaps because a sought-after network error condition had occurred
*“display”, in which
** packets are analyzed and interpreted
** filters control which packets are displayed
** options control which aspects of the packets are displayed
Navigation of the extensive menu system on the character-mode display was through a variation of
The two major modes of operation were:
* “capture”, in which
** packets are captured, stored, counted, and summarized
** filters control which packets are captured
** triggers control when capture should stop, perhaps because a sought-after network error condition had occurred
*“display”, in which
** packets are analyzed and interpreted
** filters control which packets are displayed
** options control which aspects of the packets are displayed
Navigation of the extensive menu system on the character-mode display was through a variation of Miller columns
Miller columns (also known as cascading lists) are a browsing/ visualization technique that can be applied to tree structures. The columns allow multiple levels of the hierarchy to be open at once, and provide a visual representation of the curr ...
that were originally created by Mark S. Miller at Datapoint Corporation
Datapoint Corporation, originally known as Computer Terminal Corporation (CTC), was a computer company based in San Antonio, Texas, United States. Founded in July 1968 by Phil Ray and Gus Roche, its first products were, as the company's initial ...
for their file browser. As the Sniffer manual described, “The screen shows you three panels, arranged from left to right. Immediately to the left of your current (highlighted) position is the node you just came from. Above and below you in the center panel are alternative nodes that are also reachable from the node to your left… To your right are nodes reachable from the node you're now on.”
 Pressing F10 initiated capture and a real-time display of activity.
Pressing F10 initiated capture and a real-time display of activity.
 When capture ended, packets were analyzed and displayed in one or more of the now-standard three synchronized vertical windows: multiple packet summary, single packet decoded detail, and raw numerical packet data. Highlighting linked the selected items in each window.
In the multiple-packet summary, the default display was of information at the highest level of the protocol stack present in that packet. Other displays could be requested using the “display options” menu.
The translation of data at a particular level of the network protocol stack into user-friendly text was the job of a “protocol interpreter”, or PI. Network General provided over 100 PI’s for commonly-used protocols of the day:
Decoding higher protocol levels often required the interpreter to maintain state information about connections so that subsequent packets could be property interpreted. That was implemented with a combination of locally cached data within the protocol interpreter, and the ability to look back at earlier packets stored in the capture buffer.
Sniffer customers could write their own protocol interpreters to decode new or rare protocols not supported by Network General. Interpreters were written in C and linked with the rest of the Sniffer modules to create a new executable program. The procedure for creating new PIs was documented in April 1987 as part of Sniffer version 1.20.
In addition to supporting many network protocols, there were versions of the Sniffer that collected data from the major local area networks in use in the 1980s and early 1990s:
*IBM Token-Ring
*
When capture ended, packets were analyzed and displayed in one or more of the now-standard three synchronized vertical windows: multiple packet summary, single packet decoded detail, and raw numerical packet data. Highlighting linked the selected items in each window.
In the multiple-packet summary, the default display was of information at the highest level of the protocol stack present in that packet. Other displays could be requested using the “display options” menu.
The translation of data at a particular level of the network protocol stack into user-friendly text was the job of a “protocol interpreter”, or PI. Network General provided over 100 PI’s for commonly-used protocols of the day:
Decoding higher protocol levels often required the interpreter to maintain state information about connections so that subsequent packets could be property interpreted. That was implemented with a combination of locally cached data within the protocol interpreter, and the ability to look back at earlier packets stored in the capture buffer.
Sniffer customers could write their own protocol interpreters to decode new or rare protocols not supported by Network General. Interpreters were written in C and linked with the rest of the Sniffer modules to create a new executable program. The procedure for creating new PIs was documented in April 1987 as part of Sniffer version 1.20.
In addition to supporting many network protocols, there were versions of the Sniffer that collected data from the major local area networks in use in the 1980s and early 1990s:
*IBM Token-Ring
*Token Bus
In computer networking, a token bus network is a network implementing a token-passing protocol over a virtual ring on a coaxial cable.
Network
A token is passed around the network nodes and only the node possessing the token may transmit. If a ...
*Ethernet (thick, thin, twisted pair)
*Datapoint ARCnet
*Starlan
*AppleTalk
AppleTalk is a discontinued proprietary suite of networking protocols developed by Apple Computer for their Macintosh computers. AppleTalk includes a number of features that allow local area networks to be connected with no prior setup or the ...
*Corvus Omninet
*FDDI
Fiber Distributed Data Interface (FDDI) is a standard for data transmission in a local area network.
It uses optical fiber as its standard underlying physical medium.
It was also later specified to use copper cable, in which case it may be c ...
*ISDN
Integrated Services Digital Network (ISDN) is a set of communication standards for simultaneous digital transmission of voice, video, data, and other network services over the digitalised circuits of the public switched telephone network. ...
*Frame Relay
Frame Relay (FR) is a standardized wide area network (WAN) technology that specifies the Physical layer, physical and data link layers of digital telecommunications channels using a packet switching methodology.
Frame Relay was originally devel ...
*Synchronous Data Link Control
Synchronous Data Link Control (SDLC) is a computer serial communication, serial communications protocol first introduced by IBM as part of its Systems Network Architecture (SNA). SDLC is used as layer 2, the data link layer, in the SNA protocol s ...
(SDLC)
*Asynchronous Transfer Mode
Asynchronous Transfer Mode (ATM) is a telecommunications standard defined by the American National Standards Institute and International Telecommunication Union Telecommunication Standardization Sector (ITU-T, formerly CCITT) for digital trans ...
(ATM)
*X.25
X.25 is an ITU-T standard protocol suite for Packet switched network, packet-switched data communication in wide area network, wide area networks (WAN). It was originally defined by the CCITT, International Telegraph and Telephone Consultative Co ...
* IBM PC Network (Sytek)
Competitors
Even in the early years, the Sniffer had competition, at least for some aspects of the product. Several were, like the Sniffer, ready-to-use packaged instruments: * Excelan's 1984 Nutcracker, and its 1986 LANalyzer * Communications Machinery Corporation's DRN-1700 LanScan Ethernet Monitor * Hewlett-Packard's HP-4972A LAN Protocol Analyzer * Digital Equipment Corporation's LAN Traffic Monitor * Tektronix's TMA802 Media Analyzer There were also several software-only packet monitors and decoders, often running on Unix, and often with only a command-line user interface: *tcpdump
tcpdump is a data-network packet analyzer computer program that runs under a command line interface. It allows the user to display TCP/IP and other packets being transmitted or received over a network to which the computer is attached. Distr ...
, using the Berkeley Packet Filter
The Berkeley Packet Filter (BPF; also BSD Packet Filter, classic BPF or cBPF) is a network tap and packet filter which permits computer network packets to be captured and filtered at the operating system level. It provides a raw interface to da ...
and other capture mechanisms provided by the operating system
* LANWatch, originally from FTP Software
FTP Software, Inc., was an American software company incorporated in 1986 by James van Bokkelen, John Romkey (co-author of the MIT PC/IP package), Nancy Connor, Roxanne van Bokkelen (née Ritchie), Dave Bridgham, and several other founding shar ...
See also
* Comparison of packet analyzers *Wireshark
Wireshark is a Free and open-source software, free and open-source packet analyzer. It is used for computer network, network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, ...
References
External links
* "The Ancient History of Computers and Network Sniffers" (Sharkfest 2021 keynote talk) - * *{{Cite magazine, magazine=Network World, first=Marvin, last=Chartoff, url=https://books.google.com/books?id=mRMEAAAAMBAJ&pg=PA37, title=LAN management: What's the right tool for the job?, volume=4, issue=50, page=37, date=1987-12-14, publisher=International Data Group
International Data Group (IDG, Inc.) is an American market intelligence and demand generation company focused on the technology industry. IDG, Inc.'s mission is centered around supporting the technology industry through research, data, market ...
Network analyzers