Locky on:
[Wikipedia]
[Google]
[Amazon]
Locky is ransomware malware released in 2016. It is delivered by email (that is allegedly an invoice requiring payment) with an attached 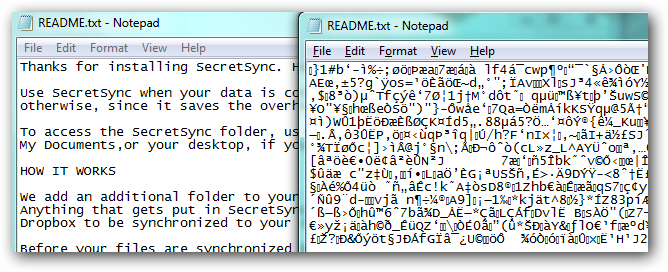
Microsoft Word
Microsoft Word is a word processor program, word processing program developed by Microsoft. It was first released on October 25, 1983, under the name Multi-Tool Word for Xenix systems. Subsequent versions were later written for several other platf ...
document that contains malicious macros. When the user opens the document, it appears to be full of gibberish, and includes the phrase "Enable macro if data encoding is incorrect," a social engineering technique. If the user does enable macros, they save and run a binary file that downloads the ''actual'' encryption Trojan, which will encrypt all files that match particular extensions. Filenames are converted to a unique 16 letter and number combination. Initially, only the .locky file extension was used for these encrypted files. Subsequently, other file extensions have been used, including .zepto, .odin, .aesir, .thor, and .zzzzz. After encryption, a message (displayed on the user's desktop) instructs them to download the Tor browser
Tor is a free overlay network for enabling anonymous communication. It is built on free and open-source software run by over seven thousand volunteer-operated relays worldwide, as well as by millions of users who route their Internet traffic ...
and visit a specific criminal-operated Web site for further information.
The website contains instructions that demand a ransom payment between 0.5 and 1 bitcoin
Bitcoin (abbreviation: BTC; Currency symbol, sign: ₿) is the first Decentralized application, decentralized cryptocurrency. Based on a free-market ideology, bitcoin was invented in 2008 when an unknown entity published a white paper under ...
(as of November 2017, one bitcoin varies in value between $9,000 and $10,000 via a bitcoin exchange
A cryptocurrency exchange, or a digital currency exchange (DCE), is a business that allows customers to trade cryptocurrencies or digital currencies for other assets, such as conventional fiat money or other digital currencies. Exchanges may acce ...
). Since the criminals possess the private key and the remote servers are controlled by them, the victims are motivated to pay to decrypt their files. Cryptocurrencies are very difficult to trace and are highly portable.

Operation
The most commonly reported mechanism of infection involves receiving an email with a Microsoft Word document attachment that contains the code. The document is gibberish, and prompts the user to enable macros to view the document. Enabling macros and opening the document launch the Locky virus. Once the virus is launched, it loads into the memory of the users system, encrypts documents as hash.locky files, installs .bmp and .txt files, and can encrypt network files that the user has access to. This has been a different route than most ransomware since it uses macros and attachments to spread rather than being installed by a Trojan or using a previous exploit.Updates
On June 22, 2016, Necurs released a new version of Locky with a new loader component, which includes several detection-avoiding techniques, such as detecting whether it is running within avirtual machine
In computing, a virtual machine (VM) is the virtualization or emulator, emulation of a computer system. Virtual machines are based on computer architectures and provide the functionality of a physical computer. Their implementations may involve ...
or within a physical machine, and relocation of instruction code.
Since Locky was released there have been numerous variants released that used different extensions for encrypted files. Many of these extensions are named after gods of Norse and Egyptian mythology. When first released, the extension used for encrypted files was .Locky. Other versions utilized the .zepto, .odin, .shit, .thor, .aesir, and .zzzzz extensions for encrypted files. The current version, released in December 2016, utilizes the .osiris extension for encrypted files.
Distribution methods
Many different distribution methods for Locky have been used since the ransomware was released. These distribution methods include exploit kits, Word and Excel attachments with malicious macros, DOCM attachments, and zipped JS attachments. The general consensus among security experts to protect yourself from ransomware, including Locky, is to keep your installed programs updated and to only open attachments from known senders.Encryption
The Locky uses RSA-2048 + AES-128 cipher with ECB mode to encrypt files. Keys are generated on the server side, making manual decryption impossible, and Locky ransomware can encrypt files on all fixed drives, removable drives, network and RAM disk drives.Prevalence
Locky is reported to have been sent to about a half-million users on February 16, 2016, and for the period immediately after the attackers increased their distribution to millions of users. Despite the newer version, Google Trend data indicates that infections have dropped off around June 2016.Notable incidents
On February 18, 2016, theHollywood Presbyterian Medical Center
CHA Hollywood Presbyterian Medical Center, formerly known as Queen of Angels – Hollywood Presbyterian Medical Center, is a private hospital located at 1300 North Vermont Avenue in Los Angeles, California. The hospital has 434 beds and is owned b ...
paid a $17,000 ransom in the form of bitcoins for the decryption key for patient data. The hospital was infected by the delivery of an email attachment disguised as a Microsoft Word invoice.
This has led to increased fear and knowledge about ransomware in general and has brought ransomware into public spotlight once again.
There appears to be a trend in ransomware being used to attack hospitals and it appears to be growing.
On May 31, Necurs went dormant, perhaps due to a glitch in the C&C server. According to Softpedia
Softpedia is a software and tech news website based in Romania. It indexes, reviews and hosts downloadable software and reports news on technology and science topics. It is ranked as among of the top download portals on the internet.
History
So ...
, there were less spam emails with Locky or Dridex
Dridex, also known as Bugat and Cridex, is a type of malware that specializes in stealing bank credentials through a system that utilizes macros from Microsoft Word.
It primarily targets Windows users who open malicious email attachments in Wor ...
attached to it. On June 22, however, MalwareTech discovered Necurs's bots
The British Overseas Territories (BOTs) or alternatively referred to as the United Kingdom Overseas Territories (UKOTs) are the fourteen dependent territory, territories with a constitutional and historical link with the United Kingdom that, ...
consistently polled the DGA until a C&C server replied with a digitally signed response. This signified Necurs was no longer dormant. The cybercriminal
Cybercrime encompasses a wide range of criminal activities that are carried out using digital devices and/or networks. It has been variously defined as "a crime committed on a computer network, especially the Internet"; Cybercriminals may explo ...
group also started sending a very large quantity of spam emails with new and improved versions of Locky and Dridex attached to them, as well as a new message and zipped JavaScript
JavaScript (), often abbreviated as JS, is a programming language and core technology of the World Wide Web, alongside HTML and CSS. Ninety-nine percent of websites use JavaScript on the client side for webpage behavior.
Web browsers have ...
code in the emails.
In Spring 2016, the Dartford Grammar School
Dartford Grammar School is a secondary foundation school for boys (ages 11–18) in Dartford, Kent, England, which admits girls to its sixth form (ages 16–18). All of the students joining the school are considered to be from the top 25% of t ...
and Dartford Science & Technology College
Dartford Science & Technology College (DSTC) is a non-selective school for girls in Dartford, Kent, England. DSTC has moved to a campus it shares with a nursery, primary school and adult education. It has two specialisms: Science and Technology ...
computers were infected with the virus. In both schools, a student had opened an infected email which quickly spread and encrypted many school files. The virus stayed on the computer for several weeks. Eventually, they managed to remove the virus by using System Restore for all of the computers.
Spam email vector
An example message with Locky as an attachment is the following: ''Dear (random name):'' ''Please find attached our invoice for services rendered and additional disbursements in the above-mentioned matter.'' ''Hoping the above to your satisfaction, we remain'' ''Sincerely,'' ''(random name)'' ''(random title)''References
{{reflist Ransomware 2016 in computing Cryptographic attacks Windows trojans