Fast-flux on:
[Wikipedia]
[Google]
[Amazon]
 Fast flux is a
Fast flux is a
 Fast-fluxing is generally classified into two types: single fluxing and double fluxing, a build-on implementation over single fluxing. The phraseologies involved in fast-fluxing includes "flux-herder mothership nodes" and "fast-flux agent nodes", referred to the backend
Fast-fluxing is generally classified into two types: single fluxing and double fluxing, a build-on implementation over single fluxing. The phraseologies involved in fast-fluxing includes "flux-herder mothership nodes" and "fast-flux agent nodes", referred to the backend
 Fast flux is a
Fast flux is a domain name system
The Domain Name System (DNS) is a hierarchical and distributed name service that provides a naming system for computers, services, and other resources on the Internet or other Internet Protocol (IP) networks. It associates various information ...
(DNS) based evasion technique used by cyber criminals to hide phishing
Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information or installing malware such as viruses, worms, adware, or ransomware. Phishing attacks have become increasingly sophisticate ...
and malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to caus ...
delivery websites behind an ever-changing network of compromised hosts acting as reverse proxies to the backend botnet master—a bulletproof
Bulletproofing is the process of making an object capable of stopping a bullet or similar high velocity projectiles (e.g. shrapnel). The term bullet resistance is often preferred because few, if any, practical materials provide complete protecti ...
autonomous system. It can also refer to the combination of peer-to-peer networking
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network, forming a peer-to-peer network of nod ...
, distributed command and control, web-based load balancing and proxy redirection used to make malware networks more resistant to discovery and counter-measures.
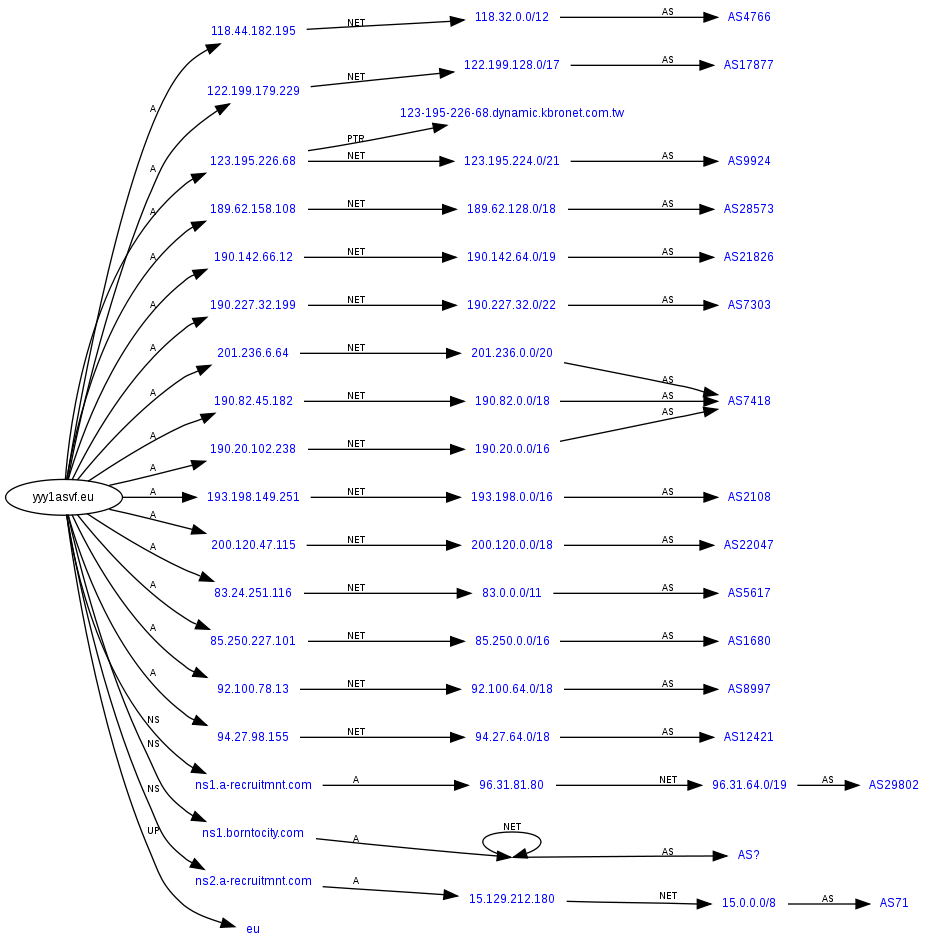
The fundamental idea behind fast-flux is to have numerous IP address
An Internet Protocol address (IP address) is a numerical label such as that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface i ...
es associated with a single fully qualified domain name
A fully qualified domain name (FQDN), sometimes also called an absolute domain name, is a domain name that specifies its exact location in the tree hierarchy of the Domain Name System (DNS). It specifies all domain levels, including the top-level ...
, where the IP addresses are swapped in and out with extremely high frequency, through changing DNS resource records, thus the authoritative name servers of the said fast-fluxing domain name
In the Internet, a domain name is a string that identifies a realm of administrative autonomy, authority, or control. Domain names are often used to identify services provided through the Internet, such as websites, email services, and more. ...
is—in most cases—hosted by the criminal actor.
Depending on the configuration and complexity of the infrastructure, fast-fluxing is generally classified into single, double, and domain fast-flux networks. Fast-fluxing remains an intricate problem in network security and current countermeasures remain ineffective.
History
Fast-fluxing was first reported by the security researchers William Salusky and Robert Danford of The Honeynet Project in 2007; the following year, they released a systematic study of fast-flux service networks in 2008. Rock Phish (2004) andStorm Worm
The Storm Worm (dubbed so by the Finnish company F-Secure) is a phishing backdoor Trojan horse that affects computers using Microsoft operating systems, discovered on January 17, 2007. The worm is also known as:
* Small.dam or Trojan-Download ...
(2007) were two notable fast-flux service networks which were used for malware distribution and phishing.
Fast-flux service network
A fast-flux service network (FFSN) is anetwork infrastructure
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or b ...
resultant of the fast-fluxed network of compromised hosts; the technique is also used by legitimate service providers such as content distribution networks (CDNs) where the dynamic IP address
An Internet Protocol address (IP address) is a numerical label such as that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface ide ...
is converted to match the domain name of the internet host
A network host is a computer or other device connected to a computer network. A host may work as a server offering information resources, services, and applications to users or other hosts on the network. Hosts are assigned at least one network a ...
, usually for the purpose of load balancing using round-robin domain name system (RR-DNS). The purpose of using FFSN infrastructure for the botnets is to relay network requests and act as a proxy to the backend bulletproof
Bulletproofing is the process of making an object capable of stopping a bullet or similar high velocity projectiles (e.g. shrapnel). The term bullet resistance is often preferred because few, if any, practical materials provide complete protecti ...
content server which functions as an " origin server".
The frontend bots, which act as an ephemeral host affixed to a control master, are called flux-agents whose network availability is indeterminate due to the dynamic nature of fast-fluxing. The backend motherships do not establish direct communication with the user agent
On the Web, a user agent is a software agent responsible for retrieving and facilitating end-user interaction with Web content. This includes all web browsers, such as Google Chrome and Safari
A safari (; originally ) is an overland jour ...
s; rather, all actions are reverse proxied through compromised frontend nodes, effectively making the attack long-lasting and resilient against take down attempts.
Types
 Fast-fluxing is generally classified into two types: single fluxing and double fluxing, a build-on implementation over single fluxing. The phraseologies involved in fast-fluxing includes "flux-herder mothership nodes" and "fast-flux agent nodes", referred to the backend
Fast-fluxing is generally classified into two types: single fluxing and double fluxing, a build-on implementation over single fluxing. The phraseologies involved in fast-fluxing includes "flux-herder mothership nodes" and "fast-flux agent nodes", referred to the backend bulletproof
Bulletproofing is the process of making an object capable of stopping a bullet or similar high velocity projectiles (e.g. shrapnel). The term bullet resistance is often preferred because few, if any, practical materials provide complete protecti ...
botnet controller and the compromised host nodes involved in reverse proxying the traffic back-and-forth between the origin
Origin(s) or The Origin may refer to:
Arts, entertainment, and media
Comics and manga
* ''Origin'' (comics), a Wolverine comic book mini-series published by Marvel Comics in 2002
* ''The Origin'' (Buffy comic), a 1999 ''Buffy the Vampire Sl ...
and clients respectively. The compromised hosts used by the fast-flux herders typically includes residential broadband access circuits, such as DSL
Digital subscriber line (DSL; originally digital subscriber loop) is a family of technologies that are used to transmit digital data over telephone lines. In telecommunications marketing, the term DSL is widely understood to mean asymmetric di ...
and cable modem
A cable modem is a type of network bridge that provides bi-directional data communication via radio frequency channels on a hybrid fiber-coaxial (HFC), radio frequency over glass (RFoG) and coaxial cable infrastructure. Cable modems are pri ...
s.
Single-flux network
In single-flux network, theauthoritative name server
A name server is a computer application that implements a network service for providing responses to queries against a directory service. It translates an often humanly meaningful, text-based identifier to a system-internal, often numeric identi ...
of a fast-fluxing domain name repeatedly permutes
In mathematics, a permutation of a set can mean one of two different things:
* an arrangement of its members in a sequence or linear order, or
* the act or process of changing the linear order of an ordered set.
An example of the first meanin ...
the DNS resource records with low time to live
Time to live (TTL) or hop limit is a mechanism which limits the lifespan or lifetime of data in a computer or network. TTL may be implemented as a counter (digital), counter or timestamp attached to or embedded in the data. Once the prescribed ev ...
(TTL) values, conventionally between 180 and 600 seconds. The permuted record within the zone file
A Domain Name System (DNS) zone file is a text file that describes a DNS zone. A DNS zone is a subset, often a single domain, of the hierarchical domain name structure of the DNS. The zone file contains mappings between domain names and IP add ...
includes A, AAAA and CNAME record
A Canonical Name (CNAME) record is a type of resource record in the Domain Name System (DNS) that maps one domain name (an alias) to another (the canonical name).
This can prove convenient when running multiple services (like an FTP server '' ...
, the disposition is usually done by means of round robin from a registry of exploited host's IP addresses and DDNS names. Although HTTP
HTTP (Hypertext Transfer Protocol) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, wher ...
and DNS
The Domain Name System (DNS) is a hierarchical and distributed name service that provides a naming system for computers, services, and other resources on the Internet or other Internet Protocol (IP) networks. It associates various informatio ...
remain commonly proxied application protocol
An application layer is an abstraction layer that specifies the shared communication protocols and interface methods used by hosts in a communications network. An ''application layer'' abstraction is specified in both the Internet Protocol Sui ...
s by the frontend flux-agents, protocols such as SMTP
The Simple Mail Transfer Protocol (SMTP) is an Internet standard communication protocol for electronic mail transmission. Mail servers and other message transfer agents use SMTP to send and receive mail messages. User-level email clients typi ...
, IMAP
In computing, the Internet Message Access Protocol (IMAP) is an Internet standard protocol used by email clients to retrieve email messages from a mail server over a TCP/IP connection. IMAP is defined by .
IMAP was designed with the goal of per ...
and POP
Pop or POP may refer to:
Arts, entertainment, and media
* Pop music, a musical genre
Artists
* POP, a Japanese idol group now known as Gang Parade
* Pop! (British group), a UK pop group
* Pop! featuring Angie Hart, an Australian band
Album ...
can also be delivered through transport layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end c ...
(L4) TCP and UDP level port binding techniques between flux-agents and backend flux-herder nodes.
Double-flux network
Double-fluxing networks involve high-frequency permutation of the fluxing domain's authoritative name servers, along with DNS resource records such as A, AAAA, or CNAME pointing to frontend proxies. In this infrastructure, the authoritative name server of the fluxing domain points to a frontend redirector node, which forwards the DNS datagram to a backend mothership node that resolves the query. The DNS resource records, including the NS record, are set with a lower TTL value, therefore resulting in an additional level indirection. The NS records in a double-fluxing network usually point to a referrer host that listens on port 53, which forwards the query to a backend DNS resolver that is authoritative for the fluxing domain. Advanced level of resilience and redundancy is achieved through blind proxy redirection techniques of the frontend nodes; Fast-fluxing domains also abuse domain wildcarding specification for spam delivery and phishing, and use DNS covert channels for transferring application layer payloads of protocols such as HTTP, SFTP, and FTP encapsulated within a DNS datagram query.Domain-flux network
Domain-flux network involves keeping a fast-fluxing network operational through continuously rotating the domain name of the flux-herder mothership nodes. The domain names are dynamically generated using a selectedpseudorandom
A pseudorandom sequence of numbers is one that appears to be statistically random, despite having been produced by a completely deterministic and repeatable process. Pseudorandom number generators are often used in computer programming, as tradi ...
domain generation algorithm Domain generation algorithms (DGA) are algorithms seen in various families of malware that are used to periodically generate a large number of domain names that can be used as rendezvous points with their command and control servers. The large numb ...
(DGA), and the flux operator mass-registers the domain names. An infected host repeatedly tries to initiate a flux-agent handshake by spontaneous generating, resolving and connecting to an IP address until an acknowledgment, to register itself to the flux-herder mothership node. A notable example includes Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows OS software (MS08-067 / CVE-2008-4250) and dictionary atta ...
, a botnet which was operational by generating 50,000 different domains in 110 top-level domains
A top-level domain (TLD) is one of the domains at the highest level in the hierarchical Domain Name System of the Internet after the root domain. The top-level domain names are installed in the root zone of the name space. For all domains i ...
(TLDs).
Security countermeasures
The detection and mitigation of fast-fluxing domain names remain an intricate challenge in network security due to the robust nature of fast-fluxing. Althoughfingerprinting
A fingerprint is an impression left by the friction ridges of a human finger. The recovery of partial fingerprints from a crime scene is an important method of forensic science. Moisture and grease on a finger result in fingerprints on surfa ...
the backend fast-flux mothership node remains increasingly difficult, service providers could detect the upstream mothership nodes through probing the frontend flux-agents in a special way by sending a crafted HTTP request that would trigger an out-of-band network request from the backend fast-flux mothership node to the client in an independent channel, such that the client could deduce the mothership node's IP address by analyzing the logs of its network traffic. Various security researchers suggests that the effective measure against fast-fluxing is to take down the domain name from its use. However, the domain name registrar
A domain name registrar is a company, person, or office that manages the reservation of Internet domain names.
A domain name registrar must be accredited by a generic top-level domain (gTLD) Domain name registry, registry or a country code top-l ...
s are reluctant in doing so, since there are not jurisdiction independent terms of service agreements that must be observed; in most cases, fast-flux operators and cybersquatter
Cybersquatting (also known as domain squatting) is the practice of registering, trafficking in, or using an Domain name, Internet domain name, with a bad faith intent to profit from the Goodwill (accounting), goodwill of a trademark belonging to so ...
s are the main source of income to those registrars.
Other countermeasures against fast-fluxing domains include deep packet inspection
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data (Network packet, packets) being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep ...
(DPI), host-based firewall, and IP-based access control lists
In computer security, an access-control list (ACL) is a list of permissions associated with a system resource (object or facility). An ACL specifies which users or system processes are granted access to resources, as well as what operations are a ...
(ACLs), although there are serious limitations in these approaches due to the dynamic nature of fast-fluxing.
See also
* Avalanche (phishing group)References
Bibliography
* * * * * * * {{DEFAULTSORT:Fast Flux Domain Name System Botnets