Censorship Circumvention on:
[Wikipedia]
[Google]
[Amazon]
Internet censorship circumvention is the use of various methods and tools to bypass internet censorship. Commonly used tools include
, Dutton, William H.; Dopatka, Anna; Law, Ginette; Nash, Victoria, Division for Freedom of Expression, Democracy and Peace, United Nations Educational, Scientific and Cultural Organization (UNESCO), Paris, 2011, 103 pp., and risks from breaking the law.
Main Page
and there is also a mobile-formatted version a
Wikipedia, the free encyclopedia
If DNS resolution is disrupted but the site is not blocked in other ways, it may be possible to access a site directly through its
, The Citizen Lab, University of Toronto, September 2007
Military Thumb Drives Expose Larger Problem
''MSNBC'' Retrieved on 25 January 2007. One example of a widely adopted sneakernet network is El Paquete Semanal in Cuba.
Casting A Wider Net: Lessons Learned in Delivering BBC Content on the Censored Internet
'', Ronald Deibert, Canada Centre for Global Security Studies and Citizen Lab, Munk School of Global Affairs, University of Toronto, 11 October 2011
Censorship Wikia
an anti-censorship site that catalogs past and present censored works, using verifiable sources, and a forum to discuss organizing against and circumventing censorship
"Circumvention Tool Evaluation: 2011"
Hal Roberts, Ethan Zuckerman, and John Palfrey, Berkman Centre for Internet & Society, 18 August 2011
"Circumvention Tool Usage Report: 2010"
Hal Roberts, Ethan Zuckerman, Jillian York, Robert Faris, and John Palfrey, Berkman Centre for Internet & Society, 14 October 2010
Digital Security and Privacy for Human Rights Defenders
by Dmitri Vitaliev, Published by Front Line – The International Foundation for the Protection of Human Rights Defenders
"Digital Tools to Curb Snooping"
''The New York Times'', 17 July 2013
Methods and Scripts useful for evading censorship through DNS filtering *
How to Bypass Internet Censorship
', also known by the titles: ''Bypassing Internet Censorship'' or ''Circumvention Tools'', a FLOSS Manual, 10 March 2011, 240 pp. Translations have been published i
ArabicBurmeseChinesePersianRussianSpanish
an
Vietnamese
"Leaping over the Firewall: A Review of Censorship Circumvention Tools"
, by Cormac Callanan (Ireland), Hein Dries-Ziekenheiner (Netherlands), Alberto Escudero-Pascual (Sweden), and Robert Guerra (Canada), Freedom House, April 2011
"Media Freedom Internet Cookbook"
by the OSCE Representative on Freedom of the Media, Vienna, 2004
"Online Survival Kit"
We Fight Censorship project of Reporters Without Borders
Free Haven Project, accessed 16 September 2011 {{DEFAULTSORT:Internet Censorship Circumvention Internet security Content-control software Internet censorship Internet privacy Circumvention
Lantern
A lantern is a source of lighting, often portable. It typically features a protective enclosure for the light sourcehistorically usually a candle, a oil lamp, wick in oil, or a thermoluminescence, thermoluminescent Gas mantle, mesh, and often a ...
and Psiphon, which bypass multiple safeguard types. Some methods use alternate DNS servers, false addresses or address lookup systems to evade less sophisticated blocking tools. However, such methods do not work if censors block the IP address
An Internet Protocol address (IP address) is a numerical label such as that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface i ...
of restricted domains in addition to DNS, rendering the bypass ineffective. Other tools tunnel network traffic to proxies in jurisdictions without censorship. Through pluggable transports, traffic obscuration, website mirrors, or archive sites, copies of sites can be accessed in areas under internet censorship.
An arms race
An arms race occurs when two or more groups compete in military superiority. It consists of a competition between two or more State (polity), states to have superior armed forces, concerning production of weapons, the growth of a military, and ...
has developed between censors and developers of circumvention software, resulting in more sophisticated blocking techniques by censors and the development of harder-to-detect tools by tool developers. Estimates of adoption of circumvention tools are disputed, but are widely understood to be in the tens of millions of monthly active users. Barriers to adoption include usability issues, difficulty finding reliable and trustworthy information about circumvention, lack of desire to access censored content,''Freedom of connection, freedom of expression: the changing legal and regulatory ecology shaping the Internet'', Dutton, William H.; Dopatka, Anna; Law, Ginette; Nash, Victoria, Division for Freedom of Expression, Democracy and Peace, United Nations Educational, Scientific and Cultural Organization (UNESCO), Paris, 2011, 103 pp., and risks from breaking the law.
Circumvention methods
Alternate names and addresses
Filters may block specific domain names, either using DNS hijacking or URL filtering. Sites are sometimes accessible through alternate names and addresses that may not be blocked. Some websites offer the same content at multiple pages or domain names. For example, the English Wikipedia is available aMain Page
and there is also a mobile-formatted version a
Wikipedia, the free encyclopedia
If DNS resolution is disrupted but the site is not blocked in other ways, it may be possible to access a site directly through its
IP address
An Internet Protocol address (IP address) is a numerical label such as that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface i ...
or modifying the host file. Using alternative DNS servers, or public recursive name servers (especially when used through an encrypted DNS client), may bypass DNS-based blocking.
Censors may block specific IP addresses. Depending on how the filtering is implemented, it may be possible to use different forms of the IP address, such as by specifying the address in a different base. For example, the following URLs all access the same site, although not all browsers will recognize all forms: http://1.1.1.1/ (dotted decimal), http://16843009/ (decimal), http://0001.0001.0001.0001/ (dotted octal), http://1.1.1.1/ (hexadecimal), and http://0x01.0x01.0x01.0x01/ (dotted hexadecimal).
Blockchain technology is an attempt to decentralize namespaces outside the control of a single entity. Decentralized namespaces enable censorship resistant domains. The BitDNS discussion began in 2010 with a desire to achieve names that are decentralized, secure and human readable.
Mirrors, caches, and copies
Cached pages: Some search engines keep copies of previously indexed webpages, or cached pages, which are often hosted by search engines and may not be blocked. Mirror and archive sites: Copies of web sites or pages may be available atmirror
A mirror, also known as a looking glass, is an object that Reflection (physics), reflects an image. Light that bounces off a mirror forms an image of whatever is in front of it, which is then focused through the lens of the eye or a camera ...
or archive
An archive is an accumulation of historical records or materials, in any medium, or the physical facility in which they are located.
Archives contain primary source documents that have accumulated over the course of an individual or organ ...
sites such as the Internet Archive's Wayback Machine
The Wayback Machine is a digital archive of the World Wide Web founded by Internet Archive, an American nonprofit organization based in San Francisco, California. Launched for public access in 2001, the service allows users to go "back in ...
or Archive.today. The Docker Registry Image Repository is a centralized storage, application stateless, and node
In general, a node is a localized swelling (a "knot") or a point of intersection (a vertex).
Node may refer to:
In mathematics
* Vertex (graph theory), a vertex in a mathematical graph
*Vertex (geometry), a point where two or more curves, lines ...
scalable HTTP
HTTP (Hypertext Transfer Protocol) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, wher ...
public service and has a performance bottleneck in the multinational upload and download scenario. Decentralized Docker Registry avoids this centralization drawback. DDR uses a network-structured P2P network
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network, forming a peer-to-peer network of Node ...
to store and query mirror manifest file
In computer programming, a manifest file is a Data file, file containing metadata for a group of accompanying files that are part of a set or coherent unit. For example, the files of a computer program may have a manifest describing the name, Soft ...
and blob routing, while each node serves as an independent mirror repository to provide mirror upload and download for the entire network.
RSS aggregators: RSS aggregators such as Feedly may be able to receive and pass on RSS feeds that are blocked when accessed directly.''Everyone's Guide to By-passing Internet Censorship'', The Citizen Lab, University of Toronto, September 2007
Alternative platforms
Decentralized Hosting: Content creators may publish to an alternative platform which is willing to host ones content.Napster
Napster was an American proprietary peer-to-peer (P2P) file sharing application primarily associated with digital audio file distribution. Founded by Shawn Fanning and Sean Parker, the platform originally launched on June 1, 1999. Audio shared ...
was the first peer to peer platform but was closed due to centralized bootstrapping vulnerabilities. Gnutella
Gnutella is a peer-to-peer network protocol. Founded in 2000, it was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model.
In June 2005, Gnutella's population was 1.81 million computer ...
was the first sustainable platform hosting by decentralization. Freenet's model is that "true freedom requires true anonymity." Later, BitTorrent
BitTorrent is a Protocol (computing), communication protocol for peer-to-peer file sharing (P2P), which enables users to distribute data and electronic files over the Internet in a Decentralised system, decentralized manner. The protocol is d ...
was developed to allocate resources with high performance and fairness. ZeroNet was the first DHT to support dynamic and updateable webpages. YaCy is the leading distributed search.
Anonymity Networks: The anonymity Tor network and I2P provides leads to more willingness to host content that would otherwise be censored. However hosting implementation and location may bring issues, and the content is still hosted by a single entity which can be controlled.
Federated: Being semi-decentralized, federated platforms such as Nextcloud
Nextcloud is a suite of Client–server model, client-server software for creating and using file hosting services. It can integrate with the Collabora Online and OnlyOffice office suites. It can be hosted in the Cloud computing, cloud or On-pre ...
and IRC
IRC (Internet Relay Chat) is a text-based chat system for instant messaging. IRC is designed for group communication in discussion forums, called '' channels'', but also allows one-on-one communication via private messages as well as chat ...
make it easier for users to find an instance where they are welcomed.
Providers with a different policy: Some platforms relying on the Cloud
In meteorology, a cloud is an aerosol consisting of a visible mass of miniature liquid droplets, frozen crystals, or other particles, suspended in the atmosphere of a planetary body or similar space. Water or various other chemicals may ...
may have more lax TOS. However nothing by design keeps it so.
See: Darknets
Proxying
Web proxies allow users to load external web pages through the proxy server, permitting the user to load the page as if it is coming from the proxy server and not the (blocked) source. Depending on how the proxy is configured, a censor may be able to determine the pages loaded or determine that the user is using a proxy server. For example, the mobile Opera Mini browser uses proxies with employing encryption and compression to speed up downloads. This has the side effect of circumventing several approaches to Internet censorship. In 2009 this led the government of China to ban all but a special Chinese version of the browser. Domain fronting: Domain fronting hides the destination of a connection by passing initial requests through acontent delivery network
A content delivery network (CDN) or content distribution network is a geographically distributed network of proxy servers and their data centers. The goal is to provide high availability and performance ("speed") by distributing the service spat ...
or other popular site which censors may be unwilling to block. This technique was used by messaging applications including Signal and Telegram. Tor's meek uses Microsoft's Azure cloud. However, large cloud providers such as Amazon Web Services
Amazon Web Services, Inc. (AWS) is a subsidiary of Amazon.com, Amazon that provides Software as a service, on-demand cloud computing computing platform, platforms and Application programming interface, APIs to individuals, companies, and gover ...
and Google Cloud no longer permit its use. Website owners can use a free account to use a Cloudflare domain for fronting.
SSH tunneling: By establishing an SSH tunnel, a user can forward all their traffic over an encrypted channel, so both outgoing requests for blocked sites and the response from those sites are hidden from the censors, for whom it appears as unreadable SSH traffic.
Virtual private network (VPN): Using a VPN, secure connections to more permissive countries can be created, browsing as if they were situated in that country. Some services are offered for a monthly fee; others are ad-supported. According to GlobalWebIndex in 2014 there were over 400 million people using virtual private networks to circumvent censorship or for increased level of privacy, although this number is not verifiable.
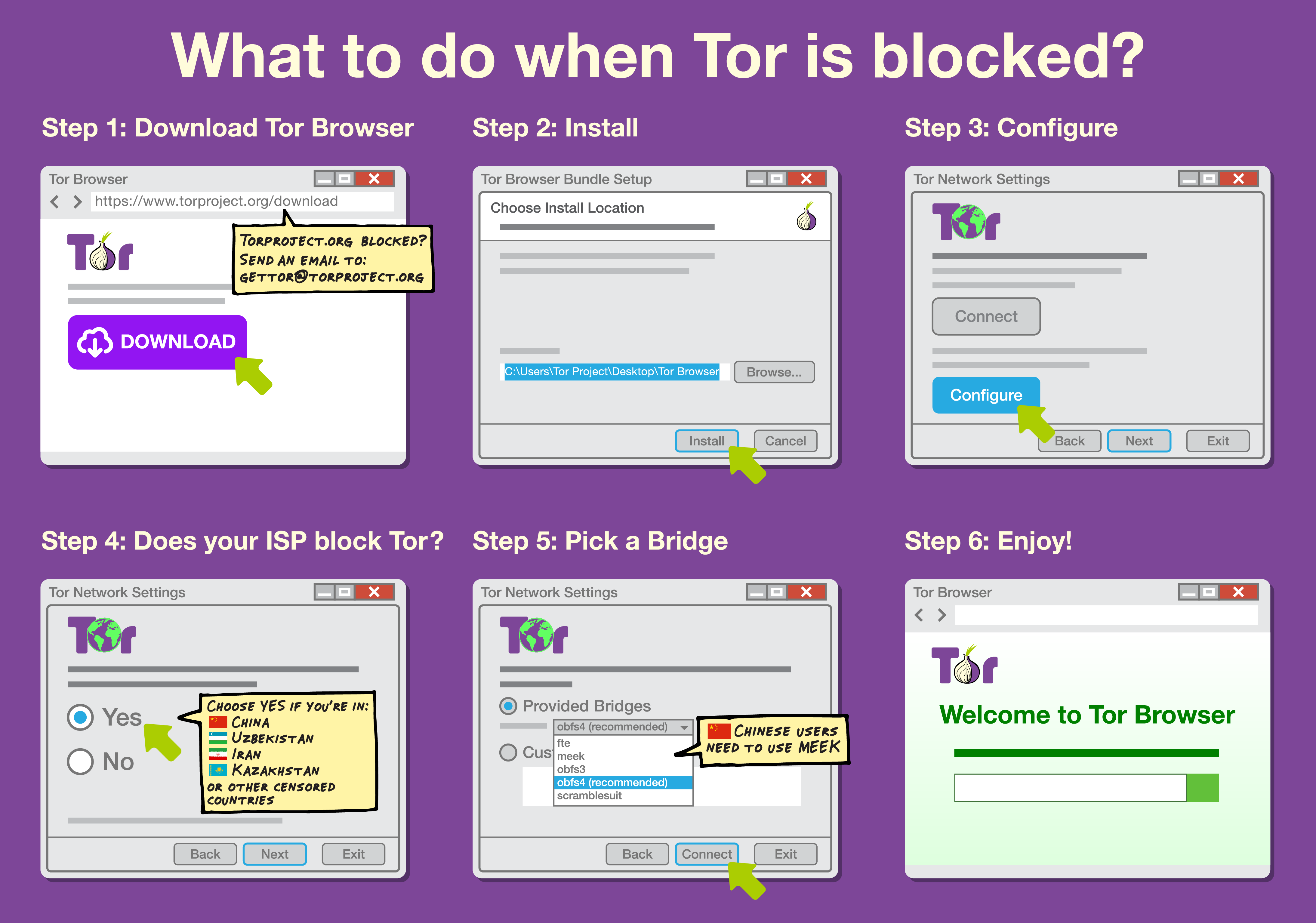
Tor: More advanced tools such as Tor route encrypted traffic through multiple servers to make the source and destination of traffic less traceable. It can in some cases be used to avoid censorship, especially when configured to use traffic obfuscation techniques.

Traffic obfuscation
A censor may be able to detect and block use of circumvention tools throughdeep packet inspection
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data (Network packet, packets) being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep ...
. There are efforts to make circumvention tools less detectable by randomizing the traffic, attempting to mimic a whitelisted protocol or tunnelling traffic through a whitelisted site by using domain fronting or Meek. Tor and other circumvention tools have adopted multiple obfuscation techniques that users can use depending on the nature of their connection, which are sometimes called "Pluggable Transports".
Internet alternatives
Functionality that people may be after might overlap with non-internet services, such as traditionalmail
The mail or post is a system for physically transporting postcards, letter (message), letters, and parcel (package), parcels. A postal service can be private or public, though many governments place restrictions on private systems. Since the mid ...
, Bluetooth, or walkie-talkies. The following are some detailed examples:
Alternative data transport
Datacasting
Datacasting (data broadcasting) is the transmission of data over a wide area using radio waves. It typically refers to supplemental information sent by television stations alongside digital terrestrial television (DTT) signals. However, datacas ...
allows transmission of Web pages and other information via satellite broadcast channels bypassing the Internet entirely. This requires a satellite dish and suitable receiver hardware but provides a powerful means of avoiding censorship. Because the system is entirely receive-only for the end user, a suitably air-gapped computer can be impossible to detect.
Sneakernets
A sneakernet is the transfer of electronic information, especially computer files, by physically carrying data on storage media from one place to another. A sneakernet can move data regardless of network restrictions simply by not using the network at all.Sullivan, Bob (13 April 2006Military Thumb Drives Expose Larger Problem
''MSNBC'' Retrieved on 25 January 2007. One example of a widely adopted sneakernet network is El Paquete Semanal in Cuba.
Adoption of circumvention tools
Circumvention tools have seen spikes in adoption in response to high-profile blocking attempts, however, studies measuring adoption of circumvention tools in countries with persistent and widespread censorship report mixed results.In response to persistent censorship
Measures and estimates of circumvention tool adoption have found widely divergent results. A 2010 study by Harvard University researchers estimated that very few users use censorship circumvention tools—likely less than 3% of users even in countries that consistently implement widespread censorship. Other studies have reported substantially larger estimates, but have been disputed. In China, anecdotal reports suggest that adoption of circumvention tools is particularly high in certain communities, such as universities, and a survey byFreedom House
Freedom House is a nonprofit organization based in Washington, D.C. It is best known for political advocacy surrounding issues of democracy, Freedom (political), political freedom, and human rights. Freedom House was founded in October 1941, wi ...
found that users generally did not find circumvention tools to be difficult to use. Market research firm GlobalWebIndex reported over 35 million Twitter users and 63 million Facebook users in China (both services are blocked). However, these estimates have been disputed; Facebook's advertising platform estimates 1 million users in China, and other reports of Twitter adoption estimate 10 million users. Other studies have pointed out that efforts to block circumvention tools in China have reduced adoption of those tools; the Tor network previously had over 30,000 users connecting from China but as of 2014 had only approximately 3,000 Chinese users.
In Thailand
Thailand, officially the Kingdom of Thailand and historically known as Siam (the official name until 1939), is a country in Southeast Asia on the Mainland Southeast Asia, Indochinese Peninsula. With a population of almost 66 million, it spa ...
, internet censorship has existed since 2002, and there is sporadic and inconsistent filtering. In a small-scale survey of 229 Thai internet users, a research group at the University of Washington found that 63% of surveyed users attempted to use circumvention tools, and 90% were successful in using those tools. Users often made on-the-spot decisions about use of circumvention tools based on limited or unreliable information, and had a variety of perceived threats, some more abstract and others based on personal experiences.
In response to blocking events
In response to the 2014 blocking of Twitter inTurkey
Turkey, officially the Republic of Türkiye, is a country mainly located in Anatolia in West Asia, with a relatively small part called East Thrace in Southeast Europe. It borders the Black Sea to the north; Georgia (country), Georgia, Armen ...
, information about alternate DNS servers was widely shared, as using another DNS server such as Google Public DNS allowed users to access Twitter. The day after the block, the total number of posts made in Turkey was up 138%, according to Brandwatch, an internet measurement firm.
After an April 2018 ban on the Telegram
Telegraphy is the long-distance transmission of messages where the sender uses symbolic codes, known to the recipient, rather than a physical exchange of an object bearing the message. Thus flag semaphore is a method of telegraphy, whereas pi ...
messaging app in Iran, web searches for VPN and other circumvention software increased as much as 48x for some search terms, but there was evidence that users were downloading unsafe software. As many as a third of Iranian internet users used the Psiphon tool in the days immediately following the block, and in June 2018 as many as 3.5 million Iranian users continued to use the tool.
Anonymity, risks, and trust
Circumvention andanonymity
Anonymity describes situations where the acting person's identity is unknown. Anonymity may be created unintentionally through the loss of identifying information due to the passage of time or a destructive event, or intentionally if a person cho ...
are different. Circumvention systems are designed to bypass blocking, but they do not usually protect identities. Anonymous systems protect a user's identity, and while they can contribute to circumvention, that is not their primary function. Open public proxy sites do not provide anonymity and can view and record the location of computers making requests as well as the websites accessed.
In many jurisdictions accessing blocked content is a serious crime
In ordinary language, a crime is an unlawful act punishable by a State (polity), state or other authority. The term ''crime'' does not, in modern criminal law, have any simple and universally accepted definition,Farmer, Lindsay: "Crime, definiti ...
, particularly content that is considered to be child pornography
Child pornography (also abbreviated as CP, also called child porn or kiddie porn, and child sexual abuse material, known by the acronym CSAM (underscoring that children can not be deemed willing participants under law)), is Eroticism, erotic ma ...
, a threat to national security
National security, or national defence (national defense in American English), is the security and Defence (military), defence of a sovereign state, including its Citizenship, citizens, economy, and institutions, which is regarded as a duty of ...
, or an incitement of violence. Thus it is important to understand the circumvention technologies and the protections they do or do not provide and to use only tools that are appropriate in a particular context. Great care must be taken to install, configure, and use circumvention tools properly. Individuals associated with high-profile rights organizations, dissident
A dissident is a person who actively challenges an established political or religious system, doctrine, belief, policy, or institution. In a religious context, the word has been used since the 18th century, and in the political sense since the 2 ...
, protest, or reform groups should take extra precautions to protect their online identities.
Circumvention sites and tools should be provided and operated by trusted third parties located outside the censoring jurisdiction that do not collect identities and other personal information. Trusted family and friends personally known to the circumventor are best, but when family and friends are not available, sites and tools provided by individuals or organizations that are only known by their reputations or through the recommendations and endorsement of others may need to be used. Commercial circumvention services may provide anonymity while surfing the Internet, but could be compelled by law to make their records and users' personal information available to law enforcement.
Software
There are five general types of Internet censorship circumvention software: CGI proxies use a script running on aweb server
A web server is computer software and underlying Computer hardware, hardware that accepts requests via Hypertext Transfer Protocol, HTTP (the network protocol created to distribute web content) or its secure variant HTTPS. A user agent, co ...
to perform the proxying function. A CGI proxy client sends the requested URL embedded within the data of HTTP requests to the CGI proxy server. The CGI proxy server sends out its own HTTP request to the ultimate destination, and then returns the result to the proxy client. A CGI proxy tool's security can be trusted as far as the operator of the proxy server can be trusted. CGI proxy tools require no manual configuration of the browser or client software installation, but they do require that the user use an alternative, potentially confusing browser interface within the existing browser.
HTTP proxies send HTTP requests
HTTP (Hypertext Transfer Protocol) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web, wher ...
through an intermediate proxying server. A client connecting through a HTTP proxy sends exactly the same HTTP request to the proxy as it would send to the destination server unproxied. The HTTP proxy parses the HTTP request; sends its own HTTP request to the ultimate destination server; and then returns the response back to the proxy client. An HTTP proxy tool's security can be trusted as far as the operator of the proxy server can be trusted. HTTP proxy tools require either manual configuration of the browser or client side software that can configure the browser for the user. Once configured, an HTTP proxy tool allows the user transparently to use his normal browser interface.
Application proxies are similar to HTTP proxies, but support a wider range of online applications.
Peer-to-peer
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network, forming a peer-to-peer network of Node ...
systems store content across a range of participating volunteer servers combined with technical techniques such as re-routing to reduce the amount of trust placed on volunteer servers or on social networks to establish trust relationships between server and client users. Peer-to-peer system can be trusted as far as the operators of the various servers can be trusted or to the extent that the architecture of the peer-to-peer system limits the amount of information available to any single server and the server operators can be trusted not to cooperate to combine the information they hold.
Re-routing systems send requests and responses through a series of proxying servers, encrypting the data again at each proxy, so that a given proxy knows at most either where the data came from or is going to, but not both. This decreases the amount of trust required of the individual proxy hosts.
Below is a list of different Internet censorship circumvention software:
See also
* Anonymous P2P * Bypassing content-control filters * Computer surveillance *Content-control software
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Such restrictions can be appl ...
* Crypto-anarchism
* Cypherpunk
*Electronic Frontier Foundation
The Electronic Frontier Foundation (EFF) is an American international non-profit digital rights group based in San Francisco, California. It was founded in 1990 to promote Internet civil liberties.
It provides funds for legal defense in court, ...
– an international non-profit digital rights advocacy and legal organization
* Freedom of information
*Freedom of speech
Freedom of speech is a principle that supports the freedom of an individual or a community to articulate their opinions and ideas without fear of retaliation, censorship, or legal sanction. The rights, right to freedom of expression has been r ...
* Global Internet Freedom Consortium (GIFC) – a consortium of organizations that develop and deploy anti-censorship technologies
* Bypassing the Great Firewall of China
*Internet freedom
Internet censorship is the legal censorship, control or suppression of what can be accessed, published, or viewed on the Internet. Censorship is most often applied to specific Network domain, internet domains (such as ''Wikipedia.org'', for exam ...
*Internet privacy
Internet privacy involves the right or mandate of personal privacy concerning the storage, re-purposing, provision to third parties, and display of information pertaining to oneself via the Internet. Internet privacy is a subset of data privacy. P ...
*Mesh networking
A mesh network is a local area network network topology, topology in which the infrastructure Node (networking), nodes (i.e. bridges, switches, and other infrastructure devices) connect directly, dynamically and non-hierarchically to as many othe ...
* Open Technology Fund (OTF) – a U.S. Government funded program created in 2012 at Radio Free Asia to support global Internet freedom technologies
* Proxy list
* Tactical Technology Collective – a non-profit foundation promoting the use of free and open source software for non-governmental organizations, and producers of NGO-in-A-Box
References
External links
*Casting A Wider Net: Lessons Learned in Delivering BBC Content on the Censored Internet
'', Ronald Deibert, Canada Centre for Global Security Studies and Citizen Lab, Munk School of Global Affairs, University of Toronto, 11 October 2011
Censorship Wikia
an anti-censorship site that catalogs past and present censored works, using verifiable sources, and a forum to discuss organizing against and circumventing censorship
"Circumvention Tool Evaluation: 2011"
Hal Roberts, Ethan Zuckerman, and John Palfrey, Berkman Centre for Internet & Society, 18 August 2011
"Circumvention Tool Usage Report: 2010"
Hal Roberts, Ethan Zuckerman, Jillian York, Robert Faris, and John Palfrey, Berkman Centre for Internet & Society, 14 October 2010
Digital Security and Privacy for Human Rights Defenders
by Dmitri Vitaliev, Published by Front Line – The International Foundation for the Protection of Human Rights Defenders
"Digital Tools to Curb Snooping"
''The New York Times'', 17 July 2013
Methods and Scripts useful for evading censorship through DNS filtering *
How to Bypass Internet Censorship
', also known by the titles: ''Bypassing Internet Censorship'' or ''Circumvention Tools'', a FLOSS Manual, 10 March 2011, 240 pp. Translations have been published i
Arabic
an
Vietnamese
"Leaping over the Firewall: A Review of Censorship Circumvention Tools"
, by Cormac Callanan (Ireland), Hein Dries-Ziekenheiner (Netherlands), Alberto Escudero-Pascual (Sweden), and Robert Guerra (Canada), Freedom House, April 2011
"Media Freedom Internet Cookbook"
by the OSCE Representative on Freedom of the Media, Vienna, 2004
"Online Survival Kit"
We Fight Censorship project of Reporters Without Borders
Free Haven Project, accessed 16 September 2011 {{DEFAULTSORT:Internet Censorship Circumvention Internet security Content-control software Internet censorship Internet privacy Circumvention