Blocklist (computing) on:
[Wikipedia]
[Google]
[Amazon]
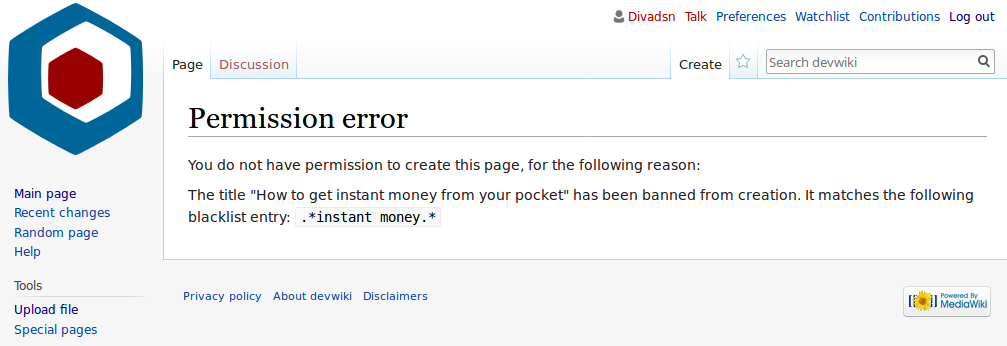 In
In
Email
Most email providers have an
Blackweb
* A
Password RBL
offers a password blacklist for Microsoft's
Squidblacklist.orgDomain BlacklistsFor Squid Proxy, and other web filtering platforms
ipfilterX by Nexus23 Labs{{dashBlocks P2P Crawlers, Malware C&C IPs, Institutions and many more
 In
In computing
Computing is any goal-oriented activity requiring, benefiting from, or creating computer, computing machinery. It includes the study and experimentation of algorithmic processes, and the development of both computer hardware, hardware and softw ...
, a blacklist, disallowlist, blocklist, or denylist is a basic access control
In physical security and information security, access control (AC) is the action of deciding whether a subject should be granted or denied access to an object (for example, a place or a resource). The act of ''accessing'' may mean consuming ...
mechanism that allows through all elements (email addresses, users, passwords, URLs, IP address
An Internet Protocol address (IP address) is a numerical label such as that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface i ...
es, domain name
In the Internet, a domain name is a string that identifies a realm of administrative autonomy, authority, or control. Domain names are often used to identify services provided through the Internet, such as websites, email services, and more. ...
s, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist
A whitelist or allowlist is a list or register of entities that are being provided a particular privilege, service, mobility, access or recognition. Entities on the list will be accepted, approved and/or recognized. Whitelisting is the reverse of ...
, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed.
Blacklists can be applied at various points in a security architecture, such as a host
A host is a person responsible for guests at an event or for providing hospitality during it.
Host may also refer to:
Places
* Host, Pennsylvania, a village in Berks County
* Host Island, in the Wilhelm Archipelago, Antarctica
People
* ...
, web proxy, DNS
The Domain Name System (DNS) is a hierarchical and distributed name service that provides a naming system for computers, services, and other resources on the Internet or other Internet Protocol (IP) networks. It associates various informatio ...
servers, email
Electronic mail (usually shortened to email; alternatively hyphenated e-mail) is a method of transmitting and receiving Digital media, digital messages using electronics, electronic devices over a computer network. It was conceived in the ...
server, firewall
Firewall may refer to:
* Firewall (computing), a technological barrier designed to prevent unauthorized or unwanted communications between computer networks or hosts
* Firewall (construction), a barrier inside a building, designed to limit the spre ...
, directory servers or application authentication gateways. The type of element blocked is influenced by the access control location. DNS servers may be well-suited to block domain names, for example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking malicious files or passwords.
Example uses include a company that might prevent a list of software from running on its network, a school that might prevent access to a list of websites from its computers, or a business that wants to ensure their computer users are not choosing easily guessed, poor passwords.
Examples of systems protected
Blacklists are used to protect a variety of systems in computing. The content of the blacklist is likely needs to be targeted to the type of system defended.Information systems
An information system includes end-point hosts like user machines and servers. A blacklist in this location may include certain types of software that are not allowed to run in the company environment. For example, a company might blacklist peer to peer file sharing on its systems. In addition to software, people, devices and Web sites can also be blacklisted.anti-spam
Various anti-spam techniques are used to prevent email spam (unsolicited bulk email).
No technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate email ( false positives) as opposed ...
feature that essentially blacklists certain email address An email address identifies an email box to which messages are delivered. While early messaging systems used a variety of formats for addressing, today, email addresses follow a set of specific rules originally standardized by the Internet Enginee ...
es if they are deemed unwanted. For example, a user who wearies of unstoppable emails from a particular address may blacklist that address, and the email client will automatically route all messages from that address to a junk-mail folder or delete them without notifying the user.
An e-mail spam
Email spam, also referred to as junk email, spam mail, or simply spam, refers to unsolicited messages sent in bulk via email. The term originates from a Monty Python sketch, where the name of a canned meat product, "Spam," is used repetitively, m ...
filter may keep a blacklist of email addresses, any mail from which would be prevented from reaching its intended destination. It may also use sending domain names or sending IP addresses to implement a more general block.
In addition to private email blacklists, there are lists that are kept for public use, including:
* China Anti-Spam Alliance
* Fabel Spamsources
* Spam and Open Relay Blocking System
* The DrMX Project
Web browsing
The goal of a blacklist in a web browser is to prevent the user from visiting a malicious or deceitful web page via filtering locally. A common web browsing blacklist is Google's Safe Browsing, which is installed by default in Firefox, Safari, and Chrome.Usernames and passwords
Blacklisting can also apply to user credentials. It is common for systems or websites to blacklist certain reserved usernames that are not allowed to be chosen by the system or website's user populations. These reserved usernames are commonly associated with built-in system administration functions. Also usually blocked by default are profane words and racial slurs. Password blacklists are very similar to username blacklists but typically contain significantly more entries than username blacklists. Password blacklists are applied to prevent users from choosing passwords that are easily guessed or are well known and could lead to unauthorized access by malicious parties. Password blacklists are deployed as an additional layer of security, usually in addition to a password policy, which sets the requirements of the password length and/or character complexity. This is because there are a significant number of password combinations that fulfill many password policies but are still easily guessed (i.e., Password123, Qwerty123).Distribution methods
Blacklists are distributed in a variety of ways. Some use simplemailing list
A mailing list is a collection of names and addresses used by an individual or an organization to send material to multiple recipients.
Mailing lists are often rented or sold. If rented, the renter agrees to use the mailing list only at contra ...
s. A DNSBL
A Domain Name System blocklist, Domain Name System-based blackhole list, Domain Name System blacklist (DNSBL) or real-time blackhole list (RBL) is a service for operation of mail servers to perform a check via a Domain Name System (DNS) query w ...
is a common distribution method that leverages the DNS
The Domain Name System (DNS) is a hierarchical and distributed name service that provides a naming system for computers, services, and other resources on the Internet or other Internet Protocol (IP) networks. It associates various informatio ...
itself. Some lists make use of rsync
rsync (remote sync) is a utility for transferring and synchronizing files between a computer and a storage drive and across networked computers by comparing the modification times and sizes of files. It is commonly found on Unix-like opera ...
for high-volume exchanges of data. Web-server functions may be used; either simple GET requests may be used or more complicated interfaces such as a RESTful
REST (Representational State Transfer) is a software architectural style that was created to describe the design and guide the development of the architecture for the World Wide Web. REST defines a set of constraints for how the architecture of ...
API.
Examples
* Companies likeGoogle
Google LLC (, ) is an American multinational corporation and technology company focusing on online advertising, search engine technology, cloud computing, computer software, quantum computing, e-commerce, consumer electronics, and artificial ...
, Symantec Symantec may refer to:
* Gen Digital, an American consumer software company formerly known as Symantec
* Symantec Security, a brand of enterprise security software purchased by Broadcom
Broadcom Inc. is an American multinational corporation, ...
and Sucuri keep internal blacklists of sites known to have malware and they display a warning before allowing the user to click them.
* Content-control software
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Such restrictions can be appl ...
such as DansGuardian and SquidGuard may work with a blacklist in order to block URLs of sites deemed inappropriate for a work or educational environment. Such blacklists can be obtained free of charge or from commercial vendors such as Squidblacklist.org.
* There are also free blacklists for Squid (software)
Squid is a caching and forwarding HTTP web proxy. It has a wide variety of uses, including speeding up a web server by caching repeated requests, caching World Wide Web (WWW), Domain Name System (DNS), and other network lookups for a group ...
proxy, such aBlackweb
* A
firewall
Firewall may refer to:
* Firewall (computing), a technological barrier designed to prevent unauthorized or unwanted communications between computer networks or hosts
* Firewall (construction), a barrier inside a building, designed to limit the spre ...
or IDS
IDS may refer to:
Computing
* IBM Informix Dynamic Server, a relational database management system
* Ideographic Description Sequence, describing a Unihan character as a combination of other characters
* Integrated Data Store, one of the first d ...
may also use a blacklist to block known hostile IP addresses and/or networks. An example for such a list would be the OpenBL project.
* Many copy protection
Copy protection, also known as content protection, copy prevention and copy restriction, is any measure to enforce copyright by preventing the reproduction of software, films, music, and other media.
Copy protection is most commonly found on vid ...
schemes include software blacklisting.
* The companPassword RBL
offers a password blacklist for Microsoft's
Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. Windows Server operating systems include it as a set of processes and services. Originally, only centralized domain management used Active Direct ...
, web sites and apps, distributed via a RESTful
REST (Representational State Transfer) is a software architectural style that was created to describe the design and guide the development of the architecture for the World Wide Web. REST defines a set of constraints for how the architecture of ...
API.
* Members of online auction
An online auction (also electronic auction, e-auction, virtual auction, or eAuction) is an auction held over the internet and accessed by internet connected devices. Similar to in-person auctions, online auctions come in a variety of types, with ...
sites may add other members to a personal blacklist. This means that they cannot bid on or ask questions about your auctions, nor can they use a "buy it now" function on your items.
* Yet another form of list is the yellow list which is a list of email server IP addresses that send mostly good email but do send some spam. Examples include Yahoo
Yahoo (, styled yahoo''!'' in its logo) is an American web portal that provides the search engine Yahoo Search and related services including My Yahoo, Yahoo Mail, Yahoo News, Yahoo Finance, Yahoo Sports, y!entertainment, yahoo!life, an ...
, Hotmail
Outlook.com, formerly Hotmail, is a free personal email service offered by Microsoft. It also provides a webmail interface accessible via web browser or mobile apps featuring mail, Calendaring software, calendaring, Address book, contacts, and ...
, and Gmail
Gmail is the email service provided by Google. it had 1.5 billion active user (computing), users worldwide, making it the largest email service in the world. It also provides a webmail interface, accessible through a web browser, and is also ...
. A yellow listed server is a server that should never be accidentally blacklisted. The yellow list is checked first and if listed then blacklist tests are ignored.
* In Linux
Linux ( ) is a family of open source Unix-like operating systems based on the Linux kernel, an kernel (operating system), operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically package manager, pac ...
modprobe
modprobe is a Linux program that provides for loading a loadable kernel module into a Linux kernel, unloading a loaded module and many other related features. It provides an ability to make decisions about which modules to load, awareness of modul ...
, the blacklist modulename entry in a modprobe configuration file indicates that all of the particular module's internal aliases are to be ignored. There are cases where two or more modules both support the same devices, or a module invalidly claims to support a device.
* Many web browsers have the ability to consult anti-phishing
Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information or installing malware such as viruses, worms, adware, or ransomware. Phishing attacks have become increasingly sophisticate ...
blacklists in order to warn users who unwittingly aim to visit a fraudulent website.
* Many peer-to-peer file sharing
Peer-to-peer file sharing is the distribution and sharing of digital media using peer-to-peer (P2P) networking technology. P2P file sharing allows users to access media files such as books, music, movies, and games using a P2P software program th ...
programs support blacklists that block access from sites known to be owned by companies enforcing copyright. An example is the Bluetack blocklist set.
Usage considerations
As expressed in a recent conference paper focusing on blacklists of domain names and IP addresses used for Internet security, "these lists generally do not intersect. Therefore, it appears that these lists do not converge on one set of malicious indicators." This concern combined with an economic model means that, while blacklists are an essential part of network defense, they need to be used in concert with whitelists and greylists.Controversy over terminology
Some major technology companies and institutions have publicly distanced themselves from the term ''blacklist'' due to a perceived connection withracism
Racism is the belief that groups of humans possess different behavioral traits corresponding to inherited attributes and can be divided based on the superiority of one Race (human categorization), race or ethnicity over another. It may also me ...
, instead recommending the terms ''denylist'' or ''blocklist''. The term's connection with racism, as well as the value in avoiding its use has been disputed.
References
External links
Squidblacklist.orgDomain BlacklistsFor Squid Proxy, and other web filtering platforms
ipfilterX by Nexus23 Labs{{dashBlocks P2P Crawlers, Malware C&C IPs, Institutions and many more
Computing
Computing is any goal-oriented activity requiring, benefiting from, or creating computer, computing machinery. It includes the study and experimentation of algorithmic processes, and the development of both computer hardware, hardware and softw ...
Computer jargon