|
Unicast Flood
In computer networking, a unicast flood occurs when a switch receives a unicast frame and the switch does not know that the addressee is on any particular switch port. Since the switch has no information regarding which port, if any, the addressee might be reached through, it forwards the frame through all ports aside from the one through which the frame was received. Background ''Unicast'' refers to a one-to-one transmission from one node in a network to another. This diagram illustrates the unicast transmission of a frame from one network node to another: center, 200px When a switch receives a unicast frame with a destination address not in the switch’s forwarding table, the frame is treated like a broadcast frame and sent to all network segments to which it is attached except the one from which it received the frame: center, 200px Causes The learning process of transparent bridging requires that the switch receive a frame from a device before unicast frames can be forwarde ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or by wireless communication. The devices may be connected in a variety of network topologies. In order to communicate over the network, computers use agreed-on rules, called communication protocols, over whatever medium is used. The computer network can include personal computers, Server (computing), servers, networking hardware, or other specialized or general-purpose Host (network), hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MAC Address
A MAC address (short for medium access control address or media access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use is common in most IEEE 802 networking technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the Open Systems Interconnection (OSI) network model, MAC addresses are used in the medium access control protocol sublayer of the data link layer. As typically represented, MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or without a separator. MAC addresses are primarily assigned by device manufacturers, and are therefore often referred to as the burned-in address, or as an Ethernet hardware address, hardware address, or physical address. Each address can be stored in the interface hardware, such as its read-only memory, or by a firmware mechanism. Many network interfaces, however, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Packet Sniffer
A packet analyzer (also packet sniffer or network analyzer) is a computer program or computer hardware such as a packet capture appliance that can Traffic analysis, analyze and Logging (computing), log traffic that passes over a computer network or part of a network. Packet capture is the process of intercepting and logging traffic. As data streams flow across the network, the analyzer captures each Network packet, packet and, if needed, decodes the packet's raw data, showing the values of various fields in the packet, and analyzes its content according to the appropriate Request for Comments, RFC or other specifications. A packet analyzer used for intercepting traffic on wireless networks is known as a wireless analyzer - those designed specifically for Wi-Fi networks are Wi-Fi analyzers. While a packet analyzer can also be referred to as a Network analyzer (other), network analyzer or protocol analyzer these terms can also have other meanings. Protocol analyzer can t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
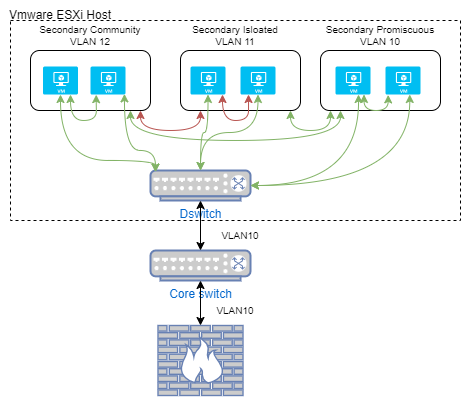
Private VLAN
Private VLAN, also known as port isolation, is a technique in computer networking where a VLAN contains network switch, switch ports that are restricted such that they can only communicate with a given uplink. The restricted ports are called ''private ports''. Each private VLAN typically contains many private ports, and a single uplink. The uplink will typically be a port (or link aggregation group) connected to a router (computing), router, Firewall (computing), firewall, server (computing), server, Internet service provider, provider network, or similar central resource. The concept was primarily introduced as a result of the limitation on the number of VLANs in network switches, a limit quickly exhausted in highly scaled scenarios. Hence, there was a requirement to create multiple network segregations with a minimum number of VLANs. The switch forwards all frame (telecommunications), frames received from a private port to the uplink port, regardless of VLAN ID or destinatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Layer 2
The data link layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. The data link layer provides the functional and procedural means to transfer data between network entities and may also provide the means to detect and possibly correct errors that can occur in the physical layer. The data link layer is concerned with local delivery of frames between nodes on the same level of the network. Data-link frames, as these protocol data units are called, do not cross the boundaries of a local area network. Inter-network routing and global addressing are higher-layer functions, allowing data-link protocols to focus on local delivery, addressing, and media arbitration. In this way, the data link layer is analogous to a neighborhood traffic cop; it endeavors to arbitrate between parties contending for access to a medium, without con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ARP Cache
An ARP cache is a collection of Address Resolution Protocol entries (mostly dynamic), that are created when an IP address is resolved to a MAC address (so the computer can effectively communicate with the IP address). The term can be used interchangeably with ARP table, although the latter is sometimes a distinct statically configured table. An ARP cache has the disadvantage of potentially being used by hackers and cyberattackers (an ARP cache poisoning In computer networking, ARP spoofing (also ARP cache poisoning or ARP poison routing) is a technique by which an attacker sends ( spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate t ... attack). An ARP cache helps the attackers hide behind a fake IP address. Beyond the fact that ARP caches may help attackers, it may also prevent the attacks by "distinguish ngbetween low level IP and IP based vulnerabilities". References Address Resolution Protocol Computer networ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rapid Spanning Tree
The Spanning Tree Protocol (STP) is a network protocol that builds a loop-free logical topology for Ethernet networks. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include backup links providing fault tolerance if an active link fails. As the name suggests, STP creates a spanning tree that characterizes the relationship of nodes within a network of connected layer-2 bridges, and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation. In 2001, the IEEE introduced Rapid Spanning Tree Protocol (RSTP) as 802.1w. RSTP provides significantly faster recovery in response to network changes or failures, introducing new convergence behaviors and bridge port roles to do this. RSTP was designed to be bac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Address Resolution Protocol
The Address Resolution Protocol (ARP) is a communication protocol for discovering the link layer address, such as a MAC address, associated with a internet layer address, typically an IPv4 address. The protocol, part of the Internet protocol suite, was defined in 1982 by , which is Internet Standard STD 37. ARP enables a host to send an IPv4 packet to another node in the local network by providing a protocol to get the MAC address associated with an IP address. The host broadcasts a request containing the node's IP address, and the node with that IP address replies with its MAC address. ARP has been implemented with many combinations of network and data link layer technologies, such as IPv4, Chaosnet, DECnet and Xerox PARC Universal Packet (PUP) using IEEE 802 standards, FDDI, X.25, Frame Relay and Asynchronous Transfer Mode (ATM). In Internet Protocol Version 6 (IPv6) networks, the functionality of ARP is provided by the Neighbor Discovery Protocol (NDP). Operating scope T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unicast
Unicast is data transmission from a single sender (red) to a single receiver (green). Other devices on the network (yellow) do not participate in the communication. In computer networking, unicast is a one-to-one transmission from one point in the network to another point; that is, one sender and one receiver, each identified by a network address. Unicast is in contrast to multicast and broadcast which are one-to-many transmissions. Internet Protocol unicast delivery methods such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are typically used. See also * Anycast * Broadcast, unknown-unicast and multicast traffic * IP address * IP multicast * Routing Routing is the process of selecting a path for traffic in a Network theory, network or between or across multiple networks. Broadly, routing is performed in many types of networks, including circuit-switched networks, such as the public switched ... References External links * Internet archit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MAC Flooding
In computer networking, a media access control attack or MAC flooding is a technique employed to compromise the security of network switches. The attack works by forcing legitimate MAC table contents out of the switch and forcing a unicast flooding behavior potentially sending sensitive information to portions of the network where it is not normally intended to go. Attack method Switches maintain a MAC table that maps individual MAC addresses on the network to the physical ports on the switch. This allows the switch to direct data out of the physical port where the recipient is located, as opposed to indiscriminately broadcasting the data out of all ports as an Ethernet hub does. The advantage of this method is that data is bridged exclusively to the network segment containing the computer that the data is specifically destined for. In a typical MAC flooding attack, a switch is fed many Ethernet frames, each containing a different source MAC address, by the attacker. The in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forwarding Information Base
A forwarding information base (FIB), also known as a forwarding table or MAC (address) table, is most commonly used in network bridging, routing, and similar functions to find the proper output network interface controller to which the input interface should forward a packet. It is a dynamic table that maps MAC addresses to ports. It is the essential mechanism that separates network switches from Ethernet hubs. Content-addressable memory (CAM) is typically used to efficiently implement the FIB, thus it is sometimes called a CAM table. Applications at data link layer At the data link layer, a FIB is most notably used to facilitate Ethernet bridging based on MAC addresses. Other data-link-layer technologies using FIBs include Frame Relay, Asynchronous Transfer Mode (ATM) and Multiprotocol Label Switching (MPLS). Bridging The role of an Ethernet switch is to forward Ethernet frames from one port to another. The presence of a FIB is one attribute that separates a switch from a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |