|
Symbolic Links
In computing, a symbolic link (also symlink or soft link) is a file whose purpose is to point to a file or directory (called the "target") by specifying a path thereto. Symbolic links are supported by POSIX and by most Unix-like operating systems, such as FreeBSD, Linux, and macOS. Limited support also exists in Windows 7 and Windows Vista, and to some degree in Windows 2000 and Windows XP in the form of shortcut files. CTSS on IBM 7090 had files linked by name in 1963. By 1978 minicomputer operating systems from DEC, and in Data General's RDOS included symbolic links. Overview A symbolic link contains a text string that is automatically interpreted and followed by the operating system as a path to another file or directory. This other file or directory is called the "target". The symbolic link is a second file that exists independently of its target. If a symbolic link is deleted, its target remains unaffected. If a symbolic link points to a target, and sometime later that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computing
Computing is any goal-oriented activity requiring, benefiting from, or creating computing machinery. It includes the study and experimentation of algorithmic processes, and development of both hardware and software. Computing has scientific, engineering, mathematical, technological and social aspects. Major computing disciplines include computer engineering, computer science, cybersecurity, data science, information systems, information technology and software engineering. The term "computing" is also synonymous with counting and calculating. In earlier times, it was used in reference to the action performed by mechanical computing machines, and before that, to human computers. History The history of computing is longer than the history of computing hardware and includes the history of methods intended for pen and paper (or for chalk and slate) with or without the aid of tables. Computing is intimately tied to the representation of numbers, though mathematical ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
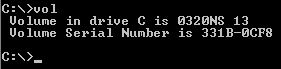
Volume (computing)
In computer data storage, a volume or logical drive is a single accessible storage area with a single file system, typically (though not necessarily) resident on a single partition of a hard disk. Although a volume might be different from a physical disk drive, it can still be accessed with an operating system's logical interface. However, a volume differs from a partition. Differences from partition A volume is not the same thing as a partition. For example, a floppy disk might be accessible as a volume, even though it does not contain a partition, as floppy disks cannot be partitioned with most modern computer software. Also, an OS can recognize a partition without recognizing any volume associated with it, as when the OS cannot interpret the filesystem stored there. This situation occurs, for example, when Windows NT-based OSes encounter disks with non-Microsoft OS partitions, such as the ext3 filesystem commonly used with Linux. Another example occurs in the Intel world w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rm (Unix)
rm (short for ''remove'') is a basic command on Unix and Unix-like operating systems used to remove objects such as computer files, directories and symbolic links from file systems and also special files such as device nodes, pipes and sockets, similar to the del command in MS-DOS, OS/2, and Microsoft Windows. The command is also available in the EFI shell. Overview The rm command removes references to objects from the filesystem using the unlink system call, where those objects might have had multiple references (for example, a file with two different names), and the objects themselves are discarded only when all references have been removed and no programs still have open handles to the objects. This allows for scenarios where a program can open a file, immediately remove it from the filesystem, and then use it for temporary space, knowing that the file's space will be reclaimed after the program exits, even if it exits by crashing. The command generally does not destroy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unlink (Unix)
In Unix-like operating systems, unlink is a system call and a command line utility to delete files. The program directly interfaces the system call, which removes the file name and (but not on GNU systems) directories like rm and rmdir. If the file name was the last hard link to the file, the file itself is deleted as soon as no program has it open. It also appears in the PHP, Node.js, R, Perl and Python standard libraries in the form of the ''unlink()'' built-in function. Like the Unix utility, it is also used to delete files. Example To delete a file named ''foo'', one could type: % unlink foo In PHP, one could use the following function to do the same: unlink("foo"); The Perl syntax is identical to the PHP syntax, save for the parentheses: unlink "foo"; In Node.js it is almost the same as the others: fs.unlink("foo", callback); In R (with the S language compatibility): unlink("foo") #Comment: using the inside argument 'recursive = TRUE', directories can b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Find (Unix)
In Unix-like and some other operating systems, find is a command-line utility that locates files based on some user-specified criteria and either prints the pathname of each matched object or, if another action is requested, performs that action on each matched object. It initiates a search from a desired starting location and then recursively traverses the nodes (directories) of a hierarchical structure (typically a tree). find can traverse and search through different file systems of partitions belonging to one or more storage devices mounted under the starting directory. The possible search criteria include a pattern to match against the filename or a time range to match against the modification time or access time of the file. By default, find returns a list of all files below the current working directory, although users can limit the search to any desired maximum number of levels under the starting directory. The related locate programs use a database of indexed fil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command-line Interface
A command-line interpreter or command-line processor uses a command-line interface (CLI) to receive commands from a user in the form of lines of text. This provides a means of setting parameters for the environment, invoking executables and providing information to them as to what actions they are to perform. In some cases the invocation is conditional based on conditions established by the user or previous executables. Such access was first provided by computer terminals starting in the mid-1960s. This provided an interactive environment not available with punched cards or other input methods. Today, many users rely upon graphical user interfaces and menu-driven interactions. However, some programming and maintenance tasks may not have a graphical user interface and use a command line. Alternatives to the command-line interface include text-based user interface menus (for example, IBM AIX SMIT), keyboard shortcuts, and various desktop metaphors centered on the pointer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Systems Research Group
The Computer Systems Research Group (CSRG) was a research group at the University of California, Berkeley that was dedicated to enhancing AT&T Unix operating system and funded by Defense Advanced Research Projects Agency. History Professor Bob Fabry of Berkeley acquired a UNIX source license from AT&T in 1974. His group started to modify UNIX, and distributed their version as the Berkeley Software Distribution (BSD). In April 1980, Fabry signed a contract with DARPA to develop UNIX even further and accommodate the specific requirements of the ARPAnet. With this funding, Fabry created the Computer Systems Research Group. The Berkeley Sockets API and Berkeley Fast File System are some of the group's most significant innovations. The sockets interface solved the problem of supporting multiple protocols (e.g. XNS and TCP/IP), and extended UNIX's "everything is a file" notion to these network protocols, while the Fast File System increased the block allocation size from 512 by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Berkeley Software Distribution
The Berkeley Software Distribution or Berkeley Standard Distribution (BSD) is a discontinued operating system based on Research Unix, developed and distributed by the Computer Systems Research Group (CSRG) at the University of California, Berkeley. The term "BSD" commonly refers to its open-source descendants, including FreeBSD, OpenBSD, NetBSD, and DragonFly BSD. BSD was initially called Berkeley Unix because it was based on the source code of the original Unix developed at Bell Labs. In the 1980s, BSD was widely adopted by workstation vendors in the form of proprietary Unix variants such as DEC Ultrix and Sun Microsystems SunOS due to its permissive licensing and familiarity to many technology company founders and engineers. Although these proprietary BSD derivatives were largely superseded in the 1990s by UNIX SVR4 and OSF/1, later releases provided the basis for several open-source operating systems including FreeBSD, OpenBSD, NetBSD, DragonFly BSD, Darwi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ln (Unix)
The command is a standard Unix command utility used to create a hard link or a symbolic link (symlink) to an existing file or directory. The use of a hard link allows multiple filenames to be associated with the same file since a hard link points to the inode of a given file, the data of which is stored on disk. On the other hand, symbolic links are special files that refer to other files by name. The command by default creates hard links, and when called with the command line parameter creates symbolic links. Most operating systems prevent hard links to directories from being created since such a capability could disrupt the structure of a file system and interfere with the operation of other utilities. The command can however be used to create symbolic links to non-existent files. History ln appeared in Issue 2 of the X/Open Portability Guidelines. The version of bundled in GNU coreutils was written by Mike Parker and David MacKenzie. The command is available as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Directory Tree
In computing, a directory is a file system cataloging structure which contains references to other computer files, and possibly other directories. On many computers, directories are known as folders, or drawers, analogous to a workbench or the traditional office filing cabinet. The name derives from books like a telephone directory that lists the phone numbers of all the people living in a certain area. Files are organized by storing related files in the same directory. In a hierarchical file system (that is, one in which files and directories are organized in a manner that resembles a tree), a directory contained inside another directory is called a subdirectory. The terms parent and child are often used to describe the relationship between a subdirectory and the directory in which it is cataloged, the latter being the parent. The top-most directory in such a filesystem, which does not have a parent of its own, is called the root directory. Overview Historically, and even ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Heuristic
A heuristic (; ), or heuristic technique, is any approach to problem solving or self-discovery that employs a practical method that is not guaranteed to be optimal, perfect, or rational, but is nevertheless sufficient for reaching an immediate, short-term goal or approximation. Where finding an optimal solution is impossible or impractical, heuristic methods can be used to speed up the process of finding a satisfactory solution. Heuristics can be mental shortcuts that ease the cognitive load of making a decision. Examples that employ heuristics include using trial and error, a rule of thumb or an educated guess. Heuristics are the strategies derived from previous experiences with similar problems. These strategies depend on using readily accessible, though loosely applicable, information to control problem solving in human beings, machines and abstract issues. When an individual applies a heuristic in practice, it generally performs as expected. However it can alternativ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |