|
Security-focused Operating System
This is a list of operating systems specifically focused on security. Operating systems for general-purpose usage may be secure without having a specific focus on security. Similar concepts include security-evaluated operating systems that have achieved certification from an auditing organization, and trusted operating systems that provide sufficient support for multilevel security and evidence of correctness to meet a particular set of requirements. Linux Android-based * Android in general is very secure, having many security features such as taking advantage of SELinux and Verified Boot. * CalyxOS is a free and open source privacy and security focused Android Custom ROM * DivestOS is a free and open source privacy and security focused Android Custom ROM * GrapheneOS is an open source privacy and security focused Android Custom ROM * Kali NetHunter is a free and open source Kali Linux based Android Custom ROM for penetration testing Debian-based * Subgraph ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs. Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computer from cellular phones and video game consoles to web servers and supercomputers. The dominant general-purpose personal computer operating system is Microsoft Windows with a market share of around 74.99%. macOS by Apple Inc. is in second place (14.84%), ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
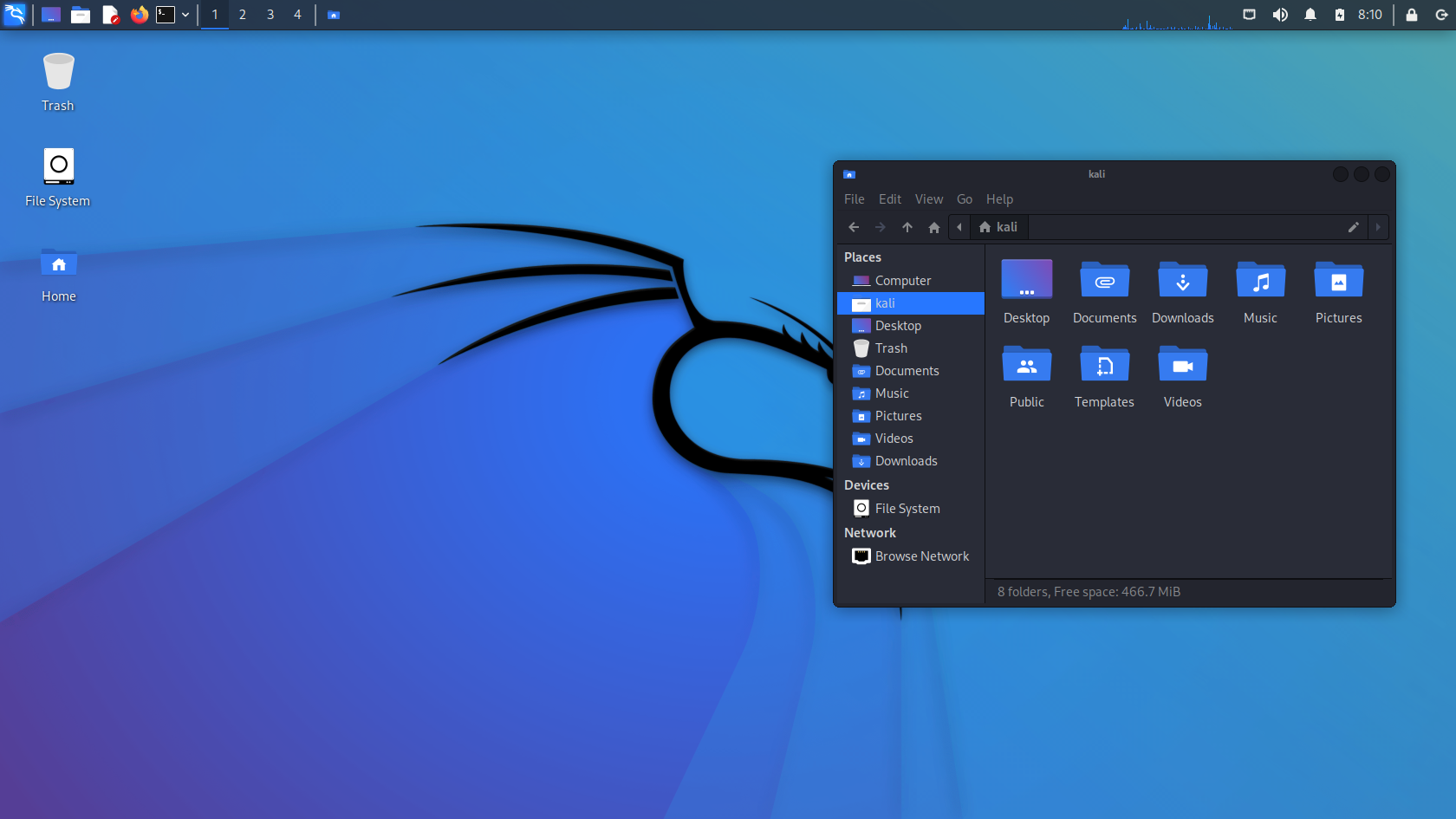
Kali Linux
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security. Kali Linux has around 600 penetration-testing programs (tools), including Armitage (a graphical cyber attack management tool), Nmap (a port scanner), Wireshark (a packet analyzer), metasploit (penetration testing framework), John the Ripper (a password cracker), sqlmap (automatic SQL injection and database takeover tool), Aircrack-ng (a software suite for penetration-testing wireless LANs), Burp suite and OWASP ZAP web application security scanners, etc. It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of BackTrack, their previous information security testing Linux distribution based on Knoppix. The name was inspired by the Hindu goddess Kali. Kali Linux is based on the Debian ''Testing'' branch. Most packages Kali uses are imported from the Debian repositories. Kali Linux's po ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VirtualBox
Oracle VM VirtualBox (formerly Sun VirtualBox, Sun xVM VirtualBox and Innotek VirtualBox) is a type-2 hypervisor for x86 virtualization developed by Oracle Corporation. VirtualBox was originally created by Innotek GmbH, which was acquired by Sun Microsystems in 2008, which was in turn acquired by Oracle in 2010. VirtualBox may be installed on Microsoft Windows, macOS, Linux, Solaris and OpenSolaris. There are also ports to FreeBSD and Genode. It supports the creation and management of guest virtual machines running Windows, Linux, BSD, OS/2, Solaris, Haiku, and OSx86, as well as limited virtualization of guests on Apple hardware. For some guest operating systems, a "Guest Additions" package of device drivers and system applications is available, which typically improves performance, especially that of graphics, and allows changing the resolution of the guest OS automatically when the window of the virtual machine on the host OS is resized. Released under the terms of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Whonix
Whonix (, ) is a Kicksecure–based security hardened Linux distribution. Its main goals are to provide strong privacy and anonymity on the Internet. The operating system consists of two virtual machines, a "Workstation" and a Tor "Gateway", running Debian GNU/Linux. All communications are forced through the Tor network. Both Whonix and Kicksecure have documentation which spans from basic operating system maintenance to more advanced topics. History The first iteration, TorBOX (February-July 2012) The initial concept was announced by Schleizer under the pseudonym ''Proper'', and later changed to ''Adrelanos in 2012 before revealing his identity in 2014''. His idea was to leverage a virtual machine acting as a transparent proxy to route all Internet traffic through the Tor network. This would have allowed to mask one's IP address, prevent DNS leaks and avoid having to configure proxy settings for individual applications (or ones who do not support them). TorBOX was at it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random-access Memory
Random-access memory (RAM; ) is a form of computer memory that can be read and changed in any order, typically used to store working data and machine code. A random-access memory device allows data items to be read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks, CD-RWs, DVD-RWs and the older magnetic tapes and drum memory), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. RAM contains multiplexing and demultiplexing circuitry, to connect the data lines to the addressed storage for reading or writing the entry. Usually more than one bit of storage is accessed by the same address, and RAM devices often have multiple data lines and are said to be "8-bit" or "16-bit", etc. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tails (operating System)
Tails, or The Amnesic Incognito Live System, is a security-focused Debian-based Linux distribution aimed at preserving privacy and anonymity. It connects to the Internet exclusively through the anonymity network Tor. The system is designed to be booted as a live DVD or live USB, and leaves no digital footprint on the machine unless explicitly told to do so. It can also be run as a virtual machine, with some additional security risks. The Tor Project provided financial support for its development in the beginnings of the project, and continues to do so alongside numerous corporate and anonymous sponsors. History Tails was first released on June 23, 2009. It is the next iteration of development on Incognito, a discontinued Gentoo-based Linux distribution. The Tor Project provided financial support for its development in the beginnings of the project. Tails also received funding from the Open Technology Fund, Mozilla, and the Freedom of the Press Foundation. Laura Poi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tor (anonymity Network)
Tor, short for The Onion Router, is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, to conceal a user's location and usage from anyone performing network surveillance or traffic analysis. Using Tor makes it more difficult to trace a user's Internet activity. Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to communicate confidentially through IP address anonymity using Tor exit nodes. History The core principle of Tor, onion routing, was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag, to protect American intelligence communications online. Onion routing is implemented by means of encryption in the application layer of the communication protoc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Xpra
xpra, abbreviated from X Persistent Remote Applications, is a set of software utilities that run X clients, typically on a remote host, and direct their display to the local machine without the X clients closing or losing any state in case the network connection between the local machine and the remote host is lost. Xpra differs from standard ''X forwarding'' primarily in allowing disconnection and reconnection without disrupting the forwarded application. It also differs from VNC and similar remote display technologies in being ''rootless'', so applications forwarded by Xpra appear on the local desktop as normal windows managed by the local window manager, rather than being all "trapped in a box together". Xpra also uses a custom protocol that is self-tuning and relatively latency-insensitive, and thus is usable over worse links than standard X. The original inspiration for making Xpra came from the original author's experience of attempting to use various setups based on NX ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux Namespaces
Namespaces are a feature of the Linux kernel that partitions kernel resources such that one set of processes sees one set of resources while another set of processes sees a different set of resources. The feature works by having the same namespace for a set of resources and processes, but those namespaces refer to distinct resources. Resources may exist in multiple spaces. Examples of such resources are process IDs, host-names, user IDs, file names, and some names associated with network access, and Inter-process communication. Namespaces are a fundamental aspect of containers in Linux. The term "namespace" is often used for a type of namespace (e.g. process ID) as well as for a particular space of names. A Linux system starts out with a single namespace of each type, used by all processes. Processes can create additional namespaces and also join different namespaces. History Linux namespaces were inspired by the wider namespace functionality used heavily throughout ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deterministic Compilation
Reproducible builds, also known as deterministic compilation, is a process of compiling software which ensures the resulting binary code can be reproduced. Source code compiled using deterministic compilation will always output the same binary. Reproducible builds can act as part of a chain of trust; the source code can be signed, and deterministic compilation can prove that the binary was compiled from trusted source code. Methods For the compilation process to be deterministic, the input to the compiler must be the same, regardless of the build environment used. This typically involves normalizing variables that may change, such as order of input files, timestamps, locales, and paths. Additionally, the compilers must not introduce non-determinism themselves. This sometimes happens when using hash tables with a random hash seed value. It can also happen when using the address of variables because that varies from address space layout randomization (ASLR). Build systems, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception. Surveillance is used by citizens for protecting their neighborhoods. And by governments for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to gather intelligence on criminals, their competitors, suppliers or customers. Religious organisations charged with detecting heresy and heterodoxy may also carry out surveillance. Auditors ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |