|
Stuxnet
Stuxnet is a Malware, malicious computer worm first uncovered on June 17, 2010, and thought to have been in development since at least 2005. Stuxnet targets supervisory control and data acquisition (SCADA) systems and is believed to be responsible for causing substantial damage to the nuclear program of Iran, Iran nuclear program. Although neither the United States nor Israel has openly admitted responsibility, multiple independent news organizations claim Stuxnet to be a cyberweapon built jointly by the two countries in a collaborative effort known as Operation Olympic Games. The program, started during the Presidency of George W. Bush, Bush administration, was rapidly expanded within the first months of Barack Obama's presidency. Stuxnet specifically targets programmable logic controllers (PLCs), which allow the automation of electromechanical processes such as those used to control machinery and industrial processes including gas centrifuges for separating nuclear material. Exp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Equation Group
The Equation Group, also known in China as APT-C-40, is a highly sophisticated Threat (computer)#Threat agents or actors, threat actor suspected of being tied to the Tailored Access Operations (TAO) unit of the United States National Security Agency (NSA). Kaspersky Labs describes them as one of the most sophisticated Advanced persistent threat, advanced persistent threats in the world and "the most advanced (...) we have seen", operating alongside the creators of Stuxnet and Flame (malware), Flame. Most of their targets have been in Iran, Russia, Pakistan, Afghanistan, India, Syria and Mali. The name originated from the group's extensive use of encryption. By 2015, Kaspersky documented 500 malware infections by the group in at least 42 countries, while acknowledging that the actual number could be in the tens of thousands due to its self-terminating protocol. In 2017, WikiLeaks Vault 7, published a discussion held within the Central Intelligence Agency, CIA on how it had been po ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kaspersky Lab
Kaspersky Lab (; ) is a Russian multinational cybersecurity and anti-virus provider headquartered in Moscow, Russia, and operated by a holding company in the United Kingdom. It was founded in 1997 by Eugene Kaspersky, Natalya Kaspersky and Alexey De-Monderik. Kaspersky Lab develops and sells antivirus, internet security, password management, endpoint security, and other cybersecurity products and services. Kaspersky expanded abroad from 2005 to 2010 and grew to $704 million in annual revenues by 2020, up 8% from 2016, though annual revenues were down 8% in North America due to US government security concerns. the software has about 400 million users and has the largest market-share of cybersecurity software vendors in Europe. Kaspersky Lab ranks fourth in the global ranking of antivirus vendors by revenue. It was the first Russian company to be included into the rating of the world's leading software companies, called the Software Top 100 (79th on the list, as of June ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberweapon
Cyberweapons are commonly defined as malware agents employed for military, paramilitary, or intelligence objectives as part of a cyberattack. This includes computer viruses, trojans, spyware, and worms that can introduce malicious code into existing software, causing a computer to perform actions or processes unintended by its operator. Characteristics A cyberweapon is usually sponsored or employed by a state or non-state actor, meets an objective that would otherwise require espionage or the use of force, and is employed against specific targets. A cyberweapon performs an action that would normally require a soldier or spy, and which would be considered either illegal or an act of war if performed directly by a human agent of the sponsor during peacetime. Legal issues include violating the privacy of the target and the sovereignty of its host nation. Example of such actions are surveillance, data theft and electronic or physical destruction. While a cyberweapon almost ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operation Olympic Games
Operation Olympic Games was an black operation, unacknowledged campaign of sabotage by means of cyber disruption, directed at Iranian Nuclear program of Iran, nuclear facilities by the United States and Israel. As reported, it is one of the first known uses of offensive Cyberwarfare, cyber weapons. Started under the Presidency of George W. Bush, administration of George W. Bush in 2006, Olympic Games was accelerated under Barack Obama, President Obama, who heeded Bush's advice to continue cyber attacks on the Iranian nuclear facility at Natanz. Bush believed that the strategy was the only way to prevent an Israeli conventional Iran–Israel relations#Israel threatening Iran, strike on Iranian nuclear facilities. History During Bush's second term, General James Cartwright, then head of United States Strategic Command, along with other intelligence officials presented Bush with sophisticated code that would act as an offensive cyber weapon. "The goal was to gain access to the Natanz ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Worm
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer. Many worms are designed only to spread, and do not attempt to change the systems they pass thro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nuclear Program Of Iran
The nuclear program of Iran is one of the most scrutinized nuclear programs in the world. The military capabilities of the program are possible through its mass enrichment activities in facilities such as Natanz and Arak. In June 2025, the International Atomic Energy Agency (IAEA) found Iran non-compliant with its nuclear obligations for the first time in 20 years. Iran retaliated by launching a new enrichment site and installing advanced centrifuges. Iran's nuclear program began in the 1950s under the Pahlavi dynasty with US support. It expanded in the 1970s with plans for power reactors, paused after the 1979 Iranian Revolution, and resumed secretly during the 1980s Iran–Iraq War. In the 1990s, Iran pursued a full nuclear fuel cycle and acquired centrifuge technology through illicit networks, including ties with Pakistan and North Korea. Undeclared enrichment sites at Natanz and Arak were exposed in 2002, and Fordow, an underground fuel enrichment site, was reveale ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Supervisory Control And Data Acquisition
SCADA (an acronym for supervisory control and data acquisition) is a control system architecture comprising computers, networked data communications and graphical user interfaces for high-level supervision of machines and processes. It also covers sensors and other devices, such as programmable logic controllers, also known as a DCS (Distributed Control System), which interface with process plant or machinery. The operator interfaces, which enable monitoring and the issuing of process commands, such as controller setpoint changes, are handled through the SCADA computer system. The subordinated operations, e.g. the real-time control logic or controller calculations, are performed by networked modules connected to the field sensors and actuators. The SCADA concept was developed to be a universal means of remote-access to a variety of local control modules, which could be from different manufacturers and allowing access through standard automation protocols. In practice, large SCA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to cause disruption to a computer, server (computing), server, Client (computing), client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types (i.e. computer viruses, Computer worm, worms, Trojan horse (computing), Trojan horses, logic bombs, ransomware, spyware, adware, rogue software, Wiper (malware), wipers and keyloggers). Malware poses serious problems to individuals and businesses on the Internet. According to NortonLifeLock, Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 66 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zero-day Vulnerability
A zero-day (also known as a 0-day) is a vulnerability or security hole in a computer system unknown to its developers or anyone capable of mitigating it. Until the vulnerability is remedied, threat actors can exploit it in a zero-day exploit, or zero-day attack. The term "zero-day" originally referred to the number of days since a new piece of software was released to the public, so "zero-day software" was obtained by hacking into a developer's computer before release. Eventually the term was applied to the vulnerabilities that allowed this hacking, and to the number of days that the vendor has had to fix them. Vendors who discover the vulnerability may create patches or advise workarounds to mitigate it – though users need to deploy that mitigation to eliminate the vulnerability in their systems. Zero-day attacks are severe threats. Definition Despite developers' goal of delivering a product that works entirely as intended, virtually all software and hardware contain bugs. I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Programmable Logic Controller
A programmable logic controller (PLC) or programmable controller is an industrial computer that has been ruggedized and adapted for the control of manufacturing processes, such as assembly lines, machines, robotic devices, or any activity that requires high reliability, ease of programming, and process fault diagnosis. PLCs can range from small modular devices with tens of Input/output, inputs and outputs (I/O), in a housing integral with the processor, to large rack-mounted modular devices with thousands of I/O, and which are often networked to other PLC and SCADA systems. They can be designed for many arrangements of digital and analog I/O, extended temperature ranges, immunity to electrical noise, and resistance to vibration and impact. PLCs were first developed in the automobile manufacturing industry to provide flexible, rugged and easily programmable controllers to replace hard-wired relay logic systems. Dick Morley, who invented the first PLC, the Modicon 084, for Gene ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
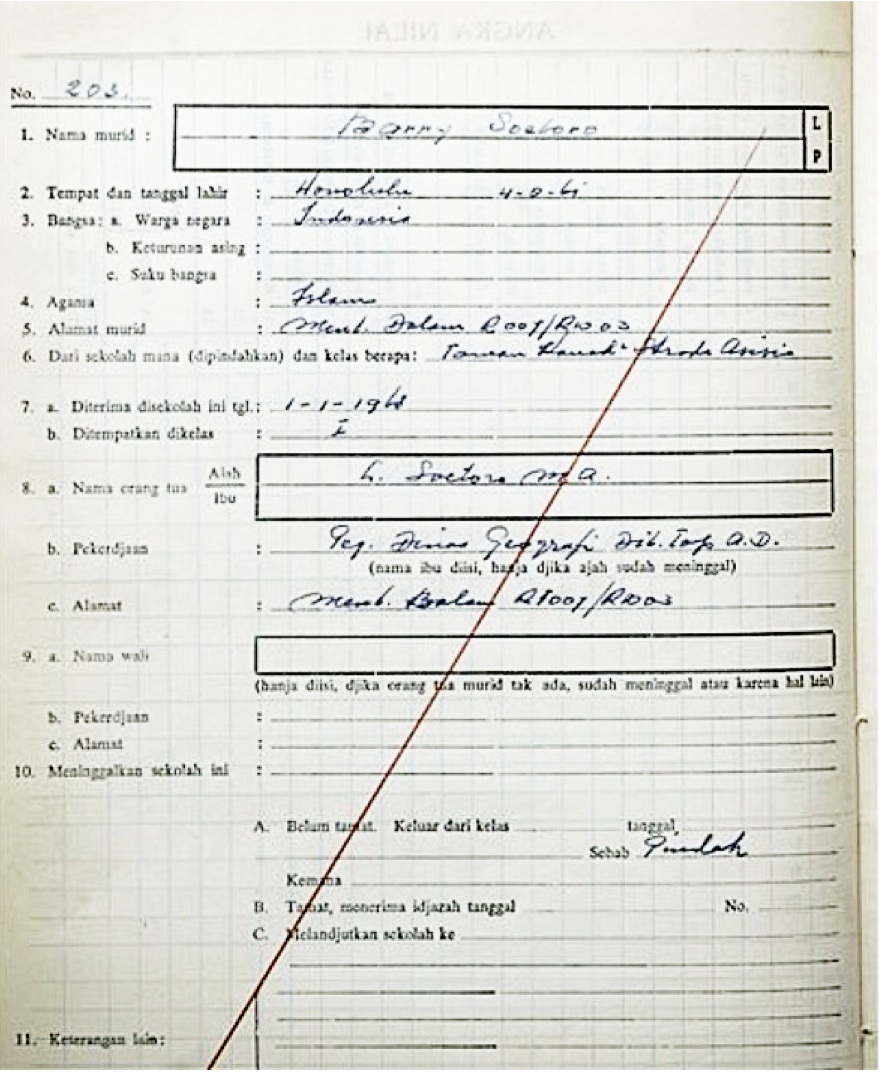
Barack Obama
Barack Hussein Obama II (born August 4, 1961) is an American politician who was the 44th president of the United States from 2009 to 2017. A member of the Democratic Party, he was the first African American president in American history. Obama previously served as a U.S. senator representing Illinois from 2005 to 2008 and as an Illinois state senator from 1997 to 2004. Born in Honolulu, Hawaii, Obama graduated from Columbia University in 1983 with a Bachelor of Arts degree in political science and later worked as a community organizer in Chicago. In 1988, Obama enrolled in Harvard Law School, where he was the first black president of the ''Harvard Law Review''. He became a civil rights attorney and an academic, teaching constitutional law at the University of Chicago Law School from 1992 to 2004. In 1996, Obama was elected to represent the 13th district in the Illinois Senate, a position he held until 2004, when he successfully ran for the U.S. Senate. In the 2008 pre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |