|
Single Loss Expectancy
Single-loss expectancy (SLE) is the monetary value expected from the occurrence of a risk on an asset. It is related to risk management and risk assessment. Single-loss expectancy is mathematically expressed as: = \times Where the exposure factor is represented in the impact of the risk over the asset, or percentage of asset lost. As an example, if the asset value is reduced by two thirds, the exposure factor value is 0.66. If the asset is completely lost, the exposure factor is 1. The result is a monetary value in the same unit as the single-loss expectancy is expressed (euros, dollars, yens, etc.): exposure factor is the subjective, potential percentage of loss to a specific asset if a specific threat is realized. The exposure factor is a subjective value that the person assessing risk must define. See also *Information assurance *Risk assessment Risk assessment is a process for identifying hazards, potential (future) events which may negatively impact on individuals, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Risk Management
Risk management is the identification, evaluation, and prioritization of risks, followed by the minimization, monitoring, and control of the impact or probability of those risks occurring. Risks can come from various sources (i.e, Threat (security), threats) including uncertainty in Market environment, international markets, political instability, dangers of project failures (at any phase in design, development, production, or sustaining of life-cycles), legal liabilities, credit risk, accidents, Natural disaster, natural causes and disasters, deliberate attack from an adversary, or events of uncertain or unpredictable root cause analysis, root-cause. Retail traders also apply risk management by using fixed percentage position sizing and risk-to-reward frameworks to avoid large drawdowns and support consistent decision-making under pressure. There are two types of events viz. Risks and Opportunities. Negative events can be classified as risks while positive events are classifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
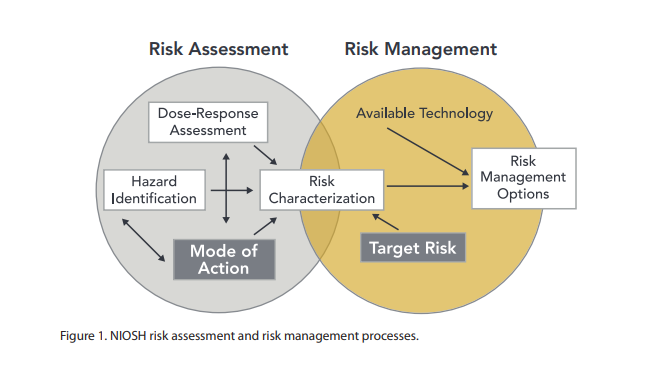
Risk Assessment
Risk assessment is a process for identifying hazards, potential (future) events which may negatively impact on individuals, assets, and/or the environment because of those hazards, their likelihood and consequences, and actions which can mitigate these effects. The output from such a process may also be called a risk assessment. Hazard analysis forms the first stage of a risk assessment process. Judgments "on the tolerability of the risk on the basis of a risk analysis" (i.e. risk evaluation) also form part of the process. The results of a risk assessment process may be expressed in a quantitative or qualitative fashion. Risk assessment forms a key part of a broader risk management strategy to help reduce any potential risk-related consequences. Categories Individual risk assessment Risk assessments can be undertaken in individual cases, including in patient and physician interactions. In the narrow sense chemical risk assessment is the assessment of a health risk in response ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exposure Factor
Exposure factor (EF), in risk management, is the subjective, potential percentage of loss to a specific asset if a specific threat is realized. It is usually applied in IT risk assessment, but may be applied to quantifying business risk more generally. capital.com Per formula: The exposure factor is usually a subjective value that the person assessing risk
In simple terms, risk is the possibility of something bad happening. Risk involves uncertainty about the effects/implications of an activity with respect to something that humans value (such ...
[...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Valuation (finance)
In finance, valuation is the process of determining the value of a (potential) investment, asset, or security. Generally, there are three approaches taken, namely discounted cashflow valuation, relative valuation, and contingent claim valuation. Valuations can be done for assets (for example, investments in marketable securities such as companies' shares and related rights, business enterprises, or intangible assets such as patents, data and trademarks) or for liabilities (e.g., bonds issued by a company). Valuation is a subjective exercise, and in fact, the process of valuation itself can also affect the value of the asset in question. Valuations may be needed for various reasons such as investment analysis, capital budgeting, merger and acquisition transactions, financial reporting, taxable events to determine the proper tax liability. In a business valuation context, various techniques are used to determine the (hypothetical) price that a third party would pay for a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Assurance
Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and data transmission, transmission of information. Information assurance includes protection of the data integrity, integrity, availability, authenticity, non-repudiation and confidentiality of user data. IA encompasses both digital protections and physical techniques. These methods apply to data in transit, both physical and electronic forms, as well as data at rest. IA is best thought of as a superset of information security (i.e. umbrella term), and as the business outcome of information risk management. Overview Information assurance (IA) is the process of processing, storing, and transmitting the right information to the right people at the right time. IA relates to the business level and Strategy, strategic risk management of information and related systems, rather than the creation and application of security controls. IA is used to benefit business ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Risk Assessment
Risk assessment is a process for identifying hazards, potential (future) events which may negatively impact on individuals, assets, and/or the environment because of those hazards, their likelihood and consequences, and actions which can mitigate these effects. The output from such a process may also be called a risk assessment. Hazard analysis forms the first stage of a risk assessment process. Judgments "on the tolerability of the risk on the basis of a risk analysis" (i.e. risk evaluation) also form part of the process. The results of a risk assessment process may be expressed in a quantitative or qualitative fashion. Risk assessment forms a key part of a broader risk management strategy to help reduce any potential risk-related consequences. Categories Individual risk assessment Risk assessments can be undertaken in individual cases, including in patient and physician interactions. In the narrow sense chemical risk assessment is the assessment of a health risk in response ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Security
Data security or data protection means protecting digital data, such as those in a database, from destructive forces and from the unwanted actions of unauthorized users, such as a cyberattack or a data breach. Technologies Disk encryption Disk encryption refers to encryption technology that encrypts data on a hard disk drive. Disk encryption typically takes form in either software (see disk encryption software) or hardware (see disk encryption hardware). Disk encryption is often referred to as on-the-fly encryption (OTFE) or transparent encryption. Software versus hardware-based mechanisms for protecting data Software-based security solutions encrypt the data to protect it from theft. However, a malicious program or a hacker could corrupt the data to make it unrecoverable, making the system unusable. Hardware-based security solutions prevent read and write access to data, which provides very strong protection against tampering and unauthorized access. Hardware- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |