|
Security Badges
An access badge is a credential used to gain entry to an area having automated access control entry points. Entry points may be doors, turnstiles, parking gates or other barriers. Access badges use various technologies to identify the holder of the badge to an access control system. The most common technologies are magnetic stripe, proximity, barcode, smart cards and various biometric devices. The magnetic stripe ID card was invented by Forrest Parry in 1960. {{webarchive, url=https://web.archive.org/web/20111027061240/http://www.suu.edu/alumni/magazine/fall04/pdf/news.pdf , date=2011-10-27 The access badge contains a number that is read by a |
Capacitor
In electrical engineering, a capacitor is a device that stores electrical energy by accumulating electric charges on two closely spaced surfaces that are insulated from each other. The capacitor was originally known as the condenser, a term still encountered in a few compound names, such as the '' condenser microphone''. It is a passive electronic component with two terminals. The utility of a capacitor depends on its capacitance. While some capacitance exists between any two electrical conductors in proximity in a circuit, a capacitor is a component designed specifically to add capacitance to some part of the circuit. The physical form and construction of practical capacitors vary widely and many types of capacitor are in common use. Most capacitors contain at least two electrical conductors, often in the form of metallic plates or surfaces separated by a dielectric medium. A conductor may be a foil, thin film, sintered bead of metal, or an electrolyte. The nonconductin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
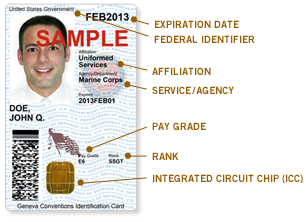
ID Card
ID or its variants may refer to: * Identity document, a document used to verify a person's identity * Identifier, a symbol which uniquely identifies an object or record People * I. D. Ffraid (1814–1875), Welsh poet and Calvinistic Methodist minister * I. D. McMaster (1923–2004), American assistant district attorney * I. D. Serebryakov (1917–1998), Russian lexicographer and translator Places * İd or Narman, a town in Turkey * Idaho, US (postal abbreviation ID) * Indonesia, ISO 3166-1 alpha-2 country code "ID" ** Indonesian language, ISO 639-1 language code "ID" Arts, entertainment, and media Music * The Id (band), an English new wave/synthpop band * New:ID, an upcoming Filipino boy band Albums * ''I.D.'' (album), a 1989 album by The Wailers Band * ''ID'' (Michael Patrick Kelly album), a 2017 studio album by Michael Patrick Kelly * ''Id'' (Siddharta album), 1999 * '' d' (Veil of Maya album), 2010 * ''ID'', an album by Anna Maria Jopek * ''The Id'' (album), a 2001 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fortification
A fortification (also called a fort, fortress, fastness, or stronghold) is a military construction designed for the defense of territories in warfare, and is used to establish rule in a region during peacetime. The term is derived from Latin ("strong") and ("to make"). From very early history to modern times, defensive walls have often been necessary for cities to survive in an ever-changing world of invasion and conquest. Some settlements in the Indus Valley Civilization were the first small cities to be fortified. In ancient Greece, large cyclopean stone walls fitted without mortar had been built in Mycenaean Greece, such as the ancient site of Mycenae. A Greek ''Towns of ancient Greece#Military settlements, phrourion'' was a fortified collection of buildings used as a military garrison, and is the equivalent of the ancient Roman, Roman castellum or fortress. These constructions mainly served the purpose of a watch tower, to guard certain roads, passes, and borders. Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Lock
An electronic lock (or electric lock) is a Lock (security device), locking device which operates by means of electric current. Electric locks are sometimes stand-alone with an electronic control assembly mounted directly to the lock. Electric locks may be connected to an access control system, the advantages of which include: key control, where keys can be added and removed without re-keying the lock cylinder; fine access control, where time and place are factors; and transaction logging, where activity is recorded. Electronic locks can also be remotely monitored and controlled, both to lock and to unlock. Operation Electric locks use magnets, solenoids, or motors to actuate the lock by either supplying or removing power. Operating the lock can be as simple as using a switch, for example an apartment intercom door release, or as complex as a biometric based access control system. There are two basic types of locks: "preventing mechanism" or operation mechanism. Types Electr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Door Security
The term door security or door security gate may refer to any of a range of measures used to strengthen doors against door breaching, ram-raiding and lock picking, and prevent crimes such as burglary and home invasions. Door security is used in commercial and government buildings, as well as in residential settings. Some strengthened doors function as fire doors to prevent or inhibit the spread of fire. Security devices Alarms Alarms — designed to warn of burglaries. Locks * Smart locks can be used to limit door access to only people with an electronic key fob or near-field communication device, like a smartphone. These devices are popular with landlords, who can enable and disable digital access without physically mailing out keys. The locks can log the times of entry, and can trigger an alarm if they are struck during a break-in attempt. * Deadbolts — unlike common spring latches, the locking mechanism of these typically prevents the bolt from being retracted by force, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Credential
A credential is a piece of any document that details a qualification, competence, or authority issued to an individual by a third party with a relevant or ''de facto'' authority or assumed competence to do so. Examples of credentials include academic diplomas, academic degrees, Professional certification, certifications, security clearances, Identity document, identification documents, badges, passwords, user names, key (lock), keys, power of attorney, powers of attorney, and so on. Sometimes publications, such as scientific papers or books, may be viewed as similar to credentials by some people, especially if the publication was peer reviewed or made in a well-known Academic journal, journal or reputable publisher. Types and documentation of credentials A person holding a credential is usually given documentation or secret knowledge (''e.g.,'' a password or key) as proof of the credential. Sometimes this proof (or a copy of it) is held by a third, trusted party. While in some c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Common Access Card
The common access card, also commonly referred to as the CAC, is the standard identification for active duty United States defense personnel. The card itself is a smart card about the size of a credit card. Defense personnel that use the CAC include the Selected Reserve and National Guard, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions (especially the Third Geneva Convention). In combination with a personal identification number, a CAC satisfies the requirement for two-factor authentication: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature and data encryption t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Card Printer
A printer is a peripheral machine which makes a durable representation of graphics or text, usually on paper. While most output is human-readable, bar code printers are an example of an expanded use for printers. Different types of printers include 3D printers, inkjet printers, laser printers, and thermal printers. History The first computer printer designed was a mechanically driven apparatus by Charles Babbage for his difference engine in the 19th century; however, his mechanical printer design was not built until 2000. He also had plans for a curve plotter, which would have been the first computer graphics printer if it was built. The first patented printing mechanism for applying a marking medium to a recording medium or more particularly an electrostatic inking apparatus and a method for electrostatically depositing ink on controlled areas of a receiving medium, was in 1962 by C. R. Winston, Teletype Corporation, using continuous inkjet printing. The ink was a red sta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometrics
Biometrics are body measurements and calculations related to human characteristics and features. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, voice, and behavioral profiling. Some researchers have coined the term behaviometrics (behavioral biom ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Control
In physical security and information security, access control (AC) is the action of deciding whether a subject should be granted or denied access to an object (for example, a place or a resource). The act of ''accessing'' may mean consuming, entering, or using. It is often used interchangeably with authorization, although the authorization may be granted well in advance of the access control decision. Access control on digital platforms is also termed admission control. The protection of external databases is essential to preserve digital security. Access control is considered to be a significant aspect of privacy that should be further studied. Access control policy (also access policy) is part of an organization’s security policy. In order to verify the access control policy, organizations use an access control model. General security policies require designing or selecting appropriate security controls to satisfy an organization's risk appetite - access policies ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |