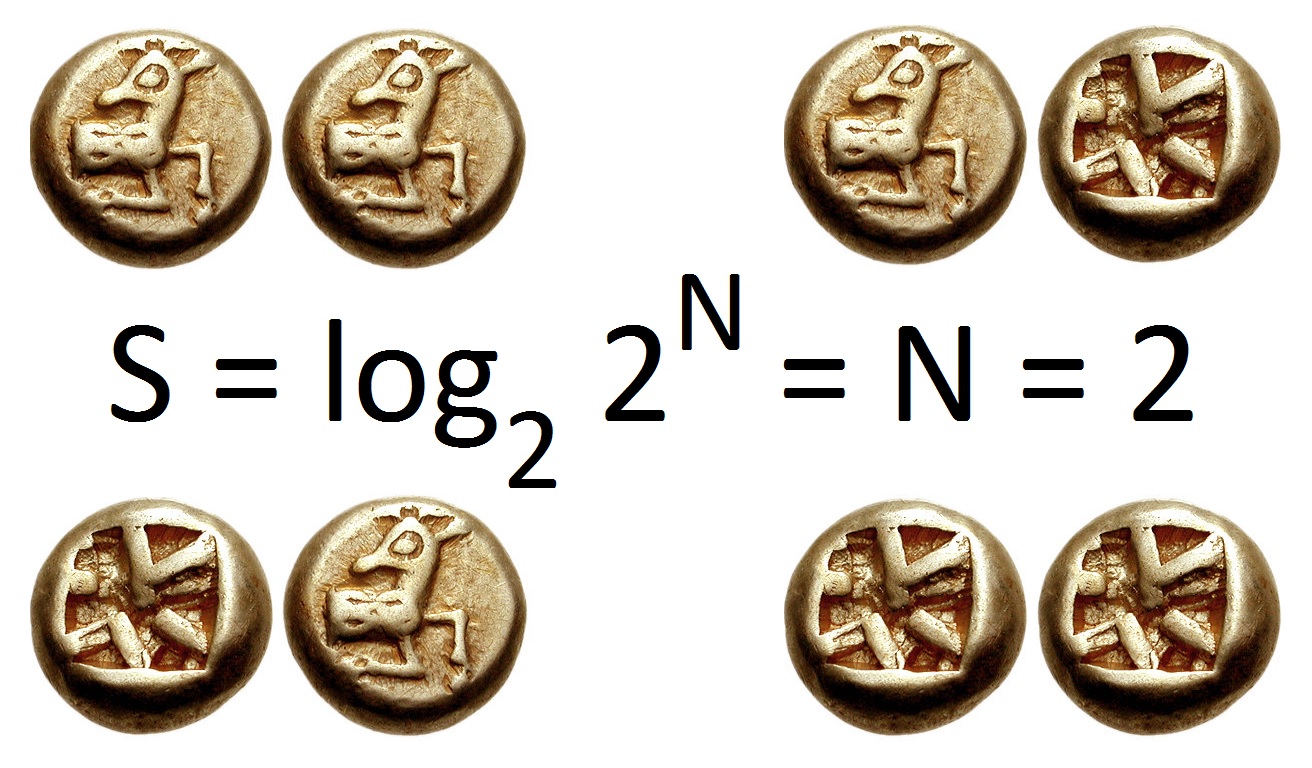|
Random Number Generator Attack
The security of cryptographic systems depends on some secret data that is known to authorized persons but unknown and unpredictable to others. To achieve this unpredictability, some randomization is typically employed. Modern cryptographic protocols often require frequent generation of random quantities. Cryptographic attacks that subvert or exploit weaknesses in this process are known as random number generator attacks. A high quality random number generation (RNG) process is almost always required for security, and lack of quality generally provides attack vulnerabilities and so leads to lack of security, even to complete compromise, in cryptographic systems. The RNG process is particularly attractive to attackers because it is typically a single isolated hardware or software component easy to locate. If the attacker can substitute pseudo-random bits generated in a way they can predict, security is totally compromised, yet generally undetectable by any upstream test of the bits. F ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Cryptographic
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or '' -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymous with encryption, convert ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Stream Cipher
stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream ( keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as ''state cipher''. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR). The pseudorandom keystream is typically generated serially from a random seed value using digital shift registers. The seed value serves as the cryptographic key for decrypting the ciphertext stream. Stream ciphers represent a different approach to symmetric encryption from block ciphers. Block ciphers operate on large blocks of digits with a fixed, unvarying transformation. This distinction is not always clear-cut: in some modes of operation, a block cipher primitive is used in such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Object Code
In computing, object code or object module is the product of an assembler or compiler In computing, a compiler is a computer program that Translator (computing), translates computer code written in one programming language (the ''source'' language) into another language (the ''target'' language). The name "compiler" is primaril .... In a general sense, object code is a sequence of statements or instructions in a computer language, usually a machine code language (i.e., binary) or an intermediate language such as register transfer language (RTL). The term indicates that the code is the goal or result of the compiling process, with some early sources referring to source code as a "subject program". Details Object files can in turn be linked to form an executable file or library file. In order to be used, object code must either be placed in an executable file, a library file, or an object file. Object code is a portion of machine code that has not yet been linked ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Reverse Engineering
Reverse engineering (also known as backwards engineering or back engineering) is a process or method through which one attempts to understand through deductive reasoning how a previously made device, process, system, or piece of software accomplishes a task with very little (if any) insight into exactly how it does so. Depending on the system under consideration and the technologies employed, the knowledge gained during reverse engineering can help with repurposing obsolete objects, doing security analysis, or learning how something works. Although the process is specific to the object on which it is being performed, all reverse engineering processes consist of three basic steps: information extraction, modeling, and review. Information extraction is the practice of gathering all relevant information for performing the operation. Modeling is the practice of combining the gathered information into an abstract model, which can be used as a guide for designing the new object or syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
David A
David (; , "beloved one") was a king of ancient Israel and Judah and the third king of the United Monarchy, according to the Hebrew Bible and Old Testament. The Tel Dan stele, an Aramaic-inscribed stone erected by a king of Aram-Damascus in the late 9th/early 8th centuries BCE to commemorate a victory over two enemy kings, contains the phrase (), which is translated as " House of David" by most scholars. The Mesha Stele, erected by King Mesha of Moab in the 9th century BCE, may also refer to the "House of David", although this is disputed. According to Jewish works such as the '' Seder Olam Rabbah'', '' Seder Olam Zutta'', and '' Sefer ha-Qabbalah'' (all written over a thousand years later), David ascended the throne as the king of Judah in 885 BCE. Apart from this, all that is known of David comes from biblical literature, the historicity of which has been extensively challenged,Writing and Rewriting the Story of Solomon in Ancient Israel; by Isaac Kalimi; page 3 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Ian Goldberg
Ian Avrum Goldberg (born March 31, 1973) is a cryptographer and cypherpunk. He is best known for breaking Netscape's implementation of SSL (with David Wagner), and for his role as chief scientist of Radialpoint (formerly Zero Knowledge Systems), a Canadian software company. Goldberg is currently a professor at the Faculty of Mathematics of the David R. Cheriton School of Computer Science within the University of Waterloo, and the Canada Research Chair in Privacy Enhancing Technologies. He was formerly Tor Project board of directors chairman, and is one of the designers of off the record messaging. Education Goldberg attended high school at the University of Toronto Schools, graduating in 1991. In 1995, he received a B.Math from the University of Waterloo in pure mathematics and computer science. He obtained a Ph.D. from the University of California, Berkeley in December 2000. His thesis was entitled ''A Pseudonymous Communications Infrastructure for the Internet''. His a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Phillip Hallam-Baker
Phillip Hallam-Baker is a computer scientist, mostly known for contributions to Internet security, since the design of HTTP at CERN in 1992. Self-employed since 2018 as a consultant and expert witness in court cases, he previously worked at Comodo, Verisign, and the MIT Artificial Intelligence Laboratory. He is a frequent participant in IETF meetings and discussions, and has written a number of RFCs. He introduced the misspelling of referrer in the original proposal to incorporate the " Referer" header field into the HTTP specification. In 2007 he authored ''the dotCrime Manifesto: How to Stop Internet Crime''; Ron Rivest Ronald Linn Rivest (; born May 6, 1947) is an American cryptographer and computer scientist whose work has spanned the fields of algorithms and combinatorics, cryptography, machine learning, and election integrity. He is an Institute Profess ... used it as a source of project ideas for his course on Computer and Network Security at MIT in 2013. Biogra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Information Entropy
In information theory, the entropy of a random variable quantifies the average level of uncertainty or information associated with the variable's potential states or possible outcomes. This measures the expected amount of information needed to describe the state of the variable, considering the distribution of probabilities across all potential states. Given a discrete random variable X, which may be any member x within the set \mathcal and is distributed according to p\colon \mathcal\to , 1/math>, the entropy is \Eta(X) := -\sum_ p(x) \log p(x), where \Sigma denotes the sum over the variable's possible values. The choice of base for \log, the logarithm, varies for different applications. Base 2 gives the unit of bits (or " shannons"), while base ''e'' gives "natural units" nat, and base 10 gives units of "dits", "bans", or " hartleys". An equivalent definition of entropy is the expected value of the self-information of a variable. The concept of information entropy was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Secure Sockets Layer
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network, such as the Internet. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol that provides security to datagram-based applications. In technical writing, references to "(D)TLS" are often seen when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first def ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Netscape Communications Corporation
Netscape Communications Corporation (originally Mosaic Communications Corporation) was an American independent computer services company with headquarters in Mountain View, California, and then Dulles, Virginia. Its Netscape (web browser), Netscape web browser was once dominant but lost to Internet Explorer and other competitors in the first browser war, with its market share falling from more than 90 percent in the mid-1990s to less than one percent in 2006. An early Netscape employee, Brendan Eich, created the JavaScript programming language, the most widely used language for client-side Scripting language, scripting of web pages. A founding engineer of Netscape, Lou Montulli, created HTTP cookies. The company also developed Secure Sockets Layer, SSL which was used for securing online communications before its successor Transport Layer Security, TLS took over. Netscape stock traded from 1995 until 1999 when the company was acquired by AOL in a Pooling (resource management)#Acc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Hardware Random Number Generator
In computing, a hardware random number generator (HRNG), true random number generator (TRNG), non-deterministic random bit generator (NRBG), or physical random number generator is a device that generates random numbers from a physical process capable of producing entropy, unlike a pseudorandom number generator (PRNG) that utilizes a deterministic algorithm and non-physical nondeterministic random bit generators that do not include hardware dedicated to generation of entropy. Many natural phenomena generate low-level, statistically random "noise" signals, including thermal and shot noise, jitter and metastability of electronic circuits, Brownian motion, and atmospheric noise. Researchers also used the photoelectric effect, involving a beam splitter, other quantum phenomena, and even the nuclear decay (due to practical considerations the latter, as well as the atmospheric noise, is not viable except for fairly restricted applications or online distribution services). Wh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Webcam
A webcam is a video camera which is designed to record or stream to a computer or computer network. They are primarily used in Videotelephony, video telephony, live streaming and social media, and Closed-circuit television, security. Webcams can be Built-in function, built-in computer hardware or Peripheral, peripheral devices, and are commonly connected to a device using USB or Internet protocol suite, wireless protocol. Webcams have been used on the Internet as early as 1993, and the first widespread commercial one became available in 1994. Early webcam usage on the Internet was primarily limited to stationary shots streamed to web sites. In the late 1990s and early 2000s, instant messaging clients added support for webcams, increasing their popularity in video conferencing. Computer manufacturers later started integrating webcams into laptop hardware. In 2020, the COVID-19 pandemic caused a shortage of webcams due to the increased number of people Remote work, working from hom ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |