|
Invalid Opcode
An illegal opcode, also called an unimplemented operation, unintended opcode or undocumented instruction, is an instruction to a CPU that is not mentioned in any official documentation released by the CPU's designer or manufacturer, which nevertheless has an effect. Illegal opcodes were common on older CPUs designed during the 1970s, such as the MOS Technology 6502, Intel 8086, and the Zilog Z80. Unlike modern processors, those older processors have a very limited transistor budget, and thus to save space their designers often omitted circuitry to detect invalid opcodes and generate a trap to an error handler. The operation of many of these opcodes happens as a side effect of the wiring of transistors in the CPU, and usually combines functions of the CPU that were not intended to be combined. On old and modern processors, there are also instructions intentionally included in the processor by the manufacturer, but that are not documented in any official specification. Overview ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
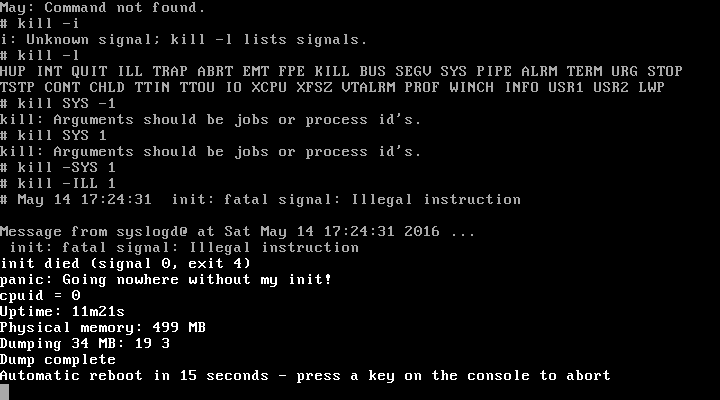
FreeBSD Illegal Instruction Kernel Panic
FreeBSD is a free-software Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version was released in 1993 developed from 386BSD, one of the first fully functional and free Unix clones on affordable home-class hardware, and has since continuously been the most commonly used BSD-derived operating system. FreeBSD maintains a complete system, delivering a kernel, device drivers, userland utilities, and documentation, as opposed to Linux only delivering a kernel and drivers, and relying on third-parties such as GNU for system software. The FreeBSD source code is generally released under a permissive BSD license, as opposed to the copyleft GPL used by Linux. The project includes a security team overseeing all software shipped in the base distribution. Third-party applications may be installed using the pkg package management system or from source via FreeBSD Ports. The project is supported and promoted by the FreeBSD Foundation. Much of Fr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Apple IIc
The Apple IIc is a personal computer introduced by Apple Inc. shortly after the launch of the Macintosh 128K, original Macintosh in 1984. It is essentially a compact and portable version of the Apple IIe. The IIc has a built-in floppy disk drive and a keyboard, and was often sold with its matching monitor. The ''c'' in the name stands for ''compact'', referring to the fact it is a complete Apple II setup in a smaller notebook-sized housing. The computer is compatible with a wide range of Apple II software and peripherals. The Apple IIc has rear peripheral expansion ports integrated onto the main logic board instead of the expansion slots and direct motherboard access of earlier Apple II models. Apple intended the Apple IIc to require less technical expertise to use. The Apple IIc weighs . It was succeeded by the Apple IIc Plus in 1988. History The Apple IIc was released on April 24, 1984, during an Apple-held event called ''Apple II Forever''. With that motto, Apple proclaimed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Fuzzing
In programming and software development, fuzzing or fuzz testing is an automated software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer program. The program is then monitored for exceptions such as crashes, failing built-in code assertions, or potential memory leaks. Typically, fuzzers are used to test programs that take structured inputs. This structure is specified, such as in a file format or protocol and distinguishes valid from invalid input. An effective fuzzer generates semi-valid inputs that are "valid enough" in that they are not directly rejected by the parser, but do create unexpected behaviors deeper in the program and are "invalid enough" to expose corner cases that have not been properly dealt with. For the purpose of security, input that crosses a trust boundary is often the most useful. For example, it is more important to fuzz code that handles a file uploaded by any user than it is to fuzz the code ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
NTVDM
Virtual DOS machines (VDM) refer to a technology that allows running 16-bit/32-bit DOS and 16-bit Windows programs when there is already another operating system running and controlling the hardware. Overview Virtual DOS machines can operate either exclusively through typical software emulation methods (e.g. dynamic recompilation) or can rely on the virtual 8086 mode of the Intel 80386 processor, which allows real mode 8086 software to run in a controlled environment by catching all operations which involve accessing protected hardware and forwarding them to the normal operating system (as exceptions). The operating system can then perform an emulation and resume the execution of the DOS software. VDMs generally also implement support for running 16-bit and 32-bit protected mode software ( DOS extenders), which has to conform to the DOS Protected Mode Interface (DPMI). When a DOS program running inside a VDM needs to access a peripheral, Windows will either allow this di ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
BIOS
In computing, BIOS (, ; Basic Input/Output System, also known as the System BIOS, ROM BIOS, BIOS ROM or PC BIOS) is a type of firmware used to provide runtime services for operating systems and programs and to perform hardware initialization during the booting process (power-on startup). The firmware comes pre-installed on the computer's motherboard. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS firmware was originally proprietary to the IBM PC; it was reverse engineered by some companies (such as Phoenix Technologies) looking to create compatible systems. The interface of that original system serves as a ''de facto'' standard. The BIOS in older PCs initializes and tests the system hardware components ( power-on self-test or POST for short), and loads a boot loader from a mass storage device which then initializes a kernel. In the era of DOS, the BIOS provided BIOS interrupt calls for the keyboard, display, st ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
LOADALL
LOADALL is the common name for two different undocumented machine instructions of Intel 80286 and Intel 80386 processors, which allow access to areas of the internal processor state that are normally outside of the IA-32 API scope, like ''descriptor cache registers''. The LOADALL for 286 processors is encoded 0Fh 05h, while the LOADALL for 386 processors is 0Fh 07h. Both variants – as the name implies – load all CPU internal registers in one operation. LOADALL had the unique ability to set up the visible part of the segment registers (selector) independently of their corresponding cached part, allowing the programmer to bring the CPU into states not otherwise allowed by the official programming model. Usage As an example of the usefulness of these techniques, LOADALL can set up the CPU to allow access to all memory from real mode, without having to switch it into unreal mode (which requires switching into protected mode, accessing memory and finally switching back to real ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Texas Instruments TMS9900
The TMS9900 was one of the first commercially available single-chip 16-bit microprocessors. Introduced in June 1976, it implemented Texas Instruments's TI-990 minicomputer architecture in a single-chip format, and was initially used for low-end models of that lineup. Its 64-pin dual in-line package, DIP format made it more expensive to implement in smaller machines than the more common 40-pin format, and it saw relatively few design wins outside TI's own use. Among those uses was their TI-99/4A, TI-99/4 and TI-99/4A home computers, which ultimately sold about 2.8 million units. By the mid-1980s, the microcomputer field was moving to 16-bit systems such as the Intel 8086 and newer 16/32-bit designs such as the Motorola 68000. With no obvious future for the chip, TI's Semiconductor division turned its attention to special-purpose 32-bit processors: the Texas Instruments TMS320, introduced in 1983, and the TMS34010, Texas Instruments TMS340 graphics processor. The 9900 architect ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
NOP (code)
In computer science, a NOP, no-op, or NOOP (pronounced "no op"; short for no operation) is a machine language instruction and its assembly language mnemonic, programming language statement, or computer protocol command that does nothing. Machine language instructions Some computer instruction sets include an instruction whose purpose is to not change the state of any of the programmer-accessible registers, status flags, or memory. It often takes a well-defined number of clock cycles to execute. In other instruction sets, there is no explicit NOP instruction, but the assembly language mnemonic NOP represents an instruction which acts as a NOP; e.g., on the SPARC, sethi 0, %g0. A NOP must not access memory, as that could cause a memory fault or page fault. A NOP is most commonly used for timing purposes, to force memory alignment, to prevent hazards, to occupy a branch delay slot, to render void an existing instruction such as a jump, as a target of an execute i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Operating System
An operating system (OS) is system software that manages computer hardware and software resources, and provides common daemon (computing), services for computer programs. Time-sharing operating systems scheduler (computing), schedule tasks for efficient use of the system and may also include accounting software for cost allocation of Scheduling (computing), processor time, mass storage, peripherals, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computerfrom cellular phones and video game consoles to web servers and supercomputers. , Android (operating system), Android is the most popular operating system with a 46% market share, followed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Fault (computing)
In digital computers, an interrupt (sometimes referred to as a trap) is a request for the processor to ''interrupt'' currently executing code (when permitted), so that the event can be processed in a timely manner. If the request is accepted, the processor will suspend its current activities, save its state, and execute a function called an ''interrupt handler'' (or an ''interrupt service routine'', ISR) to deal with the event. This interruption is often temporary, allowing the software to resume normal activities after the interrupt handler finishes, although the interrupt could instead indicate a fatal error. Interrupts are commonly used by hardware devices to indicate electronic or physical state changes that require time-sensitive attention. Interrupts are also commonly used to implement computer multitasking and system calls, especially in real-time computing. Systems that use interrupts in these ways are said to be interrupt-driven. History Hardware interrupts were ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Exception (computing)
In computing and computer programming, exception handling is the process of responding to the occurrence of ''exceptions'' – anomalous or exceptional conditions requiring special processing – during the execution of a program. In general, an exception breaks the normal flow of execution and executes a pre-registered ''exception handler''; the details of how this is done depend on whether it is a hardware or software exception and how the software exception is implemented. Exceptions are defined by different layers of a computer system, and the typical layers are CPU-defined interrupts, operating system (OS)-defined signals, programming language-defined exceptions. Each layer requires different ways of exception handling although they may be interrelated, e.g. a CPU interrupt could be turned into an OS signal. Some exceptions, especially hardware ones, may be handled so gracefully that execution can resume where it was interrupted. Definition The definition of an except ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Motorola 68000
The Motorola 68000 (sometimes shortened to Motorola 68k or m68k and usually pronounced "sixty-eight-thousand") is a 16/32-bit complex instruction set computer (CISC) microprocessor, introduced in 1979 by Motorola Semiconductor Products Sector. The design implements a 32-bit instruction set, with 32-bit registers and a 16-bit internal data bus. The address bus is 24 bits and does not use memory segmentation, which made it easier to program for. Internally, it uses a 16-bit data arithmetic logic unit (ALU) and two more 16-bit ALUs used mostly for addresses, and has a 16-bit external data bus. For this reason, Motorola termed it a 16/32-bit processor. As one of the first widely available processors with a 32-bit instruction set, large unsegmented address space, and relatively high speed for the era, the 68k was a popular design through the 1980s. It was widely used in a new generation of personal computers with graphical user interfaces, including the Macintosh 128K, Amiga, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |