|
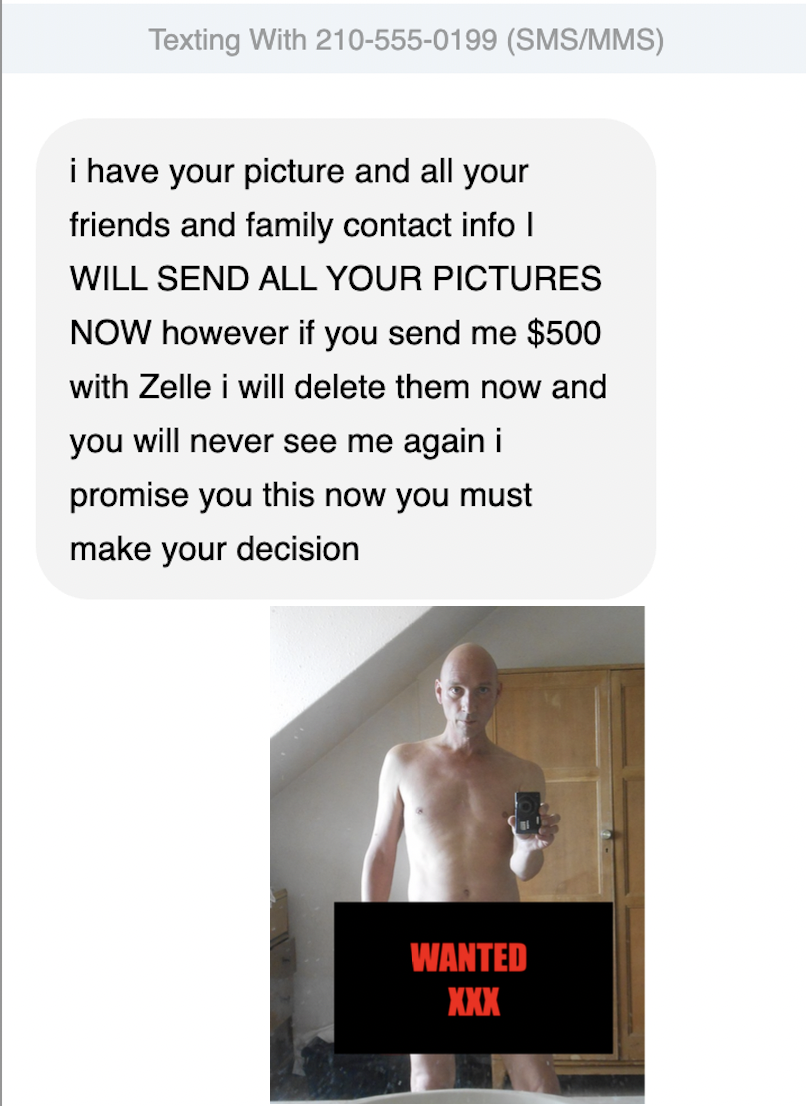
ISeeYou
iSeeYou is a security bug affecting iSight cameras in some Apple laptops. Discovery The researchers' decision to study webcam indicator lights resulted from the widely reported WebcamGate case, in which a remote access tool installed on school-issued laptops took photographs of unconsenting students. The study demonstrated that the webcam indicator light could be turned off while the camera itself was turned on by bypassing the standby state of the signal. This was performed by changing the RESET register in the device's firmware to a value of 0x00c8. Impact The security flaw was reported internationally. This vulnerability was used in the extortion of Miss Teen USA, Cassidy Wolf, when she received emails containing nude photos of herself, taken without her knowledge, from an unknown man. Wolf claimed she never knew she was being recorded and that her webcam light never turned on. The FBI arrested Jared Abrahams in relation to this crime as well as the sextortion of other ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ISight Camera
iSight is a brand name used by Apple Inc. to refer to webcams on various devices. The name was originally used for the external iSight webcam, which retailed for US$149, connected to a computer via a FireWire cable, and came with a set of mounts to place it atop any then-current Apple display, laptop computer, all-in-one desktop computer, or round surface. Apple introduced iSight at the 2003 Worldwide Developers Conference, and it was intended to be used with iChat AV, Apple's video-conferencing client. iMovie (version 4 and later) could also be used to capture video from the device. In April 2005, Apple released a firmware update for the iSight to improve audio performance. As of October 13, 2008, the external iSight was no longer for sale in the Apple online store or in retail locations. Meanwhile, Apple began using the term to refer to the camera built into Apple's iMac, MacBook, MacBook Air, and MacBook Pro computers, Thunderbolt Display, and Cinema Display. In November 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WebcamGate
''Robbins v. Lower Merion School District'' is a federal class action lawsuit, brought during February 2010 on behalf of students of two high schools in Lower Merion Township, a suburb of Philadelphia. In October 2010, the school district agreed to pay $610,000 to settle the ''Robbins'' and parallel ''Hasan'' lawsuits against it. The suit alleged that, in what was dubbed the "WebcamGate" scandal, the schools secretly spied on the students while they were in the privacy of their homes. School authorities surreptitiously and remotely activated webcams embedded in school-issued laptops the students were using at home. After the suit was brought, the school district, of which the two high schools are part, revealed that it had secretly taken more than 66,000 images. The suit charged that in doing so the district infringed on its students' privacy rights. A federal judge issued a preliminary injunction, ordering the school district to stop its secret webcam monitoring, and ordered ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Bug
A security bug or security defect is a software bug that can be exploited to gain unauthorized access or privileges on a computer system. Security bugs introduce security vulnerabilities by compromising one or more of: * Authentication of users and other entities * Authorization of access rights and privileges * Data confidentiality * Data integrity Security bugs do not need be identified nor exploited to be qualified as such and are assumed to be much more common than known vulnerabilities in almost any system. Causes Security bugs, like all other software bugs, stem from root causes that can generally be traced to either absent or inadequate: * Software developer training * Use case analysis * Software engineering methodology * Quality assurance testing * and other best practices Taxonomy Security bugs generally fall into a fairly small number of broad categories that include: * Memory safety (e.g. buffer overflow and dangling pointer bugs) * Race condition * Secure ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Remote Access Tool
In computing, the term remote desktop refers to a software- or operating system feature that allows a personal computer's desktop environment to be run remotely from one system (usually a PC, but the concept applies equally to a server or a smartphone), while being displayed on a separate client device. Remote desktop applications have varying features. Some allow attaching to an existing user's session and "remote controlling", either displaying the remote control session or blanking the screen. Taking over a desktop remotely is a form of remote administration. Overview Remote access can also be explained as the remote control of a computer by using another device connected via the internet or another network. This is widely used by many computer manufacturers and large businesses help desks for technical troubleshooting of their customer's problems. Remote desktop software captures the mouse and keyboard inputs from the local computer (client) and sends them to the remote ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Insider
''Business Insider'' (stylized in all caps: BUSINESS INSIDER; known from 2021 to 2023 as INSIDER) is a New York City–based multinational financial and business news website founded in 2007. Since 2015, a majority stake in ''Business Insider''s parent company Insider Inc. has been owned by the international publishing house Axel Springer. It operates several international editions, including one in the United Kingdom. ''Insider'' publishes original reporting and aggregates material from other outlets. it maintained a liberal policy on the use of anonymous sources. It has also published native advertising and granted sponsors editorial control of its content. The outlet has been nominated for several awards, but has also been criticized for using factually incorrect clickbait headlines to attract viewership. In 2015, Axel Springer SE acquired 88 percent of the stake in Insider Inc. for $343 million (€306 million), implying a total valuation of $442 million. From ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Washington Post
''The Washington Post'', locally known as ''The'' ''Post'' and, informally, ''WaPo'' or ''WP'', is an American daily newspaper published in Washington, D.C., the national capital. It is the most widely circulated newspaper in the Washington metropolitan area and has a national audience. As of 2023, the ''Post'' had 130,000 print subscribers and 2.5 million digital subscribers, both of which were the List of newspapers in the United States, third-largest among U.S. newspapers after ''The New York Times'' and ''The Wall Street Journal''. The ''Post'' was founded in 1877. In its early years, it went through several owners and struggled both financially and editorially. In 1933, financier Eugene Meyer (financier), Eugene Meyer purchased it out of bankruptcy and revived its health and reputation; this work was continued by his successors Katharine Graham, Katharine and Phil Graham, Meyer's daughter and son-in-law, respectively, who bought out several rival publications. The ''Post ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Guardian
''The Guardian'' is a British daily newspaper. It was founded in Manchester in 1821 as ''The Manchester Guardian'' and changed its name in 1959, followed by a move to London. Along with its sister paper, ''The Guardian Weekly'', ''The Guardian'' is part of the Guardian Media Group, owned by the Scott Trust Limited. The trust was created in 1936 to "secure the financial and editorial independence of ''The Guardian'' in perpetuity and to safeguard the journalistic freedom and liberal values of ''The Guardian'' free from commercial or political interference". The trust was converted into a limited company in 2008, with a constitution written so as to maintain for ''The Guardian'' the same protections as were built into the structure of the Scott Trust by its creators. Profits are reinvested in its journalism rather than distributed to owners or shareholders. It is considered a newspaper of record in the UK. The editor-in-chief Katharine Viner succeeded Alan Rusbridger in 2015. S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Miss Teen USA
Miss Teen USA is a beauty pageant that has been run since 1983 by the Miss Universe Organization for girls aged 14–19 years old as of January 1st of the competition year. They must be US citizens, and cannot have been married, pregnant, or have children. Unlike its sister pageants Miss Universe, which currently broadcasts on JKN18 and like its sister pageant Miss USA, it is televised on The CW television network starting in 2024, after being streamed online for several years. The Miss Universe Organization previously operated Miss Teen USA, as well as Miss USA, until 2020 when the rights to produce both pageants were licensed to Miss USA 2008 Crystle Stewart prior to her suspension in October 2022, thus returning the said pageants to the Miss Universe Organization. The parent company of all three pageants and the Miss Universe organization remains the same under the licensing agreement: JKN Metaverse Inc., a subsidiary of JKN Global Group. Prior to 1983, a beauty contes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cassidy Wolf
Cassidy Marie Wolf (born July 5, 1994) is an American TV host, model and beauty queen who was crowned Miss Teen USA 2013. Pageants While attending Great Oak High School in Temecula, she was crowned Miss Greater San Diego Teen USA. Wolf was crowned Miss California Teen USA in 2013, and later the same year Miss Teen USA 2013 on August 10, 2013, in The Bahamas. Wolf was crowned the 31st Miss Teen USA. Victim of sextortion Wolf was a victim of sextortion, after photographs of her were hacked and used in an attempt to blackmail her. The FBI ran a probe after Wolf reported a threatening email demanding a 'special performance' for the hacker, whom she suspected to be Jared James Abrahams, her former high school classmate. Wolf never created the video demanded, and on September 26, 2013, Abrahams surrendered to FBI agents in Orange County. In November 2013, Abrahams pleaded guilty to hacking over 100-150 women and installing the highly invasive malware Blackshades on their computers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sextortion
Sextortion (a portmanteau of ''sex'' and ''extortion'') employs non-physical forms of coercion to extort sexual favors from the victim. Sextortion refers to the broad category of sexual exploitation in which abuse of power is the means of coercion, as well as to the category of sexual exploitation in which threatened release of sexual images or information is the means of coercion. As used to describe an abuse of power, sextortion is a form of corruption in which people entrusted with power – such as government officials, judges, educators, law enforcement personnel, and employers – seek to extort sexual favors in exchange for something within their authority to grant or withhold. Examples of such abuses of power include: government officials who request sexual favors to obtain licenses or permits, teachers who trade good grades for sex with students, and employers who make providing sexual favors a condition of obtaining a job or getting promoted.. A Transparency Internation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware and software resources, and provides common daemon (computing), services for computer programs. Time-sharing operating systems scheduler (computing), schedule tasks for efficient use of the system and may also include accounting software for cost allocation of Scheduling (computing), processor time, mass storage, peripherals, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computerfrom cellular phones and video game consoles to web servers and supercomputers. , Android (operating system), Android is the most popular operating system with a 46% market share, followed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Bugs
A software bug is a design defect ( bug) in computer software. A computer program with many or serious bugs may be described as ''buggy''. The effects of a software bug range from minor (such as a misspelled word in the user interface) to severe (such as frequent crashing). In 2002, a study commissioned by the US Department of Commerce's National Institute of Standards and Technology concluded that "software bugs, or errors, are so prevalent and so detrimental that they cost the US economy an estimated $59 billion annually, or about 0.6 percent of the gross domestic product". Since the 1950s, some computer systems have been designed to detect or auto-correct various software errors during operations. History Terminology ''Mistake metamorphism'' (from Greek ''meta'' = "change", ''morph'' = "form") refers to the evolution of a defect in the final stage of software deployment. Transformation of a ''mistake'' committed by an analyst in the early stages of the softwa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |