|
Features From Accelerated Segment Test
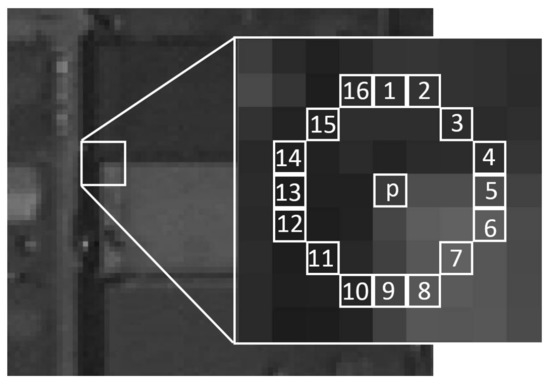
Features from accelerated segment test (FAST) is a corner detection method, which could be used to extract Feature (computer vision), feature points and later used to track and map objects in many computer vision tasks. The FAST corner detector was originally developed by Edward Rosten and Tom Drummond, and was published in 2006. The most promising advantage of the FAST corner detector is its computational efficiency. Referring to its name, it is indeed faster than many other well-known feature extraction methods, such as difference of Gaussians (DoG) used by the Scale-invariant feature transform, SIFT, Corner detection#The SUSAN corner detector, SUSAN and Harris affine region detector, Harris detectors. Moreover, when machine learning techniques are applied, superior performance in terms of computation time and resources can be realised. The FAST corner detector is very suitable for real-time video processing application because of this high-speed performance. Segment test detector ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Corner Detection
Corner detection is an approach used within computer vision systems to extract certain kinds of Feature detection (computer vision), features and infer the contents of an image. Corner detection is frequently used in motion detection, image registration, video tracking, photographic mosaic, image mosaicing, panorama stitching, 3D reconstruction and object recognition. Corner detection overlaps with the topic of interest point detection. Formalization A corner can be defined as the intersection of two edges. A corner can also be defined as a point for which there are two dominant and different edge directions in a local neighbourhood of the point. An interest point is a point in an image which has a well-defined position and can be robustly detected. This means that an interest point can be a corner but it can also be, for example, an isolated point of local intensity maximum or minimum, line endings, or a point on a curve where the curvature is locally maximal. In practice, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C (programming Language)
C (''pronounced'' '' – like the letter c'') is a general-purpose programming language. It was created in the 1970s by Dennis Ritchie and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of the targeted Central processing unit, CPUs. It has found lasting use in operating systems code (especially in Kernel (operating system), kernels), device drivers, and protocol stacks, but its use in application software has been decreasing. C is commonly used on computer architectures that range from the largest supercomputers to the smallest microcontrollers and embedded systems. A successor to the programming language B (programming language), B, C was originally developed at Bell Labs by Ritchie between 1972 and 1973 to construct utilities running on Unix. It was applied to re-implementing the kernel of the Unix operating system. During the 1980s, C gradually gained popularity. It has become one of the most widely used programming langu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pentium D
Pentium D is a range of desktop 64-bit x86-64 processors based on the NetBurst microarchitecture, which is the Multi-core processor, dual-core variant of the Pentium 4 manufactured by Intel. Each CPU comprised two cores. The brand's first processor, codenamed Smithfield and manufactured on the 90 nm process, was released on May 25, 2005, followed by the 65 nm Presler nine months later. The core implementation on the 90 nm Smithfield and later 65 nm Presler are designed differently but are functionally the same. The 90 nm Smithfield contains a single Die (integrated circuit), die, with two adjoined but functionally separate CPU cores cut from the same wafer (electronics), wafer. The later 65 nm Presler utilized a multi-chip module package, where two discrete dies each containing a single core reside on the CPU substrate. Neither the 90 nm Smithfield nor the 65 nm Presler were capable of direct core to core communication, relying instead on the Northbridge (computing), northbridge li ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shi-Tomasi
Corner detection is an approach used within computer vision systems to extract certain kinds of features and infer the contents of an image. Corner detection is frequently used in motion detection, image registration, video tracking, image mosaicing, panorama stitching, 3D reconstruction and object recognition. Corner detection overlaps with the topic of interest point detection. Formalization A corner can be defined as the intersection of two edges. A corner can also be defined as a point for which there are two dominant and different edge directions in a local neighbourhood of the point. An interest point is a point in an image which has a well-defined position and can be robustly detected. This means that an interest point can be a corner but it can also be, for example, an isolated point of local intensity maximum or minimum, line endings, or a point on a curve where the curvature is locally maximal. In practice, most so-called corner detection methods detect interest ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pentium 4
Pentium 4 is a series of single-core central processing unit, CPUs for Desktop computer, desktops, laptops and entry-level Server (computing), servers manufactured by Intel. The processors were shipped from November 20, 2000 until August 8, 2008. All Pentium 4 CPUs are based on the NetBurst microarchitecture, the successor to the P6 (microarchitecture), P6. The Pentium 4 #Willamette, Willamette (180 nm) introduced SSE2, while the #Prescott, Prescott (90 nm) introduced SSE3 and later 64-bit technology. Later versions introduced Hyper-threading, Hyper-Threading Technology (HTT). The first Pentium 4-branded processor to implement x86-64, 64-bit was the Prescott (90 nm) (February 2004), but this feature was not enabled. Intel subsequently began selling 64-bit Pentium 4s using the ''"E0" revision'' of the Prescotts, being sold on the OEM market as the Pentium 4, model F. The E0 revision also adds eXecute Disable (XD) (Intel's name for the NX bit) to Intel 64. Int ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Simulated Annealing
Simulated annealing (SA) is a probabilistic technique for approximating the global optimum of a given function. Specifically, it is a metaheuristic to approximate global optimization in a large search space for an optimization problem. For large numbers of local optima, SA can find the global optimum. It is often used when the search space is discrete (for example the traveling salesman problem, the boolean satisfiability problem, protein structure prediction, and job-shop scheduling). For problems where finding an approximate global optimum is more important than finding a precise local optimum in a fixed amount of time, simulated annealing may be preferable to exact algorithms such as gradient descent or branch and bound. The name of the algorithm comes from annealing in metallurgy, a technique involving heating and controlled cooling of a material to alter its physical properties. Both are attributes of the material that depend on their thermodynamic free energy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metaheuristic
In computer science and mathematical optimization, a metaheuristic is a higher-level procedure or heuristic designed to find, generate, tune, or select a heuristic (partial search algorithm) that may provide a sufficiently good solution to an optimization problem or a machine learning problem, especially with incomplete or imperfect information or limited computation capacity. Metaheuristics sample a subset of solutions which is otherwise too large to be completely enumerated or otherwise explored. Metaheuristics may make relatively few assumptions about the optimization problem being solved and so may be usable for a variety of problems. Their use is always of interest when exact or other (approximate) methods are not available or are not expedient, either because the calculation time is too long or because, for example, the solution provided is too imprecise. Compared to optimization algorithms and iterative methods, metaheuristics do not guarantee that a globally optimal sol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Binary Search Algorithm
In computer science, binary search, also known as half-interval search, logarithmic search, or binary chop, is a search algorithm that finds the position of a target value within a sorted array. Binary search compares the target value to the middle element of the array. If they are not equal, the half in which the target cannot lie is eliminated and the search continues on the remaining half, again taking the middle element to compare to the target value, and repeating this until the target value is found. If the search ends with the remaining half being empty, the target is not in the array. Binary search runs in logarithmic time in the worst case, making O(\log n) comparisons, where n is the number of elements in the array. Binary search is faster than linear search except for small arrays. However, the array must be sorted first to be able to apply binary search. There are specialized data structures designed for fast searching, such as hash tables, that can be searched ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decision Tree Model
In computational complexity theory, the decision tree model is the model of computation in which an algorithm can be considered to be a decision tree, i.e. a sequence of ''queries'' or ''tests'' that are done adaptively, so the outcome of previous tests can influence the tests performed next. Typically, these tests have a small number of outcomes (such as a yes–no question) and can be performed quickly (say, with unit computational cost), so the worst-case time complexity of an algorithm in the decision tree model corresponds to the depth of the corresponding tree. This notion of computational complexity of a problem or an algorithm in the decision tree model is called its decision tree complexity or query complexity. Decision tree models are instrumental in establishing lower bounds for the complexity of certain classes of computational problems and algorithms. Several variants of decision tree models have been introduced, depending on the computational model and type of quer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Profile-guided Optimization
In computer programming, profile-guided optimization (PGO, sometimes pronounced as ''pogo''), also known as profile-directed feedback (PDF) or feedback-directed optimization (FDO), is the compiler optimization technique of using prior analyses of software artifacts or behaviors (" profiling") to improve the expected runtime performance of the program. Method Optimization techniques based on static program analysis of the source code consider code performance improvements without actually executing the program. No dynamic program analysis is performed. For example, inferring or placing formal constraints on the number of iterations a loop is likely to execute is fundamentally useful when considering whether to unroll it or not, but such facts typically rely on complex runtime factors that are difficult to conclusively establish. Usually, static analysis will have incomplete information and only be able to approximate estimates of the eventual runtime conditions. The first high ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |