|
Fault Management
In network management, fault management is the set of functions that detect, isolate, and correct malfunctions in a telecommunications network, compensate for environmental changes, and include maintaining and examining error logs, accepting and acting on error detection notifications, tracing and identifying faults, carrying out sequences of diagnostics tests, correcting faults, reporting error conditions, and localizing and tracing faults by examining and manipulating database information. When a fault or event occurs, a network component will often send a notification to the network operator using a protocol such as SNMP. An alarm is a persistent indication of a fault that clears only when the triggering condition has been resolved. A current list of problems occurring on the network component is often kept in the form of an active alarm list such as is defined in RFC 3877, the Alarm MIB. A list of cleared faults is also maintained by most network management systems. Fault m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Management
Network management is the process of administering and managing computer networks. Services provided by this discipline include fault analysis, performance management, provisioning of networks and maintaining quality of service. Network management software is used by network administrators to help perform these functions. Technologies A small number of accessory methods exist to support network and network device management. Network management allows IT professionals to monitor network components within large network area. Access methods include the SNMP, command-line interface (CLI), custom XML, CMIP, Windows Management Instrumentation (WMI), Transaction Language 1 (TL1), CORBA, NETCONF, RESTCONF and the Java Management Extensions (JMX). Schemas include the Structure of Management Information (SMI), YANG, WBEM, the Common Information Model ( CIM Schema), and MTOSI amongst others. Value Effective network management can provide positive strategic impacts. For ex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
System Operator
A sysop (, an abbreviation of system operator) is an administrator of a multi-user computer system, such as a bulletin board system (BBS) or an online service virtual community.Jansen, E. & James, V. (2002). NetLingo: the Internet dictionary. Netlingo Inc., Oxnard, CA The phrase may also be used to refer to administrators of other Internet-based network services.Rhodes, D. & Butler, D. (2002). Solaris Operating Environment Boot Camp. Prentice Hall Professional. Sysops typically do not earn money, but donate their activity to the community. Co-sysops are users who may be granted certain admin privileges on a BBS. Generally, they help validate users and monitor discussion forums. Some co-sysops serve as file clerks, reviewing, describing, and publishing newly uploaded files into appropriate download directories.Gupta, A. (2004). Hacking In The Computer World. Mittal Publications. Historically, the term ''system operator'' applied to operators of any computer system, especially a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alarm Management
Alarm management is the application of human factors and ergonomics along with instrumentation engineering and systems thinking to manage the design of an alarm system to increase its usability. Most often the major usability problem is that there are too many alarms annunciated in a plant upset, commonly referred to as alarm flood (similar to an interrupt storm), since it is so similar to a flood caused by excessive rainfall input with a basically fixed drainage output capacity. However, there can also be other problems with an alarm system such as poorly designed alarms, improperly set alarm points, ineffective annunciation, unclear alarm messages, etc. Poor alarm management is one of the leading causes of unplanned downtime, contributing to over $20B in lost production every year, and of major industrial incidents. Developing good alarm management practices is not a discrete activity, but more of a continuous process (i.e., it is more of a journey than a destination). A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
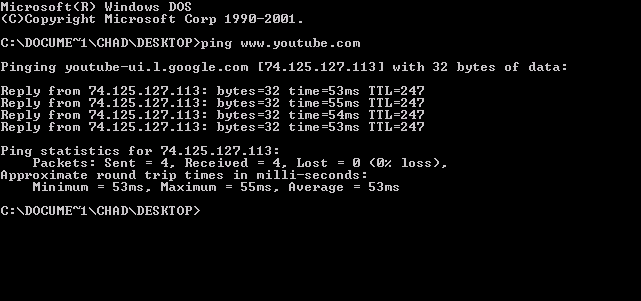
Ping (networking Utility)
ping is a computer network administration software utility used to test the reachability of a host (network), host on an Internet Protocol (IP) network. It is available in a wide range of operating systems including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a Pulse (signal processing), pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) Network packet, packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean (average), mean round-trip times, and standard deviation of the mean. Command-line options and Comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SNMP
Simple Network Management Protocol (SNMP) is an Internet Standard protocol for collecting and organizing information about managed devices on IP networks and for modifying that information to change device behavior. Devices that typically support SNMP include cable modems, routers, network switches, servers, workstations, printers, and more. SNMP is widely used in network management for network monitoring. SNMP exposes management data in the form of variables on the managed systems organized in a management information base (MIB), which describes the system status and configuration. These variables can then be remotely queried (and, in some circumstances, manipulated) by managing applications. Three significant versions of SNMP have been developed and deployed. SNMPv1 is the original version of the protocol. More recent versions, SNMPv2c and SNMPv3, feature improvements in performance, flexibility and security. SNMP is a component of the Internet Protocol Suite as define ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Phone
A mobile phone or cell phone is a portable telephone that allows users to make and receive calls over a radio frequency link while moving within a designated telephone service area, unlike fixed-location phones ( landline phones). This radio frequency link connects to the switching systems of a mobile phone operator, providing access to the public switched telephone network (PSTN). Modern mobile telephony relies on a cellular network architecture, which is why mobile phones are often referred to as 'cell phones' in North America. Beyond traditional voice communication, digital mobile phones have evolved to support a wide range of additional services. These include text messaging, multimedia messaging, email, and internet access (via LTE, 5G NR or Wi-Fi), as well as short-range wireless technologies like Bluetooth, infrared, and ultra-wideband (UWB). Mobile phones also support a variety of multimedia capabilities, such as digital photography, video recordin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Text Messaging
Text messaging, or texting, is the act of composing and sending electronic messages, typically consisting of alphabetic and numeric characters, between two or more users of mobile phones, tablet computers, smartwatches, desktops/laptops, or another type of compatible computer. Text messages may be sent over a cellular network or may also be sent via satellite or Internet connection. The term originally referred to messages sent using the Short Message Service (SMS) on mobile devices. It has grown beyond alphanumeric text to include multimedia messages using the Multimedia Messaging Service (MMS) and Rich Communication Services (RCS), which can contain digital images, videos, and sound content, as well as ideograms known as emoji ( happy faces, sad faces, and other icons), and on various instant messaging apps. Text messaging has been an extremely popular medium of communication since the turn of the century and has also influenced changes in society. Overview Text mess ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-mail
Electronic mail (usually shortened to email; alternatively hyphenated e-mail) is a method of transmitting and receiving Digital media, digital messages using electronics, electronic devices over a computer network. It was conceived in the late–20th century as the digital version of, or counterpart to, mail (hence ''wikt:e-#Etymology 2, e- + mail''). Email is a ubiquitous and very widely used communication medium; in current use, an email address is often treated as a basic and necessary part of many processes in business, commerce, government, education, entertainment, and other spheres of daily life in most countries. Email operates across computer networks, primarily the Internet access, Internet, and also local area networks. Today's email systems are based on a store-and-forward model. Email Server (computing), servers accept, forward, deliver, and store messages. Neither the users nor their computers are required to be online simultaneously; they need to connect, ty ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Administrator
A network administrator is a person designated in an organization whose responsibility includes maintaining computer infrastructures with emphasis on local area networks (LANs) up to wide area networks (WANs). Responsibilities may vary between organizations, but installing new hardware, on-site servers, enforcing licensing agreements, software-network interactions as well as network integrity and resilience are some of the key areas of focus. Duties The role of the network administrator can vary significantly depending on an organization's size, location, and socioeconomic considerations. Some organizations work on a user-to-technical support ratio, Network administrators are often involved in proactive work. This type of work will often include: * Designing network infrastructure * Implementing and configuring network hardware and software * Network monitoring and maintaining the network * Testing network for vulnerability & weakness * Providing technical support * Managing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Glitch
A glitch is a short-lived technical fault, such as a transient one that corrects itself, making it difficult to troubleshoot. The term is particularly common in the computing and electronics industries, in circuit bending, as well as among players of video games. More generally, all types of systems including human organizations and nature experience glitches. A glitch, which is slight and often temporary, differs from a more serious bug which is a genuine functionality-breaking problem. Alex Pieschel, writing for ''Arcade Review'', said: bug' is often cast as the weightier and more blameworthy pejorative, while 'glitch' suggests something more mysterious and unknowable inflicted by surprise inputs or stuff outside the realm of code". The word itself is sometimes humorously described as being short for "gremlins lurking in the computer hardware". Etymology Some reference books, including ''Random House's American Slang'', state that the term comes from the German word as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IETF
The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, a non-profit organization with local chapters around the world. Organization There is no membership in the IETF. Anyone can participate by signing up to a working group mailing list, or registering for an IETF meeting. The IETF operates in a bottom-up task creation mode, largely driven by working groups. Each working group normally has appointed two co-chairs (occasionally three); a charter that describes its focus; and what it is expected to produce, and when. It is open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Syslog
In computing, syslog () is a standard for message logging. It allows separation of the software that generates messages, the system that stores them, and the software that reports and analyzes them. Each message is labeled with a facility code, indicating the type of system generating the message, and is assigned a severity level. Computer system designers may use syslog for system management and security auditing as well as general informational, analysis, and debugging messages. A wide variety of devices, such as printers, routers, and message receivers across many platforms use the syslog standard. This permits the consolidation of logging data from different types of systems in a central repository. Implementations of syslog exist for many operating systems. When operating over a network, syslog uses a client-server architecture where a syslog server listens for and logs messages coming from clients. History Syslog was developed in the 1980s by Eric Allman as part of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |