|
Eudev
systemd is a software suite that provides an array of system components for Linux operating systems. The main aim is to unify service configuration and behavior across Linux distributions. Its primary component is a "system and service manager" — an init system used to Bootstrapping, bootstrap user space and manage process (computing), user processes. It also provides replacements for various Daemon (computing), daemons and utilities, including device management, login management, network connection management, and event logging. The name ''systemd'' adheres to the Unix convention of naming daemons by appending the letter ''d''. It also plays on the term "System D", which refers to a person's ability to adapt quickly and improvise to solve problems. Since 2015, the majority of Linux distributions have adopted systemd, having replaced other init systems such as SysV init. It has been praised by developers and users of distributions that adopted it for providing a stable, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fedora Linux
Fedora Linux is a Linux distribution developed by the Fedora Project. It was originally developed in 2003 as a continuation of the Red Hat Linux project. It contains software distributed under various free and open-source licenses and aims to be on the leading edge of open-source technologies. It is now the upstream source for CentOS Stream and Red Hat Enterprise Linux. Since the release of Fedora 21 in December 2014, three editions have been made available: personal computer, server and cloud computing. This was expanded to five editions for containerization and Internet of Things (IoT) as of the release of Fedora 37 in November 2022. A new version of Fedora Linux is released every six months. , Fedora Linux has an estimated 1.2 million users, and is also the distribution used by Linus Torvalds, creator of the Linux kernel (). Features Fedora has a reputation for focusing on innovation, integrating new technologies early on and working closely with upstream Linux commun ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Daemon (computing)
In computing, a daemon is a program that runs as a background process, rather than being under the direct control of an interactive user. Customary convention is to name a daemon process with the letter ''d'' as a suffix to indicate that it's a daemon. For example, is a daemon that implements system logging facility, and is a daemon that serves incoming SSH connections. Even though the concept can apply to many computing systems, the term ''daemon'' is used almost exclusively in the context of Unix-based systems. In other contexts, different terms are used for the same concept. Systems often start daemons at boot time that will respond to network requests, hardware activity, or other programs by performing some task. Daemons such as cron may also perform defined tasks at scheduled times. Terminology In the context of computing, the word is generally pronounced either as or . The term was coined by the programmers at MIT's Project MAC. According to Fernando J. Cor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FreeBSD
FreeBSD is a free-software Unix-like operating system descended from the Berkeley Software Distribution (BSD). The first version was released in 1993 developed from 386BSD, one of the first fully functional and free Unix clones on affordable home-class hardware, and has since continuously been the most commonly used BSD-derived operating system. FreeBSD maintains a complete system, delivering a kernel, device drivers, userland utilities, and documentation, as opposed to Linux only delivering a kernel and drivers, and relying on third-parties such as GNU for system software. The FreeBSD source code is generally released under a permissive BSD license, as opposed to the copyleft GPL used by Linux. The project includes a security team overseeing all software shipped in the base distribution. Third-party applications may be installed using the pkg package management system or from source via FreeBSD Ports. The project is supported and promoted by the FreeBSD Foundation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
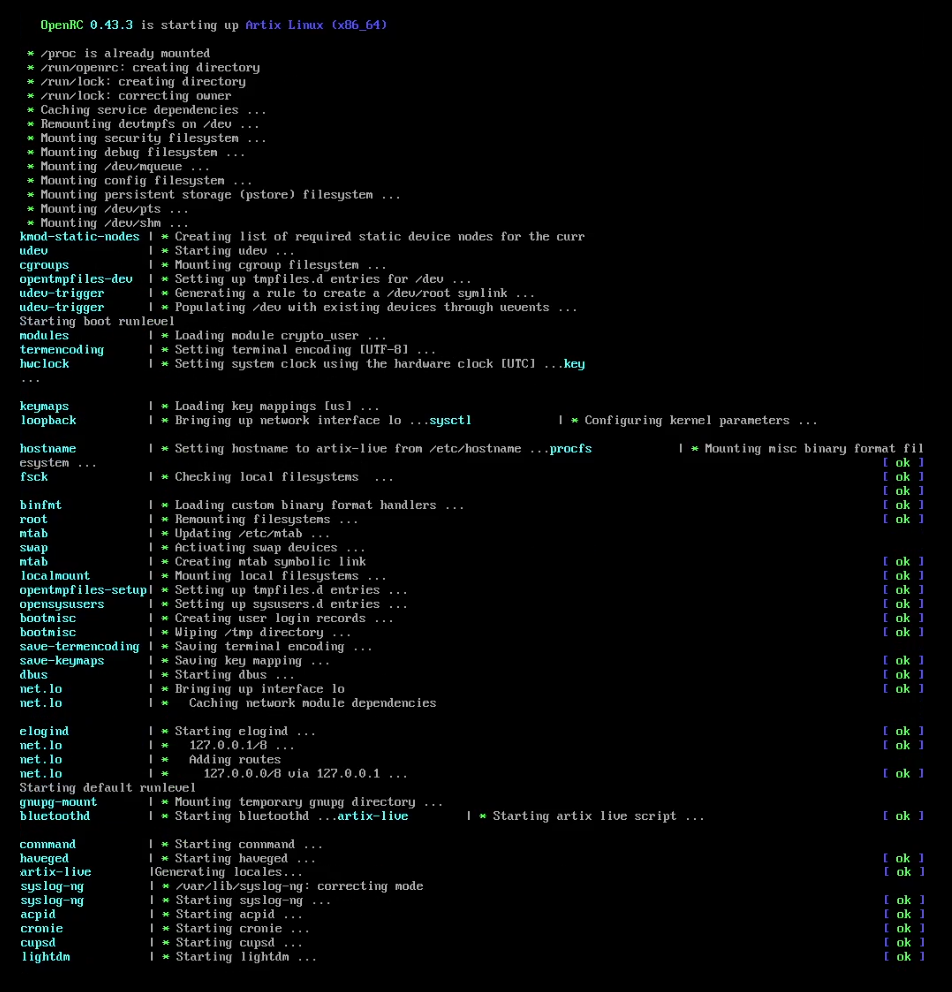
OpenRC
OpenRC is a dependency-based init system for Unix-like computer operating systems. It was created by Roy Marples, a NetBSD developer who was also active in the Gentoo Linux, Gentoo project. It became more broadly adopted as an init system outside of Gentoo following the decision by some Linux distributions not to adopt systemd. Adoption OpenRC is the default init system or Process supervision, process supervisor for: * Alpine Linux * Funtoo * Gentoo Linux * Hyperbola GNU/Linux-libre * Maemo#Maemo Leste, Maemo Leste * Nitrux OpenRC is an available init system or Process supervision, process supervisor for: * Artix Linux (some consider it the default) * Devuan * Parabola GNU/Linux-libre * Arch Linux (Available through the Arch User Repository) * PostmarketOS Design OpenRC is made up of several modular components, the main ones being an init (optional), the core dependency management system and a daemon supervisor (optional). It is written in C and POSIX-compliant shell, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Surface
The attack surface of a software environment is the sum of the different points (for " attack vectors") where an unauthorized user (the "attacker") can try to enter data to, extract data, control a device or critical software in an environment. Keeping the attack surface as small as possible is a basic security measure. Elements of an attack surface Worldwide digital change has accelerated the size, scope, and composition of an organization's attack surface. The size of an attack surface may fluctuate over time, adding and subtracting assets and digital systems (e.g. websites, hosts, cloud and mobile apps, etc.). Attack surface sizes can change rapidly as well. Digital assets eschew the physical requirements of traditional network devices, servers, data centers, and on-premise networks. This leads to attack surfaces changing rapidly, based on the organization's needs and the availability of digital services to accomplish it. Attack surface scope also varies from organization ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unix-like
A Unix-like (sometimes referred to as UN*X, *nix or *NIX) operating system is one that behaves in a manner similar to a Unix system, although not necessarily conforming to or being certified to any version of the Single UNIX Specification. A Unix-like Application software, application is one that behaves like the corresponding List of POSIX commands, Unix command or Unix shell, shell. Although there are general Unix philosophy, philosophies for Unix design, there is no technical standard defining the term, and opinions can differ about the degree to which a particular operating system or application is Unix-like. Some well-known examples of Unix-like operating systems include Linux, FreeBSD and OpenBSD. These systems are often used on servers as well as on personal computers and other devices. Many popular applications, such as the Apache HTTP Server, Apache web server and the Bash (Unix shell), Bash shell, are also designed to be used on Unix-like systems. Definition The Open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GNOME
A gnome () is a mythological creature and diminutive spirit in Renaissance magic and alchemy, introduced by Paracelsus in the 16th century and widely adopted by authors, including those of modern fantasy literature. They are typically depicted as small humanoids who live underground. Gnome characteristics are reinterpreted to suit various storytellers and artists. Paracelsus's gnome is recognized to have derived from the German miners' legend about or , the "metallurgical or mineralogical demon", according to Georg Agricola (1530), also called (literal Latinization of ''Bergmännlein'', "mountain manikin") by Agriocola in a later work (1549), and described by other names such as (sing. ; Latinization of German ). Agricola recorded that, according to the legends of that profession, these mining spirits acted as miming and laughing pranksters who sometimes threw pebbles at miners, but could also reward them by depositing a rich vein of silver ore. Paracelsus also called ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Bloat
Software bloat is a process whereby successive versions of a computer program become perceptibly slower, use more memory, disk space or processing power, or have higher hardware requirements than the previous version, while making only dubious user-perceptible improvements or suffering from feature creep. The term is not applied consistently; it is often used as a pejorative by end users, including to describe undesired user interface changes even if those changes had little or no effect on the hardware requirements. In long-lived software, bloat can occur from the software servicing a large, diverse marketplace with many differing requirements. Most end users will feel they only need some limited subset of the available functions, and will regard the others as unnecessary bloat, even if end users with different requirements require those functions. Actual (measurable) bloat can occur due to de-emphasising algorithmic efficiency in favour of other concerns like developer produ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mission Creep
Mission creep is the gradual or incremental expansion of an intervention, project or mission, beyond its original scope, focus or goals, a ratchet effect spawned by initial success. Mission creep is usually considered undesirable due to how each success breeds more ambitious interventions until a final failure happens, stopping the intervention entirely. The term was originally applied exclusively to military operations, but has recently been applied to many other fields, making the phrase autological. The phrase first appeared in 1993, in articles published in ''The Washington Post'' and in ''The New York Times'' concerning the United Nations peacekeeping mission during the Somali Civil War. History Somali Civil War The first two articles to use the term in the ''Washington Post'' were both by columnist Jim Hoagland ("Prepared for Non-Combat", April 15, 1993, and ''Beware 'mission creep' In Somalia'', July 20, 1993). The ''New York Times'' used the term for the first time i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mount Point
Mounting is a process by which a computer's operating system makes files and directories on a storage device (such as hard drive, CD-ROM, or network share) available for users to access via the computer's file system. In general, the process of mounting comprises the operating system acquiring access to the storage medium; recognizing, reading, and processing file system structure and metadata on it before registering them to the virtual file system (VFS) component. The location in the VFS to which the newly mounted medium was registered is called a " mount point"; when the mounting process is completed, the user can access files and directories on the medium from there. An opposite process of mounting is called unmounting, in which the operating system cuts off all user access to files and directories on the mount point, writes the remaining queue of user data to the storage device, refreshes file system metadata, then relinquishes access to the device, making the storage ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Process (computing)
In computing, a process is the Instance (computer science), instance of a computer program that is being executed by one or many thread (computing), threads. There are many different process models, some of which are light weight, but almost all processes (even entire virtual machines) are rooted in an operating system (OS) process which comprises the program code, assigned system resources, physical and logical access permissions, and data structures to initiate, control and coordinate execution activity. Depending on the OS, a process may be made up of multiple threads of execution that execute instructions Concurrency (computer science), concurrently. While a computer program is a passive collection of Instruction set, instructions typically stored in a file on disk, a process is the execution of those instructions after being loaded from the disk into memory. Several processes may be associated with the same program; for example, opening up several instances of the same progra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Parallelism (computing)
Parallel computing is a type of computation in which many calculations or processes are carried out simultaneously. Large problems can often be divided into smaller ones, which can then be solved at the same time. There are several different forms of parallel computing: bit-level, instruction-level, data, and task parallelism. Parallelism has long been employed in high-performance computing, but has gained broader interest due to the physical constraints preventing frequency scaling.S.V. Adve ''et al.'' (November 2008)"Parallel Computing Research at Illinois: The UPCRC Agenda" (PDF). Parallel@Illinois, University of Illinois at Urbana-Champaign. "The main techniques for these performance benefits—increased clock frequency and smarter but increasingly complex architectures—are now hitting the so-called power wall. The computer industry has accepted that future performance increases must largely come from increasing the number of processors (or cores) on a die, rather than mak ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |