|
End Node Problem
The end node problem arises when individual computers are used for sensitive work and/or temporarily become part of a trusted, well-managed network/cloud and then are used for more risky activities and/or join untrusted networks. (Individual computers on the periphery of networks/clouds are called end nodes.) End nodes often are not managed to the trusted network‘s high computer security standards. End nodes often have weak/outdated software, weak security tools, excessive permissions, mis-configurations, questionable content and apps, and covert exploitations. Cross contamination and unauthorized release of data from within a computer system becomes the problem. Within the vast cyber-ecosystem, these end nodes often attach transiently to one or more clouds/networks, some trustworthy and others not. A few examples: a corporate desktop browsing the Internet, a corporate laptop checking company webmail via a coffee shop's open Wi-Fi access point, a personal computer used to teleco ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Kernel (operating System)
A kernel is a computer program at the core of a computer's operating system that always has complete control over everything in the system. The kernel is also responsible for preventing and mitigating conflicts between different processes. It is the portion of the operating system code that is always resident in memory and facilitates interactions between hardware and software components. A full kernel controls all hardware resources (e.g. I/O, memory, cryptography) via device drivers, arbitrates conflicts between processes concerning such resources, and optimizes the use of common resources, such as CPU, cache, file systems, and network sockets. On most systems, the kernel is one of the first programs loaded on startup (after the bootloader). It handles the rest of startup as well as memory, peripherals, and input/output (I/O) requests from software, translating them into data-processing instructions for the central processing unit. The critical code of the kernel is usua ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Network Security
A network security policy (NSP) is a generic document that outlines rules for computer network access, determines how policies are enforced and lays out some of the basic architecture of the company security/ network security environment. The document itself is usually several pages long and written by a committee. A security policy is a complex document, meant to govern data access, web-browsing habits, use of passwords, encryption, email attachments and more. It specifies these rules for individuals or groups of individuals throughout the company. The policies could be expressed as a set of instructions that understood by special purpose network hardware dedicated for securing the network. Security policy should keep the malicious users out, and also exert control over potential risky users within an organization. Understanding what information and services are available and to which users, as well as what the potential is for damage and whether any protection is already in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Secure End Node
A Secure End Node is a trusted, individual computer that temporarily becomes part of a trusted, sensitive, well-managed network and later connects to many other (un)trusted networks/clouds. SEN's cannot communicate good or evil data between the various networks (e.g. exfiltrate sensitive information, ingest malware, etc.). SENs often connect through an untrusted medium (e.g. the Internet) and thus require a secure connection and strong authentication (of the device, software, user, environment, etc.). The amount of trust required (and thus operational, physical, personnel, network, and system security applied) is commensurate with the risk of piracy, tampering, and reverse engineering (within a given threat environment). An essential characteristic of SENs is they cannot persist information as they change between networks (or domains). The remote, private, and secure network might be organization's in-house network or a cloud service. A Secure End Node typically involves auth ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Node (networking)
In Computer network, networking, a node (, ‘knot’) is either a redistribution point or a communication endpoint within telecommunication networks. A physical network node is an electronic device that is attached to a network, and is capable of creating, receiving, or transmitting information over a communication channel. In data communication, a physical network node may either be data communication equipment (such as a modem, Network hub, hub, Network bridge, bridge or Network switch, switch) or data terminal equipment (such as a digital telephone handset, a printer or a host computer). A Passivity (engineering), passive distribution point such as a distribution frame or patch panel is not a node. Computer networks In data communication, a physical network node may either be data communication equipment (DCE) such as a modem, Network hub, hub, Network bridge, bridge or Network switch, switch; or data terminal equipment (DTE) such as a digital telephone handset, a printe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Host (network)
A network host is a computer or other device connected to a computer network. A host may work as a server offering information resources, services, and applications to users or other hosts on the network. Hosts are assigned at least one network address. A computer participating in networks that use the Internet protocol suite may also be called an IP host. Specifically, computers participating in the Internet are called Internet hosts. Internet hosts and other IP hosts have one or more IP addresses assigned to their network interfaces. The addresses are configured either manually by an administrator, automatically at startup by means of the Dynamic Host Configuration Protocol (DHCP), or by stateless address autoconfiguration methods. Network hosts that participate in applications that use the client–server model of computing are classified as server or client systems. Network hosts may also function as nodes in peer-to-peer applications, in which all nodes share and consum ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
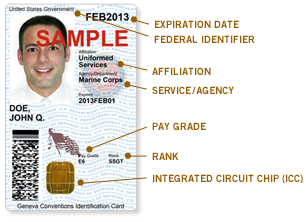
Common Access Card
The common access card, also commonly referred to as the CAC, is the standard identification for active duty United States defense personnel. The card itself is a smart card about the size of a credit card. Defense personnel that use the CAC include the Selected Reserve and National Guard, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions (especially the Third Geneva Convention). In combination with a personal identification number, a CAC satisfies the requirement for two-factor authentication: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature and data encryption t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
LiveCD
A live CD (also live DVD, live disc, or live operating system) is a complete booting, bootable computer installation including operating system which runs directly from a CD-ROM or similar storage device into a computer's memory, rather than loading from a hard disk drive. A live CD allows users to run an computer operating system, operating system for any purpose without installing it or making any changes to the computer's configuration. Live CDs can run on a computer without Computer data storage, secondary storage, such as a hard disk drive, or with a corrupted hard disk drive or file system, allowing data recovery. As CD and DVD drives have been steadily phased-out, live CDs have become less popular, being replaced by live USBs, which are equivalent systems written onto USB flash drives, which have the added benefit of having writeable storage. The functionality of a live CD is also available with an Disk enclosure, external hard disk drive connected by USB. Many live CDs o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Lightweight Portable Security
Lightweight Portable Security (LPS) or Trusted End Node Security (TENS) was a Linux LiveCD (or LiveUSB) distribution. The application Encryption Wizard, originally bundled with TENS is still actively maintained. LPS and its successor TENS was developed and publicly distributed by the United States Department of Defense’s Air Force Research Laboratory The live CD is designed to serve as a secure end node. The Air Force Research Laboratory actively maintained LPS and TENS from 2007 to 2021. It can run on almost any x86_64 computer (PC or Mac). LPS boots only in RAM, creating a pristine, non-persistent end node. It supports DoD-approved Common Access Card (CAC) readers, as required for authenticating users into PKI-authenticated gateways to access internal DoD networks. LPS turns an untrusted system (such as a home computer) into a trusted network client. No trace of work activity (or malware) can be written to the local computer's hard drive. As of September 2011 (version 1. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Etherboot
gPXE is an open-source software, open-source Preboot Execution Environment, Preboot eXecution Environment (PXE) client firmware implementation and bootloader derived from Etherboot. It can be used to enable computers without built-in PXE support to boot from the network, or to extend an existing client PXE implementation with support for additional protocols. While standard PXE clients use Trivial File Transfer Protocol, TFTP to transfer data, gPXE client firmware adds the ability to retrieve data through other protocols like Hypertext Transfer Protocol, HTTP, iSCSI and ATA over Ethernet (AoE), and can work with Wi-Fi rather than requiring a wired connection. gPXE development ceased in summer 2010, and several projects are migrating or considering migrating to iPXE as a result. PXE implementation gPXE can be loaded by a computer in several ways: *from media like floppy disk, USB flash drive, or hard disk drive, hard disk *as a pseudo Linux kernel *as an Executable and Linkab ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Wi-Fi
Wi-Fi () is a family of wireless network protocols based on the IEEE 802.11 family of standards, which are commonly used for Wireless LAN, local area networking of devices and Internet access, allowing nearby digital devices to exchange data by radio waves. These are the most widely used computer networks, used globally in small office/home office, home and small office networks to link devices and to provide Internet access with wireless routers and wireless access points in public places such as coffee shops, restaurants, hotels, libraries, and airports. ''Wi-Fi'' is a trademark of the Wi-Fi Alliance, which restricts the use of the term "''Wi-Fi Certified''" to products that successfully complete Interoperability Solutions for European Public Administrations, interoperability certification testing. Non-compliant hardware is simply referred to as WLAN, and it may or may not work with "''Wi-Fi Certified''" devices. the Wi-Fi Alliance consisted of more than 800 companies from ar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |