|
Cleartext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted. Overview With the advent of computing, the term ''plaintext'' expanded beyond human-readable documents to mean any data, including binary files, in a form that can be viewed or used without requiring a key or other decryption device. Information—a message, document, file, etc.—if to be communicated or stored in an unencrypted form is referred to as plaintext. Plaintext is used as input to an encryption algorithm; the output is usually termed ciphertext, particularly when the algorithm is a cipher. Codetext is less often used, and almost always only when the algorithm involved is actually a code. Some systems use multiple layers of encryption, with the output of one encryption algorithm becoming "plaintext" input for the next. Secure handling Insecure handling of pl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Cryptographic Algorithm
In cryptography, encryption (more specifically, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Encryption Algorithm
In cryptography, encryption (more specifically, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military mes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
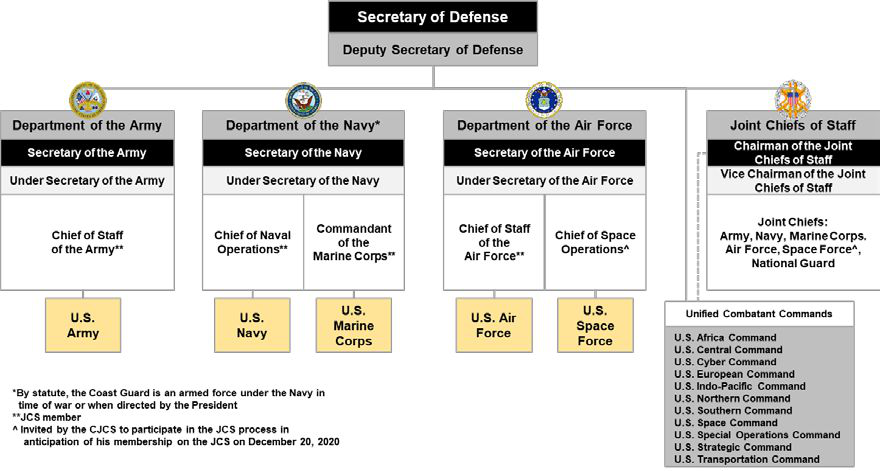 |
US Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an executive department of the U.S. federal government charged with coordinating and supervising the six U.S. armed services: the Army, Navy, Marines, Air Force, Space Force, the Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provide the military forces needed to deter war and ensure our nation's security". The current Secretary of Defense is Pete Hegseth. The Department of Defense is headed by the secretary of defense, a cabinet-level head who reports directly to the president of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
Directory (file Systems)
Directory may refer to: * Directory (computing), or folder, a file system structure in which to store computer files * Directory (OpenVMS command) * Directory service, a software application for organizing information about a computer network's users and resources * Directory (political), a system under which a country is ruled by a college of several people who jointly exercise the powers of a head of state or head of government ** French Directory The Directory (also called Directorate; ) was the system of government established by the Constitution of the Year III, French Constitution of 1795. It takes its name from the committee of 5 men vested with executive power. The Directory gov ..., the government in revolutionary France from 1795 to 1799 ** Provisional All-Russian Government, a short-lived, anti-Communist government formed during the Russian Civil War, known as "the Directory" * Business directory, a listing of information about suppliers and manufacturers * Ci ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
|
Peter Gutmann (computer Scientist)
Peter Claus Gutmann is a computer scientist in the Department of Computer Science at the University of Auckland, Auckland, New Zealand. He has a Ph.D. in computer science from the University of Auckland. His Ph.D. thesis and a book based on the thesis were about a cryptographic security architecture. He is interested in computer security issues, including security architecture, security usability (or more usually the lack thereof), and hardware security; he has discovered several flaws in publicly released cryptosystems and protocols. He is the developer of the cryptlib open source software security library and contributed to PGP version 2. In 1994 he developed the Secure FileSystem (SFS). He is also known for his analysis of data deletion on electronic memory media, magnetic and otherwise, and devised the Gutmann method for erasing data from a hard drive more or less securely. These analyses have gained great popularity, although they are based on numerous inaccuracies an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
University Of Auckland
The University of Auckland (; Māori: ''Waipapa Taumata Rau'') is a public research university based in Auckland, New Zealand. The institution was established in 1883 as a constituent college of the University of New Zealand. Initially located in a repurposed courthouse, the university has grown substantially over the years. As of 2024, it stands as the largest university in New Zealand by enrolment, teaching approximately 43,000 students across three major campuses in central Auckland. The university conducts teaching and learning within six faculties, two research institutes, and other institutes and centres. The City Campus, in the Auckland central business district, hosts the majority of students and faculties. History Origins The University of Auckland began as a constituent college of the University of New Zealand, founded on 23 May 1883 as ''Auckland University College''. Stewardship of the university during its establishment period was the responsibility of Joh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Data Remanence
Data remanence is the residual representation of digital data that remains even after attempts have been made to remove or erase the data. This residue may result from data being left intact by a nominal file deletion operation, by reformatting of storage media that does not remove data previously written to the media, or through physical properties of the storage media that allow previously written data to be recovered. Data remanence may make inadvertent disclosure of sensitive information possible should the storage media be released into an uncontrolled environment (''e.g.'', thrown in the bin (trash) or lost). Various techniques have been developed to counter data remanence. These techniques are classified as clearing, purging/sanitizing, or destruction. Specific methods include overwriting, degaussing, encryption, and media destruction. Effective application of countermeasures can be complicated by several factors, including media that are inaccessible, media that c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
US State Department
The United States Department of State (DOS), or simply the State Department, is an executive department of the U.S. federal government responsible for the country's foreign policy and relations. Equivalent to the ministry of foreign affairs of other nations, its primary duties are advising the U.S. president on international relations, administering diplomatic missions, negotiating international treaties and agreements, protecting citizens abroad and representing the U.S. at the United Nations. The department is headquartered in the Harry S Truman Building, a few blocks from the White House, in the Foggy Bottom neighborhood of Washington, D.C.; "Foggy Bottom" is thus sometimes used as a metonym. Established in 1789 as the first administrative arm of the U.S. executive branch, the State Department is considered among the most powerful and prestigious executive agencies. It is headed by the U.S. secretary of state, who reports directly to the U.S. president and is a member o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
 |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
British Secret Service
The Secret Intelligence Service (SIS), commonly known as MI6 (MI numbers, Military Intelligence, Section 6), is the foreign intelligence service of the United Kingdom, tasked mainly with the covert overseas collection and analysis of Human intelligence (intelligence gathering), human intelligence on foreign nationals in support of its Five Eyes partners. SIS is one of the British intelligence agencies and the Chief of the Secret Intelligence Service ("C") is directly accountable to the Foreign Secretary (United Kingdom), Foreign Secretary. Formed in 1909 as the foreign section of the Secret Service Bureau, the section grew greatly during the World War I, First World War, officially adopting its current name around 1920. The name "MI6" originated as a convenient label during the World War II, Second World War, when SIS was known by many names. It is still commonly used today. The existence of SIS was not officially acknowledged until 1994. That year the Intelligence Services A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
|
 |
Discarded Computers
Electronic waste (or e-waste) describes discarded electrical or electronic devices. It is also commonly known as waste electrical and electronic equipment (WEEE) or end-of-life (EOL) electronics. Used electronics which are destined for refurbishment, reuse, resale, salvage recycling through material recovery, or disposal are also considered e-waste. Informal processing of e-waste in developing countries can lead to adverse human health effects and environmental pollution. The growing consumption of electronic goods due to the Digital Revolution and innovations in science and technology, such as bitcoin, has led to a global e-waste problem and hazard. The rapid exponential increase of e-waste is due to frequent new model releases and unnecessary purchases of electrical and electronic equipment (EEE), short innovation cycles and low recycling rates, and a drop in the average life span of computers. Electronic scrap components, such as CPUs, contain potentially harmful materials s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |