|
Basic Direct Access Method
Basic Direct Access Method, or BDAM is an access method for IBM's OS/360 and successors computer operating systems on System/360 and later mainframes. BDAM "consists of routines used in retrieving data from, and storing data onto, direct access devices." BDAM is available on OS/360, OS/VS2, MVS, z/OS, and related high-end operating systems. Description ''Basic'', in IBM terminology, indicates a lower-level access method that deals with data sets in terms of physical blocks and does not provide either read-ahead, called ''anticipatory buffering'', or ''synchronization'' — that is, the user program has to explicitly wait for completion of each input/output event. With BDAM, "the programmer can directly store and retrieve a block by specifying either its actual device address, its relative position within a data set (relative block number), or the relative track within a data set at which the system is to begin a search. BDAM provides no index or structure to the file ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Method
An access method is a function of a mainframe operating system that enables access to data on disk, tape or other external devices. Access methods were present in several mainframe operating systems since the late 1950s, under a variety of names; the name ''access method'' was introduced in 1963 in the IBM OS/360 operating system.M. A. Auslander, D. C. Larkin, A. L. Scherr: "The Evolution of the MVS Operating System", pages 478-479 Access methods provide an application programming interface (API) for programmers to transfer data to or from device, and could be compared to |
Microsoft Windows
Windows is a group of several Proprietary software, proprietary graphical user interface, graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for servers, and Windows IoT for embedded systems. Defunct Windows families include Windows 9x, Windows Mobile, and Windows Phone. The first version of Windows was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). Windows is the most popular desktop operating system in the world, with Usage share of operating systems, 75% market share , according to StatCounter. However, Windows is not the most used operating system when including both mobile and desktop OSes, due to Android (operating system), Android's massive growth. , the most recent version of Windows is Windows 11 for consumer Personal compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IBM 2321 Data Cell
The IBM 2321 Data Cell announced in April 1964 (withdrawn January 1975) is a discontinued direct access storage device (DASD) for the IBM System/360. It holds up to 400 megabytes of data, with an access time of 95 milliseconds to 600 milliseconds, depending on the addressed strip position and data arrangement in each data cell. The 2321 was whimsically known as the "noodle picker" since the removable magnetic strips were flexible and resembled lasagna noodles. Characteristics The 2321 houses up to ten removable and interchangeable ''data cells'', each containing 40 megabytes. Each data cell contains 200 strips of magnetic tape, which are the basic recording media. Strips are wide and long. The total storage capacity is 400 megabytes or 800 million decimal digits. Up to eight 2321s can be attached to the IBM 2841 Control Unit, allowing an overall capacity of over three GB.IBM System Reference Library, IBM System/360 Component Descriptions, Form A26-5988 In comparison to th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Function
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called ''hash values'', ''hash codes'', ''digests'', or simply ''hashes''. The values are usually used to index a fixed-size table called a ''hash table''. Use of a hash function to index a hash table is called ''hashing'' or ''scatter storage addressing''. Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Hashing is a computationally and storage space-efficient form of data access that avoids the non-constant access time of ordered and unordered lists and structured trees, and the often exponential storage requirements of direct access of state spaces of large or variable-length keys. Use o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Buffer
In computer science, a data buffer (or just buffer) is a region of a memory used to temporarily store data while it is being moved from one place to another. Typically, the data is stored in a buffer as it is retrieved from an input device (such as a microphone) or just before it is sent to an output device (such as speakers). However, a buffer may be used when moving data between processes within a computer. This is comparable to buffers in telecommunication. Buffers can be implemented in a fixed memory location in hardware—or by using a virtual data buffer in software, pointing at a location in the physical memory. In all cases, the data stored in a data buffer are stored on a physical storage medium. A majority of buffers are implemented in software, which typically use the faster RAM to store temporary data, due to the much faster access time compared with hard disk drives. Buffers are typically used when there is a difference between the rate at which data is received and t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Macro Instruction
In computer programming, a macro (short for "macro instruction"; ) is a rule or pattern that specifies how a certain input should be mapped to a replacement output. Applying a macro to an input is known as macro expansion. The input and output may be a sequence of lexical tokens or characters, or a syntax tree. Character macros are supported in software applications to make it easy to invoke common command sequences. Token and tree macros are supported in some programming languages to enable code reuse or to extend the language, sometimes for domain-specific languages. Macros are used to make a sequence of computing instructions available to the programmer as a single program statement, making the programming task less tedious and less error-prone. (Thus, they are called "macros" because a "big" block of code can be expanded from a "small" sequence of characters.) Macros often allow positional or keyword parameters that dictate what the conditional assembler program generate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asynchronous I/O
In computer science, asynchronous I/O (also non-sequential I/O) is a form of input/output processing that permits other processing to continue before the transmission has finished. A name used for asynchronous I/O in the Windows API is overlapped I/O. Input and output (I/O) operations on a computer can be extremely slow compared to the processing of data. An I/O device can incorporate mechanical devices that must physically move, such as a hard drive seeking a track to read or write; this is often orders of magnitude slower than the switching of electric current. For example, during a disk operation that takes ten milliseconds to perform, a processor that is clocked at one gigahertz could have performed ten million instruction-processing cycles. A simple approach to I/O would be to start the access and then wait for it to complete. But such an approach (called synchronous I/O, or blocking I/O) would block the progress of a program while the communication is in progress, leaving ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Contiguous Data Storage
In computer storage, fragmentation is a phenomenon in which storage space, main storage or secondary storage, is used inefficiently, reducing capacity or performance and often both. The exact consequences of fragmentation depend on the specific system of storage allocation in use and the particular form of fragmentation. In many cases, fragmentation leads to storage space being "wasted", and in that case the term also refers to the wasted space itself. Basic principle When a computer program requests blocks of memory from the computer system, the blocks are allocated in chunks. When the computer program is finished with a chunk, it can free it back to the system, making it available to later be allocated again to another or the same program. The size and the amount of time a chunk is held by a program varies. During its lifespan, a computer program can request and free many chunks of memory. When a program is started, the free memory areas are long and contiguous. Over time a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
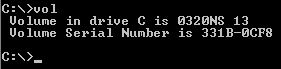
Volume (computing)
In computer data storage, a volume or logical drive is a single accessible storage area with a single file system, typically (though not necessarily) resident on a single partition of a hard disk. Although a volume might be different from a physical disk drive, it can still be accessed with an operating system's logical interface. However, a volume differs from a partition. Differences from partition A volume is not the same thing as a partition. For example, a floppy disk might be accessible as a volume, even though it does not contain a partition, as floppy disks cannot be partitioned with most modern computer software. Also, an OS can recognize a partition without recognizing any volume associated with it, as when the OS cannot interpret the filesystem stored there. This situation occurs, for example, when Windows NT-based OSes encounter disks with non-Microsoft OS partitions, such as the ext3 filesystem commonly used with Linux. Another example occurs in the Intel world w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Extent (file Systems)
In computing, an extent is a contiguous area of storage reserved for a file in a file system, represented as a range of block numbers, or tracks on count key data devices. A file can consist of zero or more extents; one file fragment requires one extent. The direct benefit is in storing each range compactly as two numbers, instead of canonically storing every block number in the range. Also, extent allocation results in less file fragmentation. Extent-based file systems can also eliminate most of the metadata overhead of large files that would traditionally be taken up by the block-allocation tree. But because the savings are small compared to the amount of stored data (for all file sizes in general) but make up a large portion of the metadata (for large files), the overall benefits in storage efficiency and performance are slight. In order to resist fragmentation, several extent-based file systems do allocate-on-flush. Many modern fault-tolerant file systems also do copy-o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Control Block
In IBM mainframe operating systems, such as OS/360, MVS, z/OS, a Data Control Block (DCB) is a description of a dataset in a program. A DCB is coded in Assembler programs using the DCB macro instruction (which expands into a large number of "define constant" instructions). High level language programmers use library routines containing DCBs. A DCB is one of the many ''control blocks'' used in these operating systems. A ''control block'' is a data area with a predefined structure, very similar to a C struct, but typically only related to system's functions. A DCB may be compared to a FILE structure in C, but it is much more complex, offering many more options for various access methods. The control block acted as the Application programming interface between Logical IOCS and the application program and usually was defined within (and resided within) the application program itself. The addresses of I/O subroutines would be resolved during a linkedit phase after compilation or else ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IBM 3390
IBM manufactured magnetic disk storage devices from 1956 to 2003, when it sold its hard disk drive business to Hitachi. Both the hard disk drive (HDD) and floppy disk drive (FDD) were invented by IBM and as such IBM's employees were responsible for many of the innovations in these products and their technologies. The basic mechanical arrangement of hard disk drives has not changed since the IBM 1301. Disk drive performance and characteristics are measured by the same standards now as they were in the 1950s. Few products in history have enjoyed such spectacular declines in cost and physical size along with equally dramatic improvements in capacity and performance. IBM manufactured 8-inch floppy disk drives from 1969 until the mid-1980s, but did not become a significant manufacturer of smaller-sized, 5.25- or 3.5-inch floppy disk drives (the dimension refers to the diameter of the floppy disk, not the size of the drive). IBM always offered its magnetic disk drives for sale but did no ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |