|
Sanitization (classified Information)
Redaction or sanitization is the process of removing information sensitivity, sensitive information from a document so that it may be distributed to a broader audience. It is intended to allow the selective disclosure of information. Typically, the result is a document that is suitable for publication or for dissemination to others rather than the intended audience of the original document. When the intent is secrecy, secrecy protection, such as in dealing with classified information, redaction attempts to reduce the document's classification level, possibly yielding an unclassified document. When the intent is privacy, privacy protection, it is often called data anonymization. Originally, the term ''sanitization'' was applied to printed documents; it has since been extended to apply to computer files and the problem of data remanence. Government secrecy In the context of government documents, redaction (also called sanitization) generally refers more specifically to the process ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Sensitivity
Information sensitivity is the control of access to information or knowledge that might result in loss of an advantage or level of security if disclosed to others. Loss, misuse, modification, or Access control, unauthorized access to sensitive information can adversely affect the privacy or welfare of an individual, trade secrets of a business or even the national security, security and international relations of a nation depending on the level of sensitivity and nature of the information. Non-sensitive information Public information This refers to information that is already a matter of public record or knowledge. With regard to government and private organizations, access to or release of such information may be requested by any member of the public, and there are often formal processes laid out for how to do so. The accessibility of government-held public records is an important part of government transparency, accountability to its citizens, and the values of democracy. Publ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Military Intelligence
Military intelligence is a military discipline that uses information collection and analysis List of intelligence gathering disciplines, approaches to provide guidance and direction to assist Commanding officer, commanders in decision making process, their decisions. This aim is achieved by providing an intelligence analysis, assessment of data from a range of sources, directed towards the commanders' mission requirements or responding to questions as part of operational or campaign planning. To provide an analysis, the commander's information requirements are first identified, which are then incorporated into intelligence collection, analysis, and dissemination. Areas of study may include the operational environment, hostile, friendly and neutral forces, the civilian population in an area of combat operations, and other broader areas of interest. Intelligence activities are conducted at all levels, from tactical to strategic, in peacetime, the period of transition to war, and d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cut, Copy, And Paste
Cut, copy, and paste are essential commands of modern human–computer interaction and user interface design. They offer an interprocess communication technique for transferring data through a computer's user interface. The ''cut'' command removes the selected data from its original position, and the ''copy'' command creates a duplicate; in both cases the selected data is kept in temporary storage called the clipboard. Clipboard data is later inserted wherever a ''paste'' command is issued. The data remains available to any application supporting the feature, thus allowing easy data transfer between applications. The command names are an interface metaphor based on the physical procedure used in manuscript print editing to create a page layout, like with paper. The commands were pioneered into computing by Xerox PARC in 1974, popularized by Apple Computer in the 1983 Lisa workstation and the 1984 Macintosh computer, and in a few home computer applications such as the 1984 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nicola Calipari
Nicola Calipari (June 23, 1953March 4, 2005) was an Italian major general and SISMI military intelligence officer. Calipari was accidentally killed in Iraq by American soldiers while escorting a recently released Italian hostage, journalist Giuliana Sgrena, to Baghdad International Airport. During the 1990s, Calipari was involved in several rescues of people kidnapped by 'Ndrangheta and other criminal organizations in Italy. He had spent most of his career in the Italian police, rising to a senior position, before joining the Italian military Security and Intelligence Service (SISMI) two years before his death. Calipari's death sparked one of the most serious diplomatic incidents between the U.S. and Italy since the end of World War II. Calipari is one of only five US or European general officers to be injured or killed during combat operations in Iraq and Afghanistan. Personal life Calipari was born in Reggio Calabria on June 23, 1953. He is survived by his wife and two ch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metadata Removal Tool
Metadata removal tool or metadata scrubber is a type of privacy software built to protect the privacy of its users by removing potentially privacy-compromising metadata from files before they are shared with others, e.g., by sending them as e-mail attachments or by posting them on the Web. Overview Metadata can be found in many types of files such as documents, spreadsheets, presentations, images, and audio files. They can include information such as details on the file authors, file creation and modification dates, geographical location, document revision history, thumbnail images, and comments. Metadata may be added to files by users, but some metadata is often automatically added to files by authoring applications or by devices used to produce the files, without user intervention. Since metadata is sometimes not clearly visible in authoring applications (depending on the application and its settings), there is a risk that the user will be unaware of its existence or will forg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Word
Microsoft Word is a word processor program, word processing program developed by Microsoft. It was first released on October 25, 1983, under the name Multi-Tool Word for Xenix systems. Subsequent versions were later written for several other platforms including IBM PCs running DOS (1983), Apple Macintosh running the Classic Mac OS (1985), AT&T UNIX PC (1985), Atari ST (1988), OS/2 (1989), Microsoft Windows (1989), SCO Unix (1990), Handheld PC (1996), Pocket PC (2000), macOS (2001), Web browsers (2010), iOS (2014), and Android (operating system), Android (2015). Microsoft Word has been the ''de facto'' standard word processing software since the 1990s when it eclipsed WordPerfect. Commercial versions of Word are licensed as a standalone product or as a component of Microsoft Office, which can be purchased with a perpetual license, as part of the Microsoft 365 suite as a Software as a service, subscription, or as a one-time purchase with Office 2024. History In 1981, Microsoft ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backup
In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere so that it may be used to restore the original after a data loss event. The verb form, referring to the process of doing so, is "wikt:back up, back up", whereas the noun and adjective form is "wikt:backup, backup". Backups can be used to data recovery, recover data after its loss from File deletion, data deletion or Data corruption, corruption, or to recover data from an earlier time. Backups provide a simple form of IT disaster recovery; however not all backup systems are able to reconstitute a computer system or other complex configuration such as a computer cluster, active directory server, or database server. A backup system contains at least one copy of all data considered worth saving. The computer data storage, data storage requirements can be large. An information repository model may be used to provide structure to this storage. There are different types of data stor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Undo
Undo is an interaction technique which is implemented in many computer programs. It erases the last change done to the document, reverting it to an older state. In some more advanced programs, such as graphic processing, undo will negate the last command done to the file being edited. With the possibility of undo, users can explore and work without fear of making mistakes, because they can easily be undone. The expectations for undo are easy to understand: to have a predictable functionality, and to include all "undoable" commands. Usually undo is available until the user undoes all executed operations. But there are some actions which are not stored in the undo list, and thus they cannot be undone. For example, ''save file'' is not undoable, but is queued in the list to show that it was executed. Another action which is usually not stored, and thus not undoable, is ''scrolling'' or ''selection''. The opposite of to undo is to redo. The redo command reverses the undo or advances ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Feature (software Design)
A feature is "a prominent or distinctive user-visible aspect, quality, or characteristic of a software system or systems", as defined by Kang et al. At the implementation level, "it is a structure that extends and modifies the structure of a given software in order to satisfy a stakeholder’s requirement, to implement and encapsulate a design decision, and to offer a configuration option", as defined by Apel et al. Context The term feature means the same for software as it does for any kind of system. For example, the British Royal Navy's HMS Dreadnought (1906) was considered an important milestone in naval technology because of its advanced features that did not exist in pre-dreadnought battleships. Feature also applies to computer hardware. In the early history of computers, devices such as Digital Equipment Corporation's PDP-7 minicomputer (created in 1964) was noted for having a wealth of features, such as being the first version of the PDP minicomputer series to use ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
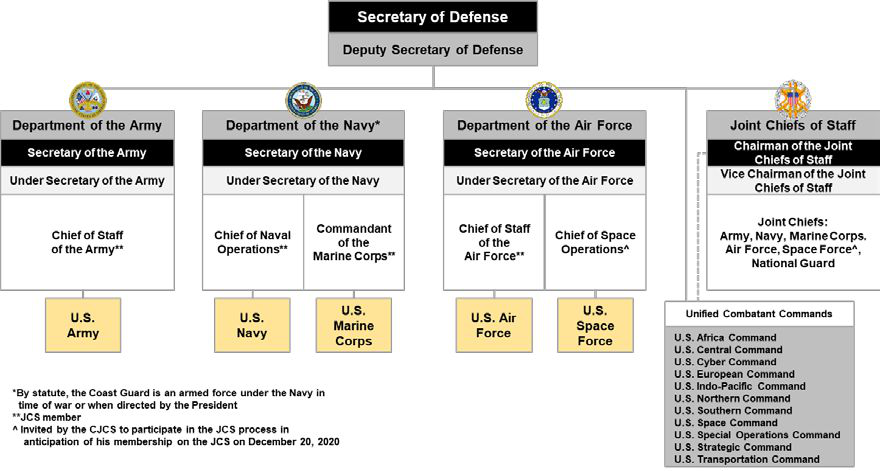
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random Access Memory
Random-access memory (RAM; ) is a form of electronic computer memory that can be read and changed in any order, typically used to store working data and machine code. A random-access memory device allows data items to be read or written in almost the same amount of time irrespective of the physical location of data inside the memory, in contrast with other direct-access data storage media (such as hard disks and magnetic tape), where the time required to read and write data items varies significantly depending on their physical locations on the recording medium, due to mechanical limitations such as media rotation speeds and arm movement. In today's technology, random-access memory takes the form of integrated circuit (IC) chips with MOS (metal–oxide–semiconductor) memory cells. RAM is normally associated with volatile types of memory where stored information is lost if power is removed. The two main types of volatile random-access semiconductor memory are static ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Storage
Disc or disk may refer to: * Disk (mathematics) In geometry, a disk (Spelling of disc, also spelled disc) is the region in a plane (geometry), plane bounded by a circle. A disk is said to be ''closed'' if it contains the circle that constitutes its boundary, and ''open'' if it does not. Fo ..., a two dimensional shape, the interior of a circle * Disk storage * Optical disc * Floppy disk Music * Disc (band), an American experimental music band * ''Disk'' (album), a 1995 EP by Moby Other uses * Disc harrow, a farm implement * Discus throw or disc throw, a track and field event involving a heavy disc * Intervertebral disc, a cartilage between vertebrae * Disk (functional analysis), a subset of a vector space * ''Disc'' (magazine), a British music magazine * Disk, a part of a flower * Disc number, numbers assigned to Inuit by the Government of Canada * Galactic disc, a disc-shaped group of stars Abbreviations * Death-inducing signaling complex * DISC assessmen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |