|
Renaissance Technologies
Renaissance Technologies LLC, also known as RenTech or RenTec, is an American hedge fund based in East Setauket, New York, on Long Island, which specializes in systematic trading using quantitative models derived from mathematical and statistical analysis. Their signature Medallion fund is famed for the best record in investing history. Renaissance was founded in 1982 by James Simons, a mathematician who formerly worked as a code breaker during the Cold War. In 1988, the firm established its most profitable portfolio, the Medallion Fund, which used an improved and expanded form of Leonard Baum's mathematical models, improved by algebraist James Ax, to explore correlations from which they could profit. Elwyn Berlekamp was instrumental in evolving trading to shorter-dated, pure systems driven decision-making. The hedge fund was named Medallion in honor of the math awards that Simons and Ax had won. Renaissance's flagship Medallion fund, which is run mostly for fund employees, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Private Company
A privately held company (or simply a private company) is a company whose shares and related rights or obligations are not offered for public subscription or publicly negotiated in the respective listed markets, but rather the company's stock is offered, owned, traded, exchanged privately, or Over-the-counter (finance), over-the-counter. In the case of a closed corporation, there are a relatively small number of shareholders or company members. Related terms are closely-held corporation, unquoted company, and unlisted company. Though less visible than their public company, publicly traded counterparts, private companies have major importance in the world's economy. In 2008, the 441 list of largest private non-governmental companies by revenue, largest private companies in the United States accounted for ($1.8 trillion) in revenues and employed 6.2 million people, according to ''Forbes''. In 2005, using a substantially smaller pool size (22.7%) for comparison, the 339 companies on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Baum–Welch Algorithm
In electrical engineering, statistical computing and bioinformatics, the Baum–Welch algorithm is a special case of the expectation–maximization algorithm used to find the unknown parameters of a hidden Markov model (HMM). It makes use of the forward-backward algorithm to compute the statistics for the expectation step. History The Baum–Welch algorithm was named after its inventors Leonard E. Baum and Lloyd R. Welch. The algorithm and the Hidden Markov models were first described in a series of articles by Baum and his peers at the IDA Center for Communications Research, Princeton in the late 1960s and early 1970s. One of the first major applications of HMMs was to the field of speech processing. In the 1980s, HMMs were emerging as a useful tool in the analysis of biological systems and information, and in particular genetic information. They have since become an important tool in the probabilistic modeling of genomic sequences. Description A hidden Markov model describes th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security (finance)
A security is a tradable financial asset. The term commonly refers to any form of financial instrument, but its legal definition varies by jurisdiction. In some countries and languages people commonly use the term "security" to refer to any form of financial instrument, even though the underlying legal and regulatory regime may not have such a broad definition. In some jurisdictions the term specifically excludes financial instruments other than equities and Fixed income instruments. In some jurisdictions it includes some instruments that are close to equities and fixed income, e.g., equity warrants. Securities may be represented by a certificate or, more typically, they may be "non-certificated", that is in electronic ( dematerialized) or "book entry only" form. Certificates may be ''bearer'', meaning they entitle the holder to rights under the security merely by holding the security, or ''registered'', meaning they entitle the holder to rights only if they appear on a secur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
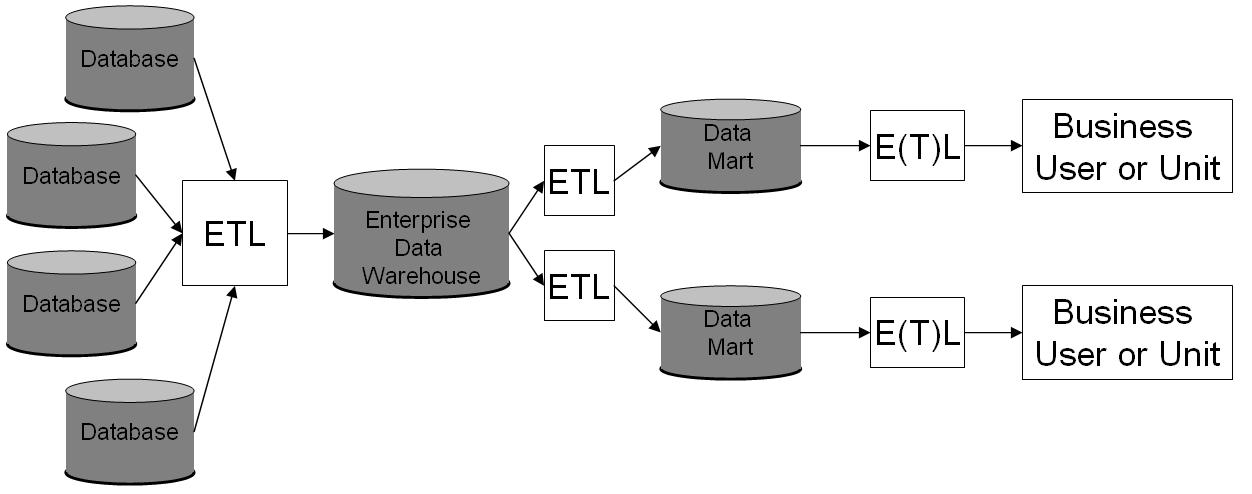
Data Warehouse
In computing, a data warehouse (DW or DWH), also known as an enterprise data warehouse (EDW), is a system used for Business reporting, reporting and data analysis and is considered a core component of business intelligence. DWs are central Repository (version control), repositories of integrated data from one or more disparate sources. They store current and historical data in one single place that are used for creating analytical reports for workers throughout the enterprise. The data stored in the warehouse is uploaded from the operational systems (such as marketing or sales). The data may pass through an operational data store and may require data cleansing for additional operations to ensure data quality before it is used in the DW for reporting. Extract, transform, load (ETL) and extract, load, transform (ELT) are the two main approaches used to build a data warehouse system. ETL-based data warehousing The typical extract, transform, load (ETL)-based data warehouse uses ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Petabyte
The byte is a unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character of text in a computer and for this reason it is the smallest addressable unit of memory in many computer architectures. To disambiguate arbitrarily sized bytes from the common 8-bit definition, network protocol documents such as The Internet Protocol () refer to an 8-bit byte as an octet. Those bits in an octet are usually counted with numbering from 0 to 7 or 7 to 0 depending on the bit endianness. The first bit is number 0, making the eighth bit number 7. The size of the byte has historically been hardware-dependent and no definitive standards existed that mandated the size. Sizes from 1 to 48 bits have been used. The six-bit character code was an often-used implementation in early encoding systems, and computers using six-bit and nine-bit bytes were common in the 1960s. These systems often had memory words o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantitative Investing
Quantitative analysis is the use of mathematical and statistical methods in finance and investment management. Those working in the field are quantitative analysts (quants). Quants tend to specialize in specific areas which may include derivative structuring or pricing, risk management, investment management and other related finance occupations. The occupation is similar to those in industrial mathematics in other industries. The process usually consists of searching vast databases for patterns, such as correlations among liquid assets or price-movement patterns (trend following or mean reversion). Although the original quantitative analysts were "sell side quants" from market maker firms, concerned with derivatives pricing and risk management, the meaning of the term has expanded over time to include those individuals involved in almost any application of mathematical finance, including the buy side. Applied quantitative analysis is commonly associated with quantitative investm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chern–Simons Theory
The Chern–Simons theory is a 3-dimensional topological quantum field theory of Schwarz type developed by Edward Witten. It was discovered first by mathematical physicist Albert Schwarz. It is named after mathematicians Shiing-Shen Chern and James Harris Simons, who introduced the Chern–Simons 3-form. In the Chern–Simons theory, the action is proportional to the integral of the Chern–Simons 3-form. In condensed-matter physics, Chern–Simons theory describes the topological order in fractional quantum Hall effect states. In mathematics, it has been used to calculate knot invariants and three-manifold invariants such as the Jones polynomial. Particularly, Chern–Simons theory is specified by a choice of simple Lie group G known as the gauge group of the theory and also a number referred to as the ''level'' of the theory, which is a constant that multiplies the action. The action is gauge dependent, however the partition function of the quantum theory is well-defined wh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Oswald Veblen Prize In Geometry
__NOTOC__ The Oswald Veblen Prize in Geometry is an award granted by the American Mathematical Society for notable research in geometry or topology. It was founded in 1961 in memory of Oswald Veblen. The Veblen Prize is now worth US$5000, and is awarded every three years. The first seven prize winners were awarded for works in topology. James Harris Simons and William Thurston were the first ones to receive it for works in geometry (for some distinctions, see geometry and topology). As of 2020, there have been thirty-four prize recipients. List of recipients * 1964 Christos Papakyriakopoulos * 1964 Raoul Bott * 1966 Stephen Smale * 1966 Morton Brown and Barry Mazur * 1971 Robion Kirby * 1971 Dennis Sullivan * 1976 William Thurston * 1976 James Harris Simons * 1981 Mikhail Gromov for: ::''Manifolds of negative curvature.'' Journal of Differential Geometry 13 (1978), no. 2, 223–230. ::''Almost flat manifolds.'' Journal of Differential Geometry 13 (1978), no. 2, 231–241. ::'' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
State University Of New York At Stony Brook
Stony Brook University (SBU), officially the State University of New York at Stony Brook, is a public research university in Stony Brook, New York. Along with the University at Buffalo, it is one of the State University of New York system's two flagship institutions. Its campus consists of 213 buildings on over of land in Suffolk County and it is the largest public university (by area) in the state of New York. Opened in 1957 in Oyster Bay as the State University College on Long Island, the institution moved to Stony Brook in 1962. In 2001, Stony Brook was elected to the Association of American Universities, a selective group of major research universities in North America. It is also a member of the larger Universities Research Association. It is classified among "R1: Doctoral Universities – Very high research activity". Stony Brook University, in partnership with Battelle, manages Brookhaven National Laboratory, a national laboratory of the United States Departm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IBM Research
IBM Research is the research and development division for IBM, an American multinational information technology company headquartered in Armonk, New York, with operations in over 170 countries. IBM Research is the largest industrial research organization in the world and has twelve labs on six continents. IBM employees have garnered six Nobel Prizes, six Turing Awards, 20 inductees into the U.S. National Inventors Hall of Fame, 19 National Medals of Technology, five National Medals of Science and three Kavli Prizes. , the company has generated more patents than any other business in each of 25 consecutive years, which is a record. History The roots of today's IBM Research began with the 1945 opening of the Watson Scientific Computing Laboratory at Columbia University. This was the first IBM laboratory devoted to pure science and later expanded into additional IBM Research locations in Westchester County, New York, starting in the 1950s,Beatty, Jack, (editor''Colussus: how ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computational Linguistics
Computational linguistics is an Interdisciplinarity, interdisciplinary field concerned with the computational modelling of natural language, as well as the study of appropriate computational approaches to linguistic questions. In general, computational linguistics draws upon linguistics, computer science, artificial intelligence, mathematics, logic, philosophy, cognitive science, cognitive psychology, psycholinguistics, anthropology and neuroscience, among others. Sub-fields and related areas Traditionally, computational linguistics emerged as an area of artificial intelligence performed by computer scientists who had specialized in the application of computers to the processing of a natural language. With the formation of the Association for Computational Linguistics (ACL) and the establishment of independent conference series, the field consolidated during the 1970s and 1980s. The Association for Computational Linguistics defines computational linguistics as: The term "comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Science
Computer science is the study of computation, automation, and information. Computer science spans theoretical disciplines (such as algorithms, theory of computation, information theory, and automation) to Applied science, practical disciplines (including the design and implementation of Computer architecture, hardware and Computer programming, software). Computer science is generally considered an area of research, academic research and distinct from computer programming. Algorithms and data structures are central to computer science. The theory of computation concerns abstract models of computation and general classes of computational problem, problems that can be solved using them. The fields of cryptography and computer security involve studying the means for secure communication and for preventing Vulnerability (computing), security vulnerabilities. Computer graphics (computer science), Computer graphics and computational geometry address the generation of images. Progr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)