|
Quantum Byzantine Agreement
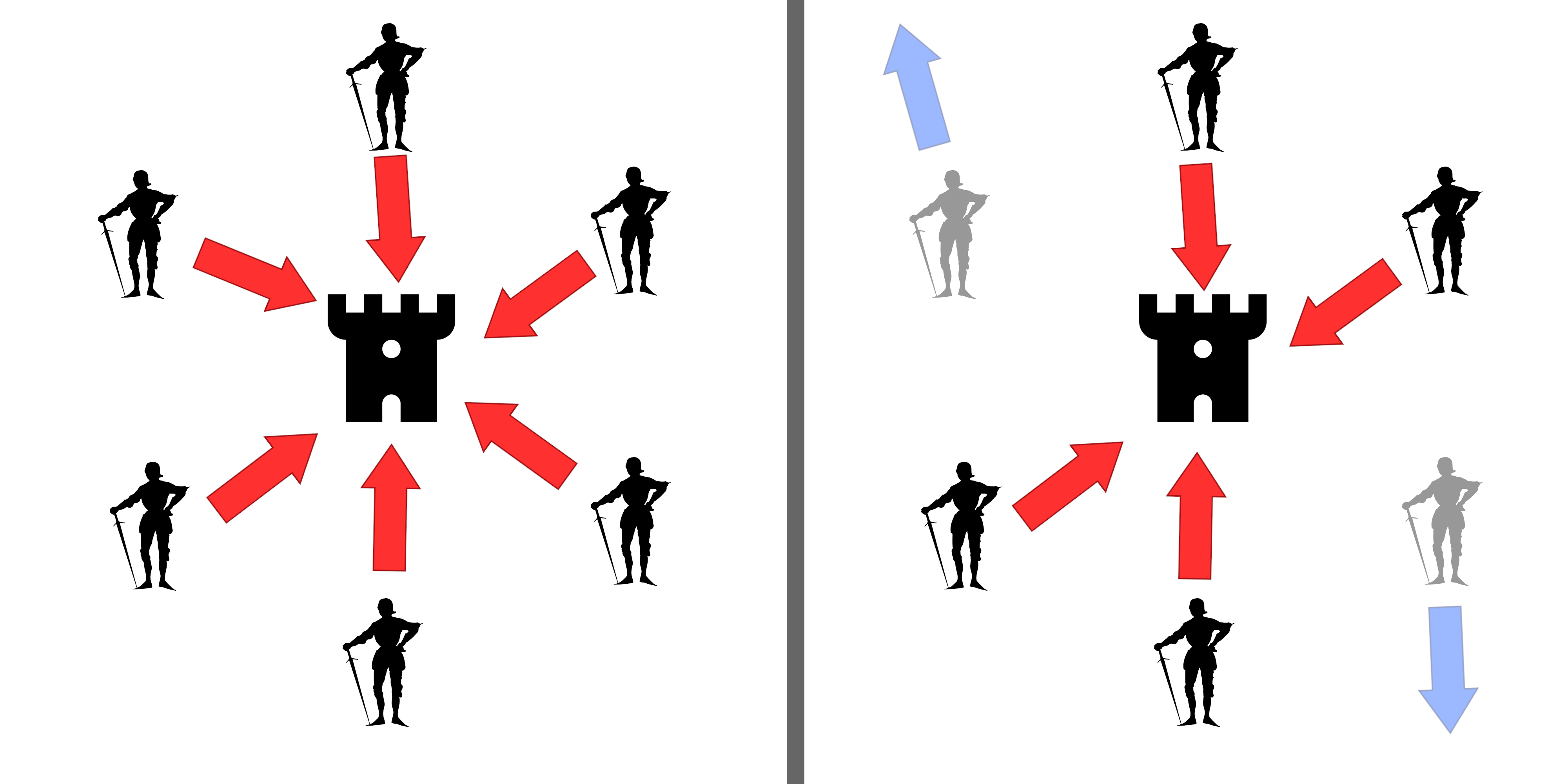
Byzantine fault tolerant protocols are algorithms that are robust to arbitrary types of failures in distributed algorithms. The Byzantine agreement protocol is an essential part of this task. The constant-time quantum version of the Byzantine protocol, is described below. Introduction The Byzantine Agreement protocol is a protocol in distributed computing. It takes its name from a problem formulated by Lamport, Shostak and Pease in 1982, which itself is a reference to a historical problem. The Byzantine army was divided into divisions with each division being led by a General with the following properties: *Each General is either loyal or a traitor to the Byzantine state. *All Generals communicate by sending and receiving messages. *There are only two commands: attack and retreat. *All loyal Generals should agree on the same plan of action: attack or retreat. *A small linear fraction of bad Generals should not cause the protocol to fail (less than a \tfrac fraction). (See for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Byzantine Fault Tolerance
A Byzantine fault is a condition of a system, particularly a distributed computing system, where a fault occurs such that different symptoms are presented to different observers, including imperfect information on whether a system component has failed. The term takes its name from an allegory, the "Byzantine generals problem", developed to describe a situation in which, to avoid catastrophic failure of a system, the system's actors must agree on a strategy, but some of these actors are unreliable in such a way as to cause other (good) actors to disagree on the strategy and they may be unaware of the disagreement. A Byzantine fault is also known as a Byzantine generals problem, a Byzantine agreement problem, or a Byzantine failure. Byzantine fault tolerance (BFT) is the resilience of a fault-tolerant computer system or similar system to such conditions. Definition A Byzantine fault is any fault presenting different symptoms to different observers. A Byzantine failure is the los ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Qubits
In quantum computing, a qubit () or quantum bit is a basic unit of quantum information—the quantum version of the classic binary bit physically realized with a two-state device. A qubit is a two-state (or two-level) quantum-mechanical system, one of the simplest quantum systems displaying the peculiarity of quantum mechanics. Examples include the spin of the electron in which the two levels can be taken as spin up and spin down; or the polarization of a single photon in which the two spin states (left-handed and the right-handed circular polarization) can also be measured as horizontal and vertical linear polarization. In a classical system, a bit would have to be in one state or the other. However, quantum mechanics allows the qubit to be in a coherent superposition of multiple states simultaneously, a property that is fundamental to quantum mechanics and quantum computing. Etymology The coining of the term ''qubit'' is attributed to Benjamin Schumacher. In the acknowledgmen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fault Tolerance
Fault tolerance is the ability of a system to maintain proper operation despite failures or faults in one or more of its components. This capability is essential for high-availability, mission-critical, or even life-critical systems. Fault tolerance specifically refers to a system's capability to handle faults without any degradation or downtime. In the event of an error, end-users remain unaware of any issues. Conversely, a system that experiences errors with some interruption in service or graceful degradation of performance is termed 'resilient'. In resilience, the system adapts to the error, maintaining service but acknowledging a certain impact on performance. Typically, fault tolerance describes computer systems, ensuring the overall system remains functional despite hardware or software issues. Non-computing examples include structures that retain their integrity despite damage from fatigue, corrosion or impact. History The first known fault-tolerant computer was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed Computing Problems
Distribution may refer to: Mathematics *Distribution (mathematics), generalized functions used to formulate solutions of partial differential equations *Probability distribution, the probability of a particular value or value range of a variable **Cumulative distribution function, in which the probability of being no greater than a particular value is a function of that value *Frequency distribution, a list of the values recorded in a sample * Inner distribution, and outer distribution, in coding theory *Distribution (differential geometry), a subset of the tangent bundle of a manifold * Distributed parameter system, systems that have an infinite-dimensional state-space * Distribution of terms, a situation in which all members of a category are accounted for *Distributivity, a property of binary operations that generalises the distributive law from elementary algebra *Distribution (number theory) *Distribution problems, a common type of problems in combinatorics where the goa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Information Science
Quantum information science is a field that combines the principles of quantum mechanics with information theory to study the processing, analysis, and transmission of information. It covers both theoretical and experimental aspects of quantum physics, including the limits of what can be achieved with quantum information. The term quantum information theory is sometimes used, but it does not include experimental research and can be confused with a subfield of quantum information science that deals with the processing of quantum information. Scientific and engineering studies Quantum teleportation, Quantum entanglement, entanglement and the manufacturing of quantum computers depend on a comprehensive understanding of quantum physics and engineering. Google and IBM have invested significantly in quantum computer hardware research, leading to significant progress in manufacturing quantum computers since the 2010s. Currently, it is possible to create a quantum computer with over 100 qub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Broadcasting (computing)
In computer networking, telecommunication and information theory, broadcasting is a method of transferring a message to all recipients simultaneously. Broadcasting can be performed as a high-level operation in a program, for example, broadcasting in Message Passing Interface, or it may be a low-level networking operation, for example broadcasting on Ethernet. All-to-all communication is a computer communication method in which each sender Message passing, transmits messages to all receivers within a group. In networking this can be accomplished using broadcast or multicast. This is in contrast with the Point-to-point (telecommunications), point-to-point method in which each sender communicates with one receiver. Addressing methods There are four principal addressing methods in the Internet Protocol: Overview In computer networking, broadcasting refers to transmitting a packet (information technology), packet that will be received by every device on the network. In practice, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Broadcast
Broadcasting is the data distribution, distribution of sound, audio audiovisual content to dispersed audiences via a electronic medium (communication), mass communications medium, typically one using the electromagnetic spectrum (radio waves), in a :wikt:one-to-many, one-to-many model. Broadcasting began with AM radio, which came into popular use around 1920 with the spread of vacuum tube radio transmitters and radio receiver, receivers. Before this, most implementations of electronic communication (early radio, telephone, and telegraph) were wikt:one-to-one, one-to-one, with the message intended for a single recipient. The term ''broadcasting'' evolved from its use as the agricultural method of sowing seeds in a field by casting them broadly about. It was later adopted for describing the widespread distribution of information by printed materials or by telegraph. Examples applying it to "one-to-many" radio transmissions of an individual station to multiple listeners appeared as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Qubit
In quantum computing, a qubit () or quantum bit is a basic unit of quantum information—the quantum version of the classic binary bit physically realized with a two-state device. A qubit is a two-state (or two-level) quantum-mechanical system, one of the simplest quantum systems displaying the peculiarity of quantum mechanics. Examples include the spin of the electron in which the two levels can be taken as spin up and spin down; or the polarization of a single photon in which the two spin states (left-handed and the right-handed circular polarization) can also be measured as horizontal and vertical linear polarization. In a classical system, a bit would have to be in one state or the other. However, quantum mechanics allows the qubit to be in a coherent superposition of multiple states simultaneously, a property that is fundamental to quantum mechanics and quantum computing. Etymology The coining of the term ''qubit'' is attributed to Benjamin Schumacher. In the acknow ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
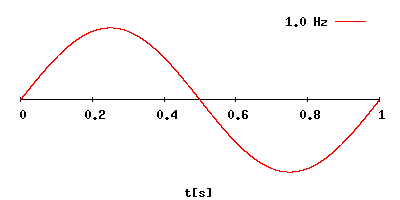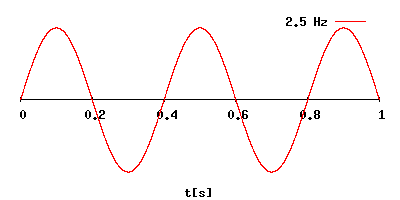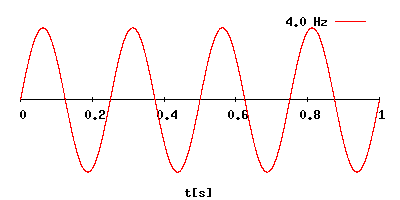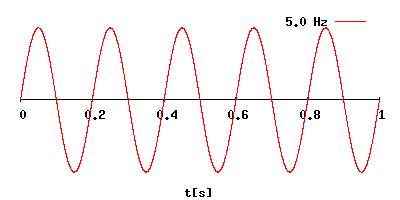
GHZ State
The hertz (symbol: Hz) is the unit of frequency in the International System of Units (SI), often described as being equivalent to one event (or cycle) per second. The hertz is an SI derived unit whose formal expression in terms of SI base units is 1/s or s−1, meaning that one hertz is one per second or the reciprocal of one second. It is used only in the case of periodic events. It is named after Heinrich Rudolf Hertz (1857–1894), the first person to provide conclusive proof of the existence of electromagnetic waves. For high frequencies, the unit is commonly expressed in multiples: kilohertz (kHz), megahertz (MHz), gigahertz (GHz), terahertz (THz). Some of the unit's most common uses are in the description of periodic waveforms and musical tones, particularly those used in radio- and audio-related applications. It is also used to describe the clock speeds at which computers and other electronics are driven. The units are sometimes also used as a representation of the e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protocol (computing)
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any variation of a physical quantity. The protocol defines the rules, syntax, semantics, and synchronization of communication and possible error recovery methods. Protocols may be implemented by hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses predetermined for that particular situation. The specified behavior is typically independent of how it is to be implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, so there is a close analogy between protocols and programming languages: ''protocols are to communica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
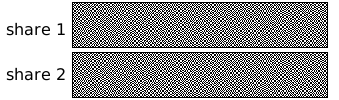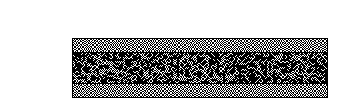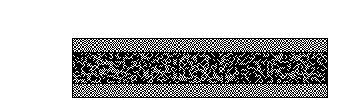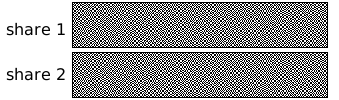
Secret Sharing
Secret sharing (also called secret splitting) refers to methods for distributing a secrecy, secret among a group, in such a way that no individual holds any intelligible information about the secret, but when a sufficient number of individuals combine their 'shares', the secret may be reconstructed. Whereas ''insecure'' secret sharing allows an attacker to gain more information with each share, ''secure'' secret sharing is 'all or nothing' (where 'all' means the necessary number of shares). In one type of secret sharing scheme there is one ''dealer'' and ''n'' ''players''. The dealer gives a share of the secret to the players, but only when specific conditions are fulfilled will the players be able to reconstruct the secret from their shares. The dealer accomplishes this by giving each player a share in such a way that any group of ''t'' (for ''threshold'') or more players can together reconstruct the secret but no group of fewer than ''t'' players can. Such a system is called a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |