|
Proof Of Personhood
Proof of personhood (PoP) is a means of resisting malicious attacks on peer to peer networks, particularly, attacks that utilize multiple fake identities, otherwise known as a Sybil attack. Decentralized online platforms are particularly vulnerable to such attacks by their very nature, as notionally democratic and responsive to large voting blocks. In PoP, each unique human participant obtains one equal unit of voting power, and any associated rewards. The term is used in for cryptocurrency and blockchains as a parallel to proof of work, proof of stake, and other consensus mechanisms which attempt to distribute voting power and rewards to participants proportionately to an investment of resources. Background The problem of Sybil attacks using many virtual identities has been recognized for decades as a fundamental challenge for distributed systems that expect each human user to have only one account or identity. CAPTCHAs attempt to rate-limit automated Sybil attacks by using ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sybil Attack
A Sybil attack is a type of attack on a computer network service in which an attacker subverts the service's reputation system by creating a large number of pseudonymous identities and uses them to gain a disproportionately large influence. It is named after the subject of the book '' Sybil'', a case study of a woman diagnosed with dissociative identity disorder. The name was suggested in or before 2002 by Brian Zill at Microsoft Research. The term pseudospoofing had previously been coined by L. Detweiler on the Cypherpunks mailing list and used in the literature on peer-to-peer systems for the same class of attacks prior to 2002, but this term did not gain as much influence as "Sybil attack". Description The Sybil attack in computer security is an attack wherein a reputation system is subverted by creating multiple identities. A reputation system's vulnerability to a Sybil attack depends on how cheaply identities can be generated, the degree to which the reputation system accept ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymity
Anonymity describes situations where the acting person's identity is unknown. Anonymity may be created unintentionally through the loss of identifying information due to the passage of time or a destructive event, or intentionally if a person chooses to withhold their identity. There are various situations in which a person might choose to remain anonymous. Acts of charity have been performed anonymously when benefactors do not wish to be acknowledged. A person who feels threatened might attempt to mitigate that threat through anonymity. A witness to a crime might seek to avoid retribution, for example, by anonymously calling a crime tipline. In many other situations (like conversation between strangers, or buying some product or service in a shop), anonymity is traditionally accepted as natural. Some writers have argued that the term "namelessness", though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proof Of Space
Proof of space (PoS) is a type of consensus algorithm achieved by demonstrating one's legitimate interest in a service (such as sending an email) by allocating a non-trivial amount of Computer memory, memory or disk space to solve a challenge presented by the service provider. The concept was formulated in 2013 by Dziembowski ''et al.'' and (with a different formulation) by Ateniese ''et al.''. Proofs of space are very similar to proof-of-work system, proofs of work (PoW), except that instead of computation, storage is used to earn cryptocurrency. Proof-of-space is different from memory-hard functions in that the Bottleneck (software), bottleneck is not in the number of memory access events, but in the amount of memory required. After the release of Bitcoin, alternatives to its PoW Cryptocurrency mining, mining mechanism were researched, and PoS was studied in the context of cryptocurrencies. Proofs of space are seen as fairer and Green computing, greener alternatives by blockch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proof Of Authority
Proof of authority (PoA) is an algorithm used with blockchains that delivers comparatively fast transactions through a consensus mechanism based on identity as a stake. The most notable platforms using PoA are VeChain, Bitgert, Palm Network and Xodex. Proof-of-authority In PoA-based networks, transactions and blocks are validated by approved accounts, known as validators. Validators run software allowing them to put transactions in blocks. The process is automated and does not require validators to be constantly monitoring their computers. It, however, does require maintaining the computer (the authority node) uncompromised. The term was coined by Gavin Wood, co-founder of Ethereum Ethereum is a decentralized blockchain with smart contract functionality. Ether (abbreviation: ETH) is the native cryptocurrency of the platform. Among cryptocurrencies, ether is second only to bitcoin in market capitalization. It is open-s ... and Parity Technologies. With PoA, individuals ea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Democracy
Democracy (from , ''dēmos'' 'people' and ''kratos'' 'rule') is a form of government in which political power is vested in the people or the population of a state. Under a minimalist definition of democracy, rulers are elected through competitive Election, elections while more expansive or maximalist definitions link democracy to guarantees of civil liberties and human rights in addition to competitive elections. In a direct democracy, the people have the direct authority to Deliberation, deliberate and decide legislation. In a representative democracy, the people choose governing officials through elections to do so. The definition of "the people" and the ways authority is shared among them or delegated by them have changed over time and at varying rates in different countries. Features of democracy oftentimes include freedom of assembly, freedom of association, association, personal property, freedom of religion and freedom of speech, speech, citizenship, consent of the governe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deepfake
''Deepfakes'' (a portmanteau of and ) are images, videos, or audio that have been edited or generated using artificial intelligence, AI-based tools or AV editing software. They may depict real or fictional people and are considered a form of synthetic media, that is media that is usually created by artificial intelligence systems by combining various media elements into a new media artifact. While the act of creating fake content is not new, deepfakes uniquely leverage machine learning and artificial intelligence techniques, including facial recognition algorithms and artificial neural networks such as variational autoencoders (VAEs) and generative adversarial networks (GANs). In turn, the field of image forensics develops techniques to detect manipulated images. Deepfakes have garnered widespread attention for their potential use in creating child sexual abuse material, celebrity pornographic videos, revenge porn, fake news, hoaxes, bullying, and financial fraud. Acade ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Artificial Intelligence
Artificial intelligence (AI) is the capability of computer, computational systems to perform tasks typically associated with human intelligence, such as learning, reasoning, problem-solving, perception, and decision-making. It is a field of research in computer science that develops and studies methods and software that enable machines to machine perception, perceive their environment and use machine learning, learning and intelligence to take actions that maximize their chances of achieving defined goals. High-profile applications of AI include advanced web search engines (e.g., Google Search); recommendation systems (used by YouTube, Amazon (company), Amazon, and Netflix); virtual assistants (e.g., Google Assistant, Siri, and Amazon Alexa, Alexa); autonomous vehicles (e.g., Waymo); Generative artificial intelligence, generative and Computational creativity, creative tools (e.g., ChatGPT and AI art); and Superintelligence, superhuman play and analysis in strategy games (e.g., ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zero-knowledge Proof
In cryptography, a zero-knowledge proof (also known as a ZK proof or ZKP) is a protocol in which one party (the prover) can convince another party (the verifier) that some given statement is true, without conveying to the verifier any information ''beyond'' the mere fact of that statement's truth. The intuition underlying zero-knowledge proofs is that it is trivial to prove possession of the relevant information simply by revealing it; the hard part is to prove this possession without revealing this information (or any aspect of it whatsoever). In light of the fact that one should be able to generate a proof of some statement ''only'' when in possession of certain secret information connected to the statement, the verifier, even after having become convinced of the statement's truth, should nonetheless remain unable to prove the statement to further third parties. Zero-knowledge proofs can be interactive, meaning that the prover and verifier exchange messages according to some pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Homomorphic Encryption
Homomorphic encryption is a form of encryption that allows computations to be performed on encrypted data without first having to decrypt it. The resulting computations are left in an encrypted form which, when decrypted, result in an output that is identical to that of the operations performed on the unencrypted data. While homomorphic encryption does not protect against side-channel attacks that observe behavior, it can be used for privacy-preserving outsourced storage and computation. This allows data to be encrypted and outsourced to commercial cloud environments for processing, all while encrypted. As an example of a practical application of homomorphic encryption: encrypted photographs can be scanned for points of interest, without revealing the contents of a photo. However, observation of side-channels can see a photograph being sent to a point-of-interest lookup service, revealing the fact that photographs were taken. Thus, homomorphic encryption eliminates the need ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
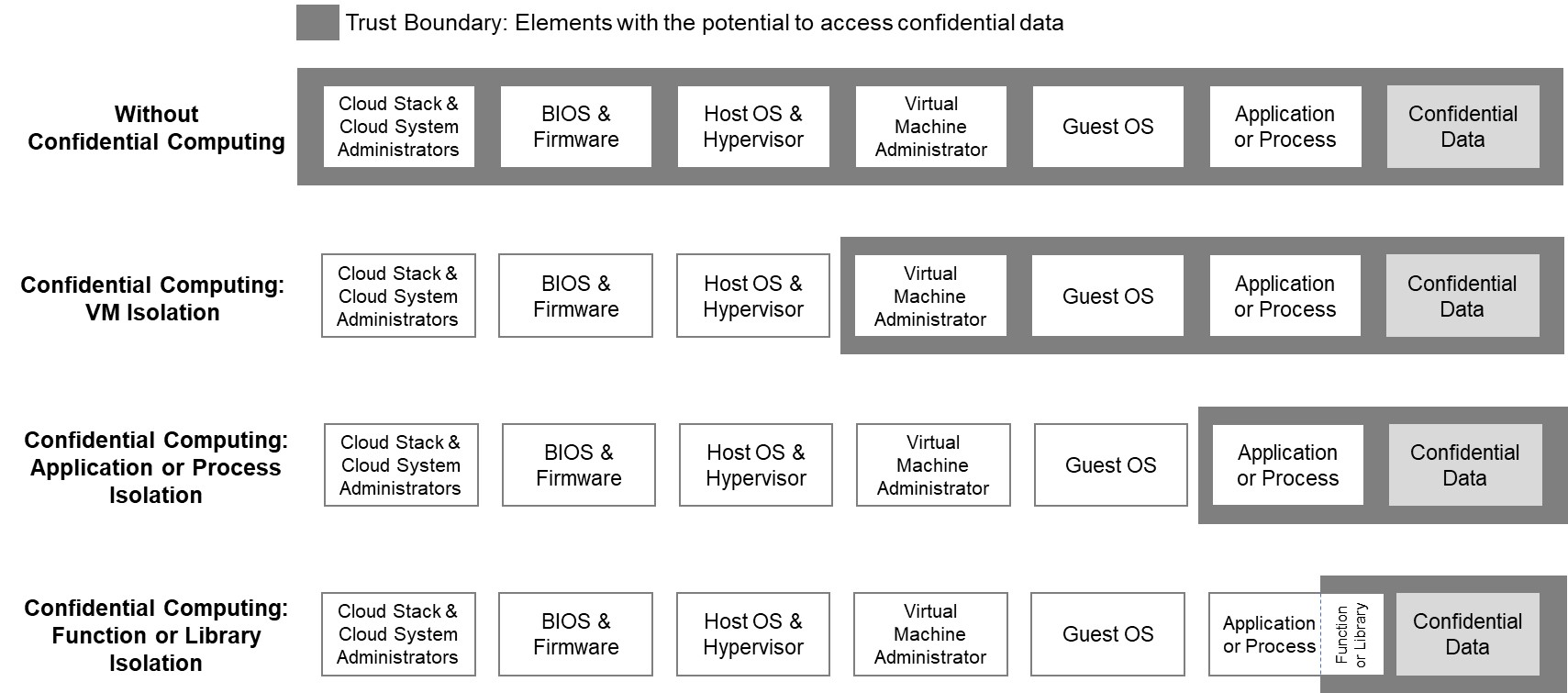
Confidential Computing
Confidential computing is a security and Privacy-enhancing technologies, privacy-enhancing computational technique focused on protecting data in use. Confidential computing can be used in conjunction with storage and network encryption, which protect data at rest and data in transit respectively. It is designed to address software, protocol, cryptographic, and basic physical and supply-chain attacks, although some critics have demonstrated architectural and side-channel attacks effective against the technology. The technology protects data in use by performing computations in a hardware-based trusted execution environment (TEE). Confidential data is released to the TEE only once it is assessed to be trustworthy. Different types of confidential computing define the level of data isolation used, whether virtual machine, application software, application, or function (computer programming), function, and the technology can be deployed in on-premise data centers, edge locations, or the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Social Exclusion
Social exclusion or social marginalisation is the social disadvantage and relegation to the fringe of society. It is a term that has been used widely in Europe and was first used in France in the late 20th century. In the EU context, the European Commission defines it as ''"a situation whereby a person is prevented (or excluded) from contributing to and benefiting from economic and social progress"''. It is used across disciplines including education, sociology, psychology, healthcare, politics and economics. Social exclusion is the process in which individuals are blocked from (or denied full access to) various rights, opportunities and resources that are normally available to members of a different group, and which are fundamental to social integration and observance of human rights within that particular group (e.g. due process). Alienation or disenfranchisement resulting from social exclusion can be connected to a person's social class, race, skin color, religious aff ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |