|
Meltdown (security Vulnerability)
Meltdown is one of the two original speculative execution CPU vulnerabilities (the other being Spectre). Meltdown affects Intel x86 microprocessors, IBM Power microprocessors, and some ARM-based microprocessors. It allows a rogue process to read all memory, even when it is not authorized to do so. Meltdown affects a wide range of systems. At the time of disclosure (2018), this included all devices running any but the most recent and patched versions of iOS, Linux, macOS, or Windows. Accordingly, many servers and cloud services were impacted, as well as a potential majority of smart devices and embedded devices using ARM-based processors (mobile devices, smart TVs, printers and others), including a wide range of networking equipment. A purely software workaround to Meltdown has been assessed as slowing computers between 5 and 30 percent in certain specialized workloads, although companies responsible for software correction of the exploit reported minimal impact from g ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intel X86
x86 (also known as 80x86 or the 8086 family) is a family of complex instruction set computer (CISC) instruction set architectures initially developed by Intel, based on the 8086 microprocessor and its 8-bit-external-bus variant, the 8088. The 8086 was introduced in 1978 as a fully 16-bit extension of 8-bit Intel's 8080 microprocessor, with memory segmentation as a solution for addressing more memory than can be covered by a plain 16-bit address. The term "x86" came into being because the names of several successors to Intel's 8086 processor end in "86", including the 80186, 80286, 80386 and 80486. Colloquially, their names were "186", "286", "386" and "486". The term is not synonymous with IBM PC compatibility, as this implies a multitude of other computer hardware. Embedded systems and general-purpose computers used x86 chips before the PC-compatible market started, some of them before the IBM PC (1981) debut. , most desktop and laptop computers sold are based on the x ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Embedded Device
An embedded system is a specialized computer system—a combination of a computer processor, computer memory, and input/output peripheral devices—that has a dedicated function within a larger mechanical or Electronics, electronic system. It is embedded as part of a complete device often including electrical or electronic hardware and mechanical parts. Because an embedded system typically controls physical operations of the machine that it is embedded within, it often has real-time computing constraints. Embedded systems control many devices in common use. , it was estimated that ninety-eight percent of all microprocessors manufactured were used in embedded systems. Modern embedded systems are often based on microcontrollers (i.e. microprocessors with integrated memory and peripheral interfaces), but ordinary microprocessors (using external chips for memory and peripheral interface circuits) are also common, especially in more complex systems. In either case, the proc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
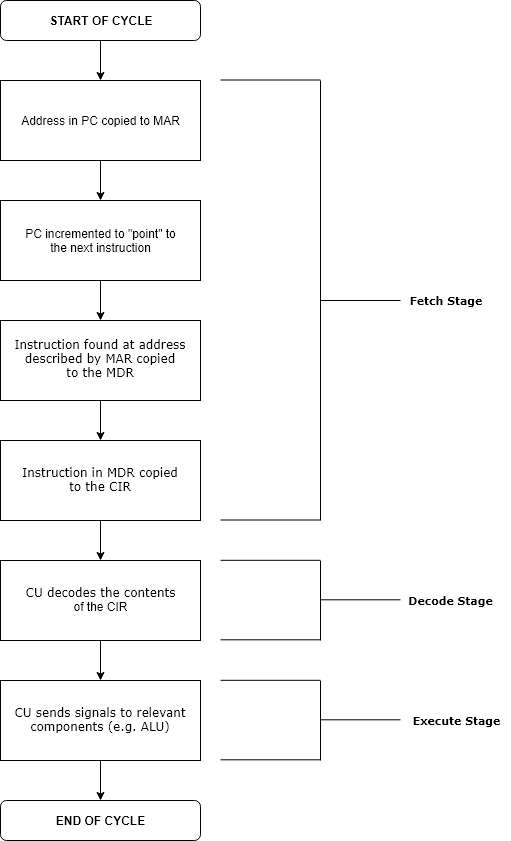
Instruction Cycle
The instruction cycle (also known as the fetch–decode–execute cycle, or simply the fetch–execute cycle) is the cycle that the central processing unit (CPU) follows from boot-up until the computer has shut down in order to process instructions. It is composed of three main stages: the fetch stage, the decode stage, and the execute stage. In simpler CPUs, the instruction cycle is executed sequentially, each instruction being processed before the next one is started. In most modern CPUs, the instruction cycles are instead executed concurrently, and often in parallel, through an instruction pipeline: the next instruction starts being processed before the previous instruction has finished, which is possible because the cycle is broken up into separate steps. Role of components Program counter The program counter (PC) is a register that holds the memory address of the next instruction to be executed. After each instruction copy to the memory address register (MAR), the PC can ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Race Condition
A race condition or race hazard is the condition of an electronics, software, or other system where the system's substantive behavior is dependent on the sequence or timing of other uncontrollable events, leading to unexpected or inconsistent results. It becomes a bug when one or more of the possible behaviors is undesirable. The term ''race condition'' was already in use by 1954, for example in David A. Huffman's doctoral thesis "The synthesis of sequential switching circuits". Race conditions can occur especially in logic circuits or multithreaded or distributed software programs. Using mutual exclusion can prevent race conditions in distributed software systems. In electronics A typical example of a race condition may occur when a logic gate combines signals that have traveled along different paths from the same source. The inputs to the gate can change at slightly different times in response to a change in the source signal. The output may, for a brief period, chan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TechCrunch
TechCrunch is an American global online newspaper focusing on topics regarding high tech, high-tech and Startup company, startup companies. It was founded in June 2005 by Archimedes Ventures, led by partners Michael Arrington and Keith Teare. In 2010, AOL acquired the company for approximately $25 million. Following the 2015 Verizon Communications#Acquisition of AOL and Yahoo, acquisition of AOL and Yahoo! by Verizon, the site was owned by Verizon Media from 2015 through 2021. In 2021, Verizon sold its media assets, including AOL, Yahoo!, and TechCrunch, to the private equity firm Apollo Global Management. Apollo integrated them into a new entity called Yahoo! Inc. (2017–present), Yahoo! Inc. In addition to its news reporting, TechCrunch is also known for its annual Disrupt conference, a technology event hosted in several cities across the United States, Europe, and China. History TechCrunch was founded in June 2005 by Archimedes Ventures, led by partners Michael Arrington a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AnandTech
''AnandTech'' was an online computer hardware magazine owned by Future plc. It was founded in April 1997 by then-14-year-old Anand Lal Shimpi, who was CEO and editor-in-chief until August 2014, with Ryan Smith replacing him as editor-in-chief. The website was a source of hardware reviews for off-the-shelf components and exhaustive benchmarking, targeted towards computer-building enthusiasts, but later expanded to cover mobile devices such as smartphones and tablets. Some of their articles on mass-market products such as mobile phones were syndicated by CNNMoney. The large accompanying forum is recommended by some books for bargain hunting in the technology field. AnandTech was acquired by Purch on 17 December 2014. Purch was acquired by Future in 2018. On August 30, 2024, the publication shut down. The content of the website was said to be preserved, but no new articles or reviews would be published. The AnandTech forums would continue to operate. History In its early s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Verge
''The Verge'' is an American Technology journalism, technology news website headquarters, headquartered in Lower Manhattan, New York City and operated by Vox Media. The website publishes news, feature stories, guidebooks, product reviews, consumer electronics news, and podcasts. The website was launched on November 1, 2011, and uses Vox Media's proprietary multimedia publishing platform Chorus. In 2014, Nilay Patel was named editor-in-chief and Dieter Bohn executive editor; Helen Havlak was named editorial director in 2017. ''The Verge'' won five Webby Awards for the year 2012 including awards for Best Writing (Editorial), Best Podcast for ''The Vergecast'', Best Visual Design, Best Consumer Electronics Site, and Best Mobile News App. History Origins Between March and April 2011, up to nine of ''Engadget''s writers, editors, and product developers, including editor-in-chief Joshua Topolsky, left AOL, the company behind that website, to start a new gadget site. The other ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Central Processing Unit
A central processing unit (CPU), also called a central processor, main processor, or just processor, is the primary Processor (computing), processor in a given computer. Its electronic circuitry executes Instruction (computing), instructions of a computer program, such as arithmetic, logic, controlling, and input/output (I/O) operations. This role contrasts with that of external components, such as main memory and I/O circuitry, and specialized coprocessors such as graphics processing units (GPUs). The form, CPU design, design, and implementation of CPUs have changed over time, but their fundamental operation remains almost unchanged. Principal components of a CPU include the arithmetic–logic unit (ALU) that performs arithmetic operation, arithmetic and Bitwise operation, logic operations, processor registers that supply operands to the ALU and store the results of ALU operations, and a control unit that orchestrates the #Fetch, fetching (from memory), #Decode, decoding and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intel
Intel Corporation is an American multinational corporation and technology company headquartered in Santa Clara, California, and Delaware General Corporation Law, incorporated in Delaware. Intel designs, manufactures, and sells computer components such as central processing units (CPUs) and related products for business and consumer markets. It is one of the world's List of largest semiconductor chip manufacturers, largest semiconductor chip manufacturers by revenue, and ranked in the Fortune 500, ''Fortune'' 500 list of the List of largest companies in the United States by revenue, largest United States corporations by revenue for nearly a decade, from 2007 to 2016 Fiscal year, fiscal years, until it was removed from the ranking in 2018. In 2020, it was reinstated and ranked 45th, being the List of Fortune 500 computer software and information companies, 7th-largest technology company in the ranking. It was one of the first companies listed on Nasdaq. Intel supplies List of I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dell
Dell Inc. is an American technology company that develops, sells, repairs, and supports personal computers (PCs), Server (computing), servers, data storage devices, network switches, software, computer peripherals including printers and webcams among other products and services. Dell is based in Round Rock, Texas. Founded by Michael Dell in 1984, Dell started making IBM IBM PC compatible, clone computers and pioneered selling cut-price PCs directly to customers, managing its supply chain management, supply chain and electronic commerce. The company rose rapidly during the 1990s and in 2001 it became the largest global PC vendor for the first time. Dell was a pure hardware vendor until 2009 when it acquired Perot Systems. Dell then entered the market for IT services. The company has expanded storage and networking systems. In the late 2000s, it began expanding from offering computers only to delivering a range of technology for enterprise customers. Dell is a subsidiary of Dell ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PC World
''PC World'' (stylized as PCWorld) is a global computer magazine published monthly by IDG. Since 2013, it has been an online-only publication. It offers advice on various aspects of PCs and related items, the Internet, and other personal technology products and services. In each publication, ''PC World'' reviews and tests hardware and software products from a variety of manufacturers, as well as other technology related devices such as still and video cameras, audio devices and televisions. The current editorial director of ''PC World'' is Jon Phillips, formerly of ''Wired''. In August 2012, he replaced Steve Fox, who had been editorial director since the December 2008 issue of the magazine. Fox replaced the magazine's veteran editor Harry McCracken, who resigned that spring, after some rocky times, including quitting and being rehired over editorial control issues in 2007. ''PC World'' is published under other names such as PC Advisor and PC Welt in some countries. ''PC W ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |