|
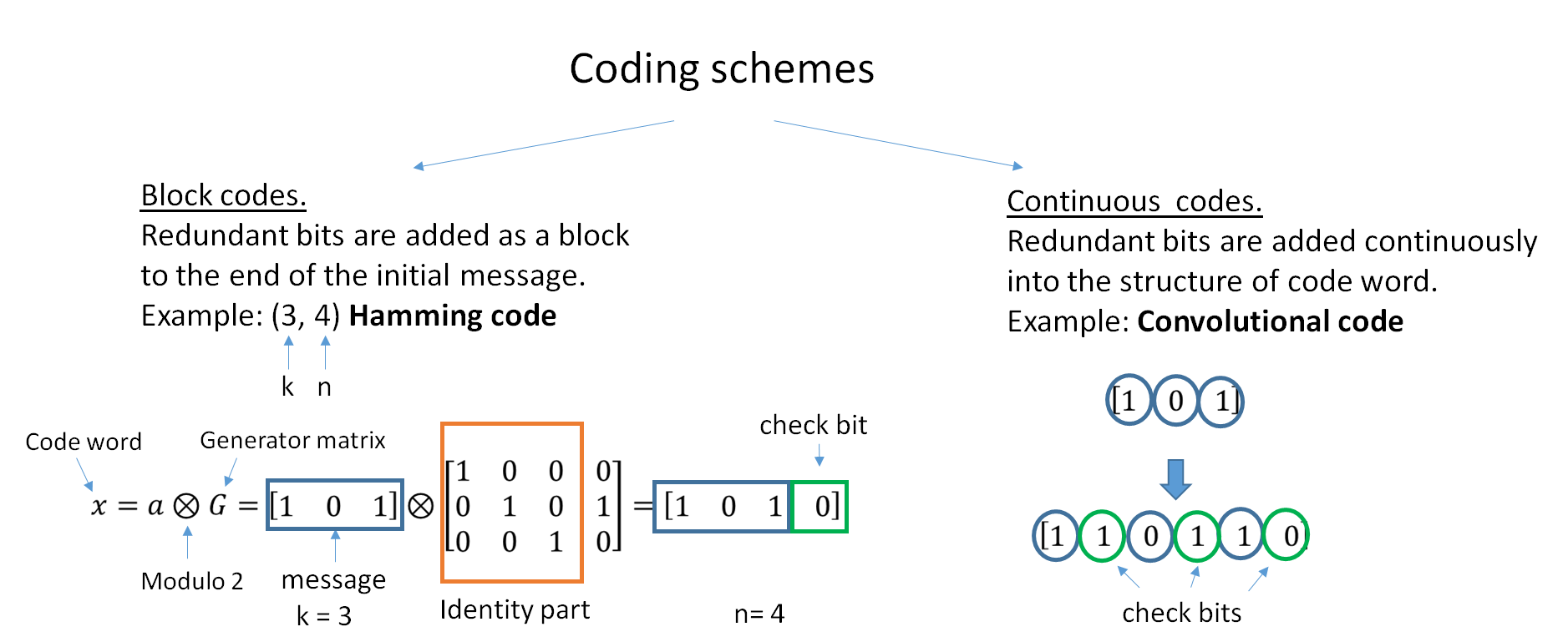
Locally Testable Code
A locally testable code is a type of error-correcting code for which it can be determined if a string is a word in that code by looking at a small (frequently constant) number of bits of the string. In some situations, it is useful to know if the data is corrupted without decoding all of it so that appropriate action can be taken in response. For example, in communication, if the receiver encounters a corrupted code, it can request the data be re-sent, which could increase the accuracy of said data. Similarly, in data storage, these codes can allow for damaged data to be recovered and rewritten properly. In contrast, locally decodable codes use a small number of bits of the codeword to probabilistically recover the original information. The fraction of errors determines how likely it is that the decoder correctly recovers the original bit; however, not all locally decodable codes are locally testable. Clearly, any valid codeword should be accepted as a codeword, but strings t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error-correcting Code
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is the sender encodes the message with redundant information in the form of an ECC. The redundancy allows the receiver to detect a limited number of errors that may occur anywhere in the message, and often to correct these errors without retransmission. The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code. ECC contrasts with error detection in that errors that are encountered can be corrected, not simply detected. The advantage is that a system using ECC does not require a reverse channel to request retransmission of data when an error occurs. The downside is that there is a fixed overhead that is added to the message, thereby requiring a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hadamard Code
The Hadamard code is an error-correcting code named after Jacques Hadamard that is used for error detection and correction when transmitting messages over very noisy or unreliable channels. In 1971, the code was used to transmit photos of Mars back to Earth from the NASA space probe Mariner 9. Because of its unique mathematical properties, the Hadamard code is not only used by engineers, but also intensely studied in coding theory, mathematics, and theoretical computer science. The Hadamard code is also known under the names Walsh code, Walsh family, and Walsh–Hadamard code in recognition of the American mathematician Joseph Leonard Walsh. The Hadamard code is an example of a linear code of length 2^m over a binary alphabet. Unfortunately, this term is somewhat ambiguous as some references assume a message length k = m while others assume a message length of k = m+1. In this article, the first case is called the Hadamard code while the second is called the augmented Hadam ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hamming Code
In computer science and telecommunication, Hamming codes are a family of linear error-correcting codes. Hamming codes can detect one-bit and two-bit errors, or correct one-bit errors without detection of uncorrected errors. By contrast, the simple parity code cannot correct errors, and can detect only an odd number of bits in error. Hamming codes are perfect codes, that is, they achieve the highest possible rate for codes with their block length and minimum distance of three. Richard W. Hamming invented Hamming codes in 1950 as a way of automatically correcting errors introduced by punched card readers. In his original paper, Hamming elaborated his general idea, but specifically focused on the Hamming(7,4) code which adds three parity bits to four bits of data. In mathematical terms, Hamming codes are a class of binary linear code. For each integer there is a code-word with block length and message length . Hence the rate of Hamming codes is , which is the highest p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gilbert–Varshamov Bound
In coding theory, the Gilbert–Varshamov bound (due to Edgar Gilbert and independently Rom Varshamov.) is a limit on the parameters of a (not necessarily linear) code. It is occasionally known as the Gilbert– Shannon–Varshamov bound (or the GSV bound), but the name "Gilbert–Varshamov bound" is by far the most popular. Varshamov proved this bound by using the probabilistic method for linear codes. For more about that proof, see Gilbert–Varshamov bound for linear codes. Statement of the bound Let :A_q(n,d) denote the maximum possible size of a ''q''-ary code C with length ''n'' and minimum Hamming distance ''d'' (a ''q''-ary code is a code over the field \mathbb_q of ''q'' elements). Then: :A_q(n,d) \geqslant \frac. Proof Let C be a code of length n and minimum Hamming distance d having maximal size: :, C, =A_q(n,d). Then for all x\in\mathbb_q^n , there exists at least one codeword c_x \in C such that the Hamming distance d(x,c_x) between x and c_x satisfies :d(x ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Long Code (mathematics)
In theoretical computer science and coding theory, the long code is an error-correcting code that is locally decodable. Long codes have an extremely poor rate, but play a fundamental role in the theory of hardness of approximation. Definition Let f_1,\dots,f_ : \^k\to \ for k=\log n be the list of ''all'' functions from \^k\to\. Then the long code encoding of a message x\in\^k is the string f_1(x)\circ f_2(x)\circ\dots\circ f_(x) where \circ denotes concatenation of strings. This string has length 2^n=2^. The Walsh-Hadamard code is a subcode of the long code, and can be obtained by only using functions f_i that are linear functions when interpreted as functions \mathbb F_2^k\to\mathbb F_2 on the finite field In mathematics, a finite field or Galois field (so-named in honor of Évariste Galois) is a field that contains a finite number of elements. As with any field, a finite field is a set on which the operations of multiplication, addition, subtr ... with two elements. S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bitwise XOR
In computer programming, a bitwise operation operates on a bit string, a bit array or a binary numeral (considered as a bit string) at the level of its individual bits. It is a fast and simple action, basic to the higher-level arithmetic operations and directly supported by the processor. Most bitwise operations are presented as two-operand instructions where the result replaces one of the input operands. On simple low-cost processors, typically, bitwise operations are substantially faster than division, several times faster than multiplication, and sometimes significantly faster than addition. While modern processors usually perform addition and multiplication just as fast as bitwise operations due to their longer instruction pipelines and other architectural design choices, bitwise operations do commonly use less power because of the reduced use of resources. Bitwise operators In the explanations below, any indication of a bit's position is counted from the right (least signif ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Uniform Distribution (discrete)
In probability theory and statistics, the discrete uniform distribution is a symmetric probability distribution wherein a finite number of values are equally likely to be observed; every one of ''n'' values has equal probability 1/''n''. Another way of saying "discrete uniform distribution" would be "a known, finite number of outcomes equally likely to happen". A simple example of the discrete uniform distribution is throwing a fair dice. The possible values are 1, 2, 3, 4, 5, 6, and each time the die is thrown the probability of a given score is 1/6. If two dice are thrown and their values added, the resulting distribution is no longer uniform because not all sums have equal probability. Although it is convenient to describe discrete uniform distributions over integers, such as this, one can also consider discrete uniform distributions over any finite set. For instance, a random permutation is a permutation generated uniformly from the permutations of a given length, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Probabilistically Checkable Proofs
In computational complexity theory, a probabilistically checkable proof (PCP) is a type of mathematical proof, proof that can be checked by a randomized algorithm using a bounded amount of randomness and reading a bounded number of bits of the proof. The algorithm is then required to accept correct proofs and reject incorrect proofs with very high probability. A standard proof (or Certificate (complexity), certificate), as used in the Formal verification, verifier-based definition of the complexity class NP (complexity), NP, also satisfies these requirements, since the checking procedure deterministically reads the whole proof, always accepts correct proofs and rejects incorrect proofs. However, what makes them interesting is the existence of probabilistically checkable proofs that can be checked by reading only a few bits of the proof using randomness in an essential way. Probabilistically checkable proofs give rise to many complexity classes depending on the number of queries req ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
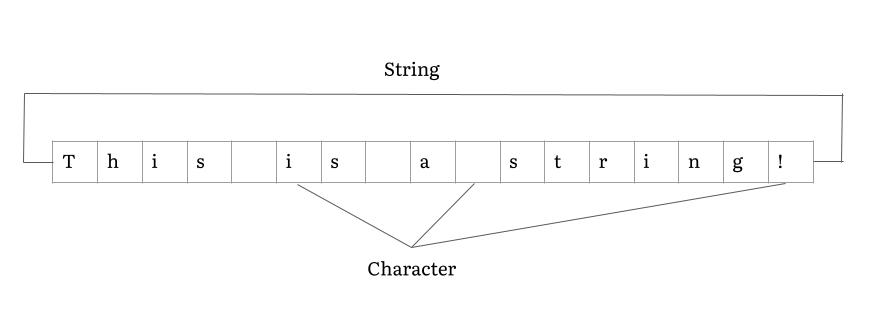
String (computer Science)
In computer programming, a string is traditionally a sequence of characters, either as a literal constant or as some kind of variable. The latter may allow its elements to be mutated and the length changed, or it may be fixed (after creation). A string is generally considered as a data type and is often implemented as an array data structure of bytes (or words) that stores a sequence of elements, typically characters, using some character encoding. ''String'' may also denote more general arrays or other sequence (or list) data types and structures. Depending on the programming language and precise data type used, a variable declared to be a string may either cause storage in memory to be statically allocated for a predetermined maximum length or employ dynamic allocation to allow it to hold a variable number of elements. When a string appears literally in source code, it is known as a string literal or an anonymous string. In formal languages, which are used in ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quanta Magazine
''Quanta Magazine'' is an editorially independent online publication of the Simons Foundation covering developments in physics, mathematics, biology and computer science. ''Undark Magazine'' described ''Quanta Magazine'' as "highly regarded for its masterful coverage of complex topics in science and math." The science news aggregator ''RealClearScience'' ranked ''Quanta Magazine'' first on its list of "The Top 10 Websites for Science in 2018." In 2020, the magazine received a National Magazine Award for General Excellence from the American Society of Magazine Editors for its "willingness to tackle some of the toughest and most difficult topics in science and math in a language that is accessible to the lay reader without condescension or oversimplification." The articles in the magazine are freely available to read online. ''Scientific American'', Wired (magazine), ''Wired'', ''The Atlantic'', and ''The Washington Post'', as well as international science publications like ''Spekt ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |